A security administrator ran a port scanning tool against a virtual server that is hosting a secure website. A list of open ports was provided as documentation. The management team has requested that non-essential ports be disabled on the firewall. Which of the following ports must remain open?
A company is implementing a check-in desk to heighten physical security. Which of the following access controls would be the most appropriate to facilitate this implementation?
Users report that the FinanceApp software is not running, and they need immediate
access. Issues with the FinanceApp software occur every week after the IT team
completes server system updates. The users, however, do not want to contact the
help desk every time the issue occurs. The users also report the new MarketApp
software is not usable when it crashes, which can cause significant downtime. The
technician who restarted the MarketApp software noticed it is running under a test
account, which is a likely cause of the crashes.
INSTRUCTIONS
Using the Services menu provided, modify the appropriate application services to
remedy the stated issues.

A technician is setting up a repurposed server. The minimum requirements are 2TB while ensuring the highest performance and providing support for one drive failure. The technician has the following six drives available:
Which of the following drive selections should the technician utilize to best accomplish this goal?
A server administrator is reviewing the following specifications:
VM01 Host:
CPU: 2 Physical, 4 Cores
RAM: 16GB
Storage: 16TB
Server 1 on VM01:
CPU: 1 virtual socket, 1 core per socket
RAM: 4GB
Storage: 8TB
Server 2 on VM01:
CPU: 2 virtual sockets, 2 cores per socket
RAM: 8GB
Storage: 10TB
Which of the following is described given these specifications?
Which of the following would allow a server administrator to ensure all maximum available resources are being utilized?
Which of the following types of physical security controls would most likely be a target of a social engineering attack?
While a technician is troubleshooting a performance issue on a database server, users are disconnected from the database. An administrator is asked to intervene and restore access. Which of the following steps should the administrator take first?
A technician is setting up a repurposed server. The minimum requirements are 2TB while ensuring the highest performance and providing support for one drive failure. The technician has the following six drives available:
500GB, 10,000rpm
600GB, 10,000rpm
500GB, 7,200rpm
500GB, 10,000rpm
600GB, 15,000rpm
600GB, 10,000rpm
Which of the following drive selections should the technician utilize to best accomplish this goal?
A server administrator set up a monitoring application on various servers to keep track of CPU usage, memory consumption, and disk space utilization. Which of the following should be configured on the application so it can send email alerts about a specific issue?
An administrator has deployed a new virtual server from a template. After confirming access to the subnet's gateway, the administrator is unable to log on with the domain credentials. Which of the following is the most likely cause of the issue?
Which of the following describes the concept of allocating more resources than what is available on a hypervisor?
A technician is connecting a server’s secondary NIC to a separate network. The technician connects the cable to the switch but then does not see any link lights on the NIC. The technician confirms there is nothing wrong on the network or with the physical connection. Which of the following should the technician perform NEXT?
A technician is attempting to update a server’s firmware. After inserting the media for the firmware and restarting the server, the machine starts normally into the OS. Which of the following should the technician do
NEXT to install the firmware?
Which of me following BEST describes a disaster recovery site with a target storage array that receives replication traffic and servers that are only powered on In the event of a disaster?
Following a recent power outage, a server in the datacenter has been constantly going offline and losing its configuration. Users have been experiencing access issues while using the application on the server. The server technician notices the data and time are incorrect when the server is online. All other servers are working. Which of the following would MOST likely cause this issue? (Choose two.)
A security analyst suspects a remote server is running vulnerable network applications. The analyst does not have administrative credentials for the server. Which of the following would MOST likely help the analyst determine if the applications are running?
Which of the following encryption methodologies would MOST likely be used to ensure encrypted data cannot be retrieved if a device is stolen?
An administrator is configuring a server that will host a high-performance financial application. Which of the following disk types will serve this purpose?
A server technician is configuring the IP address on a newly installed server. The documented configuration specifies using an IP address of 10.20.10.15 and a default gateway of 10.20.10.254. Which of the following subnet masks would be appropriate for this setup?
Which of the following can be used to map a network drive to a user profile?
An administrator needs to perform bare-metal maintenance on a server in a remote datacenter. Which of the following should the administrator use to access the server’s console?
Which of the following actions should a server administrator take once a new backup scheme has been configured?
A server administrator is exporting Windows system files before patching and saving them to the following location:
\\server1\ITDept\
Which of the following is a storage protocol that the administrator is MOST likely using to save this data?
Which of the following tools will analyze network logs in real time to report on suspicious log events?
A server administrator needs to harden a server by only allowing secure traffic and DNS inquiries. A port scan reports the following ports are open:
A technician is attempting to reboot a remote physical Linux server. However, attempts to command a shutdown -----now result in the loss of the SSH connection. The server still responds to pings. Which of the following should the technician use to command a remote shutdown?
Which of the following would a systems administrator implement to ensure all web traffic is secure?
A server administrator wants to run a performance monitor for optimal system utilization. Which of the following metrics can the administrator use for monitoring? (Choose two.)
Which of the following licenses would MOST likely include vendor assistance?
A server administrator is swapping out the GPU card inside a server. Which of the following actions should the administrator take FIRST?
An administrator is investigating a physical server mat will not Boot into the OS. The server has three hard drives configured in a RAID 5 array. The server passes POST, out the OS does not load. The administrator verities the CPU and RAM are Doth seated correctly and checks the dual power supplies. The administrator then verifies all the BIOS settings are correct and connects a bootable USB drive in the server, and the OS loads correctly. Which of the following is causing the issue?
A server technician has received reports of database update errors. The technician checks the server logs and determines the database is experiencing synchronization errors. To attempt to correct the errors, the technician should FIRST ensure:
A systems administrator needs to configure a new server and external storage for a new production application environment. Based on end-user specifications, the new solution needs to adhere to the following basic requirements:
1. The OS must be installed in a separate disk partition. In case of hard drive failure, it cannot be affected.
2. Application data IOPS performance is a must.
3. Data availability is a high priority, even in the case of multiple hard drive failures.
Which of the following are the BEST options to comply with the user requirements? (Choose three.)
The Chief Information Officer (CIO) of a datacenter is concerned that transmissions from the building can be detected from the outside. Which of the following would resolve this concern? (Choose two.)
Users in an office lost access to a file server following a short power outage. The server administrator noticed the server was powered off. Which of the following should the administrator do to prevent this situation in the future?
A company wants to deploy software to all users, Out very few of men will be using the software at any one point in time. Which of the following licensing models would be BEST lot the company?
A backup application is copying only changed files each line it runs. During a restore, however, only a single file is used. Which of the following backup methods does this describe?
A server is performing slowly, and users are reporting issues connecting to the application on that server. Upon investigation, the server administrator notices several unauthorized services running on that server that are successfully communicating to an external site. Which of the following are MOST likely causing the issue?
(Choose two.)
A systems administrator is investigating a server with a RAID array that will not boot into the OS. The administrator notices all the hard drives are reporting to be offline. The administrator checks the RAID controller and verifies the configuration is correct. The administrator then replaces one of the drives with a known-good drive, but it appears to be unavailable as well. Next, the administrator takes a drive out of the server and places it in a spare server, and the drive is available and functional. Which of the following is MOST likely causing the issue?
Hosting data in different regional locations but not moving it for long periods of time describes:
A server administrator has configured a web server. Which of the following does the administrator need to install to make the website trusted?
A technician is working on a Linux server. The customer has reported that files in the home directory are missing. The /etc/ f stab file has the following entry:
nfsserver:/home /home nfs defaults 0 0
However, a df -h /home command returns the following information:
/dev/sda2 10G 1G 9G 10% /home
Which of the following should the technician attempt FIRST to resolve the issue?
A technician is installing a variety of servers in a rack. Which of the following is the BEST course of action for the technician to take while loading the rack?
A technician runs top on a dual-core server and notes the following conditions:
top –- 14:32:27, 364 days, 14 usersload average 60.5 12.4 13.6
Which of the following actions should the administrator take?
Which of the following technologies would allow an administrator to build a software RAID on a Windows server?
Which of the following should an administrator use to transfer log files from a Linux server to a Windows workstation?
Which of the following is a method that is used to prevent motor vehicles from getting too close to building entrances and exits?
A server administrator has been creating new VMs one by one. The administrator notices the system requirements are very similar, even with different applications. Which of the following would help the administrator accomplish this task in the SHORTEST amount of time and meet the system requirements?
A server technician is installing a new server OS on legacy server hardware. Which of the following should the technician do FIRST to ensure the OS will work as intended?
A datacenter technician is attempting to troubleshoot a server that keeps crashing. The server runs normally for approximately five minutes, but then it crashes. After restoring the server to operation, the same cycle repeats. The technician confirms none of the configurations have changed, and the load on the server is steady from power-on until the crash. Which of the following will MOST likely resolve the issue?
A server administrator is installing an OS on a new server. Company policy states no one is to log in directly to the server. Which of the following Installation methods is BEST suited to meet the company policy?
A server administrator needs to deploy five VMs, all of which must have the same type of configuration. Which of the following would be the MOST efficient way to perform this task?
A company deploys antivirus, anti-malware, and firewalls that can be assumed to be functioning properly. Which of the following is the MOST likely system vulnerability?
A server technician has been asked to upload a few files from the internal web server to the internal FTP server. The technician logs in to the web server using PuTTY, but the connection to the FTP server fails. However, the FTP connection from the technician’s workstation is suсcessful. To troubleshoot the issue, the technician executes the following command on both the web server and the workstation:
ping ftp.acme.local
The IP address in the command output is different on each machine. Which of the following is the MOST likely reason for the connection failure?
A server administrator must respond to tickets within a certain amount of time. The server administrator needs to adhere to the:
A technician has received multiple reports of issues with a server. The server occasionally has a BSOD, powers off unexpectedly, and has fans that run continuously. Which of the following BEST represents what the technician should investigate during troubleshooting?
A storage administrator needs to implement SAN-based shared storage that can transmit at 16Gb over an optical connection. Which of the following connectivity options would BEST meet this requirement?
The Chief Information Officer of a data center is concerned that transmissions from the building can be detected from the outside. Which of the
following would resolve this concern? (Select TWO).
A server administrator is setting up a new payroll application. Compliance regulations require that all financial systems logs be stored in a central location. Which of the following should the administrator configure to ensure this requirement is met?
The accounting department needs more storage and wants to retain the current data for quick read-write access. The accounting server does not have any internet drive bays available to keep both disks however the server does have USB 3 0 and eSATA ports available. Which of the following is the BEST way to accomplish the department's goals?
Which of the following commands should a systems administrator use to create a batch script to map multiple shares'?
A technician is attempting to log in to a Linux server as root but cannot remember the administrator password. Which of the following is the LEAST destructive method of resetting the administrator password?
Which of the following ensures a secondary network path is available if the primary connection fails?
The HIDS logs on a server indicate a significant number of unauthorized access attempts via USB devices at startup. Which of the following steps should a server administrator take to BEST secure the server without limiting functionality?
A server administrator has received calls regarding latency and performance issues with a file server. After reviewing all logs and server features the administrator discovers the server came with four Ethernet ports, out only one port is currently in use. Which of the following features will enable the use of all available ports using a single IP address?
An administrator needs to increase the size of an existing RAID 6 array that is running out of available space. Which of the following is the best way the administrator can perform this task?
Which of the following BEST describes a guarantee of the amount of time it will take to restore a downed service?
A storage engineer responds to an alarm on a storage array and finds the battery on the RAID controller needs to be replaced. However, the
replacement part will not be available for 14 days. The engineer needs to identify the impact of the failed battery on the system. Which of the following best describes the impact?
An administrator has been asked to disable CPU hyperthreading on a server to satisfy a licensing issue. Which of the following best describes how the administrator will likely perform this action?
A systems administrator has several different types of hard drives. The administrator is setting up a MAS that will allow end users to see all the drives within the NAS. Which of the following storage types should the administrator use?
A technician learns users are unable to tog in to a Linux server with known-working LDAP credentials. The technician logs in to the server with a local account and confirms the system is functional can communicate over the network, and is configured correctly However, the server log has entries regarding Kerberos errors. Which of the following is the MOST likely source of the issue?
A server administrator encounters some issues with the server OS after applying monthly patches. Which of the following troubleshooting steps should the administrator perform?
A VLAN needs to be configured within a virtual environment for a new VM. Which of the following will ensure the VM receives a correct IP address?
A server administrator is implementing an authentication policy that will require users to use a token during login. Which of the following types of authentication is the administrator implementing?
A new application server has been configured in the cloud to provide access to all clients within the network. On-site users are able to access all resources, but remote users are reporting issues connecting to the new application. The server administrator verifies that all users are configured with the appropriate group memberships. Which of the following is MOST likely causing the issue?
Which of the following refers to the requirements that dictate when to delete data backups?
A server administrator receives the following output when trying to ping a local host:
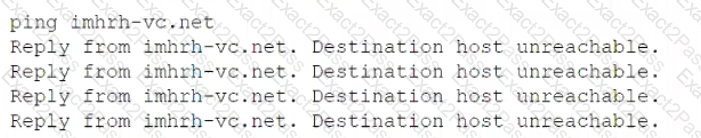
Which of the following is MOST likely the issue?
Which of the following describes a configuration in winch both nodes of a redundant system respond to service requests whenever possible?
A technician is creating a network snare that will be used across both Unix and Windows clients at the same time. Users need read and write access to the files. Which of the following would be BEST for the technician to deploy?
A server shut down after an extended power outage. When power was restored, the system failed to start. A few seconds into booting, the Num Lock, Scroll Lock, and Caps Lock LEDs flashed several times, and the system stopped. Which of the following is the MOST likely cause of the issue?
A systems administrator needs to back up changes made to a data store on a daily basis during a short time frame. The administrator wants to maximize RTO when restoring data. Which of the following backup methodologies would best fit this scenario?
A systems administrator is trying to determine why users in the human resources department cannot access an application server. The systems administrator reviews the application logs but does not see any attempts by the users to access the application. Which of the following is preventing the users from accessing the application server?
Which of the following commands would MOST likely be used to register a new service on a Windows OS?
A technician has beer tasked to install a new CPU. Prior to the retaliation the server must be configured. Which of the following should the technician update?
A server administrator wants to check the open ports on a server. Which of the following commands should the administrator use to complete the task?
A security technician generated a public/private key pair on a server. The technician needs to copy the key pair to another server on a different subnet. Which of the following is the most secure method to copy the keys?
HTTP
Two developers are working together on a project, and they have built out a set of snared servers that both developers can access over the internet. Which of the following cloud models is this an example of?
A company has a data center that is located at its headquarters, and it has a warm site that is located 20mi (32km) away, which serves as a DR location. Which of the following should the company design and implement to ensure its DR site is adequate?
A human resources analyst is attempting to email the records for new employees to an outside payroll company. Each time the analyst sends an email containing employee records, the email is rejected with an error message. Other emails outside the company are sent correctly. Which of the following is MOST likely generating the error?
An administrator is configuring a host-based firewall tor a server. The server needs to allow SSH, FTP, and LDAP traffic. Which of the following ports must be configured so this traffic will be allowed? (Select THREE).
The management team has mandated the use of data-at-rest encryption on all corporate servers. Using this encryption paradigm will ensure:
An administrator is troubleshooting an application performance issue on a virtual server with two vCPUs. The application performance logs indicate CPU contention. The administrator adds more vCPU cores to the VM, yet the issue persists. Which of the following is the most likely reason for this issue?
A systems administrator recently upgraded the memory in a server, and now the server does not turn on, and nothing is displayed on the screen.
Which of the following is the next step the administrator should take to diagnose the error without opening the machine?
Which of the following should be configured in pairs on a server to provide network redundancy?
The management team at a healthcare organization is concerned about being able to access the dairy vital records if there is an IT disaster that causes both servers and the network lo be offline. Which of the following backup types can the organization use to mitigate this risk?
Which of the following is a system that scans outgoing email for account numbers, sensitive phrases, and other forms of Pll?
A technician is setting up a small office that consists of five Windows 10 computers. The technician has been asked to use a simple IP configuration without manually adding any IP addresses. Which of the following will the technician MOST likely use for the IP address assignment?
A server administrator made a change in a server's BIOS in an attempt to fix an issue with the OS not turning on. However, the change did not successfully correct the issue. Which of the following should the server administrator do NEXT?
A server technician downloaded new firmware from the manufacturer's website. The technician then attempted to install the firmware on the server, but the installation failed, stating the file is potentially corrupt. Which of the following should the technician have checked prior to installing the firmware?
A technician has moved a data drive from a new Windows server to an older Windows server. The hardware recognizes the drive, but the data is not visible to the OS. Which of the following is the most likely cause of the issue?
An administrator received an alert that a backup job has been unsuccessful in the previous three attempts. The administrator discovers the issue occurred while backing up a user's data on a network share. Which of the following actions would be best to allow the job to complete successfully?
Which of the following actions should the server administrator perform on the server?
Several new components have been added to a mission-critical server, and corporate policy states all new components must meet server hardening requirements. Which of the following should be applied?
A user can successfully connect to a database server from a home office but is unable to access it from a hotel room. Which of the following authentication methods is most likely
configured?
A technician wants to duplicate a physical server to a remote private cloud for disaster recovery purposes. Which of the following techniques would best accomplish this goal?
Which of the following will protect critical data during a natural disaster?
Hackers recently targeted a company with an attack that resulted in a system breach, which compromised the organization's data. Because of the system breach, the administrator had to bypass normal change management procedures. Which of the following change management activities was necessary?
A company created a new DR plan. The management team would like to begin performing a review of this plan without endangering company data and with a minimal time commitment. Which of the following testing methods would best allow for this type of review?
Which of the following should a server administrator configure to ensure access to motherboard software is restricted?
A technician is configuring a new server with four disks for the development team. The requirements are disk redundancy and maximum usable disk capacity. Which of the following RAID levels should be used for this server?
A server administrator is connecting a new storage array to a server. The administrator has obtained multiple IP addresses for the array. Which of the following connection types is the server most likely using to connect to the array?
A server administrator is replacing a faulty PSU. The management team has asked for a solution that prevents further downtime in the future. Which of the following can the server administrator implement?
A server administrator is gathering business requirements to determine how frequently backups need to be performed on an application server. Which of the following is the administrator attempting to establish?
A server administrator is tasked with resolving an issue with the server's local storage. The administrator turns on the server and only two out of the four drives are found. After several reboots, an additional hard drive connects and disconnects randomly. Which of the following is most likely the cause?
Several mobile users are reporting intermittent performance issues when attempting to access network shares on the file server. After some investigation, the server administrator notices the server resources are running at maximum capacity, even during non-peak usage times. A recent port scan of the network identified this server as having too many unnecessary ports open to the public. Which of the following is the most likely cause of the performance issues?
An administrator is installing a new server and OS. After installing the OS, the administrator logs in and wants to quickly check the network configuration. Which of the following is the best command to use to
accomplish this task?
A technician is sizing a new server and, for service reasons, needs as many hot-swappable components as possible. Which of the following server components can most commonly be replaced without downtime? (Select three).
A systems administrator notices the fans are running at full speed in a newly upgraded server. Which of the following should be done to address this issue?
An administrator is troubleshooting connectivity to a remote server. The goal is to remotely connect to the server to make configuration changes. To further troubleshoot, a port scan revealed the ports on the
server as follows:
Port 22: Closed
Port 23: Open
Port 990: Closed
Which of the following next steps should the administrator take?
Reboot the workstation and then the server.
A technician needs to replace two RAID controllers on a database server as part of an upgrade. The server has six external storage arrays and eight internal disks that are controlled by the two RAID controllers. The technician completes the replacement and powers the systems back on, but the server OS detects several missing disks in the configuration. Which of the following steps should the technician take first to resolve this issue?
A technician is configuring a new server with four disks for the development team. The requirements are disk redundancy and maximum usable disk capacity. Which of the following RAID levels should be used for this server?
A systems administrator notices a newly added server cannot see any of the LUNs on the SAN. The SAN switch and the local HBA do not display any link lights. Which of the following is most likely the issue?
A Windows server has experienced a BSOD, and the administrator needs to monitor the reboot. The server is in a datacenter with no OOB management. Which of the following tools should the administrator use to complete this task?
An analyst is planning a new point-to-point Ethernet connection between a university campus and a newly acquired space downtown that is about 5mi (8km) away. The analyst would like the fastest possible connection speed. Which of the following would best meet the analyst's needs?
Which of the following technologies can successfully back up files that are used by other processes without stopping those processes?
A systems administrator is installing Windows on an 8TB drive and would like to create a single 8TB partition on the disk. Which of the following options should the administrator use?
Which of the following types of locks utilizes key fobs or key cards held against a sensor/reader to gain access?
Which of the following types of asset management documentation is commonly used as a reference when processing the replacement of a faulty server component?
Which of the following backup methods can be performed while a server is running, will not interrupt files in use, and can be used to fully restore the server if needed?
A software developer is unable to reach an internal website. The developer's attempt to ping the FQDN returns the following IP address: 104.18.17.32. Which of the following is the most likely reason for this result?
A site is considered a warm site when it:
has basic technical facilities connected to it.
has faulty air conditioning that is awaiting service.
is almost ready to take over all operations from the primary site.
An administrator is setting up a new server and has been asked to install an operating system that does not have a GUI because the server has limited resources. Which of the
following installation options should the administrator use?
Which of the following factors would most likely impact the selection of an organization's cloud provider?