Last Update 18 hours ago Total Questions : 115
The Security, Professional (JNCIP-SEC) content is now fully updated, with all current exam questions added 18 hours ago. Deciding to include JN0-637 practice exam questions in your study plan goes far beyond basic test preparation.
You'll find that our JN0-637 exam questions frequently feature detailed scenarios and practical problem-solving exercises that directly mirror industry challenges. Engaging with these JN0-637 sample sets allows you to effectively manage your time and pace yourself, giving you the ability to finish any Security, Professional (JNCIP-SEC) practice test comfortably within the allotted time.
You want to configure the SRX Series device to map two peer interfaces together and ensure that there is no switching or routing lookup to forward traffic.
Which feature on the SRX Series device is used to accomplish this task?
You need to set up source NAT so that external hosts can initiate connections to an internal device, but only if a connection to the device was first initiated by the internal device.
Which type of NAT solution provides this functionality?
An ADVPN configuration has been verified on both the hub and spoke devices and it seems fine. However, OSPF is not functioning as expected.
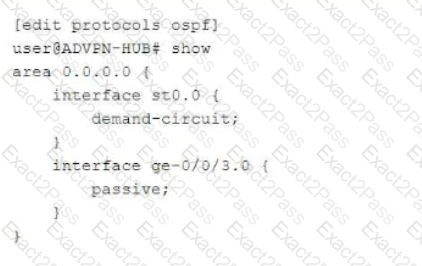
Referring to the exhibit, which two statements under interface st0.0 on both the hub and spoke devices would solve this problem? (Choose two.)
Referring to the exhibit,
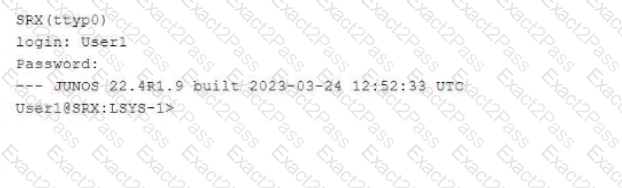
which two statements about User1 are true? (Choose two.)
What are three attributes that APBR queries from the application system cache module. (Choose Three)
You have an initial setup of ADVPN with two spokes and a hub. A host at partner Spoke-1 is sending traffic to a host at partner Spoke-2.
In this scenario, which statement is true?
Which two statements about transparent mode and Ethernet switching mode on an SRX series
device are correct.

