Which of the following statements are true for this search? (Select all that apply.) SEARCH: sourcetype=access* |fields action productld status
Which of the following is true about a datamodel that has been accelerated?
The time range specified for a historical search defines the ____________ .------questionable on ans
Which of the following searches will return all clientip addresses that start with 108?
Given the following eval statement:
...| eval fieldl - if(isnotnull(fieldl),fieldl,0), field2 = if(isnull
Which of the following is the equivalent using f ilinull?
Which of the following is included with the Splunk Common Information Model (CIM) Add-on?
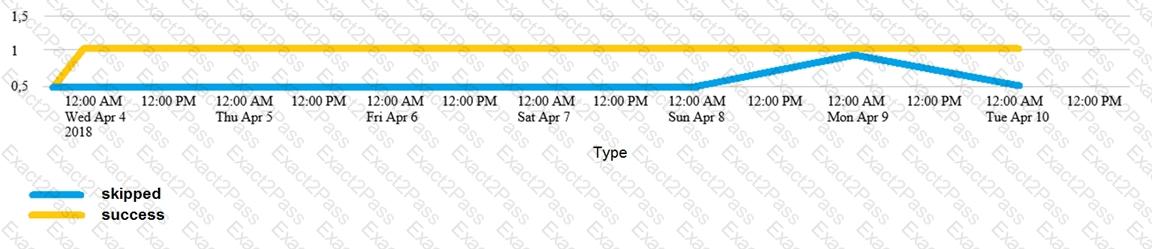
Which of the following searches would create a graph similar to the one below?
If there are fields in the data with values that are " " or empty but not null, which of the following would add a value?
There are several ways to access the field extractor. Which option automatically identifies data type, source type, and sample event?
Which knowledge object is used to normalize field names to comply with the Splunk Common Information Model (CIM)?
Which of the following searches will show the number of categoryld used by each host?
A user wants to create a new field alias for a field that appears in two sourcetypes.
How many field aliases need to be created?
What is the correct Boolean order of evaluation for the where command from first to last?
Which of the following eval commands will provide a new value for host from src if it exists?
Which of the following options will define the first event in a transaction?
When using multiple expressions in a single eval command, which delimiter is used?
Which of the following commands connects an additional table of data directly to the right side of the existing table?
Which of the following transforming commands can be used with transactions?
Which of the following statements would help a user choose between the transaction and stats commands?
This clause is used to group the output of a stats command by a specific name.
To create a tag, which of the following conditions must be met by the user?
Two separate results tables are being combined using the join command. The outer table has the following values:
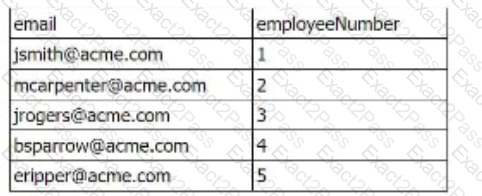
The inner table has the following values:
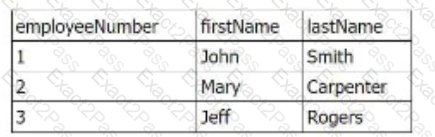
The line of SPL used to join the tables is: join employeeNumber type=outer
How many rows are returned in the new table?
To identify all of the contributing events within a transaction that contains at least one REJECT event, which syntax is correct?
Which of the following searches show a valid use of macro? (Select all that apply)
What is the correct syntax to search for a tag associated with a value on a specific fields?
Which of the following statements about data models and pivot are true? (select all that apply)
Which of the following searches will return events contains a tag name Privileged?
A field alias has been created based on an original field. A search without any transforming commands is then executed in Smart Mode. Which field name appears in the results?
Which of the following is the correct way to use the data model command to search field in the data model within the web dataset?
Which of the following statements about event types is true? (select all that apply)
Which of the following statements describes the command below (select all that apply)
Sourcetype=access_combined | transaction JSESSIONID
Which of the following Statements about macros is true? (select all that apply)
Which of the following statements describe data model acceleration? (select all that apply)
When using the Field Extractor (FX), which of the following delimiters will work? (select all that apply)
The Field Extractor (FX) is used to extract a custom field. A report can be created using this custom field. The created report can then be shared with other people in the organization. If another person in the organization runs the shared report and no results are returned, why might this be? (select all that apply)
Which of the following can be used with the eval command tostring function (select all that apply)
Data model fields can be added using the Auto-Extracted method. Which of the following statements describe Auto-Extracted fields? (select all that apply)
A user wants to convert numeric field values to strings and also to sort on those values.
Which command should be used first, the eval or the sort?
Which of the following workflow actions can be executed from search results? (select all that apply)
Which of the following statements describe the Common Information Model (CIM)? (select all that apply)
Which of the following statements describe the search string below?
| datamodel Application_State All_Application_State search
What does the fillnull command replace null values with, it the value argument is not specified?
When performing a regular expression (regex) field extraction using the Field Extractor (FX), what happens when the require option is used?
Which of the following describes the Splunk Common Information Model (CIM) add-on?
What does the Splunk Common Information Model (CIM) add-on include? (select all that apply)
By default, how is acceleration configured in the Splunk Common Information Model (CIM) add-on?