Last Update 23 hours ago Total Questions : 105
The Network Security Expert 8 Written Exam content is now fully updated, with all current exam questions added 23 hours ago. Deciding to include NSE8_812 practice exam questions in your study plan goes far beyond basic test preparation.
You'll find that our NSE8_812 exam questions frequently feature detailed scenarios and practical problem-solving exercises that directly mirror industry challenges. Engaging with these NSE8_812 sample sets allows you to effectively manage your time and pace yourself, giving you the ability to finish any Network Security Expert 8 Written Exam practice test comfortably within the allotted time.
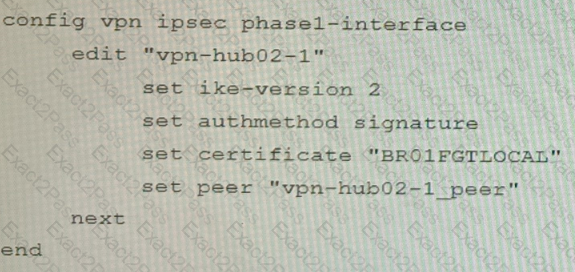
An HA topology is using the following configuration:
Based on this configuration, how long will it take for a failover to be detected by the secondary cluster member?
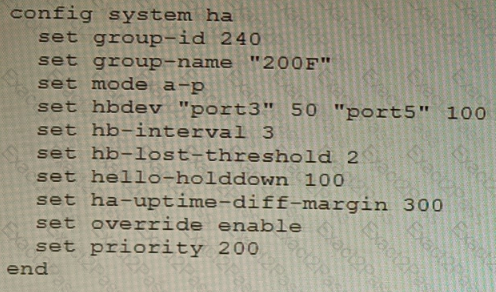
Refer to the exhibit, which shows diagnostic output.
A customer reports that ICMP traffic flow from 192.168.1.11 to 93.190.134.171 is not corresponding to the SD-WAN setup.
What is the problem in this scenario?
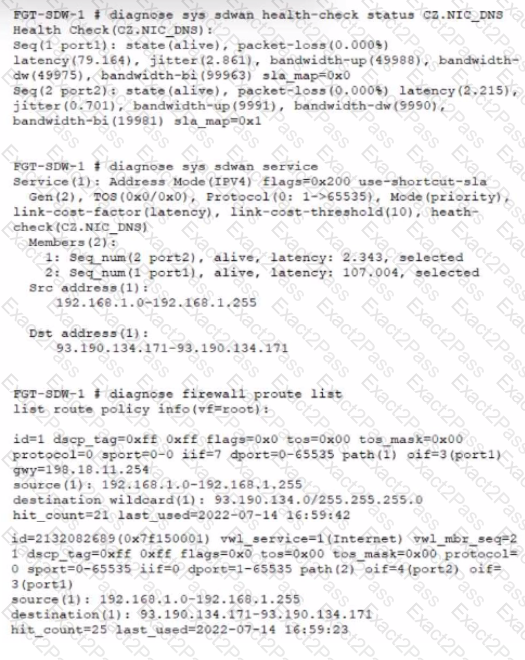
Refer to the exhibit.
A customer reports that they are not able to reach subnet 10.10.10.0/24 from their FortiGate device.
Based on the exhibit, what should you do to correct the situation?
Refer to the exhibit.
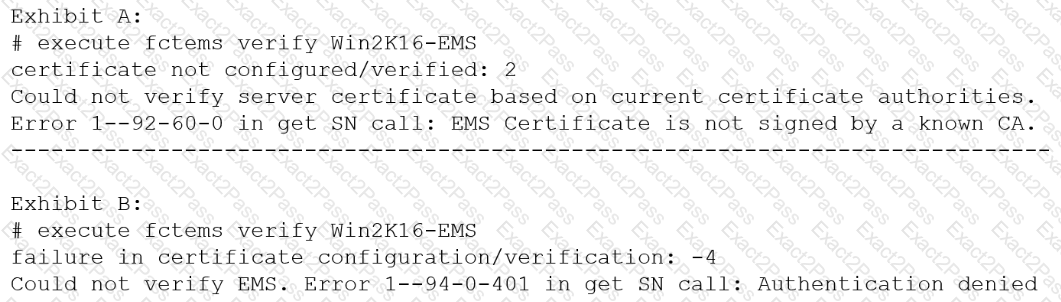
The exhibit shows two error messages from a FortiGate root Security Fabric device when you try to configure a new connection to a FortiClient EMS Server.
Referring to the exhibit, which two actions will fix these errors? (Choose two.)
A Hub FortiGate is connecting multiple branch FortiGate devices separating the traffic centrally in unique VRFs. Routing information is exchanged using BGP between the Hub and the Branch FortiGate devices.
You want to efficiently enable route leaking of specific routes between the VRFs.
Which two steps are required to achieve this requirement? (Choose two.)
Refer to the exhibit.
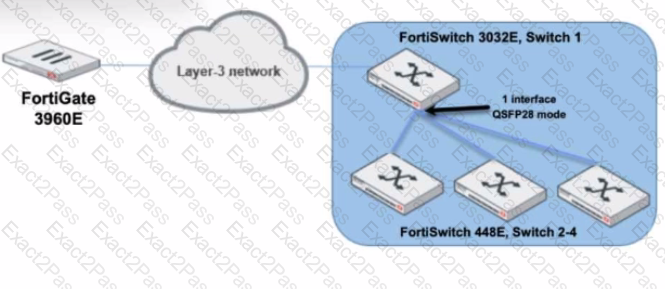
You are managing a FortiSwitch 3032E that is managed by FortiLink on a FortiGate 3960E. The 3032E is heavily utilized and there is only one port free.
The requirement is to add an additional three FortiSwitch 448E devices with 10Gbps SFP+ connectivity directly to the 3032E. The plan is to use split port (phy-mode) with QSFP28 mode to connect the new 448E switches.
In this scenario, which statement about the switch deployment is correct?
Refer to the exhibits.
Exhibit A
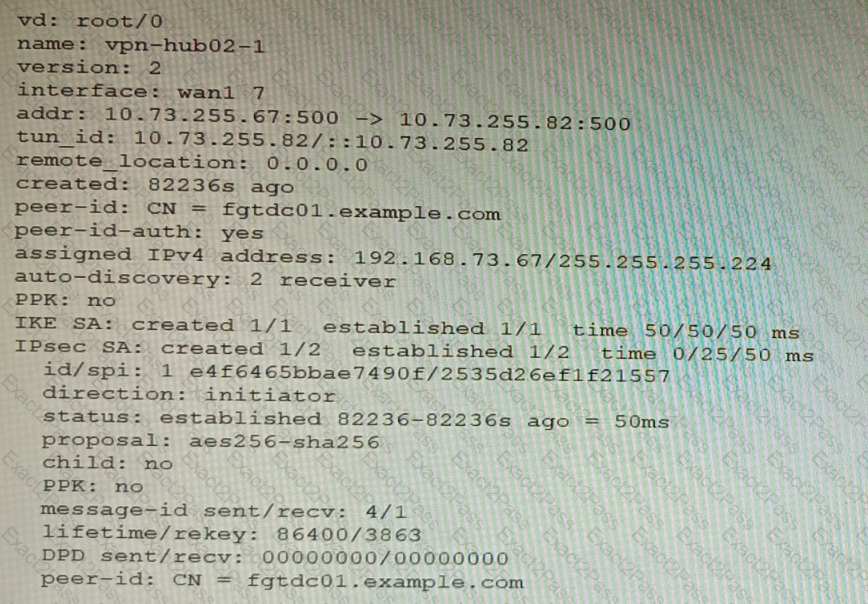
Exhibit B
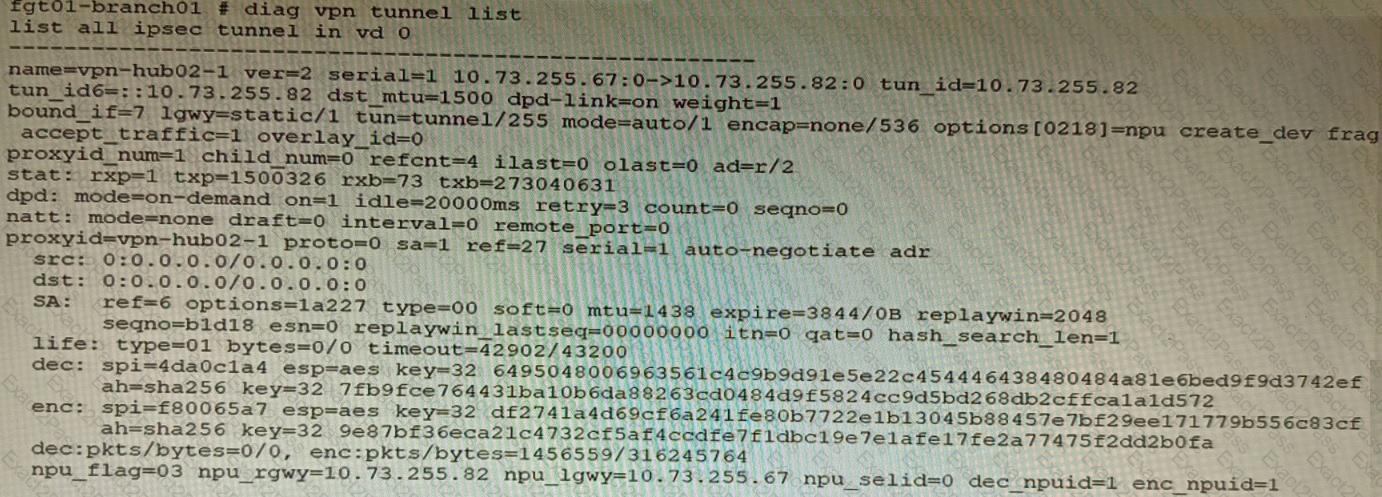
Exhibit C
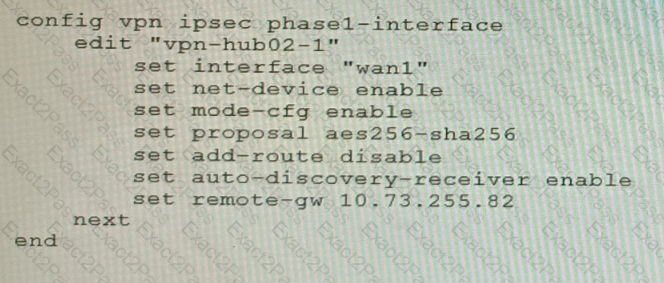
A customer is trying to set up a VPN with a FortiGate, but they do not have a backup of the configuration. Output during a troubleshooting session is shown in the exhibits A and B and a baseline VPN configuration is shown in Exhibit C Referring to the exhibits, which configuration will restore VPN connectivity?
A)
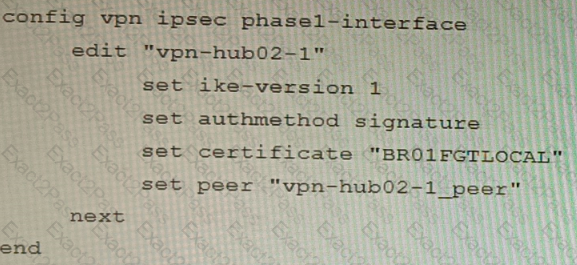
B)
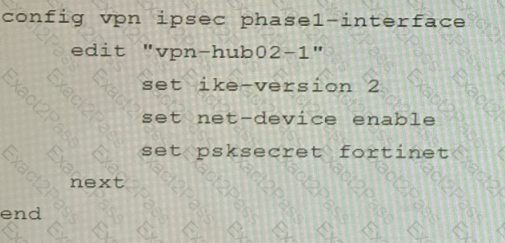
C)
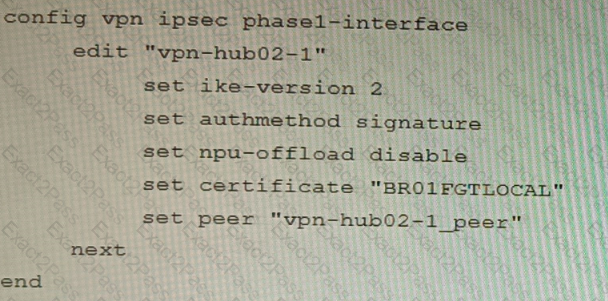
D)