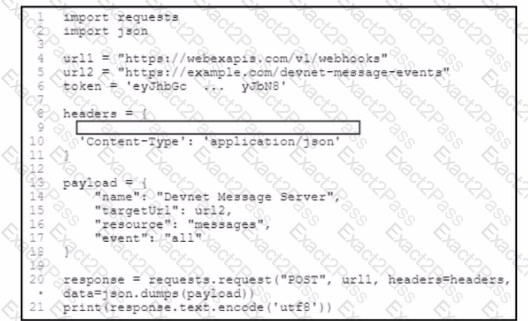
Refer to the exhibit. A developer needs to create a webhook to send all Cisco Webex messages to a third-party tool by using the Cisco Webex API. The developer must Auhenticate with the API before any API calls can be made. To automate the procedure, a Python script is used. Which code snippet must be placed onto the blank in the code?
A)

B)

C)

D)


Refer to the exhibit. A network engineer must configure new interfaces on a set of devices and is planning to use an Ansible playbook for the task. All devices support SSH and NETCONF protocol, and the interface variables are unique per device. In which directory are the YAML files including variables hosted to automate the task with the netconf_config module?
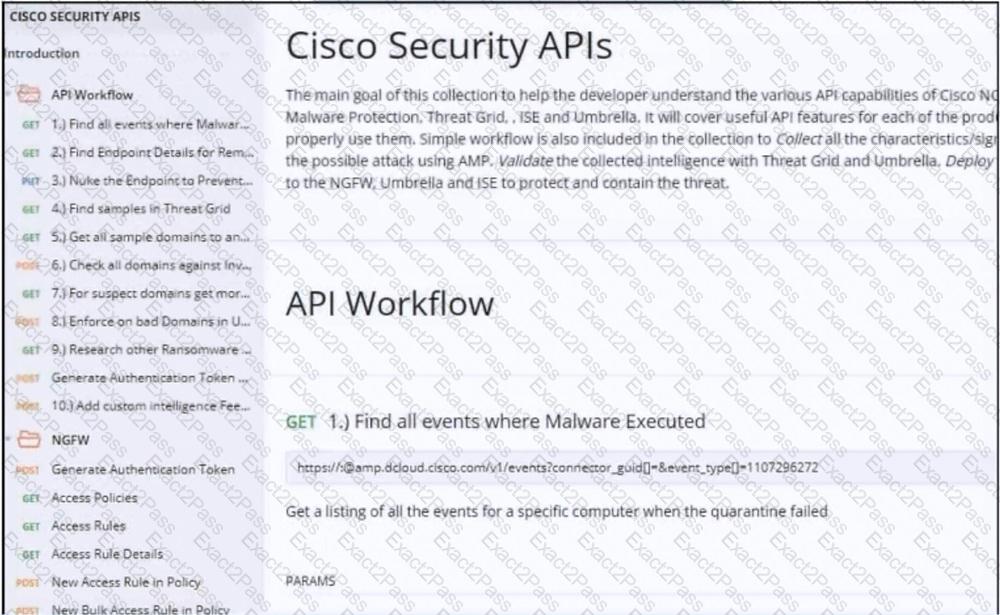
Refer to the exhibit.
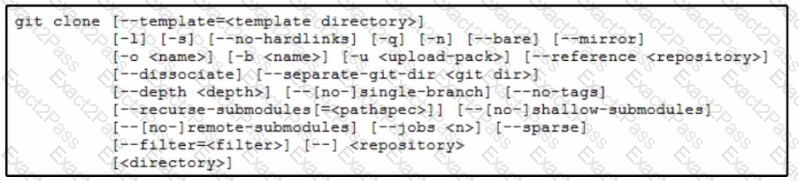
A network engineer must improve the fabric discovery process in a data center. The engineer wants to check current ACI scripts in the myproject repository and clone them to a folder named aci. The engineer will optimize the scripts from the new folder. Which command performs this task on the Git repository?
A)

B)

C)

D)

Which type of OWASP threat forges a malicious HTTP request into an application?
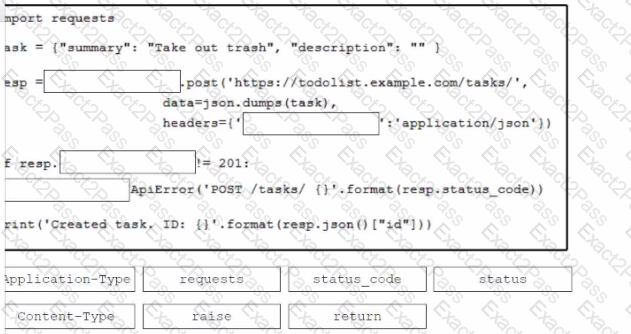
Drag and drop the code from the bottom onto the box where the code is missing to construct a Python script that calls a REST API request. Not all options are used.
What is a capability of model-driven programmability for infrastructure automation?
A company requires a new platform to store large volumes of log data that is generated in their assembly plant. The platform must be scalable, so the underlying technology must provide a path for fast deployment of new nodes for data and indexing? The data contains sensitive information, so specialist encryption tools must be used to secure the data. Which application deployment model meets the requirements?
Drag and drop the API characteristics from the left onto the categories on the right.

A developer creates an application that must provide an encrypted connection or API keys. The keys will be used to communicate with a REST API. Which command must be used for the secure connection?
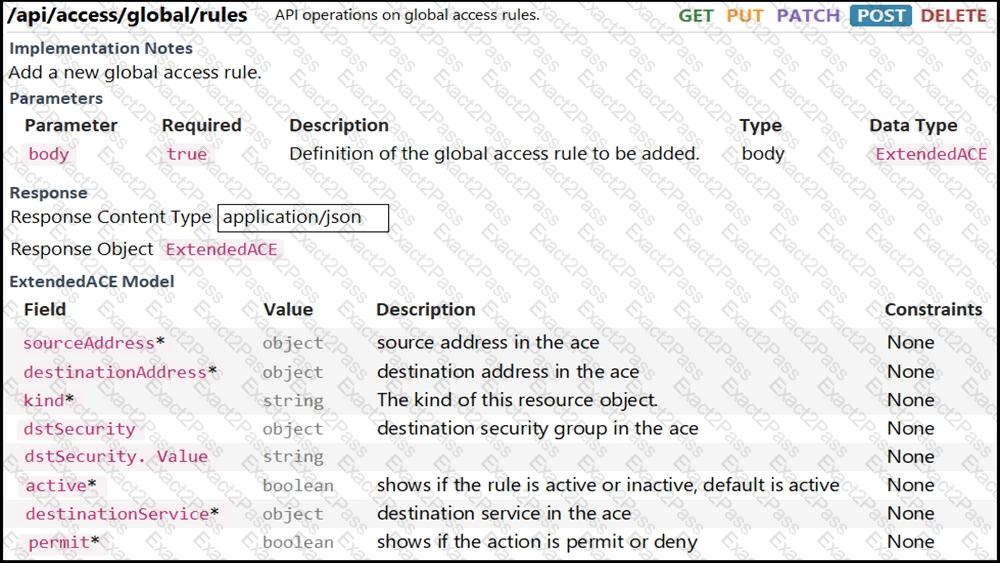
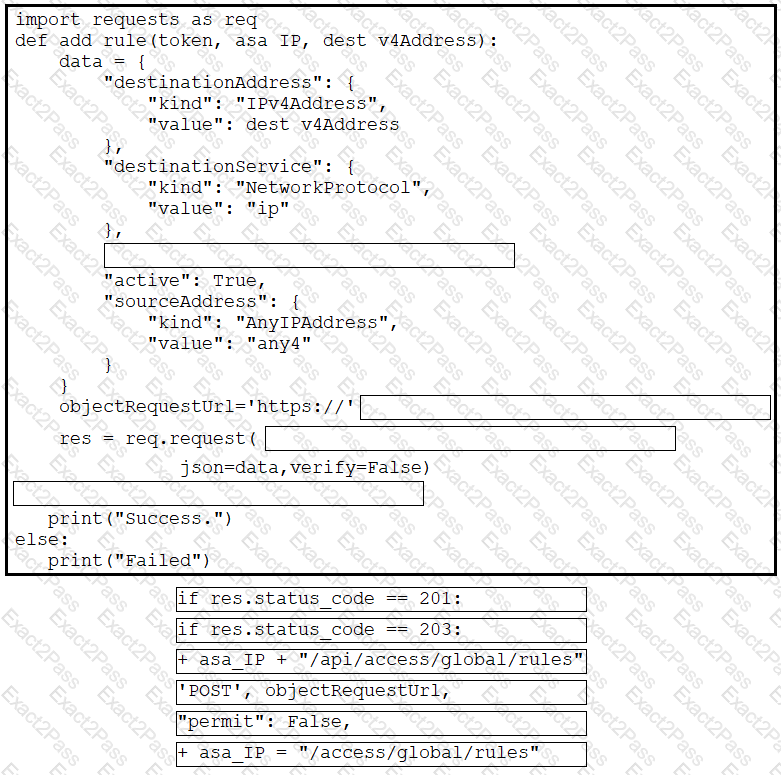
Refer to the exhibit. Drag and drop the code from the bottom onto the box where the code is missing to complete the function that adds a new global access rule that denies traffic using the Cisco ASA REST API. Not all options are used.
A network engineer makes several API calls lo Cisco Prime to retrieve a list of all devices. Each time a response is received, only a subset of the devices is returned. The engineer :ices that HTTP code 429 is returned instead of 200 for some API calls. Why did the response exclude some of the devices?
A file in a local Git repository has been updated and issued the git add . command. The git diff command has been run to compare the changes to the previous commit, but nothing shows. Which action identifies the problem?
Which IP service is responsible for automatically assigning an IP address to a device?
Which Cisco platform is used to manage data center infrastructure through third-party tools and system integrations?
A developer creates a program in which an object maintains a list of classes based on the observer pattern. The classes are dependent on the object. Whenever the state of the object changes, it notifies the dependent classes directly through callbacks. Which advantage of the observer pattern offers minimum dependencies and maximum flexibility between dependent objects or classes?
A development team is creating an application used for contactless payments. The application must:
Be web-based
Capture and process the credit card information for a purchase.
Which security action must the web application use to gather and process the private customer data?
Which Python function is used to parse a string that contains JSON data into a Python dictionary?
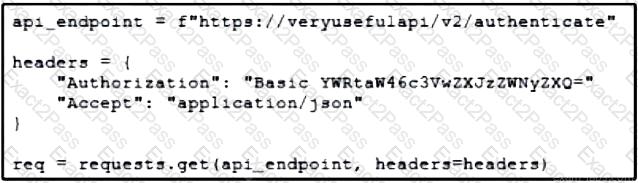
Refer to the exhibit. A developer is part of a team that is working on an open-source project in which source code is hosted in a public GitHub repository. While the application was built, security concerns were addressed by encrypting the credentials on the server. After a few months, the developer realized that a hacker managed to gain access to the account. The exhibit contains part of the source code for the login process. Why was the attacker able to access the developer's account?
A developer completed the creation of a script using Git. Before delivering it to the customer, the developer wants to be sure about all untracked files, without losing any information. Which command gathers this information?
What is an advantage of device-level management as compared to controller-level management to automate the configuration of network devices?
When a Cisco IOS XE networking device is configured by using RESTCONF, what is the default data encoding method?
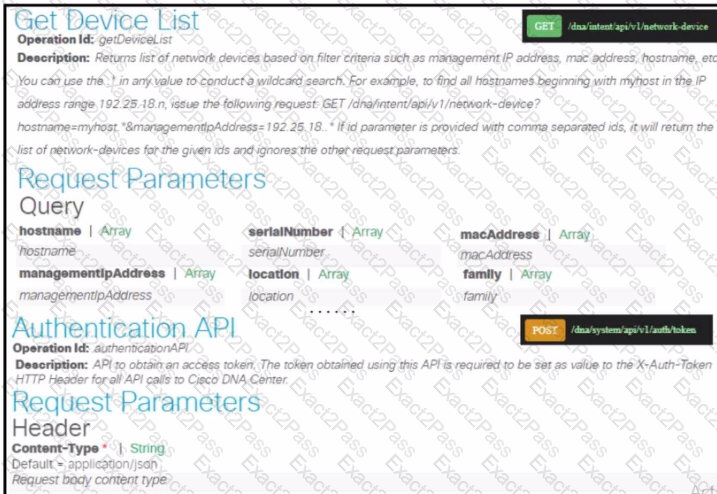
Refer to the exhibit. Drag and drop the code snippets from the bottom onto the blanks in the Python script to retrieve a list of hosts using the Cisco DNA Center API. Not all options …used.
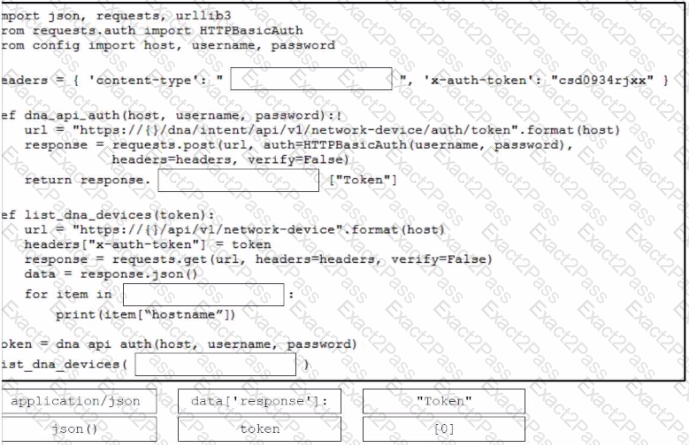
A developer plans to deploy a new application that will use an API to implement automated data collection from Webex with these requirements:
The application was created by using the request library.
Requires HTTP basic authentication.
Provides data in JSON or XML formats.
Which Cisco DevNet resource helps the developer with how to use the API?
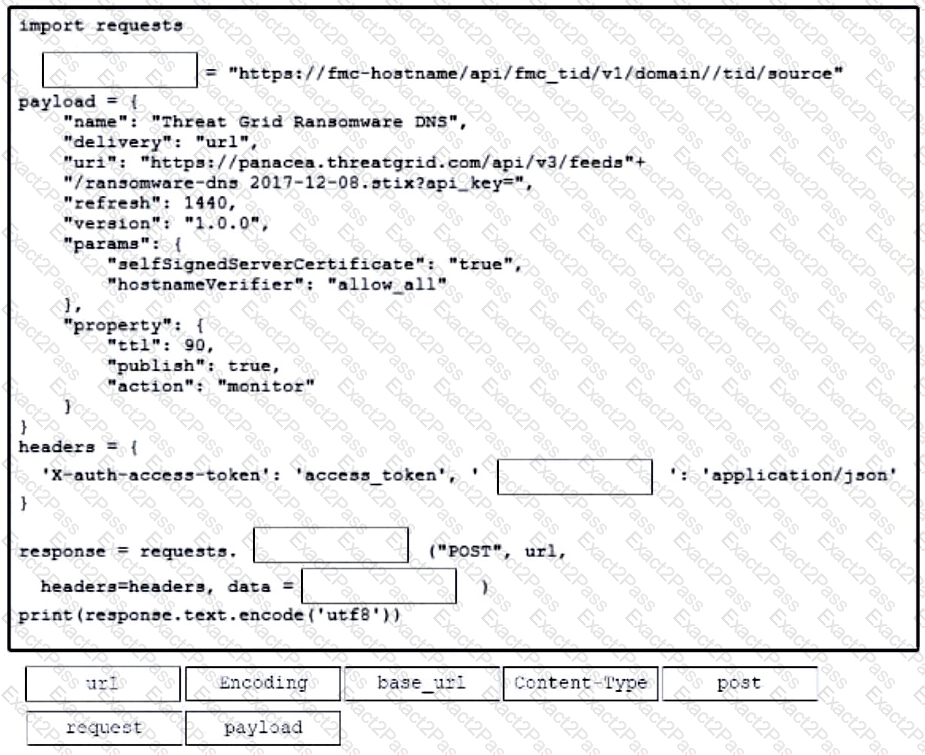
Refer to the exhibit. Drag and drop the code from the bottom onto the box where the code is missing to construct a Python script that calls a REST API request. Not all options are used.
An engineer must configure Cisco Nexus devices and wants to automate this workflow. The engineer will use an Ansible playbook to configure devices through Cisco NX REST API. Before the code is run, which resource must be used to verify that the REST API requests work as expected?
During which step of the CI/CD pipeline for infrastructure automation is code from multiple developers combined to compile and test different components?
Refer to the exhibit.
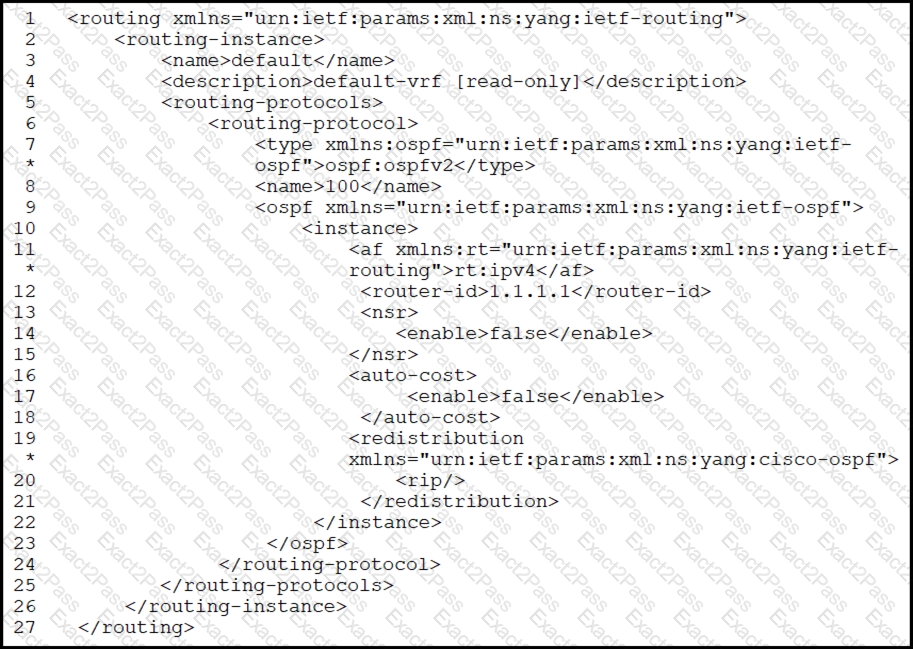
What are two characteristics of the NETCONF response? (Choose two.)
Refer to the exhibit.

A developer needs to create a Docker image that listens on port 5000. Which code snippet must be placed onto the blank in the code?
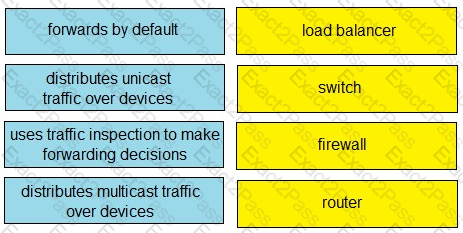
Drag and drop the functions from the left onto the networking devices on the right.
Which OWASP threat takes advantage of a web application that the user has already authenticated to execute an attack?
What is a benefit of a model-driven approach for infrastructure automation?
Refer to the exhibit.
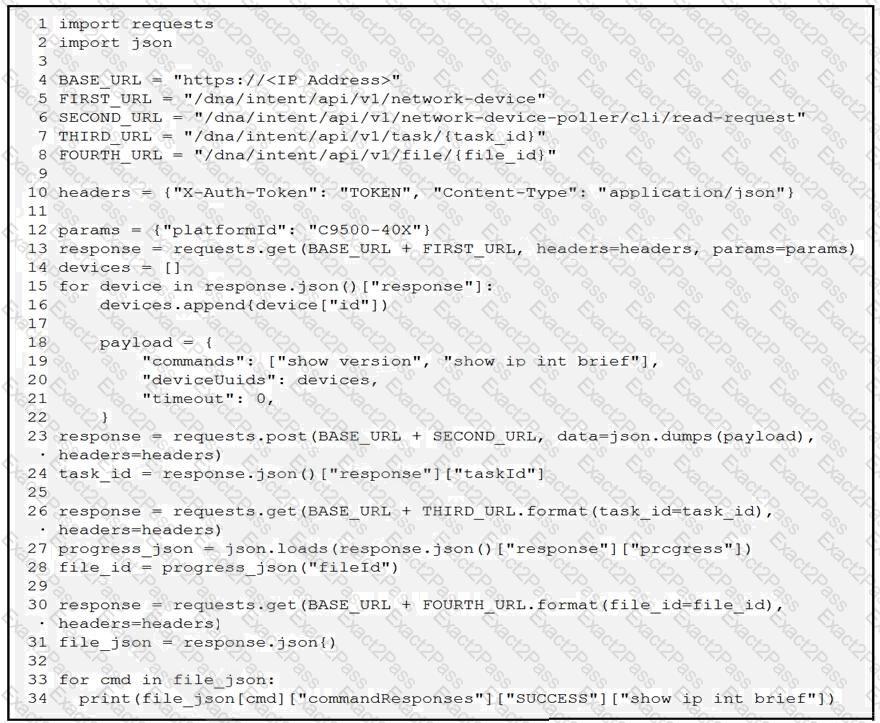
A network engineer must collect information from the network using Cisco DNA Center APIs. The script must query for the devices with 'platformId' 'C9540-x' and then send commands to be executed. Which process is automated by the Python script?
Refer to the exhibit.

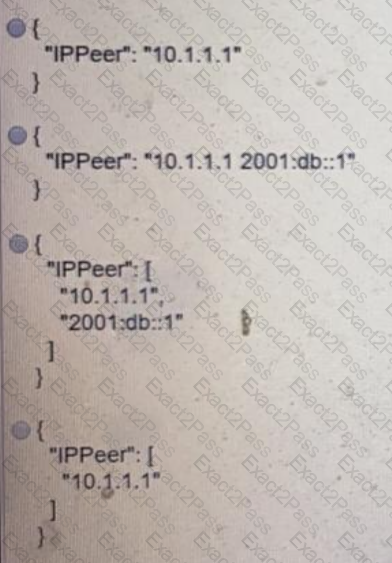
Which JSON snippet configures a new interface according to YANG model?
A)
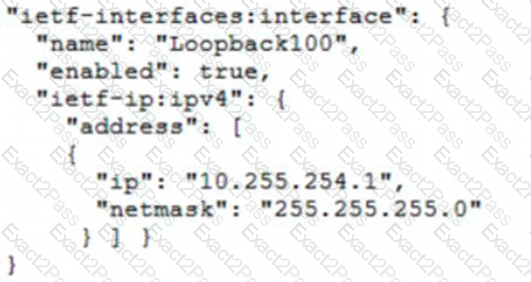
B)

C)
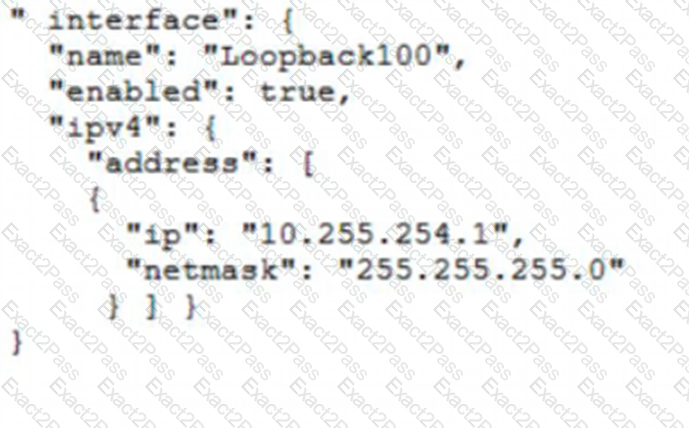
D)
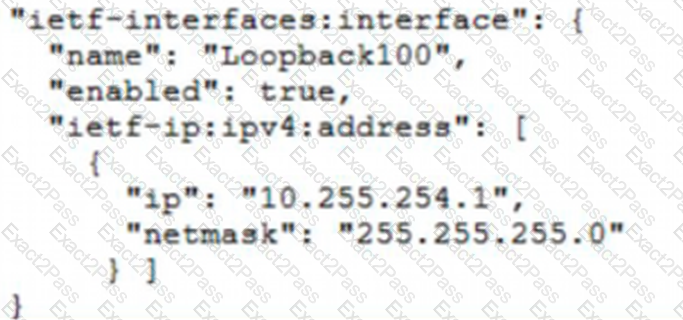
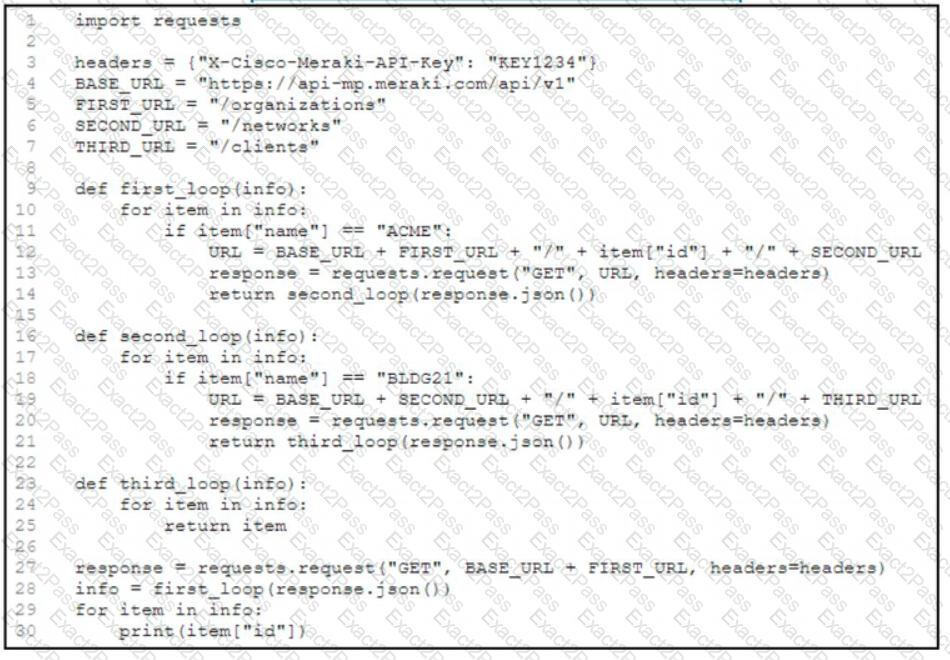
Refer to the exhibit. A network engineer must collect information from the network. The engineer prepares a script to automate workflow by using Cisco Meraki API. The script must run over nested loops to collect organization and network information and uses the collected data for final collection. Which process is being automated by using the Python script?
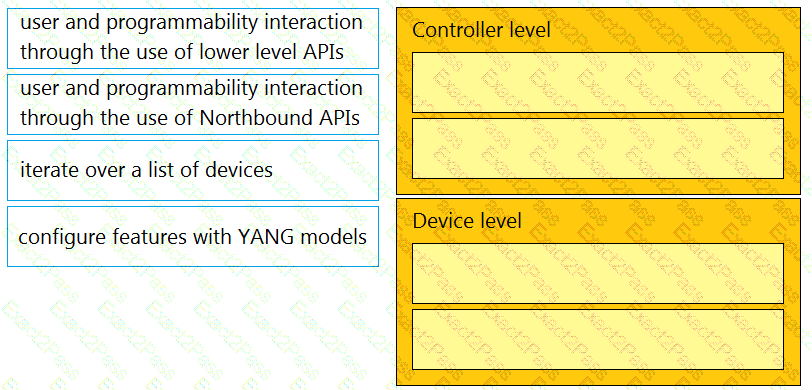
Drag and drop the types of management from the left onto the levels at which they are performed on the right.
How does a synchronous API request differ from an asynchronous API request?
Drag and drop the code snippets from the bottom into the Python script to write API output to a csv file. Not all options are used.
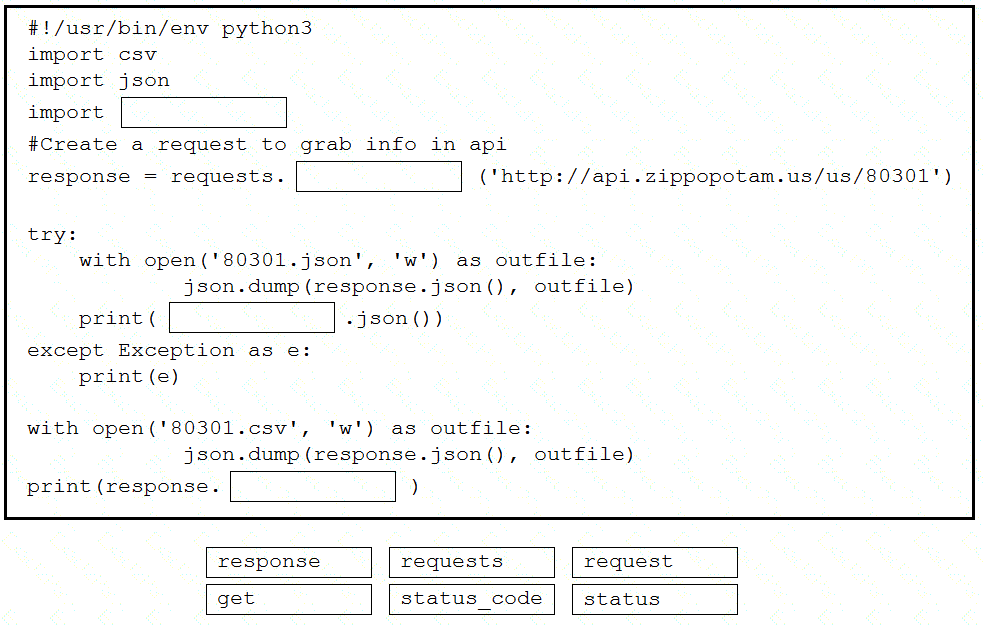
Drag and drop the code snippets from the bottom to the blanks in the code to complete the HTTP response. Not all options are used.
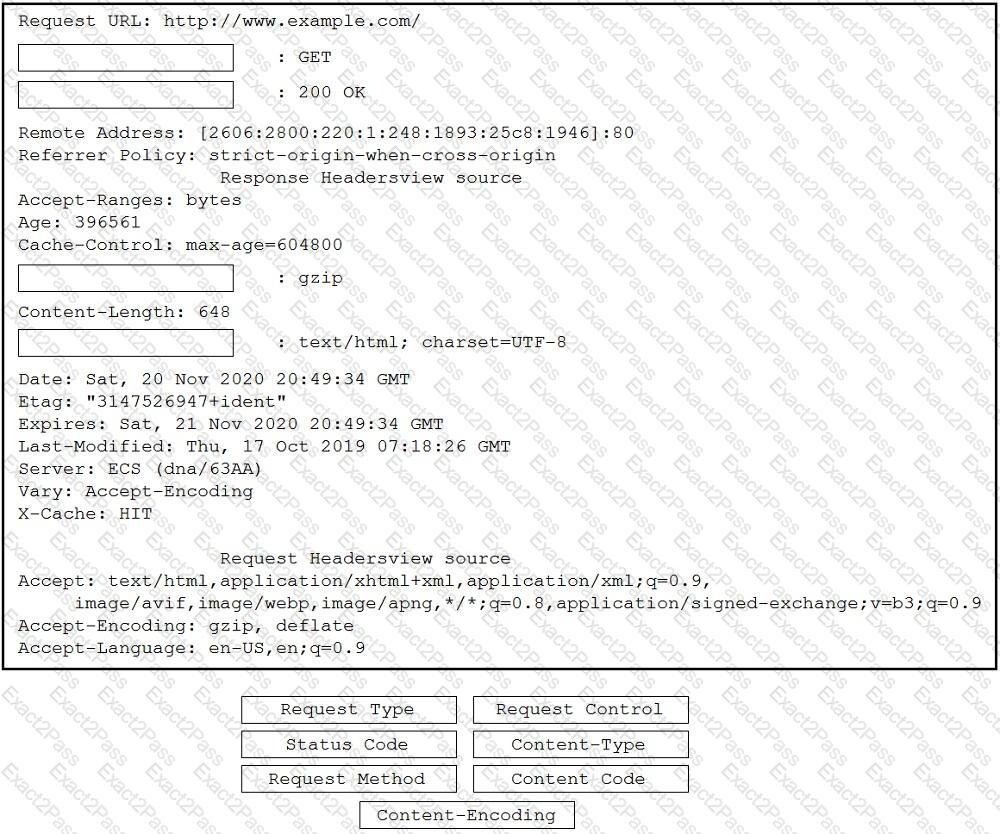
In which two ways is an application characterized when interacting with a webhook? (Choose two.)
Refer to the exhibit.
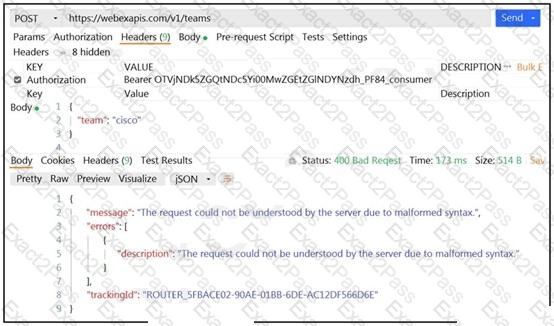
A developer wants to create a room named cisco through Webex API. The developer prepares the request by putting an API token inside the authorization header; however, the given HTTP call returns error code 400. How must the call parameters be changed to ensure a valid response?
Refer to the exhibit.
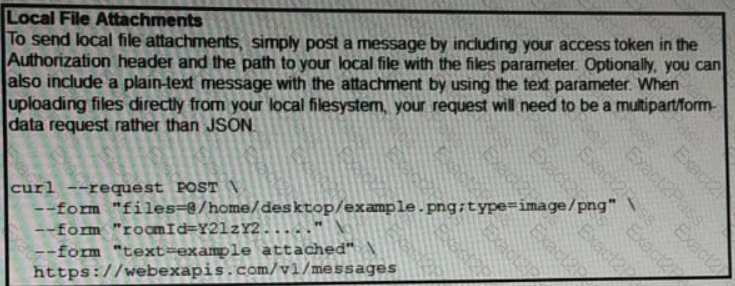
A developer needs to upload a local file by using the REST API. The developer gathers information according to the documentation and sends the request by using the cURL command in the exhibit but gets an error code. Which action should be followed to get valid response?
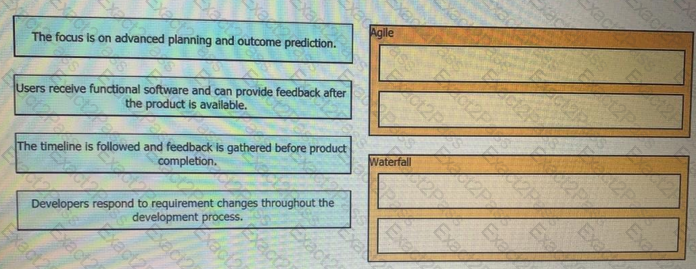
Which advantage does the agile process offer compared to waterfall software development?
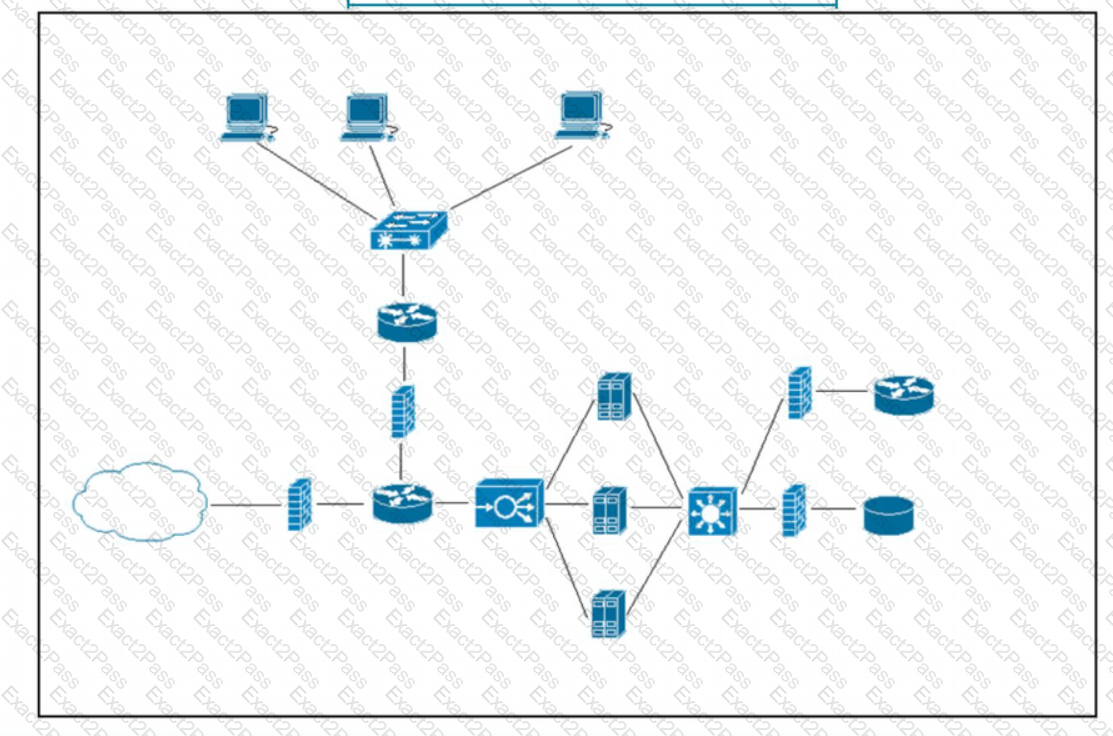
Refer to the exhibit. What does the load balancer enable in the network topology?
A developer created a new secure API and is testing the functionality locally. The API was added to a container for further testing, and other team members and applications need to connect to the API. Which command exposes the API in the container as port 8443 and allows connections external to the host?
A developer creates a web application that receives a username and password and uses them to sync the credentials to other services through HTTPS. API keys to services are part of the configuration files of the application, but the credentials to the database that stores the synchronization logs are obtained through an external vault service. What is the security issue in this scenario?
Refer to the exhibit.
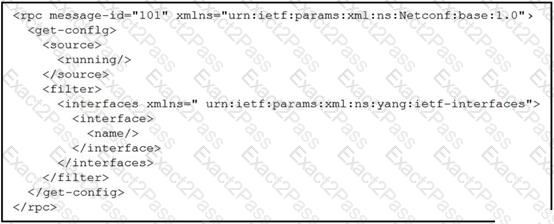
A network engineer uses model-driven programmability to monitor and perform changes on the network. The network engineer decides to use the NETCONF RPC message to complete one of their tasks. What is accomplished by sending the RPC message?
Refer to the exhibit.
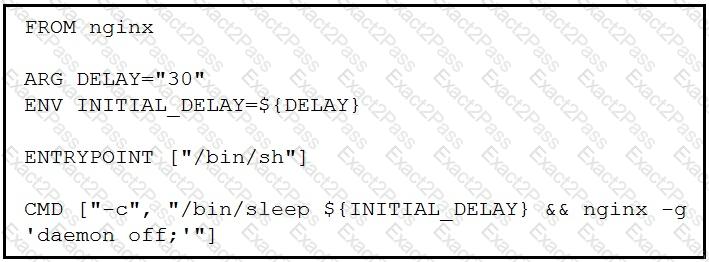
Which command, including arguments, is executed when the container starts?
An engineer must configure Cisco Nexus devices and wants to automate this workflow. The engineer enables the Cisco NX-OS REST API to configure the devices by using an Ansible playbook. Before running the code,
which resource must be used to verify that the code works correctly?
Several teams at a company are developing a new CRM solution to track customer interactions with a goal of improving customer satisfaction and driving higher revenue. The proposed solution contains these components:
• MySQL database that stores data about customers
• HTML5 and JavaScript UI that runs on Apache
• REST API written in Python
What are two advantages of applying the MVC design pattern to the development of the solution? (Choose two.)
Refer to the exhibit.
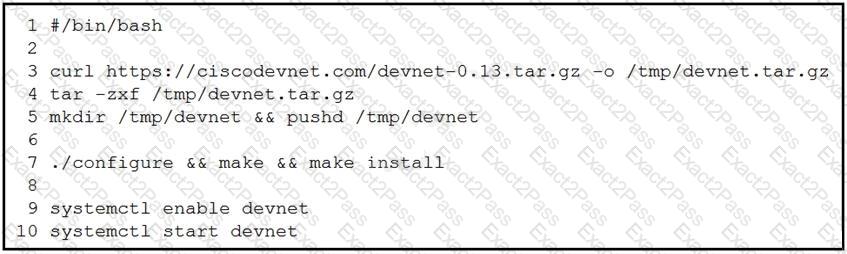
A network engineer works on a Cisco DevNet application that is available for download on the Cisco DevNet website. The engineer prepares a bash script to automate operations that relate to the application. Which workflow is being automated in the bash script?
Refer to the exhibit.
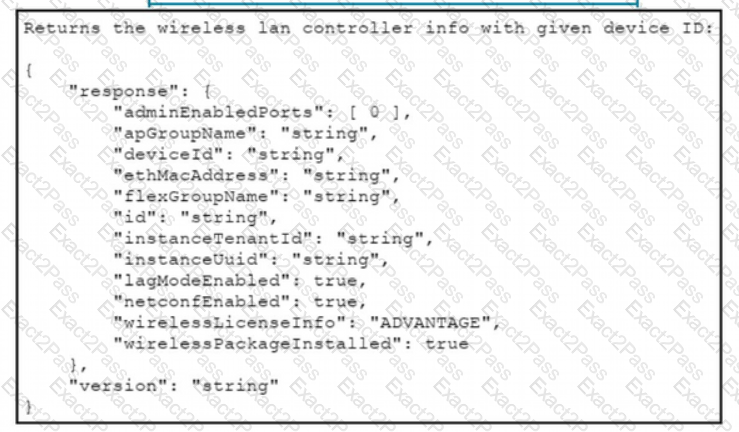
Drag and drop the code from the bottom onto the blanks in the code to construct a cURL command using the Cisco DNA Center API. which will provide the details of a WLAN controller with Id af397748444. Not at options are used.
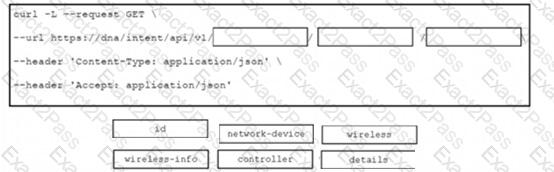
Refer to the exhibit.
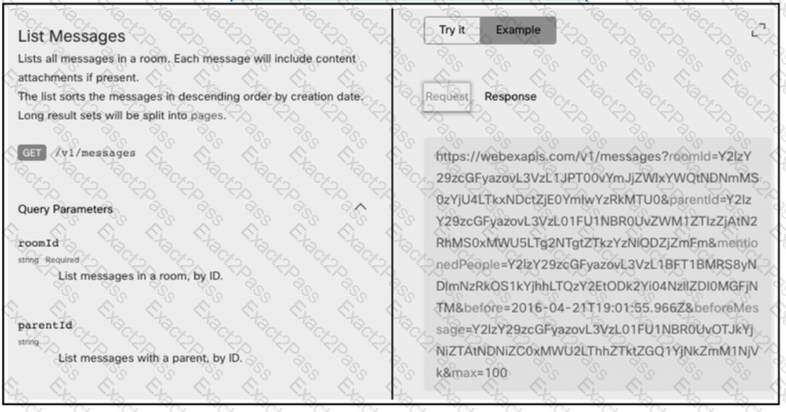
A developer needs to automatically retrieve all of the messages of a Webex room with the roomld of
HY2l2Y292cGFyazovL3Vz397748444YjU5NjAtNTk0ZJ0xMWVhLTk0Mj". Using the Webex API documentation shown, drag and drop the code snippets from below onto the code to complete the Python script to list all of the messages in the room. Not all options are used.

Where is an IP packet routed if the packet does not match any routes in the routing table?
Drag and drop the code from the bottom onto the box where the code is missing in the Python script to complete a function to return all the clients on a network by using the Cisco Meraki Dashboard API. Not all options are used.
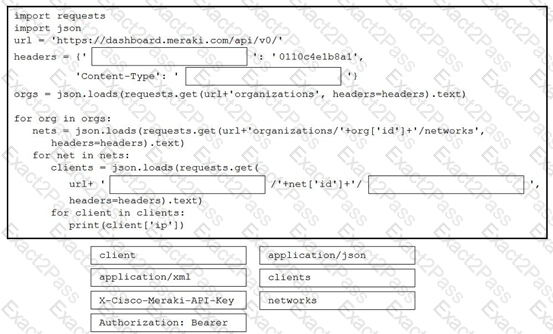
Refer to the exhibit.
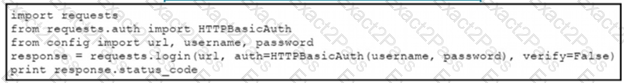
The script returns an output of 401. To use the supplied URL. an HTTP GET request must Be sent with an Authorization header. The header value is a BaseG4 encoded concatenation of the username and password. Which action must be taken to return an output of 200?
Which HTTP response code should be returned when the request is completed, but there is no content to send for the request?
A developer is working on a feature for a new application. The changes in the existing branch named 'feat00304' must be integrated into a single commit with the current working primary branch named 'prodapp411926287'. Which git command must be used?
What is a requirement when authenticating a RESTCONF API session with a router that runs Cisco IOS XE Software?
Refer to the exhibit.
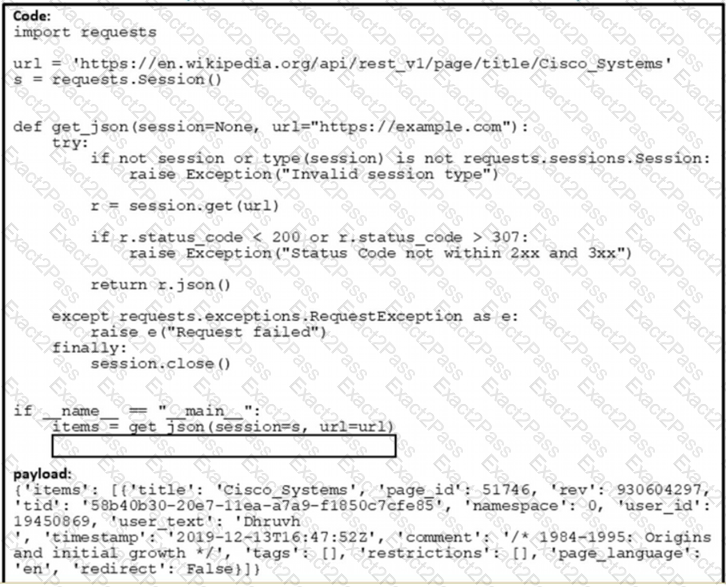
Which command needs to be placed on the box where the code is missing to output the value of page_jd in the Python 3.7 script?
A)

B)

C)

D)

Refer to the exhibit.
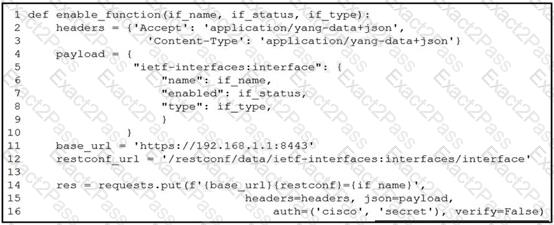
A network engineer wants to automate the port enable/disable process on specific Cisco switches. The engineer creates a script to send a request through RESTCONF and uses ietf as the YANG model and JSON as payload. Which command enables an interface named Loopback1?
Refer to the exhibit.
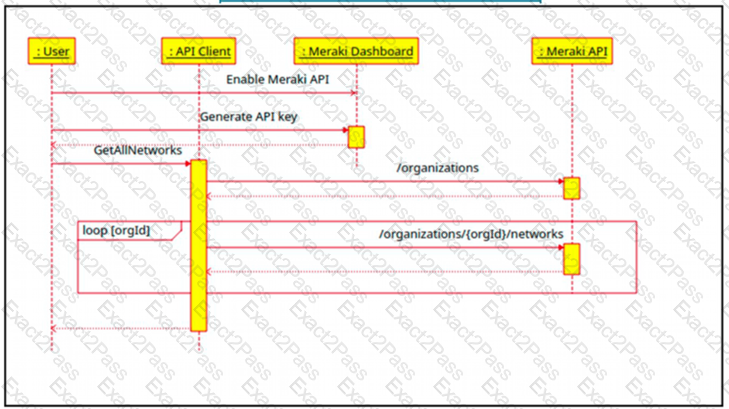
The Cisco Meraki API manages two organizations. In each organization, two independent networks are defined. How many calls to the /organizations/(orgid)networks endpoint will be run parallel by the GetAllNetwork function of the API client?
What is a benefit of using functions in the code for the development process?
Which response status code is used by a RESTful interface to indicate successful execution of a request?
Which task is performed because the test-driven development approach is being used?
Refer to Exhibit.
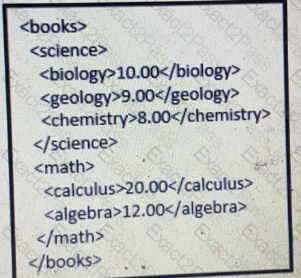
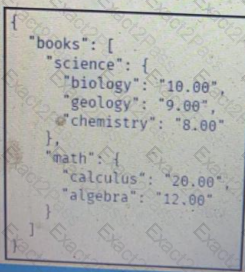
Which JSON is equivalent to the XML-encoded data.
A)

B)
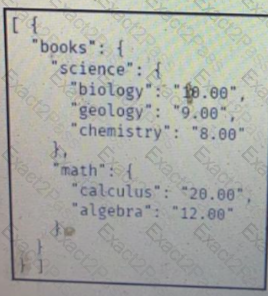
C)
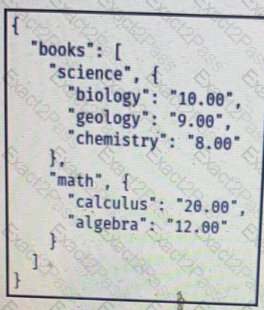
D)
Refer to the exhibit.
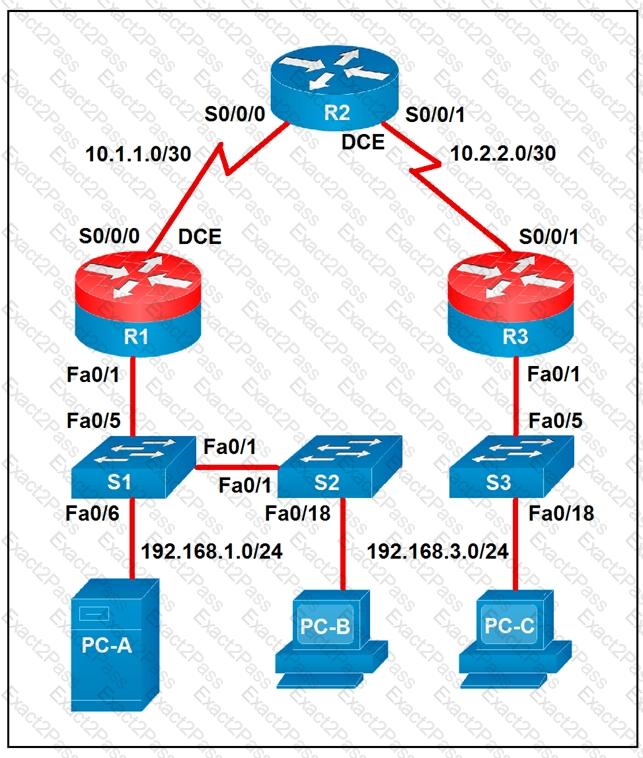
Which two statements about the network diagram are true? (Choose two.)
A developer is writing an application that a REST API and the application requires a valid from the API which element of the response is used in the conditional check?
Which statement about authentication a RESTCONF API session with a router that runs Cisco IOS XE software is true?
Drag and drop the HTTP status codes from the left onto the correct descriptions on the right.
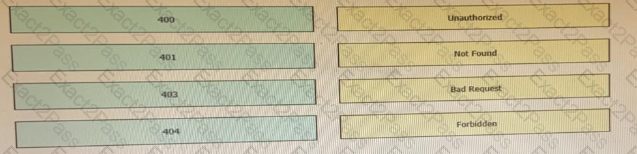
Refer to the exhibit.
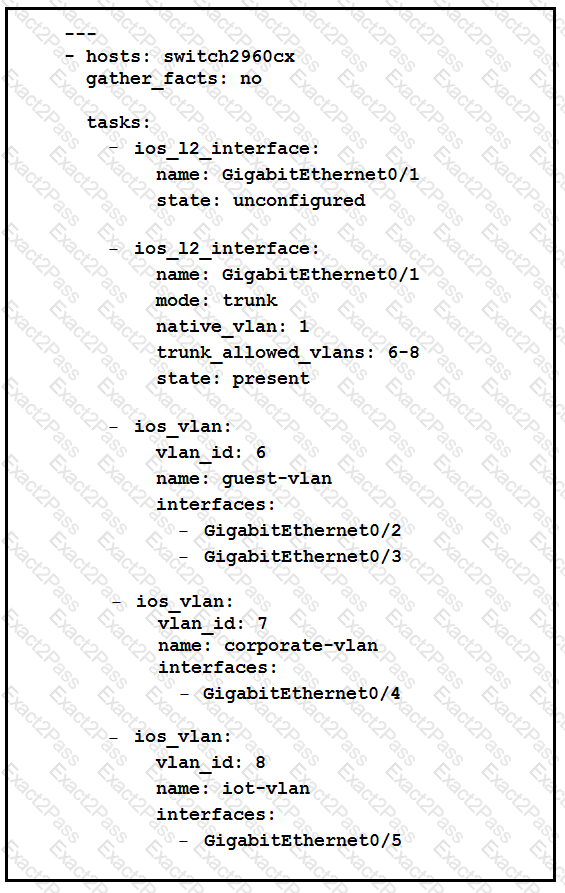
Which two statement describe the configuration of the Ansible script is run? (Choose two.)
Refer to the exhibit.
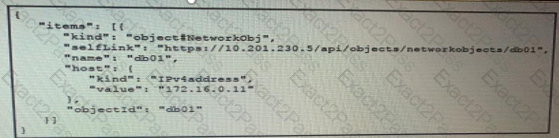
The JSON data in the exhibit has been parsed and stored in a variable, “data”. What returns the value “172.16.0.11” ?
Drag and drop the function on the left onto the type of plane that handles the function on the right.
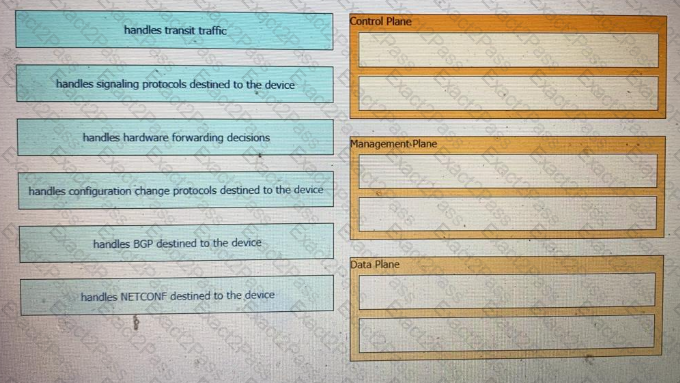
What are two benefit of managing network configuration via APIs? (Choose two.)
A developer needs to prepare the file README.md in the working tree for the next commit operation using Git. Which command needs to be used to accomplish this?
Refer to the exhibit.
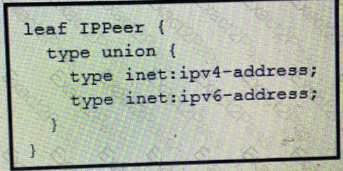
What is the value of the node defined by this YANG structure?
Which device is a system that monitors and controls incoming and outgoing network traffic based on predetermined security rules?
Refer to the exhibit.
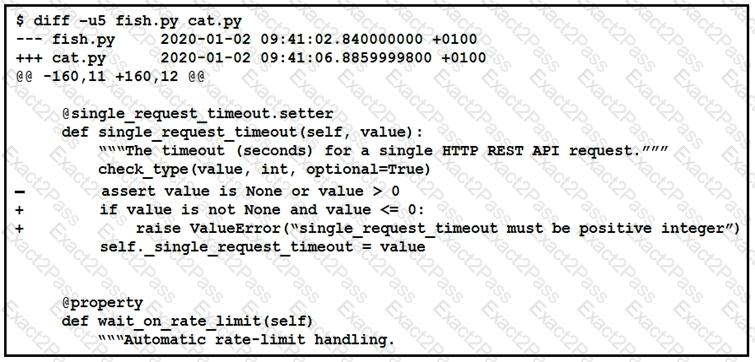
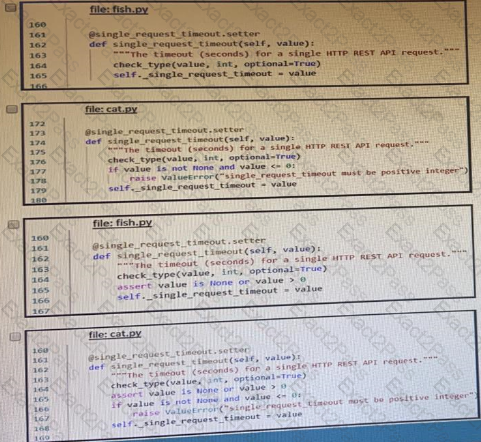
The output of a unified diff when comparing two versions of a python script is shown. Which two “single_request _timeout ()”
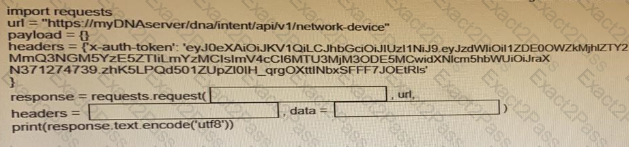
Fill in the blanks to complete the python script to retrieve a list of network devices using the Cisco DNA center API.
Which platform has an API that be used to obtain a list of vulnerable software on user devices?
Which two statements describe the advantages of using a version control system? (Choose two.)
In DNS, which record specifies an alias that refers to another name that ultimately resolves to an IP address?
How is a branch called "my-bug-fix" started to develop a fix needed in a product?
Drag and drop the network component names from the left onto the correct descriptions on the right. Not all options are used.
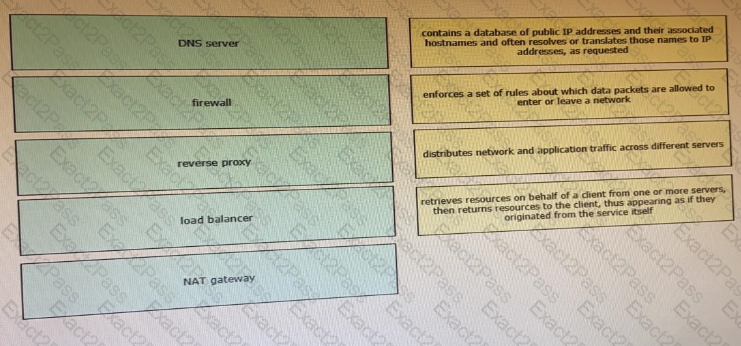
Which HTTP status Code means that the server cannot or will not process the request because of perceived client error?
Refer to the exhibit.
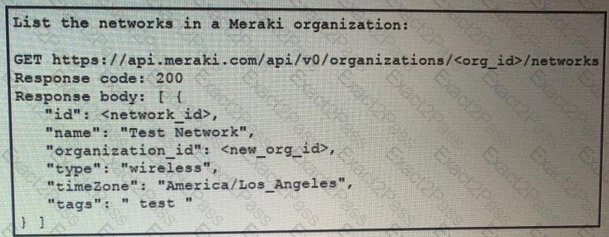
Fill in the blanks to complete the cURL command to the list of networks in the Meraki organization with an id of 384279060
Refer to the exhibit.
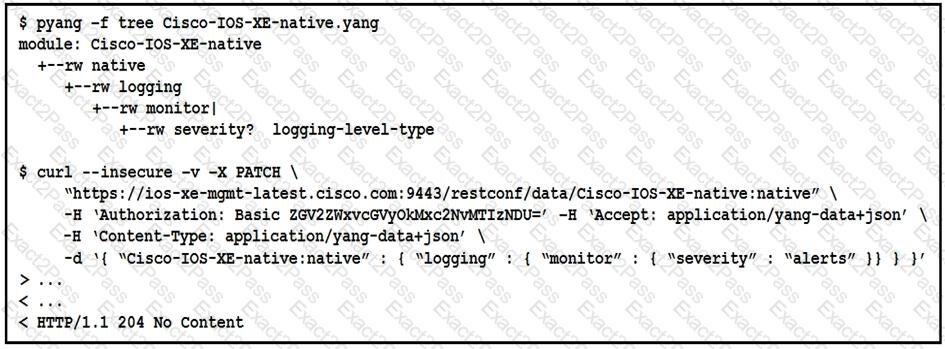
The definition of the YANG module and a RESTCONF query sent to a Cisco IOc XE device is shown. Which statement is correct if the RESTCONF interface responds with a 204 status code?
What operation is performed with YANG model-driven programmability in NX-OS?
What is used in Layer 2 switches to direct packet transmission to the intended recipient?
Drag and drop the characteristics from the left onto the corresponding software development methodologies on the right?
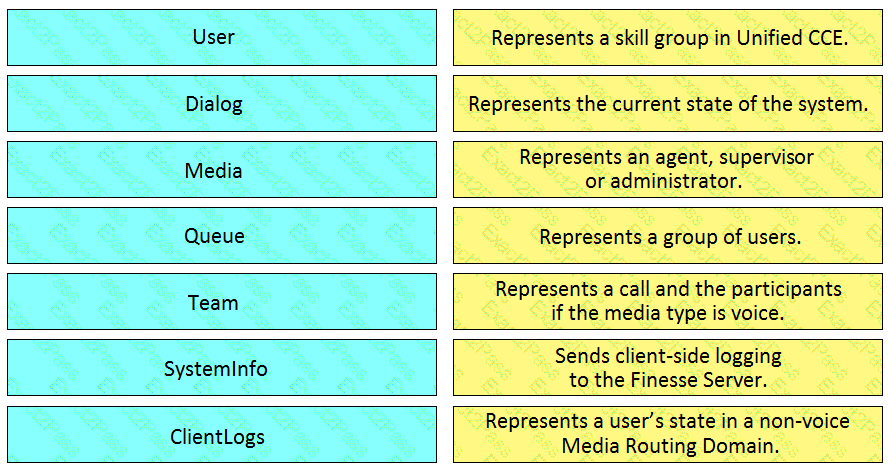
Drag and drop the element of the Finesse API on the left onto the description of its functionally on the right.
Which mechanism is used to consume a RESTful API design when large amounts of data are returned?
Which REST architectural constraint indicates that no client context should be stored on the server between requests?
Before which process is code review performed when version control is used?
A developer is reviewing a code that was written by a colleague. It runs fine, but there are many lines of code to do a seemingly simple task repeatedly. Which action organizes the code?