Last Update 17 hours ago Total Questions : 542
The Microsoft 365 Administrator Exam content is now fully updated, with all current exam questions added 17 hours ago. Deciding to include MS-102 practice exam questions in your study plan goes far beyond basic test preparation.
You'll find that our MS-102 exam questions frequently feature detailed scenarios and practical problem-solving exercises that directly mirror industry challenges. Engaging with these MS-102 sample sets allows you to effectively manage your time and pace yourself, giving you the ability to finish any Microsoft 365 Administrator Exam practice test comfortably within the allotted time.
You need to ensure that the support technicians can meet the technical requirement for the Montreal office mobile devices.
What is the minimum of dedicated support technicians required?
You have an Azure AD tenant and a Microsoft 365 E5 subscription. The tenant contains the users shown in the following table.
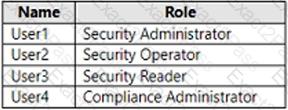
You plan to implement Microsoft Defender for Endpoint.
You verify that role-based access control (RBAC) is turned on in Microsoft Defender for Endpoint.
You need to identify which user can view security incidents from the Microsoft 365 Defender portal.
Which user should you identify?
You have a Microsoft 365 E5 subscription that uses Microsoft Intune.
You have devices enrolled in Intune as shown in the following table.
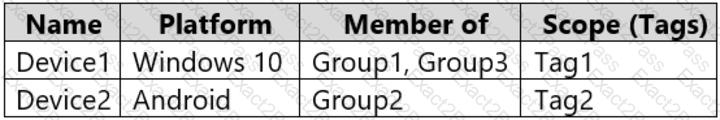
You create the device configuration profiles shown in the following table.
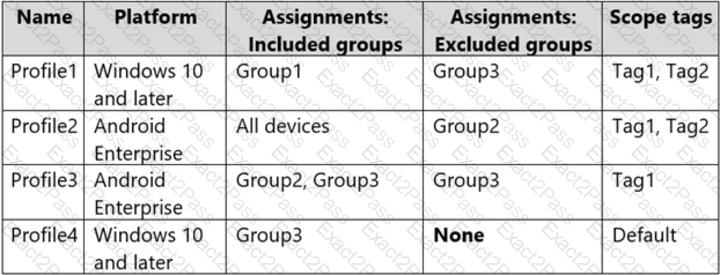
Which profiles will be applied to each device? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.

You have a Microsoft 365 subscription.
You register two applications named App1 and App2 to Azure AD.
You need to ensure that users who connect to App1 require multi-factor authentication (MFA). MFA is required only for App1. What should you do?
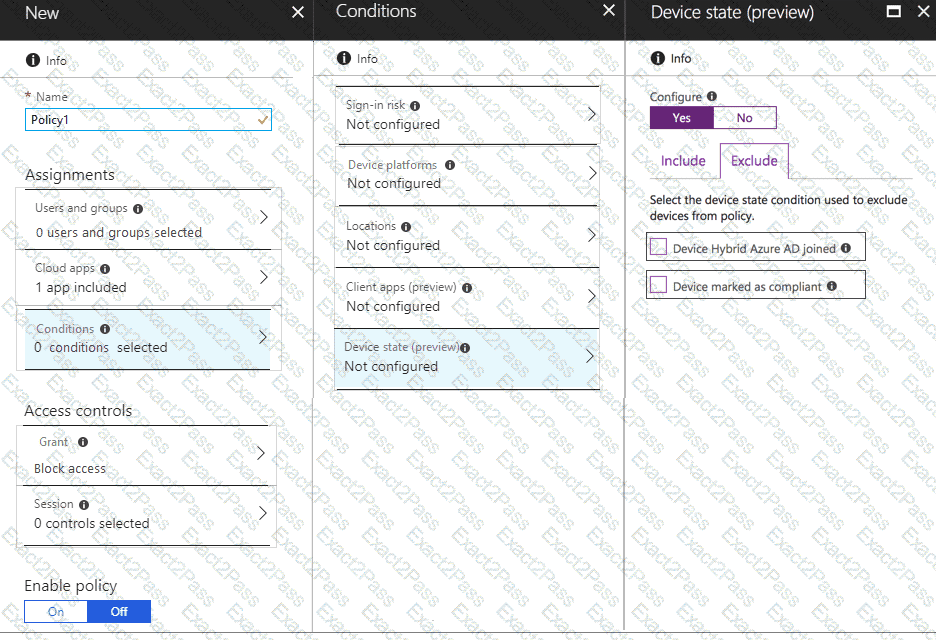
You need to configure a conditional access policy to meet the compliance requirements.
You add Exchange Online as a cloud app.
Which two additional settings should you configure in Policy1? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
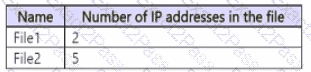
You have a Microsoft 365 E5 subscription that contains a SharePoint site named Site1. Site1 contains the files shown in the following table.
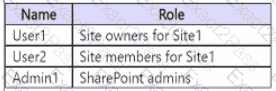
You have the users shown in the following table.
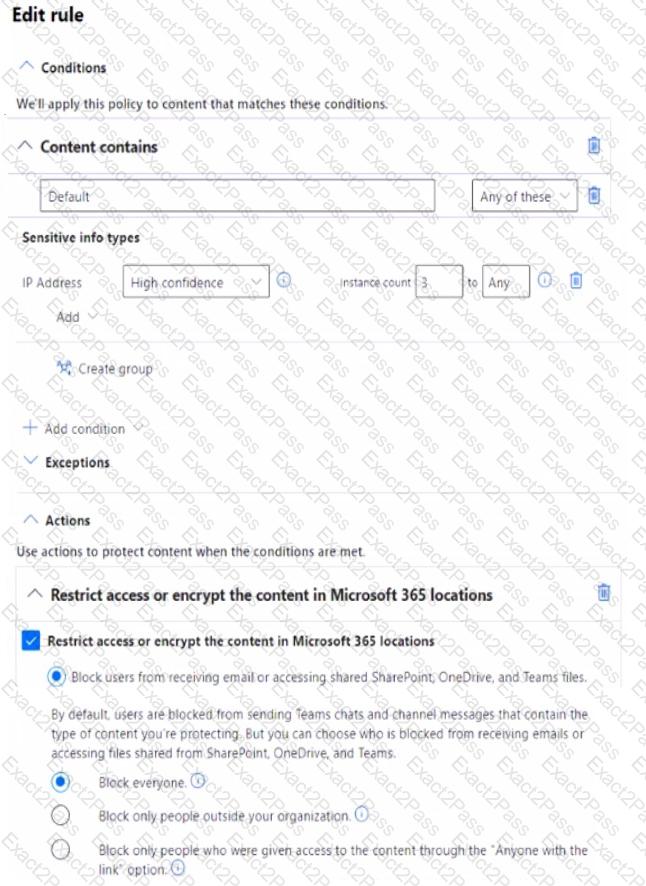
You create a data loss prevention (DLP) policy with an advanced DLP rule and apply the policy to Site1. The DLP rule is configured as shown in the following exhibit.
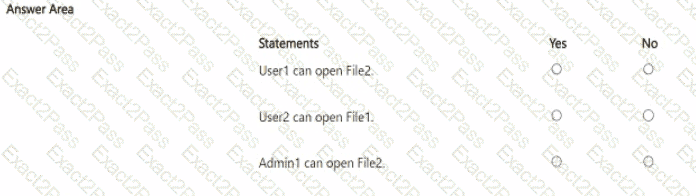
For each of the following statements, select Yes if the statement is true Otherwise, select No
NOTE: Each correct selection is worth one point.
Your company has three main offices and one branch office. The branch office is used for research.
The company plans to implement a Microsoft 365 tenant and to deploy multi-factor authentication.
You need to recommend a Microsoft 365 solution to ensure that multi-factor authentication is enforced only for users in the branch office.
What should you include in the recommendation?

