Last Update 2 hours ago Total Questions : 65
The Cloud Associate (JNCIA-Cloud) content is now fully updated, with all current exam questions added 2 hours ago. Deciding to include JN0-214 practice exam questions in your study plan goes far beyond basic test preparation.
You'll find that our JN0-214 exam questions frequently feature detailed scenarios and practical problem-solving exercises that directly mirror industry challenges. Engaging with these JN0-214 sample sets allows you to effectively manage your time and pace yourself, giving you the ability to finish any Cloud Associate (JNCIA-Cloud) practice test comfortably within the allotted time.
Which two tools are used to deploy a Kubernetes environment for testing and development purposes? (Choose two.)
Click to the Exhibit button.
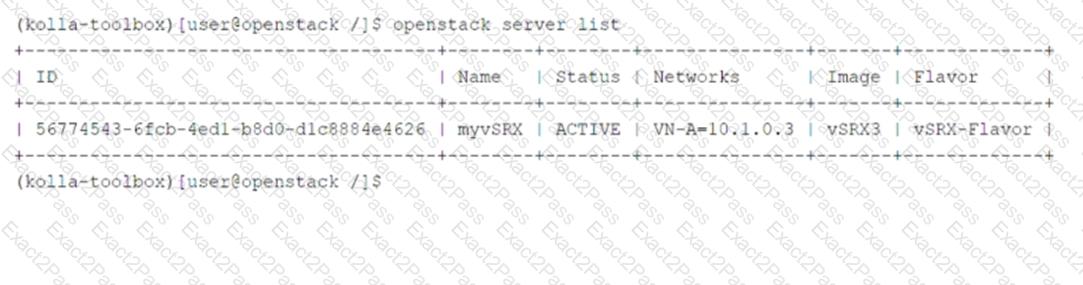
Referring to the exhibit, which two statements are correct? (Choose two.)
Which virtualization method requires less duplication of hardware resources?
Which component of Kubernetes runs on all nodes and ensures that the containers are running in a pod?
When considering OpenShift and Kubernetes, what are two unique resources of OpenShift? (Choose two.)
Which encapsulation protocol uses tunneling to provide a Layer 2 overlay over an underlying Layer 3 network?
Which component of Kubernetes runs on each node maintaining network rules?

