The SWIFT PKI certificates are used for… (Select the correct answer)
•Connectivity
•Generic
•Products Cloud
•Products OnPrem
•Security
Asymmetric signing and encryption end to end
Asymmetric signing and encryption end to SWIFT only
Symmetric encryption only
Asymmetric signing only
SWIFT Public Key Infrastructure (PKI) certificates are cryptographic credentials used to secure communications over the SWIFT network. Let’s evaluate each option:
•Option A: Asymmetric signing and encryption end to end
This is correct. SWIFT PKI certificates utilize asymmetric cryptography (public and private key pairs) for both signing and encryption. Signing ensures the authenticity and integrity of messages (e.g., verifying the sender), while encryption provides confidentiality end to end—from the sender’s environment to the receiver’s environment across the SWIFT network. This end-to-end security is achieved using PKI certificates managed by Hardware Security Modules (HSMs), as mandated by CSCF Control "1.3 Cryptographic Failover." SWIFT documentation confirms that PKI supports full message security throughout the transmission process.
•Option B: Asymmetric signing and encryption end to SWIFT only
This is incorrect. The security provided by PKI certificates extends beyond just the connection to SWIFT (e.g., to the SWIFT Secure IP Network). It covers the entire message journey, including the recipient’s environment, ensuring end-to-end protection rather than stopping at SWIFT’s boundary.
•Option C: Symmetric encryption only
This is incorrect. SWIFT PKI relies on asymmetric cryptography for key exchange and signing, not symmetric encryption alone. While symmetric encryption may be used internally (e.g., for session keys derived from asymmetric key exchange), the PKI certificates themselves are based on asymmetric algorithms (e.g., RSA), as outlined in SWIFT’s security guidelines.
•Option D: Asymmetric signing only
This is incorrect. PKI certificates are used for both asymmetric signing (for authenticity and integrity) and encryption (for confidentiality), not just signing. The dual purpose is essential for the secure transmission of SWIFT messages.
Summary of Correct Answer:
SWIFT PKI certificates are used for asymmetric signing and encryption end to end (A), ensuring comprehensive security.
References to SWIFT Customer Security Programme Documents:
•SWIFT Customer Security Controls Framework (CSCF) v2024: Control 1.3 specifies the use of PKI for end-to-end security.
•SWIFT Security Guidelines: Details PKI usage for asymmetric signing and encryption.
•SWIFT PKI Documentation: Confirms end-to-end cryptographic protection using PKI certificates.
========
The outsourcing agent of the SWIFT user provided them with an independent assessment report covering the CSP components in their scope, and using the latest CSCF version for testing. Is it enough to support the CSP attestation for the outsourced components? (Select the correct answer)
•Swift Customer Security Controls Policy
•Swift Customer Security Controls Framework v2025
•Independent Assessment Framework
•Independent Assessment Process for Assessors Guidelines
•Independent Assessment Framework - High-Level Test Plan Guidelines
•Outsourcing Agents - Security Requirements Baseline v2025
•CSP Architecture Type - Decision tree
•CSP_controls_matrix_and_high_test_plan_2025
•Assessment template for Mandatory controls
•Assessment template for Advisory controls
•CSCF Assessment Completion Letter
•Swift_CSP_Assessment_Report_Template
Yes, after confirmation and validation of the scope
Yes, only if the outsourcing agent is a global trusted provider and published the report on their compliance portal
No, an audit report (and not an assessment) is required from the outsourcing agent as an external provider
No, except if the cloud provider components are partially covered by the SWIFT Alliance Connect Virtual programme
The "Outsourcing Agents - Security Requirements Baseline v2025" and "Independent Assessment Framework" address reliance on outsourcing agents’ assessments. Let’s evaluate each option:
•Option A: Yes, after confirmation and validation of the scope
This is correct. The SWIFT user can rely on the outsourcing agent’s independent assessment report if it covers the relevant CSP components and uses the latest CSCF version. However, the user’s assessor must confirm and validate the scope and findings to ensure alignment with the user’s attestation, as per the "Independent Assessment Process for Assessors Guidelines."
•Option B: Yes, only if the outsourcing agent is a global trusted provider and published the report on their compliance portal
This is incorrect. The CSP does not require the outsourcing agent to be a "global trusted provider" or publish the report publicly; validation by the user’s assessor is sufficient.
•Option C: No, an audit report (and not an assessment) is required from the outsourcing agent as an external provider
This is incorrect. An independent assessment report is acceptable, not necessarily an audit report, as long as it meets CSCF standards, per the "Outsourcing Agents - Security Requirements Baseline v2025."
•Option D: No, except if the cloud provider components are partially covered by the SWIFT Alliance Connect Virtual programme
This is incorrect. The Alliance Connect Virtual programme’s coverage is irrelevant; the key is the report’s validity and scope validation.
Summary of Correct Answer:
The report is sufficient after confirmation and validation of the scope (A).
References to SWIFT Customer Security Programme Documents:
•Outsourcing Agents - Security Requirements Baseline v2025: Allows reliance on agent assessments.
•Independent Assessment Process for Assessors Guidelines: Requires scope validation.
•Swift_CSP_Assessment_Report_Template: Supports integrated reporting.
========
The Alliance Gateway application is considered a messaging interface.
•Connectivity
•Generic
•Products Cloud
•Products OnPrem
•Security
TRUE
FALSE
Alliance Gateway (SAG) is a SWIFT product that facilitates connectivity between messaging interfaces and the SWIFT network. Let’s evaluate the statement:
•A messaging interface in SWIFT terminology refers to applications like Alliance Access (SAA) or Alliance Entry, which are responsible for creating, validating, and processing SWIFT messages (e.g., FIN MT messages). These interfaces handle the business logic of message flows, interfacing with back-office systems and preparing messages for transmission.
•Alliance Gateway, however, is classified as a communication interface. It acts as a hub to consolidate message flows from multiple messaging interfaces (e.g., Alliance Access) and connects them to the SWIFT network via SwiftNet Link (SNL). SAG does not create or process messages; it manages their transport, ensuring secure transmission over the SWIFT Secure IP Network (SIPN). This distinction is clear in SWIFT documentation, where SAG is described as a connectivity layer, not a messaging interface.
•The CSCF reinforces this separation by applying specific controls to messaging interfaces (e.g., "2.1 Internal Data Transmission Security" for Alliance Access) and communication interfaces (e.g., "1.1 SWIFT Environment Protection" for SAG). Since SAG does not perform the functions of a messaging interface, the statement is false.
Summary of Correct Answer:
Alliance Gateway is a communication interface, not a messaging interface, making the statement false.
References to SWIFT Customer Security Programme Documents:
•SWIFT Customer Security Controls Framework (CSCF) v2024: Differentiates messaging interfaces (Control 2.1) from communication interfaces (Control 1.1).
•SWIFT Alliance Gateway Documentation: Describes SAG as a communication interface for SWIFTNet connectivity.
•SWIFT Architecture Glossary: Clarifies the roles of messaging interfaces (e.g., Alliance Access) versus communication interfaces (e.g., Alliance Gateway).
========
The SWIFT user has a local communication interface as their main channel to SWIFT. For contingency, the SWIFT user also has a connector as a backup channel. What is the architecture type for this SWIFT user? (Select the correct answer)
•Swift Customer Security Controls Policy
•Swift Customer Security Controls Framework v2025
•Independent Assessment Framework
•Independent Assessment Process for Assessors Guidelines
•Independent Assessment Framework - High-Level Test Plan Guidelines
•Outsourcing Agents - Security Requirements Baseline v2025
•CSP Architecture Type - Decision tree
•CSP_controls_matrix_and_high_test_plan_2025
•Assessment template for Mandatory controls
•Assessment template for Advisory controls
•CSCF Assessment Completion Letter
•Swift CSP Assessment Report Template
A1
A2
A3
A4
The SWIFT CSP defines architecture types (A1 to A4) based on the components a user owns and manages, as outlined in the "CSP Architecture Type - Decision tree" and "Swift Customer Security Controls Framework v2025." These types determine the applicable security controls and assessment requirements. Let’s analyze the scenario:
•A local communication interface refers to a component like Alliance Gateway (SAG), which manages connectivity to the SWIFT network via SwiftNet Link (SNL) and VPN boxes. The user owns this interface locally as their main channel.
•A connector (or customer connector) is a custom application or integration layer that connects to SWIFT services, often used as an alternative or backup channel. In this case, it serves as a contingency backup.
•The architecture types are:
oA1: Full stack (owns messaging interface, communication interface, and network components, e.g., Alliance Access, Alliance Gateway, VPN boxes).
oA2: Owns a customer connector and communication interface, with the messaging interface hosted elsewhere (e.g., by a service bureau or SWIFT).
oA3: Owns only a customer connector, relying on external communication and messaging interfaces.
oA4: Uses a fully hosted solution (e.g., Alliance Cloud or Lite2), owning no local components.
•The scenario indicates the user owns a local communication interface (e.g., SAG) as the primary channel and a connector as a backup. However, there is no mention of owning a messaging interface (e.g., Alliance Access) locally. This suggests the messaging interface is likely hosted externally (e.g., by a service bureau or SWIFT), which aligns with the A2 architecture type. The "CSP Architecture Type - Decision tree" classifies A2 as a user with a communication interface and a customer connector, where the messaging interface is not locally owned. The backup connector does not change the primary architecture type, as it is an additional component within the A2 framework.
•Option A: A1
This is incorrect. A1 requires ownership of a messaging interface (e.g., Alliance Access), which is not mentioned.
•Option B: A2
This is correct. A2 fits the scenario of owning a communication interface and a customer connector, with the messaging interface potentially hosted elsewhere.
•Option C: A3
This is incorrect. A3 involves only a customer connector, not a communication interface.
•Option D: A4
This is incorrect. A4 applies to fully hosted solutions with no local ownership of connectors or interfaces.
Summary of Correct Answer:
The SWIFT user with a local communication interface as the main channel and a connector as a backup is of architecture type A2 (B).
References to SWIFT Customer Security Programme Documents:
•Swift Customer Security Controls Framework v2025: Defines architecture types A1-A4.
•CSP Architecture Type - Decision tree: Classifies A2 for communication interface and customer connector ownership.
•Assessment template for Mandatory controls: Applies to A2 architecture.
========
How many Swift Security Officers does an organization need at minimum?

1
2
3
4
This question determines the minimum number of Swift Security Officers (SOs) required by an organization under theSwift Customer Security Programme (CSP).
Step 1: Understand Security Officer Requirements
TheSwift Customer Security Controls Framework (CSCF) v2024, underControl 2.3: System Access Control, and theSwift User Handbookoutline the roles and minimum requirements for Security Officers, who manage security settings and keys.
Step 2: Analyze the Requirement
TheSwift User HandbookandSwift Security Best Practicesspecify that at least two Security Officers are required to ensure segregation of duties and continuity (e.g., in case one is unavailable).
This minimum is enforced to prevent single points of failure and align withControl 2.3, which mandates multi-factor authentication and role separation for privileged access.
Step 3: Evaluate Each Option
A. 1: Insufficient, as a single SO risks unavailability or lack of segregation, perSwift Security Best Practices.Conclusion: Incorrect.
B. 2: Meets the minimum requirement for redundancy and segregation, as stated in theSwift User Handbook.Conclusion: Correct.
C. 3: Exceeds the minimum but is not required unless the organization’s risk assessment demands it, per theCSCF v2024.Conclusion: Incorrect (not minimum).
D. 4: Also exceeds the minimum, not mandated as a baseline.Conclusion: Incorrect (not minimum).
Step 4: Conclusion and Verification
The correct answer isB, as theCSCF v2024andSwift User Handbookmandate a minimum of two Swift Security Officers.
References
Swift Customer Security Controls Framework (CSCF) v2024, Control 2.3: System Access Control.
Swift User Handbook, Section: Security Officer Roles.
Swift Security Best Practices, Section: Segregation of Duties.
A Swift user has moved from one Service Bureau to another What are the obligations of the Swift user in the CSP context?

To inform the SB certification office at Swift WW
To reflect that in the next attestation cycle
None if there is no impact in the architecture tope
To submit an updated attestation reflecting this change within 3 months
This question addresses the obligations of a Swift user who has switched from one Service Bureau (SB) to another under the Customer Security Programme (CSP).
Step 1: Understand CSP Obligations for Changes
TheSwift Customer Security Controls Framework (CSCF) v2024andIndependent Assessment Frameworkrequire Swift users to maintain accurate and up-to-date information regarding their infrastructure,including changes in service providers like Service Bureaus. Such changes may impact compliance and architecture types.
Step 2: Evaluate Each Option
A. To inform the SB certification office at Swift WWThere is no specific "SB certification office" mentioned in theCSCF v2024orSwift CSP Guidelines. Notifications are typically handled through attestation updates, not a dedicated office.Conclusion: Incorrect.
B. To reflect that in the next attestation cycleWhile changes must be reflected in attestations, delaying this until the next cycle (e.g., annually) is insufficient if the change affects compliance. TheSwift CSP Compliance Guidelinesrequire timely updates for significant changes.Conclusion: Incorrect.
C. None if there is no impact in the architecture typeEven if the architecture type (e.g., A2, A4) remains unchanged, a switch in Service Bureau may affect security controls, vendor management, or connectivity. TheCSCF v2024underControl 1.1: Swift Environment Protectionrequires users to report changes that could impact compliance, regardless of architecture type.Conclusion: Incorrect.
D. To submit an updated attestation reflecting this change within 3 monthsTheSwift CSP Compliance GuidelinesandIndependent Assessment Frameworkmandate that significant changes (e.g., switching Service Bureaus) be reported through an updated attestation within 3 months. This ensures Swift is informed of potential compliance impacts and allows for review.Conclusion: Correct.
Step 3: Conclusion and Verification
The correct answer isD, as theCSCF v2024andSwift CSP Compliance Guidelinesrequire an updated attestation within 3 months to reflect a change in Service Bureau.
References
Swift Customer Security Controls Framework (CSCF) v2024, Control 1.1: Swift Environment Protection.
Swift Independent Assessment Framework, Section: Change Reporting.
Swift CSP Compliance Guidelines, Section: Timely Updates.
A Treasury Management System (TMS) application is installed on the same machine as the customer connector, connecting to a Service Bureau. Are these applications/systems in scope of CSCF? (Select the correct answer)
•Swift Customer Security Controls Policy
•Swift Customer Security Controls Framework v2025
•Independent Assessment Framework
•Independent Assessment Process for Assessors Guidelines
•Independent Assessment Framework - High-Level Test Plan Guidelines
•Outsourcing Agents - Security Requirements Baseline v2025
•CSP Architecture Type - Decision tree
•CSP_controls_matrix_and_high_test_plan_2025
•Assessment template for Mandatory controls
•Assessment template for Advisory controls
•CSCF Assessment Completion Letter
•Swift_CSP_Assessment_Report_Template
The TMS application, the customer connector, and the hosting system are in the scope of the CSCF
Only the customer connector application is in scope of the CSCF. The TMS application is a back-office
The TMS application is the highest risk and must be secured appropriately. The customer connector should be secured on a best effort basis
The TMS application, the customer connector, and the hosting system are in scope only if they connect directly to SWIFT, not towards a Service Bureau
The SWIFT Customer Security Controls Framework (CSCF) defines the scope of components that must comply with its security controls, particularly those handling SWIFT-related data or connectivity. Let’s analyze the scenario:
•A Treasury Management System (TMS) application is a back-office system used to manage financial operations, such as payments or liquidity management. A customer connector is a custom application or integration layer that connects the user’s systems (e.g., TMS) to the SWIFT infrastructure, in this case via a Service Bureau. The hosting system is the physical or virtual machine on which both applications are installed.
•The TMS and customer connector are on the same machine, and the customer connector connects to a Service Bureau, which hosts the SWIFT communication infrastructure (e.g., Alliance Gateway).
•CSCF Scope: The "Swift Customer Security Controls Framework v2025" and "CSP Architecture Type - Decision tree" define the scope as including:
oCustomer connectors: These are in scope because they facilitate SWIFT connectivity (e.g., sending/receiving SWIFT messages), even if connecting via a Service Bureau.
oSystems hosting in-scope components: The hosting system (machine) is in scope because it runs the customer connector, which is directly involved in SWIFT data flows.
oBack-office systems (e.g., TMS): Normally, back-office systems are out of scope unless they are closely integrated with SWIFT infrastructure. In this case, the TMS is installed on the same machine as the customer connector, creating a shared environment. The CSCF considers systems in the same environment as in-scope if they could impact the security of SWIFT-related components (e.g., Control "1.1 SWIFT Environment Protection").
•Service Bureau Context: Connecting to a Service Bureau (architecture type A2) does not exempt the local components from CSCF scope. The "Independent Assessment Framework" requires assessing all local components that interact with SWIFT, even if the communication layer is outsourced.
•Option A: The TMS application, the customer connector, and the hosting system are in the scope of the CSCF
This is correct. The customer connector is explicitly in scope as it handles SWIFT data flows. The hosting system is in scope because it runs the connector. The TMS, while typically a back-office system, is in scope because it shares the same machine, creating a risk of lateral movement or privilege escalation (e.g., CSCF Control "1.1"). The "CSP_controls_matrix_and_high_test_plan_2025" includes shared environments in the assessment scope.
•Option B: Only the customer connector application is in scope of the CSCF. The TMS application is a back-office
This is incorrect. While the TMS is a back-office system, its co-location on the same machine as the customer connector brings it into scope due to shared risks, as per CSCF guidelines.
•Option C: The TMS application is the highest risk and must be secured appropriately. The customer connector should be secured on a best effort basis
This is incorrect. The CSCF does not prioritize the TMS as the "highest risk" nor suggest "best effort" security for the customer connector. Both components must be secured per mandatory controls when in scope.
•Option D: The TMS application, the customer connector, and the hosting system are in scope only if they connect directly to SWIFT, not towards a Service Bureau
This is incorrect. The CSCF scope includes components connecting via a Service Bureau, as they still handle SWIFT data and are part of the user’s architecture (e.g., A2).
Summary of Correct Answer:
The TMS application, customer connector, and hosting system are all in scope of the CSCF (A) due to their shared environment and connectivity to SWIFT via a Service Bureau.
References to SWIFT Customer Security Programme Documents:
•Swift Customer Security Controls Framework v2025: Control 1.1 includes shared environments in scope.
•CSP Architecture Type - Decision tree: Classifies A2 for Service Bureau setups with local connectors.
•Independent Assessment Framework: Requires assessing all components in shared environments.
========
A detailed CSP assessment report has been provided to the Swift user following the assessment. Is a completion letter also mandated to be supplied?

Yes
No
This question concerns the deliverables following a CSP assessment, specifically whether a completion letter is mandated alongside a detailed assessment report.
Step 1: Understand CSP Assessment Deliverables
The Swift Customer Security Programme (CSP) requires an independent assessment to validate compliance with theCustomer Security Controls Framework (CSCF) v2024. TheIndependent Assessment Frameworkoutlines the process and deliverables, including the submission of assessment reports and related documentation to Swift.
Step 2: Analyze the Requirement for a Completion Letter
TheIndependent Assessment Frameworkmandates that, following an assessment, the assessor provides a detailed report to the Swift user, documenting the findings, control effectiveness, and any remediation actions.
Additionally, Swift requires acompletion letterto confirm that the assessment has been conducted in accordance with CSP guidelines. This letter, typically signed by the assessor or the user’s authorized representative, certifies the completion of the assessment and is submitted to Swift as part of the attestation process. This is detailed in theSwift CSP Compliance Guidelinesand theIndependent Assessment Framework, which specify that both the report and the completion letter are required for formal submission.
The completion letter serves as an official acknowledgment that the assessment meets Swift’s quality and procedural standards, complementing the detailed report.
Step 3: Conclusion and Verification
The answer isA, as theCSCF v2024andIndependent Assessment Frameworkmandate that a completion letter must be supplied alongside the detailed assessment report to fulfill Swift’s compliance requirements.
References
Swift Customer Security Controls Framework (CSCF) v2024, Section: Independent Assessment Requirements.
Swift Independent Assessment Framework, Section: Deliverables and Attestation.
Swift CSP Compliance Guidelines, Section: Assessment Submission Process.
Which statements are true of Alliance Messaging Hub (AMH)? (Select the correct answer)
•Connectivity
•Generic
•Products Cloud
•Products OnPrem
•Security
AMH is highly resilient, and can consist of multiple instances and sites in parallel
AMH provides advanced integration capabilities
AMH is a messaging interface able to connect to other financial networks, not only SWIFT
All of the above
Alliance Messaging Hub (AMH) is a SWIFT product designed as a centralized messaging platform for financial institutions, enabling them to manage multiple messaging flows, including SWIFT and non-SWIFT networks. Let’s evaluate each statement:
•Statement A: AMH is highly resilient, and can consist of multiple instances and sites in parallel
This is true. AMH is designed for high availability and resilience, supporting deployments across multiple instances and sites to ensure continuity of operations. This capability is critical for large financial institutions handling high volumes of transactions. SWIFT documentation highlights AMH’s ability to operate in a distributed architecture, with instances running in parallel across primary and backup sites. This aligns with CSCF Control "1.1 SWIFT Environment Protection," which emphasizes the need for resilient infrastructure to prevent disruptions in the SWIFT environment.
•Statement B: AMH provides advanced integration capabilities
This is true. AMH offers advanced integration features, allowing institutions to connect various back-office systems, payment engines, and other financial applications to a single hub. It supports multiple message standards (e.g., SWIFT MT, ISO 20022) and provides transformation and routing capabilities, making it a versatile integration platform. This is a key selling point of AMH, as noted in SWIFT’s product documentation, enabling seamless interoperability across diverse systems.
•Statement C: AMH is a messaging interface able to connect to other financial networks, not only SWIFT
This is true. AMH is not limited to SWIFT messaging; it can connect to other financial networks, such as domestic payment systems, real-time gross settlement (RTGS) systems, or proprietary networks. AMH acts as a universal messaging hub, supporting multiple protocols and standards beyond SWIFT’s ecosystem (e.g., FIX for securities trading). This capability is well-documented in SWIFT’s AMH product overview, positioning it as a flexible solution for institutions with diverse connectivity needs.
•Statement D: All of the above
Since all three statements (A, B, and C) are true, this option is the correct answer. AMH’s design for resilience, advanced integration, and multi-network connectivity makes it a comprehensive messaging solution.
Summary of Correct Answer:
All statements about AMH are true, making "All of the above" (D) the correct choice.
References to SWIFT Customer Security Programme Documents:
•SWIFT Customer Security Controls Framework (CSCF) v2024: Control 1.1 emphasizes resilience, which AMH supports through its architecture.
•SWIFT Alliance Messaging Hub Documentation: Highlights AMH’s multi-site resilience, integration capabilities, and support for non-SWIFT networks.
•SWIFT Product Overview: Describes AMH as a universal messaging hub for SWIFT and other financial networks.
========
Which user roles are available in Alliance Cloud by default. (Choose all that apply.)

Role and Operator management
Message Management
Administrator
Message Security Administrator
This question pertains to the default user roles available in Alliance Cloud, a SWIFT cloud-based messaging solution:
Step 1: Alliance Cloud Overview
Alliance Cloud provides a hosted messaging service (e.g., for Alliance Lite2 or RMA), with predefined roles for managing operations, security, and messages. Default roles are outlined in the product documentation.
Select the supporting documents to conduct a CSP assessment. (Choose all that apply.)

The CSP User Handbook
The mapping to industry standards article
The Controls Matrix and High Level Test P an
The Customer Security Controls Framework
This question identifies the supporting documents for a CSP assessment under theSwift Customer Security Programme (CSP).
Step 1: Understand Assessment Documentation
TheIndependent Assessment FrameworkandCSCF v2024specify the documents assessors must use to evaluate compliance with CSCF controls.
Step 2: Evaluate Each Option
A. The CSP User HandbookTheSwift CSP User Handbookprovides guidance on CSP requirements, processes, and best practices, making it a key supporting document for assessors.Conclusion: Correct.
B. The mapping to industry standards articleWhile useful for context, this article is not a primary document for conducting assessments. TheCSCF v2024focuses on its own controls, not industry mappings, which are advisory.Conclusion: Incorrect.
C. The Controls Matrix and High Level Test PlanTheControls Matrix(part of the CSCF) maps controls to components, and theHigh Level Test Planoutlines assessment procedures. Both are essential for structuring and executing the assessment, per theIndependent Assessment Framework.Conclusion: Correct.
D. The Customer Security Controls FrameworkTheCSCF v2024is the foundational document defining controls and requirements, mandatory for all assessments.Conclusion: Correct.
Step 3: Conclusion and Verification
The correct answers areA, C, and D, as these documents are explicitly referenced in theCSCF v2024andIndependent Assessment Frameworkfor conducting CSP assessments.
References
Swift Customer Security Controls Framework (CSCF) v2024, Section: Assessment Guidance.
Swift Independent Assessment Framework, Section: Supporting Documents.
Swift CSP User Handbook, Section: Assessment Process.
Which authentication methods are possible on the Alliance Interfaces? (Choose all that apply.)

Password
LDAP Authentication
Radius One-time password
Password and TOTP
This question identifies the authentication methods supported by Alliance Interfaces (e.g., Alliance Access, Alliance Gateway) under theSwift Customer Security Controls Framework (CSCF) v2024.
Step 1: Understand Authentication on Alliance Interfaces
TheCSCF v2024, underControl 2.3: System Access Control, mandates strong authentication for access to Swift-related components, including Alliance Interfaces. TheSwift Alliance Gateway Technical DocumentationandAlliance Access User Guidedetail supported methods.
Step 2: Evaluate Each Option
A. PasswordAlliance Interfaces support basic password authentication as a standard method, as noted in theAlliance Access User Guide. While not the strongest alone, it is permitted with additional controls.Conclusion: Correct.
B. LDAP AuthenticationLDAP (Lightweight Directory Access Protocol) is supported for centralized authentication, integrating with enterprise directory services, per theSwift Security Best PracticesandControl 2.3.Conclusion: Correct.
C. Radius One-time passwordRADIUS with one-time passwords (OTP) is not a standard authentication method for Alliance Interfaces. TheAlliance Gateway Technical Documentationdoes not list RADIUS OTP as supported, focusing instead on password, LDAP, and TOTP.Conclusion: Incorrect.
D. Password and TOTPTime-based One-Time Password (TOTP) combined with password (multi-factor authentication) is supported for enhanced security, as required byControl 2.3and detailed in theSwift Security Best Practicesfor privileged access.Conclusion: Correct.
Step 3: Conclusion and Verification
The correct answers areA, B, and D, as these methods are supported by Alliance Interfaces, aligning withCSCF v2024and related documentation.
References
Swift Customer Security Controls Framework (CSCF) v2024, Control 2.3: System Access Control.
Swift Alliance Gateway Technical Documentation, Section: Authentication Methods.
Swift Security Best Practices, Section: Multi-Factor Authentication.
Which operator session flows are expected to be protected in terms of confidentiality and integrity? (Choose all that apply.)

System administrator sessions towards a host running a Swift related component
All sessions to and from a jump server used to access a component in a secure zone
All sessions towards a secure zone (on-premises or hosted by a third-party or a Cloud Provider)
All sessions towards a Swift related application run by an Outsourcing Agent, a Service Bureau or an L2BA Provider
This question addresses the obligations of Swift users regarding the submission of assessment-related documents to Swift under the Customer Security Programme (CSP).
Step 1: Understand CSP Assessment Submission Requirements
TheSwift Customer Security Controls Framework (CSCF) v2024and theIndependent Assessment Frameworkoutline the process for CSP assessments, including what must be submitted to Swift. The focus is on ensuring compliance through attestation, with specific deliverables defined.
Step 2: Evaluate Each Option
A. Yes, all documents produced from the assessment must be provided proactively to SwiftThis is incorrect. TheIndependent Assessment Frameworkdoes not require proactive submission of all assessment documents (e.g., detailed reports, working papers). Only the completion letter and attestation are typically submitted unless otherwise requested by Swift.Conclusion: Incorrect.
B. No, it is not required to provide Swift with any documents by default. However, Swift can request a copy of the Assessment completion letterTheCSCF v2024andIndependent Assessment Frameworkstate that users are not required to proactively submit the full assessment report or other documents. However, Swift retains the right to request the completion letter (certifying assessment completion) or additional evidence during quality assurance reviews. This aligns with theSwift CSP Compliance Guidelines.Conclusion: Correct.
C. Yes, a copy of (only) the assessment report must be provided to Swift, no other documentsThis is incorrect. The full assessment report is not mandated for proactive submission; only the completion letter is typically required unless requested. TheIndependent Assessment Frameworkemphasizes the completion letter as the key deliverable.Conclusion: Incorrect.
D. Yes, in cases where a customer performs an Independent assessment rather than an audit then a copy of the assessment report must be provided. However, it is not required for the Swift user to provide any forms when an Internal/External Audit is performedThis is partially misleading. TheIndependent Assessment Frameworkdoes not distinguish between independent assessments and audits in terms of mandatory report submission. For both, the completion letter is the default submission, with reports requested only if needed. The differentiation based on assessment type is not supported byCSCF v2024guidelines.Conclusion: Incorrect.
Step 3: Conclusion and Verification
The correct answer isB, as theCSCF v2024andIndependent Assessment Frameworkdo not require proactive submission of the full assessment report, but Swift can request the completion letter as part of its oversight process.
References
Swift Customer Security Controls Framework (CSCF) v2024, Section: Independent Assessment Requirements.
Swift Independent Assessment Framework, Section: Deliverables and Submission.
Swift CSP Compliance Guidelines, Section: Document Submission Rules.
=========================
This question identifies which operator session flows must be protected for confidentiality and integrity under theSwift Customer Security Controls Framework (CSCF) v2024.
Step 1: Understand Session Protection Requirements
TheCSCF v2024, underControl 2.4: Secure Session Management, mandates that all sessions involving access to Swift-related components or secure zones must be protected using strong encryption (e.g., TLS) and integrity controls to prevent unauthorized access or data tampering. This applies to operator and administrator sessions interacting with the Swift environment.
Step 2: Evaluate Each Option
A. System administrator sessions towards a host running a Swift related componentAdministrator sessions to hosts running Swift components (e.g., Alliance Access, Gateway) are in scope, as they require protection perControl 2.4to ensure confidentiality and integrity of administrative actions.Conclusion: Correct.
B. All sessions to and from a jump server used to access a component in a secure zoneJump servers are used to access secure zones (perControl 1.1: Swift Environment Protection), and all sessions to and from them must be encrypted and integrity-protected, as specified inControl 2.4.Conclusion: Correct.
C. All sessions towards a secure zone (on-premises or hosted by a third-party or a Cloud Provider)Secure zones, whether on-premises or hosted (e.g., by outsourcing agents or cloud providers), contain Swift components and must have all incoming sessions protected perControl 2.4andControl 1.1.Conclusion: Correct.
D. All sessions towards a Swift related application run by an Outsourcing Agent, a Service Bureau or an L2BA ProviderSessions to Swift-related applications managed by outsourcing agents or service bureaus (e.g., Components C, D, E in the diagram) are in scope, as they handle Swift traffic and must be secured perControl 2.4and theSwift Outsourcing Guidelines.Conclusion: Correct.
Step 3: Conclusion and Verification
All options (A, B, C, D) are correct, asControl 2.4of theCSCF v2024requires protection of all listed session types to ensure confidentiality and integrity across the Swift ecosystem, including secure zones, hosted environments, and outsourced applications.
References
Swift Customer Security Controls Framework (CSCF) v2024, Control 2.4: Secure Session Management, Control 1.1: Swift Environment Protection.
Swift Security Best Practices, Section: Session Security.
Swift Outsourcing Guidelines, Section: Session Protection.
From the outsourcing agent diagram, which components in the diagram are in scope and applicable for the Swift user.

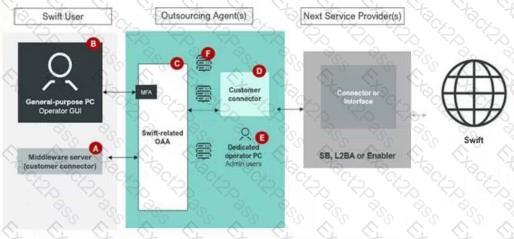
Components A, B, C, D and E
Components A and B
Components C, D and E
None of the above
This question determines which components in the outsourcing agent diagram are in scope and applicable for the Swift user under theSwift Customer Security Controls Framework (CSCF) v2024.
Step 1: Understand CSCF Scope and the Diagram
TheCSCF v2024defines the scope as systems directly involved in Swift messaging, connectivity, or security within the user’s control or responsibility, including those managed by outsourcing agents. The diagram includes:
A. Middleware server (customer connector): Part of the Swift user’s environment.
B. General-purpose PC Operator GUI: An operator system in the user’s environment.
C. Swift-related OAA: The messaging interface in the outsourcing agent’s environment.
D. Customer connector: A connector in the outsourcing agent’s environment interfacing with the next service provider.
E. Dedicated PC Admin users: Administrative systems in the outsourcing agent’s environment.
TheIndependent Assessment Frameworkholds the Swift user accountable for in-scope components, even when outsourced, perControl 1.1: Swift Environment Protection.
Step 2: Analyze Component Applicability
A. Middleware server (customer connector): Located in the Swift user’s environment, this connects to the outsourcing agent. While it facilitates Swift traffic, it is typically considered part of the user’s local infrastructure and not directly in the outsourcing agent’s scope for user responsibility, unless explicitly outsourced. TheCSCF v2024scope focuses on Swift-related systems managed by the outsourcing agent when the user relies on them.
B. General-purpose PC Operator GUI: This is a user-side operator system, not a core Swift component. PerControl 1.2: Logical Access Control, it is out of the secure zone and not in scope for the outsourcing agent’s responsibility.
C. Swift-related OAA: This is the messaging interface (e.g., Alliance Access) managed by the outsourcing agent. It is in scope for the Swift user, as they are responsible for its security and compliance, perControl 1.1.
D. Customer connector: This connector, within the outsourcing agent’s environment, interfaces with the next service provider (e.g., SB, L2BA). It is in scope, as the user must ensure its security underControl 1.1.
E. Dedicated PC Admin users: These administrative systems, managed by the outsourcing agent, are in scope because they control Swift-related components, perControl 1.2.
Step 3: Match with Options
A. Components A, B, C, D and E: Includes A and B, which are not in scope for the outsourcing agent’s responsibility under the user’s purview.
B. Components A and B: Only includes user-side components, not the outsourcing agent’s in-scope systems.
C. Components C, D and E: Includes the outsourcing agent’s Swift-related OAA, customer connector, and admin PCs, which are in scope for the user’s compliance responsibility.
D. None of the above: Incorrect, as C, D, and E are applicable.
Step 4: Conclusion and Verification
The correct answer isC, as Components C, D, and E, managed by the outsourcing agent, are in scope and applicable for the Swift user’s compliance under theCSCF v2024.
References
Swift Customer Security Controls Framework (CSCF) v2024, Control 1.1: Swift Environment Protection, Control 1.2: Logical Access Control.
Swift Independent Assessment Framework, Section: Outsourcing Scope.
Swift Outsourcing Guidelines, Section: User Responsibility.
What is expected regarding Token Management when (physical or software-based) tokens are used? (Choose all that apply.)

Similar to user accounts, individual assignment and ownership for accurate traceability and revocation in case of potential tampering, loss or in case of user role change
Have in place a strict token assignment process. This avoids the need to perform g a regular review of assigned tokens
Individuals must not share their tokens. Tokens must remain under the control and supervision of its owner
All tokens must be stored in a safe when not used
This question relates to Control 5.2 – Token Management in the CSCF, which outlines requirements for managing physical or software-based tokens used for authentication or cryptographic operations in the SWIFT environment. Let’s evaluate each option:
A. Similar to user accounts, individual assignment and ownership for accurate traceability and revocation in case of potential tampering, loss or in case of user role change
CSCF Control 5.2 mandates that tokens (e.g., HSM tokens or software tokens) be uniquely assigned to individuals to ensure traceability and accountability. This allows for revocation in cases of tampering, loss, or role changes, mirroring user account management principles under Control 5.1 – Logical Access Control.
Can an internal audit department submit and approve their Swift user's attestation on the KYC-SA Swift portal?

Yes, providing this is agreed by the head of IT operations and the CISO
No, this is never an option
Yes, an internal auditor can submit the attestation for approval provided they have the appropriate credentials for switt.com. The CISO remains in charge of the approval of the attestation
Yes, with approval from the Chief auditor
This question examines whether an internal audit department can submit and approve a Swift user’s attestation on the KYC-SA Swift portal.
Step 1: Understand Attestation Process
TheIndependent Assessment FrameworkandCSCF v2024require attestations to be submitted by an independent party or authorized user representative, not the internal audit department, to ensure objectivity.
Step 2: Evaluate Each Option
A. Yes, providing this is agreed by the head of IT operations and the CISOInternal audit cannot submit or approve attestations, regardless of internal agreements, per theIndependent Assessment Framework.Conclusion: Incorrect.
B. No, this is never an optionTheCSCF v2024andSwift CSP Compliance Guidelinesprohibit internal audit from submitting or approving attestations, as they lack independence from the audited entity.Conclusion: Correct.
C. Yes, an internal auditor can submit the attestation for approval provided they have the appropriate credentials for swift.com. The CISO remains in charge of the approval of the attestationIncorrect. Internal auditors cannot submit or approve, even with credentials, due to independence requirements.Conclusion: Incorrect.
D. Yes, with approval from the Chief auditorIncorrect. Chief auditor approval does not override the independence requirement.Conclusion: Incorrect.
Step 3: Conclusion and Verification
The correct answer isB, as theCSCF v2024andIndependent Assessment Frameworkprohibit internal audit from submitting or approving attestations.
References
Swift Customer Security Controls Framework (CSCF) v2024, Section: Independent Assessment.
Swift Independent Assessment Framework, Section: Attestation Submission.
Swift CSP Compliance Guidelines, Section: Independence Requirements.
The Physical Security protection control is also aimed at protecting the “on call” and “working from home” employees’ equipment used to access the Swift-related components.

TRUE
FALSE
This question pertains to Control 7.3 – Physical Security in the CSCF:
Step 1: Control 7.3 Overview
Control 7.3 focuses on “physically securing SWIFT-related systems and components” (e.g., servers, HSMs) within the user’s premises to prevent unauthorized access, tampering, or theft.
To verify the applicability of a CSCF control to a specific component, several actions may be considered. Which one does not apply in this case?
•Swift Customer Security Controls Policy
•Swift Customer Security Controls Framework v2025
•Independent Assessment Framework
•Independent Assessment Process for Assessors Guidelines
•Independent Assessment Framework - High-Level Test Plan Guidelines
•Outsourcing Agents - Security Requirements Baseline v2025
•CSP Architecture Type - Decision tree
•CSP_controls_matrix_and_high_test_plan_2025
•Assessment template for Mandatory controls
•Assessment template for Advisory controls
•CSCF Assessment Completion Letter
•Swift_CSP_Assessment_Report_Template
Check in the CSP Policy document
Check appendix F of the CSCF
Check carefully the Introduction section of the CSCF
Open a case with SWIFT support via the case manager on swift.com if further information or solution cannot be found in the documentation
Verifying the applicability of a CSCF control to a specific component involves consulting relevant SWIFT documentation and processes. The "Swift Customer Security Controls Framework v2025" and associated guidelines provide the framework for this determination. Let’s evaluate each option:
•Option A: Check in the CSP Policy document
This does not apply. The "Swift Customer Security Controls Policy" is a high-level document outlining the CSP’s objectives and requirements but does not provide detailed guidance on control applicability to specific components. Control applicability is determined by the CSCF itself (e.g., through appendices or the control matrix), not the policy document, which is more strategic than operational.
•Option B: Check appendix F of the CSCF
This applies. Appendix F of the CSCF (or a similar appendix in the v2025 version) typically includes guidance on control applicability, mapping controls to different architecture types and components. This is a standard action for assessors, as noted in the "Independent Assessment Process for Assessors Guidelines."
•Option C: Check carefully the Introduction section of the CSCF
This applies. The Introduction section of the CSCF provides an overview of the framework’s scope, objectives, and how controls apply to various components, making it a relevant resource for verification.
•Option D: Open a case with SWIFT support via the case manager on swift.com if further information or solution cannot be found in the documentation
This applies. If documentation does not resolve the applicability question, SWIFT support via the case manager on swift.com is a recognized escalation path, as outlined in the "Independent Assessment Framework" and SWIFT operational guidelines.
Summary of Correct Answer:
Checking the CSP Policy document (A) does not apply, as it is not the appropriate resource for verifying control applicability to specific components.
References to SWIFT Customer Security Programme Documents:
•Swift Customer Security Controls Framework v2025: Provides applicability guidance in appendices (e.g., Appendix F) and the Introduction.
•Independent Assessment Process for Assessors Guidelines: Recommends using CSCF appendices and support channels.
•CSP_controls_matrix_and_high_test_plan_2025: Supports control applicability analysis.
========
An application only uses (i) the SWIFT API for reporting and gpi basic tracker calls through (ii) a tailored account not allowing business transactions management. Is this application in scope of the CSCF? (Select the correct answer)
•Swift Customer Security Controls Policy
•Swift Customer Security Controls Framework v2025
•Independent Assessment Framework
•Independent Assessment Process for Assessors Guidelines
•Independent Assessment Framework - High-Level Test Plan Guidelines
•Outsourcing Agents - Security Requirements Baseline v2025
•CSP Architecture Type - Decision tree
•CSP_controls_matrix_and_high_test_plan_2025
•Assessment template for Mandatory controls
•Assessment template for Advisory controls
•CSCF Assessment Completion Letter
•Swift_CSP_Assessment_Report_Template
Yes, it is in scope and considered a customer connector because it reads business transaction data
No, it can be descoped because there is no business transaction management being performed
No, it is not in scope because the API connection method is not in scope of the CSP
Yes, it is in scope because the API connection method is less secure than SWIFT interfaces
The CSCF applies to all SWIFT users and components that handle SWIFT-related data or connectivity, including customer connectors and interfaces. The scope is defined by the "Swift Customer Security Controls Framework v2025" and the "CSP Architecture Type - Decision tree." Let’s evaluate the scenario and options:
•The application uses the SWIFT API for reporting and gpi basic tracker calls (e.g., tracking payment statuses via the SWIFT gpi Tracker) through a tailored account that does not allow business transaction management (e.g., creating or sending MT messages like MT103). This limits its functionality to read-only or monitoring activities.
•CSCF Scope: The CSCF applies to components that process or manage SWIFT business transactions (e.g., payment messages) or provide connectivity to the SWIFT network. The "CSP Architecture Type - Decision tree" classifies components into architecture types (A1-A4), with customer connectors and interfaces in scope if they handle transactional data or enable SWIFT connectivity. Reporting and tracking via APIs, without transaction management, do not constitute business transaction processing.
•Option A: Yes, it is in scope and considered a customer connector because it reads business transaction data
This is incorrect. While the application reads transaction data (e.g., via gpi Tracker), the CSCF scope is primarily focused on components that manage or transmit business transactions (e.g., creating or sending messages). Reading data for reporting purposes does not classify it as a customer connector requiring full CSCF compliance unless it also handles transactional flows. The "Swift_CSP_Assessment_Report_Template" focuses on transactional interfaces.
•Option B: No, it can be descoped because there is no business transaction management being performed
This is correct. Since the application does not manage business transactions (e.g., it cannot initiate or modify payments), it falls outside the primary scope of the CSCF. The "Independent Assessment Framework" allows for descoping of components that do not process transactional data, provided they are isolated from the SWIFT secure zone. This aligns with the "CSP Architecture Type - Decision tree," which excludes non-transactional reporting tools from mandatory assessment.
•Option C: No, it is not in scope because the API connection method is not in scope of the CSP
This is incorrect. The SWIFT API connection method is within the CSP scope if it interacts with SWIFT services (e.g., gpi Tracker), but the key factor is the lack of transaction management, not the API itself.
•Option D: Yes, it is in scope because the API connection method is less secure than SWIFT interfaces
This is incorrect. Security of the connection method (e.g., API vs. traditional interfaces) does not determine CSCF scope. The scope is based on functionality (transaction management), and the statement’s premise about security is not a valid criterion per CSCF guidelines.
Summary of Correct Answer:
The application is not in scope of the CSCF and can be descoped because it does not perform business transaction management (B).
References to SWIFT Customer Security Programme Documents:
•Swift Customer Security Controls Framework v2025: Defines scope based on transaction management.
•CSP Architecture Type - Decision tree: Guides descoping of non-transactional components.
•Independent Assessment Framework: Allows descoping of reporting-only applications.
========
Which statements are correct about the Alliance Access LSO and RSO? (Select the two correct answers that apply)
•Connectivity
•Generic
•Products Cloud
•Products OnPrem
•Security
They are Alliance Security Officers
Their PKI certificates are stored either on an HSM Token or on an HSM-box
They are the business profiles that can sign the SWIFT financial transactions
They are responsible for the configuration and management of the security functions in the messaging interface
The Local Security Officer (LSO) and Remote Security Officer (RSO) are roles defined within the SWIFT Alliance suite, particularly for managing security in messaging interfaces like Alliance Access. Let’s evaluate each option:
•Option A: They are Alliance Security Officers
This is correct. The LSO and RSO are collectively referred to as Alliance Security Officers within the SWIFT ecosystem. The LSO is typically an on-site officer responsible for local security management, while the RSO can perform similar functions remotely, often for distributed environments. These roles are critical for configuring and maintaining security settings in Alliance Access, as outlined in SWIFT’s operational documentation. The CSCF Control "6.1 Security Awareness" emphasizes the importance of trained security officers, which aligns with the LSO/RSO roles.
•Option B: Their PKI certificates are stored either on an HSM Token or on an HSM-box
This is incorrect. While PKI certificates are used for authentication and are managed within the SWIFT environment, they are not specifically tied to the LSO or RSO roles in terms of storage. PKI certificates for SWIFTNet are stored and managed by the Hardware Security Module (HSM), either as an HSM token (e.g., a smart card) or an HSM-box (e.g., a physical or virtual HSM device). However, these certificates are associated with the SWIFT application or user roles (e.g., for message signing), not the LSO/RSO profiles themselves. The LSO/RSO uses these certificates as part of their duties, but the statement implies ownership or storage, which is inaccurate. CSCF Control "1.3 Cryptographic Failover" specifies HSM management, not LSO/RSO certificate storage.
•Option C: They are the business profiles that can sign the SWIFT financial transactions
This is incorrect. The LSO and RSO are security management roles, not business profiles authorized to sign financial transactions. Signing SWIFT financial transactions (e.g., MT103 messages) is the responsibility of authorized business users or automated processes within Alliance Access, who use PKI certificates managed by the HSM. The LSO/RSO’s role is to configure and oversee security, not to perform transactional activities. This distinction is clear in SWIFT’s role-based access control documentation.
•Option D: They are responsible for the configuration and management of the security functions in the messaging interface
This is correct. The LSO and RSO are tasked with configuring and managing security functions within Alliance Access, such as user access control, authentication settings, and compliance with CSCF requirements. This includes managing PKI certificate usage, setting up secure communication channels, and ensuring the messaging interface adheres to security policies. For example, the LSO can define security profiles and monitor access, as detailed in the Alliance Access Administration Guide, aligning with CSCF Control "2.1 Internal Data Transmission Security."
Summary of Correct Answers:
The LSO and RSO are Alliance Security Officers (A) and are responsible for the configuration and management of security functions in the messaging interface (D). Their PKI certificates are not stored by them, and they do not sign transactions.
References to SWIFT Customer Security Programme Documents:
•SWIFT Customer Security Controls Framework (CSCF) v2024: Control 6.1 highlights the role of security officers like LSO/RSO.
•SWIFT Alliance Access Documentation: Describes LSO/RSO responsibilities for security configuration.
•SWIFT Security Guidelines: Details PKI certificate management by HSM, not LSO/RSO.
========
Is it necessary to formally explain to the Swift user the testing methodology that will be used for the CSP assessment during the kick-off?

Yes
No
This question concerns the assessor’s obligations during the CSP assessment kick-off:
Step 1: CSP Assessment Process
The IAF recommends a kick-off meeting to align expectations between the assessor and SWIFT user, including explaining the testing methodology (e.g., HLTP, sampling, evidence collection).
Compliance to 2.9 Transaction Business Controls can be obtained through different ways. Which of the following one does not ensure compliance?
•Swift Customer Security Controls Policy
•Swift Customer Security Controls Framework v2025
•Independent Assessment Framework
•Independent Assessment Process for Assessors Guidelines
•Independent Assessment Framework - High-Level Test Plan Guidelines
•Outsourcing Agents - Security Requirements Baseline v2025
•CSP Architecture Type - Decision tree
•CSP_controls_matrix_and_high_test_plan_2025
•Assessment template for Mandatory controls
•Assessment template for Advisory controls
•CSCF Assessment Completion Letter
•Swift_CSP_Assessment_Report_Template
More than one of the measures proposed in the implementation guidelines are implemented
A customer-designed implementation that encounters the control objective and addresses the risk driver
Reliance on a recent business assessment or regulator response confirming effectiveness of the existing control
Any implementation if approved by the CIO
CSCF Control 2.9 (Transaction Business Controls) requires institutions to implement measures to ensure the accuracy and integrity of SWIFT transactions (e.g., payment validation, authorization). Compliance can be achieved through various methods, as outlined in the "Swift Customer Security Controls Framework v2025" and its implementation guidelines. Let’s evaluate each option:
•Option A: More than one of the measures proposed in the implementation guidelines are implemented
This ensures compliance. The CSCF provides implementation guidelines for Control 2.9, suggesting measures like dual authorization or automated validation. Implementing multiple measures meets the control’s objective of ensuring transaction integrity.
•Option B: A customer-designed implementation that encounters the control objective and addresses the risk driver
This ensures compliance. The CSCF allows flexibility for customer-designed solutions, provided they meet the control objective (e.g., preventing fraudulent transactions) and address the identified risk drivers (e.g., human error), as validated in the "Assessment template for Mandatory controls."
•Option C: Reliance on a recent business assessment or regulator response confirming effectiveness of the existing control
This ensures compliance. If a recent assessment (e.g., by an internal audit or regulator) confirms that existing controls effectively meet the CSCF 2.9 requirements, this can be accepted as evidence of compliance, per the "Independent Assessment Framework."
•Option D: Any implementation if approved by the CIO
This does not ensure compliance. The Chief Information Officer (CIO) approval alone does not guarantee that the implementation meets CSCF requirements. Compliance must be based on objective evidence and alignment with the control’s intent, as assessed against the "CSP_controls_matrix_and_high_test_plan_2025" and validated by an independent assessor, not just internal approval.
Summary of Correct Answer:
Reliance on CIO approval alone (D) does not ensure compliance with CSCF 2.9.
References to SWIFT Customer Security Programme Documents:
•Swift Customer Security Controls Framework v2025: Control 2.9 and implementation guidelines.
•Independent Assessment Framework: Requires objective validation, not just CIO approval.
•Assessment template for Mandatory controls: Specifies evidence-based compliance.
========
Can a Swift user choose to implement the security controls (example: logging and monitoring) in systems which are not directly in scope of the CSCE?

Yes
No
This question asks whether a Swift user can implement security controls (e.g., logging and monitoring) in systems not directly in scope of the CSCF. Let’s analyze this based on Swift CSP guidelines.
Step 1: Define CSCF Scope and Security Controls
TheSwift Customer Security Controls Framework (CSCF) v2024defines its scope as the Swift-related infrastructure, including messaging interfaces, communication interfaces, and operator systems (asdetailed in Question 4). Security controls likelogging and monitoringare mandated underControl Objective 6: Detect Anomalous Activity, specifically in controls likeControl 6.1: Security Event Logging.
Step 2: Analyze the Question
The question focuses on whether a Swift user can apply CSCF security controls (e.g., logging and monitoring) to systemsnot directly in scopeof the CSCF. Systems not in scope include back-office systems, general-purpose servers, or other infrastructure that does not directly process Swift messages or connect to the Swift network.
Step 3: Evaluate Swift CSP Guidance
The CSCF mandates that security controls must be applied to in-scope systems to ensure the security of the Swift environment. However, Swift also encourages adefense-in-depthapproach, as outlined in theSwift Customer Security Programme – Security Best Practices. This approach recommends extending security practices beyond the minimum scope to enhance overall security.
Control 6.1: Security Event Loggingrequires logging and monitoring for in-scope systems to detect anomalous activity. While this control is mandatory for in-scope systems, the CSCF does not prohibit applying similar controls to out-of-scope systems. In fact, theSwift CSP FAQ(available on swift.com) clarifies that users may implement additional security measures on out-of-scope systems to reduce risks to the Swift environment (e.g., monitoring back-office systems that interact with Swift middleware).
Implementing logging and monitoring on out-of-scope systems can help detect threats that might indirectly affect the Swift environment, such as lateral movement from a compromised back-office system to a Swift-related system.
Step 4: Conclusion and Verification
A Swift usercanchoose to implement security controls like logging and monitoring on systems not directly in scope of the CSCF. This is not mandatory but is considered a best practice under Swift’s defense-in-depth strategy. The CSCF does not restrict users from applying additional security measures beyond its defined scope, and such actions align with the broader goal of enhancing cybersecurity across the user’s environment.
References
Swift Customer Security Controls Framework (CSCF) v2024, Control 6.1: Security Event Logging.
Swift Customer Security Programme – Security Best Practices, Section: Defense-in-Depth.
Swift CSP FAQ, Section: Scope and Applicability of Security Controls.
Which ones are Alliance Lite2 key components? (Choose all that apply.)

A web interface
An AutoClient
A HSM box
A WebSphere MQ Server
This question identifies the key components of Alliance Lite2 under theSwift Customer Security Programme (CSP).
Step 1: Understand Alliance Lite2 Components
Alliance Lite2 is a browser-based Swift solution for smaller institutions, with a simplified architecture. Its components are detailed in theSwift Alliance Lite2 User Guideand referenced in theCSCF v2024context.
Step 2: Evaluate Each Option
A. A web interfaceThe web interface is the primary user access point for Alliance Lite2, enabling message sending and receiving via a browser. This is a core component, as confirmed in theSwift Alliance Lite2 User Guide.Conclusion: Correct.
B. An AutoClientThe AutoClient is an optional automated client for batch processing and integration with back-office systems, considered a key component for enhanced functionality, per theSwift Alliance Lite2 Technical Documentation.Conclusion: Correct.
C. A HSM boxWhile HSMs are used for cryptographic security in Swift environments, Alliance Lite2 relies on Swift-managed HSM infrastructure, not user-managed HSM boxes. It is not a key user-side component, per theSwift Security Best Practices.Conclusion: Incorrect.
D. A WebSphere MQ ServerWebSphere MQ is a middleware solution not integral to Alliance Lite2, which uses a lightweight architecture without requiring such servers. TheSwift Alliance Lite2 User Guidedoes not list it as a component.Conclusion: Incorrect.
Step 3: Conclusion and Verification
The correct answers areAandB, as the web interface and AutoClient are the key user-side components of Alliance Lite2, consistent with theSwift Alliance Lite2 User GuideandCSCF v2024.
References
Swift Alliance Lite2 User Guide, Section: System Components.
Swift Customer Security Controls Framework (CSCF) v2024, Control 1.1: Swift Environment Protection.
Swift Alliance Lite2 Technical Documentation, Section: Architecture.
What are the possible impacts for a SWIFT user to be non-compliant to CSP? (Select the two correct answers that apply)
•Swift Customer Security Controls Policy
•Swift Customer Security Controls Framework v2025
•Independent Assessment Framework
•Independent Assessment Process for Assessors Guidelines
•Independent Assessment Framework - High-Level Test Plan Guidelines
•Outsourcing Agents - Security Requirements Baseline v2025
•CSP Architecture Type - Decision tree
•CSP_controls_matrix_and_high_test_plan_2025
•Assessment template for Mandatory controls
•Assessment template for Advisory controls
•CSCF Assessment Completion Letter
•Swift_CSP_Assessment_Report_Template
To be reported to their supervisors (if applicable)
To be seen as non-compliant to their counterparts in KYC-SA
To be contacted by SWIFT to provide the CSP assessment report and detailed information about the reason of non-compliance
To be delisted from the BIC directory
The "Swift Customer Security Controls Policy" and "Independent Assessment Framework" outline the consequences of non-compliance with the CSP. Let’s evaluate each option:
•Option A: To be reported to their supervisors (if applicable)
This does not apply. Non-compliance is managed by SWIFT, not internal reporting to supervisors, unless specified by the user’s internal governance (not a CSP requirement).
•Option B: To be seen as non-compliant to their counterparts in KYC-SA
This applies. Non-compliance is reflected in the KYC-SA portal, where counterparties can view the user’s status, impacting trust and business relationships, as per the "Independent Assessment Framework."
•Option C: To be contacted by SWIFT to provide the CSP assessment report and detailed information about the reason of non-compliance
This applies. SWIFT engages with non-compliant users, requesting assessment reports and remediation plans, as outlined in the "Swift_CSP_Assessment_Report_Template" and "Independent Assessment Process for Assessors Guidelines."
•Option D: To be delisted from the BIC directory
This does not apply. Delisting is an extreme measure not automatically triggered by non-compliance; it requires persistent failure to remediate after engagement, which is not guaranteed.
Summary of Correct Answers:
Possible impacts include being seen as non-compliant in KYC-SA (B) and being contacted by SWIFT for reports (C).
References to SWIFT Customer Security Programme Documents:
•Independent Assessment Framework: Details non-compliance impacts.
•Swift_CSP_Assessment_Report_Template: Supports SWIFT follow-up.
•CSP_controls_matrix_and_high_test_plan_2025: Reflects KYC-SA visibility.
========
Where is the implementation of multi-factor authentication deemed sufficient to support control 4.2 compliance? (Choose all that apply.)

When accessing an outsourcing agent or an L2BA Swift-related application
When logging-in on an interface, a connector, or the system running such component
When login on the jump server filtering access to local Swift secure zone
On the General Operator PC used to access a Swift-related component
Control 4.2 of the Swift Customer Security Controls Framework (CSCF) mandates the implementation of Multi-Factor Authentication (MFA) to "prevent compromise of a single authentication factor allowing access to SWIFT systems." The control applies to various access points within the SWIFT environment to ensure robust security. Let’s evaluate each option against CSCF v2024 and related guidelines:
A. When accessing an outsourcing agent or an L2BA Swift-related application
CSCF v2024 Control 4.2 explicitly states that MFA is required for "SWIFT-related applications or components managed by third-party service providers" (e.g., outsourcing agents) and Level 2 Business Applications (L2BA). This ensures that external entitieshandling SWIFT-related processes adhere to the same security standards. The scope includes any operator access to these applications, making MFA mandatory here.
Select the correct statement(s).

The public and private keys of a Swift certificate are stored on the Hardware Security Module
The certificate stored on the Swift Hardware Security Module is used during the decryption operation of a message
The decryption operation uses the encryption private key of the receiver
To verify the signature the SwiftNetLink uses the signing private key of the receiver
This question involves the role of the Hardware Security Module (HSM) and cryptographic operations in the Swift environment. Let’s evaluate each option.
Step 1: Understand HSM and Cryptographic Operations in Swift
The HSM is a secure device used to manage cryptographic keys and perform encryption/decryption operations, as detailed inControl 2.5B: Cryptographic Key Managementof theCSCF v2024. Swift uses public key infrastructure (PKI) for secure messaging, with HSMs storing keys and certificates.
Step 2: Evaluate Each Option
A. The public and private keys of a Swift certificate are stored on the Hardware Security ModuleIn the Swift environment, the HSM stores both the private key (for signing/decryption) and the public key (for verification/encryption) as part of the certificate pair. This is a standard practice for secure key management, as confirmed in theSwift Security Best PracticesandControl 2.5B, which mandates secure storage of cryptographic keys in HSMs.Conclusion: This statement is correct.
B. The certificate stored on the Swift Hardware Security Module is used during the decryption operation of a messageThe HSM uses the private key stored in the certificate to perform decryption of incoming Swift messages. This is part of the secure message handling process, as outlined inControl 2.5Band theSwift Alliance Gateway Technical Documentation.Conclusion: This statement is correct.
C. The decryption operation uses the encryption private key of the receiverDecryption uses theprivate keyof the receiver, not the “encryption private key” (a misnomer). The correct term is the receiver’s private key, which corresponds to the public key used for encryption. This error makes the statement technically incorrect, despite the intended meaning.Conclusion: This statement is incorrect.
D. To verify the signature the SwiftNetLink uses the signing private key of the receiverSignature verification requires the sender’s public key, not the receiver’s private key. The SwiftNetLink (SNL) uses the public key to verify the signature, as perControl 2.5BandSwift Security Best Practices. The private key is used for signing, not verification.Conclusion: This statement is incorrect.
Step 3: Conclusion and Verification
The verified statements areAandB, as they accurately describe the HSM’s role in key storage and decryption, consistent with Swift CSP documentation.
References
Swift Customer Security Controls Framework (CSCF) v2024, Control 2.5B: Cryptographic Key Management.
Swift Security Best Practices, Section: HSM Usage.
Swift Alliance Gateway Technical Documentation, Section: Cryptographic Operations.
What are the conditions required to permit reliance on the compliance conclusion of a control assessed in the previous year? (Choose all that apply.)

The control compliance conclusion must have already been relied on the past two years
The previous assessment was performed on the (correct) CSCF version of the previous year
The control definition has not changed
The control-design and implementation are the same
This question outlines conditions for relying on a previous year’s control assessment under theCSCF v2024.
Step 1: Understand Reliance on Previous Assessments
TheIndependent Assessment Frameworkallows reliance on prior assessments to reduce redundancy, provided specific conditions are met, as detailed in theCSCF v2024andSwift CSP Compliance Guidelines.
Step 2: Evaluate Each Option
A. The control compliance conclusion must have already been relied on the past two yearsThere is no requirement in theCSCF v2024orIndependent Assessment Frameworkthat reliance must have occurred for two prior years. Reliance is assessed annually based on current conditions.Conclusion: Incorrect.
B. The previous assessment was performed on the (correct) CSCF version of the previous yearThe assessment must align with the CSCF version active at the time, ensuring relevance. This is a condition in theIndependent Assessment Framework.Conclusion: Correct.
C. The control definition has not changedIf the control definition in theCSCF v2024has not been updated, prior conclusions remain valid, per theSwift CSP FAQ.Conclusion: Correct.
D. The control-design and implementation are the sameContinuity in design and implementation is required to ensure the control’s effectiveness has not changed, as specified in theIndependent Assessment Framework.Conclusion: Correct.
Step 3: Conclusion and Verification
The correct answers areB, C, and D, as these conditions ensure the prior assessment’s relevance and accuracy under theCSCF v2024.
References
Swift Customer Security Controls Framework (CSCF) v2024, Section: Assessment Reliance.
Swift Independent Assessment Framework, Section: Reliance Conditions.
Swift CSP FAQ, Section: Assessment Continuity.
What are the three main objectives of the Customer Security Controls Framework? (Select the correct answer)
•Swift Customer Security Controls Policy
•Swift Customer Security Controls Framework v2025
•Independent Assessment Framework
•Independent Assessment Process for Assessors Guidelines
•Independent Assessment Framework - High-Level Test Plan Guidelines
•Outsourcing Agents - Security Requirements Baseline v2025
•CSP Architecture Type - Decision tree
•CSP_controls_matrix_and_high_test_plan_2025
•Assessment template for Mandatory controls
•Assessment template for Advisory controls
1. Secure your environment
2. Know and Limit Access
3. Detect and Respond
1. Restrict Internet Access and Protect Critical Systems from General IT Environment
2. Reduce Attack Surface and Vulnerabilities
3. Physically Secure the Environment
1. Secure and Protect
2. Prevent and Detect
3. Share and Prepare
1. Raise pragmatically the security bar
2. Maintain appropriate cyber-security hygiene
3. React promptly
The Customer Security Controls Framework (CSCF), part of the SWIFT Customer Security Programme, aims to enhance the security of the SWIFT ecosystem by defining mandatory and advisory security controls for users. The three main objectives are explicitly outlined in the CSCF documentation and reflect a holistic approach to security. Let’s evaluate each option:
•Option A: 1. Secure your environment, 2. Know and Limit Access, 3. Detect and Respond
This is correct. These three objectives align directly with the core principles of the CSCF:
oSecure your environment: This involves implementing controls to protect the SWIFT-related infrastructure (e.g., CSCF Control 1.1 SWIFT Environment Protection, 1.2 Physical Security) against unauthorized access and threats.
oKnow and Limit Access: This focuses on managing access controls and authentication (e.g., CSCF Control 2.2 External Transmission Security, 6.1 Security Awareness) to ensure only authorized personnel can interact with the SWIFT environment.
oDetect and Respond: This emphasizes monitoring and incident response (e.g., CSCF Control 4.1 Logging and 5.1 Operational Incident Response) to identify and mitigate security incidents. These objectives are explicitly stated in the "Swift Customer Security Controls Framework v2025" and reinforced across related documents like the "CSP_controls_matrix_and_high_test_plan_2025."
•Option B: 1. Restrict Internet Access and Protect Critical Systems from General IT Environment, 2. Reduce Attack Surface and Vulnerabilities, 3. Physically Secure the Environment
This is incorrect. While these are specific controls within the CSCF (e.g., Control 1.1, 2.3 System Hardening, 1.2), they are not the overarching objectives. They are implementation details rather than the high-level goals of the framework.
•Option C: 1. Secure and Protect, 2. Prevent and Detect, 3. Share and Prepare
This is incorrect. These terms are vague and do not match the official CSCF objectives. "Share and Prepare" is not a recognized objective, and the phrasing does not align with SWIFT documentation.
•Option D: 1. Raise pragmatically the security bar, 2. Maintain appropriate cyber-security hygiene, 3. React promptly
This is incorrect. While these concepts are related to security improvement, they are not the specific objectives outlined in the CSCF. The language is more general and lacks the structured focus of the official objectives.
Summary of Correct Answer:
The three main objectives of the CSCF are to Secure your environment, Know and Limit Access, and Detect and Respond (A), as defined in the framework’s core principles.
References to SWIFT Customer Security Programme Documents:
•Swift Customer Security Controls Framework v2025: Outlines the three main objectives (Secure, Know and Limit, Detect and Respond).
•CSP_controls_matrix_and_high_test_plan_2025: Aligns controls with these objectives.
•Independent Assessment Framework: Supports the assessment of these objectives.
========
Who can connect to SWIFT? (Select all answers that apply)
•Connectivity
•Generic
•Products Cloud
•Products OnPrem
•Security
Financial institutions, such as banks and securities broker-dealers
Individuals who use online banking for international transfers
Market infrastructures that provide financial institutions with centralized transaction processing
Corporates that work with multiple banking partners
SWIFT (Society for Worldwide Interbank Financial Telecommunication) is a global cooperative that provides a secure messaging network primarily for financial transactions. Its services are designed for entities involved in the financial ecosystem, and access is restricted to members or participants who meet SWIFT’s membership criteria. Let’s evaluate each option:
•Option A: Financial institutions, such as banks and securities broker-dealers
This is correct. SWIFT’s core users are financial institutions, including banks, broker-dealers, and other entities regulated under financial authorities. These institutions are direct members of SWIFT or connect through correspondent banking relationships. The SWIFT Customer Security Programme (CSP) and CSCF are tailored to secure the messaging environment for these entities, with controls like "1.1 SWIFT Environment Protection" designed to safeguard their operations. Membership requires adherence to SWIFT’s security standards, and these institutions use SWIFTNet for payments, securities, trade, and treasury services.
•Option B: Individuals who use online banking for international transfers
This is incorrect. Individuals, including those using online banking for international transfers, do not connect directly to SWIFT. Instead, they rely on their banks or financial service providers, which act as intermediaries using SWIFT’s network. SWIFT is a business-to-business (B2B) network, not a consumer-facing platform. The CSCF does not address individual users; its focus is on institutional security controls, such as those protecting the SWIFT secure zone.
•Option C: Market infrastructures that provide financial institutions with centralized transaction processing
This is correct. Market infrastructures, such as clearinghouses, central securities depositories (CSDs), and payment systems (e.g., TARGET2 or CHAPS), are eligible to connect to SWIFT. These entities facilitate centralized transaction processing for financial institutions and are part of the broader financial ecosystem. SWIFT documentation recognizes their role, and they are subject to the same security requirements under the CSP. For example, CSCF Control "1.2 Physical Security" applies to these infrastructures when they host SWIFT-related components.
•Option D: Corporates that work with multiple banking partners
This is correct. Corporates, especially large multinational corporations with complex financial operations, can connect to SWIFT through SWIFT’s corporate connectivity options, such as Alliance Lite2 or SWIFT for Corporates. These services allow corporates to send and receive payment instructions directly via SWIFTNet, bypassing some intermediary steps with banks. This capability is outlined in SWIFT’s corporate access documentation, and such entities must comply with CSP security controls when integrating with the SWIFT network. The CSCF extends to these participants, ensuring their environments are secure (e.g., Control "6.1 Security Awareness").
Summary of Correct Answers:
Financial institutions (A), market infrastructures (C), and corporates with multiple banking partners (D) can connect to SWIFT, either as direct members or through specific connectivity options. Individuals (B) do not have direct access.
References to SWIFT Customer Security Programme Documents:
•SWIFT Customer Security Controls Framework (CSCF) v2024: Applies to all SWIFT users, including financial institutions, market infrastructures, and corporates, with security controls tailored to their environments (Controls 1.1, 6.1).
•SWIFT Membership Guidelines: Outlines eligibility for financial institutions, market infrastructures, and corporates, excluding individuals.
•SWIFT for Corporates Documentation: Details corporate connectivity options like Alliance Lite2.
Select the correct statement about SWIFT Alliance Cloud.
•Connectivity
•Generic
•Products Cloud
•Products OnPrem
•Security
Alliance Cloud is a SWIFT cloud-based solution. It provides a universal channel to the financial community and to SWIFT Value Added services and initiatives
Alliance Cloud is a cloud-based solution. It is offered by the 3 official public cloud providers. This allows customers the choice to select their preferred cloud provider
Alliance Cloud is a cloud-based solution. It is offered by any public cloud provider that subscribed to the digital connectivity initiative
Alliance Cloud is a SWIFT cloud-based solution. It consists of an Alliance Access instance deployed at one of the three SWIFT-approved public cloud providers
SWIFT Alliance Cloud is a managed cloud service provided by SWIFT to deliver a fully hosted SWIFT infrastructure, reducing the local footprint for users. Let’s evaluate each option:
•Option A: Alliance Cloud is a SWIFT cloud-based solution. It provides a universal channel to the financial community and to SWIFT Value Added services and initiatives
This is partially correct but incomplete. Alliance Cloud is indeed a SWIFT-managed cloud solution, and it facilitates connectivity to the financial community and SWIFT Value Added Services (e.g., SWIFT gpi, Sanctions Screening). However, the term "universal channel" is vague and not a precise description of Alliance Cloud’s functionality, which is more accurately defined as a hosted messaging and connectivity platform. This option lacks specificity about the deployment model.
•Option B: Alliance Cloud is a cloud-based solution. It is offered by the 3 official public cloud providers. This allows customers the choice to select their preferred cloud provider
This is incorrect. Alliance Cloud is a SWIFT-managed service deployed on specific public cloud providers approved by SWIFT, not a solution where customers can choose any of the "3 official public cloud providers." SWIFT partners with select providers (e.g., AWS, Microsoft Azure, Google Cloud) but controls the deployment and configuration, limiting customer choice to SWIFT-approved instances.
•Option C: Alliance Cloud is a cloud-based solution. It is offered by any public cloud provider that subscribed to the digital connectivity initiative
This is incorrect. Alliance Cloud is not available on any public cloud provider that subscribes to a "digital connectivity initiative." It is hosted exclusively on SWIFT-approved public cloud providers, ensuring compliance with SWIFT’s security and operational standards. The term "digital connectivity initiative" is not a recognized framework in SWIFT documentation for Alliance Cloud.
•Option D: Alliance Cloud is a SWIFT cloud-based solution. It consists of an Alliance Access instance deployed at one of the three SWIFT-approved public cloud providers
This is correct. Alliance Cloud is a SWIFT-managed cloud solution that includes a hosted Alliance Access instance (a messaging interface) deployed on one of the three SWIFT-approved public cloud providers (e.g., AWS, Microsoft Azure, Google Cloud). This setup provides a fully managed environment for SWIFT connectivity, reducing the user’s local infrastructure needs. The CSCF applies to this cloud deployment, with SWIFT managing many security controls (e.g., "1.1 SWIFT Environment Protection"). SWIFT documentation confirms this model, emphasizing the use of approved providers.
Summary of Correct Answer:
The correct statement is D, accurately describing Alliance Cloud as a SWIFT-managed solution with an Alliance Access instance on SWIFT-approved public cloud providers.
References to SWIFT Customer Security Programme Documents:
•SWIFT Customer Security Controls Framework (CSCF) v2024: Supports cloud deployments on approved providers (Control 1.1).
•SWIFT Alliance Cloud Documentation: Details the deployment on SWIFT-approved public cloud providers with Alliance Access.
•SWIFT Cloud Partnership Guidelines: Lists approved providers like AWS, Azure, and Google Cloud.
========
