You have an Azure subscription.
You need to implement approval-based time-bound role activation.
What should you use?
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.
What can you protect by using the information protection solution in the Microsoft 365 compliance center?
For each of the following statements, select Yes if the statement is true. Otherwise, select No. NOTE: Each correct selection is worth one point.

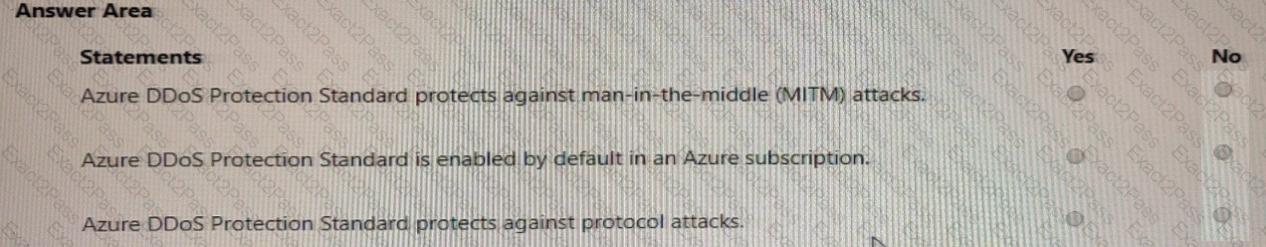
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.
Which Microsoft 365 feature can you use to restrict users from sending email messages that contain lists of customers and their associated credit card numbers?
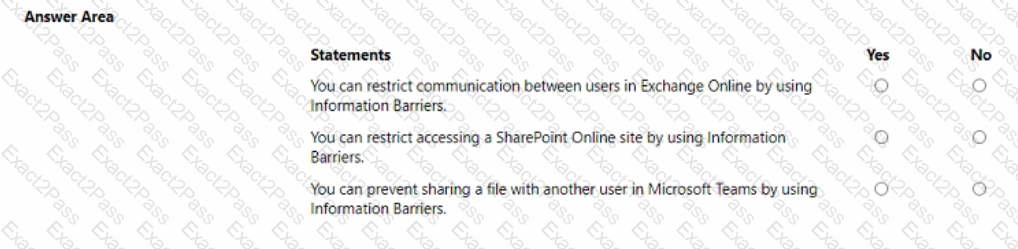
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.
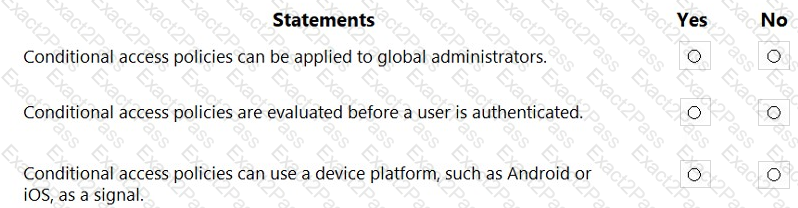
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.
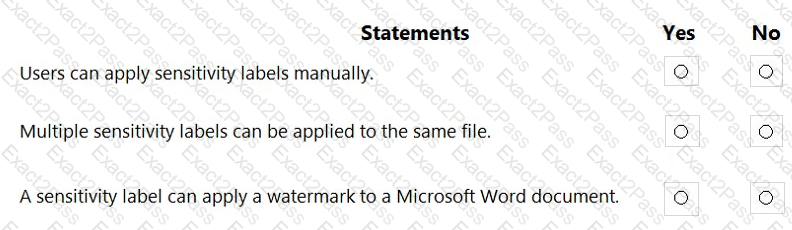
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.

What feature in Microsoft Defender for Endpoint provides the first line of defense against cyberthreats by reducing the attack surface?
Which two tasks can you implement by using data loss prevention (DLP) policies in Microsoft 365? Each correct answer presents a complete solution.
NOTE: Each correct selection is worth one point.
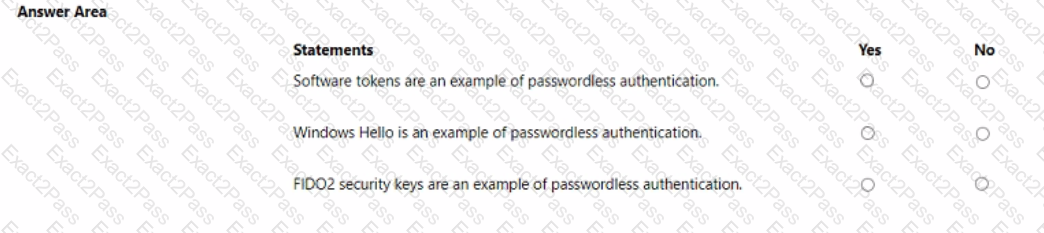
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.
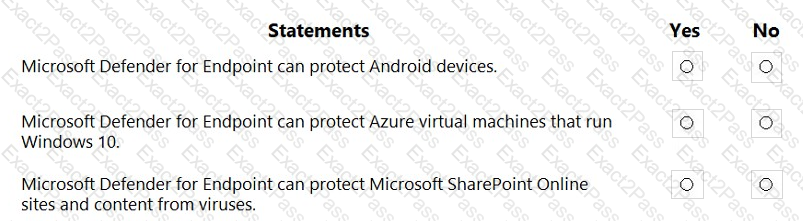
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.
Which pillar of identity relates to tracking the resources accessed by a user?
Microsoft 365 Endpoint data loss prevention (Endpoint DLP) can be used on which operating systems?
What are customers responsible for when evaluating security in a software as a service (SaaS) cloud services model?
What are two reasons to deploy multiple virtual networks instead of using just one virtual network? Each correct answer presents a complete solution.
NOTE; Each correct selection is worth one point.
What is the purpose of Azure Active Directory (Azure AD) Password Protection?
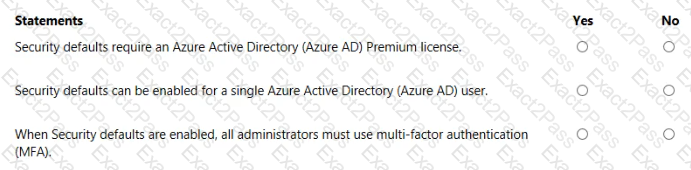
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.
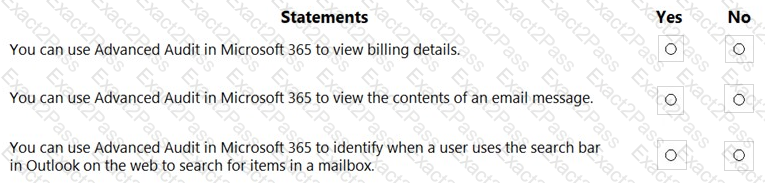
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point
You need to keep a copy of all files in a Microsoft SharePoint site for one year, even if users delete the files from the site. What should you apply to the site?
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.

What are three uses of Microsoft Cloud App Security? Each correct answer presents a complete solution.
NOTE: Each correct selection is worth one point.
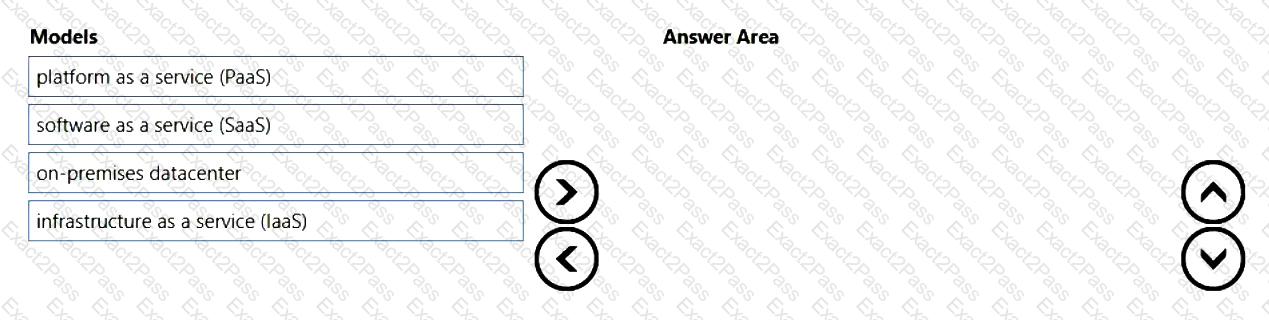
You need to identify which cloud service models place the most responsibility on the customer in a shared responsibility model.
in which order should you list the service models from the most customer responsibility (on the top) to the least customer responsibility (on the bottom)? To answer, move all models from the list of models to the answer area and arrange them in the correct order.
What can you use to provide threat detection for Azure SQL Managed Instance?
What are two capabilities of Microsoft Defender for Endpoint? Each correct selection presents a complete solution.
NOTE: Each correct selection is worth one point.
Which three authentication methods does Windows Hello for Business support? Each correct answer presents a complete solution.
NOTE: Each correct selection is worth one point.
What can you use to deploy Azure resources across multiple subscriptions in a consistent manner?
In the shared responsibility model for an Azure deployment, what is Microsoft solely responsible for managing?
In a hybrid identity model, what can you use to sync identities between Active Directory Domain Services (AD DS) and Azure Active Directory (Azure AD)?
For each of the following statements, select Yes if the statement is true. Otherwise, select No. NOTE: Each correct selection is worth one point.
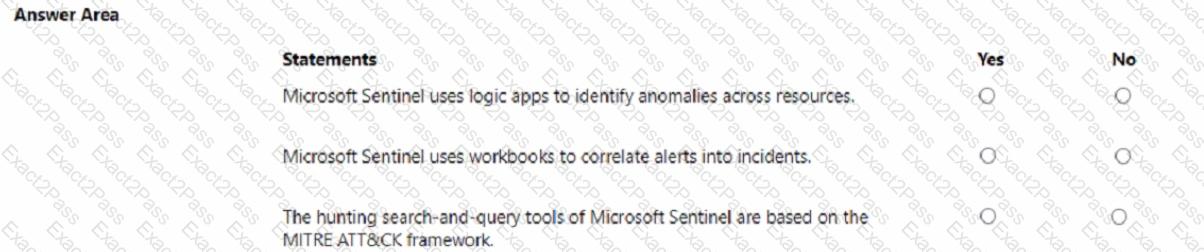
You have an Azure subscription.
You need to implement approval-based, tiProme-bound role activation.
What should you use?
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.
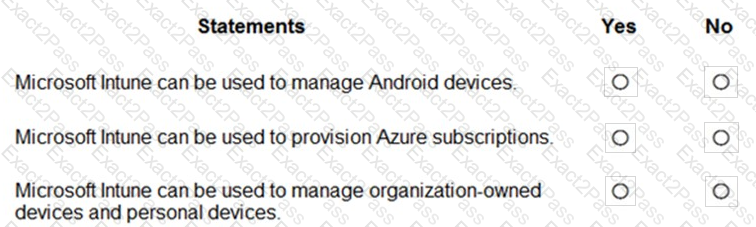
Which Microsoft 365 compliance center feature can you use to identify all the documents on a Microsoft SharePoint Online site that contain a specific key word?
Which type of identity is created when you register an application with Active Directory (Azure AD)?
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.
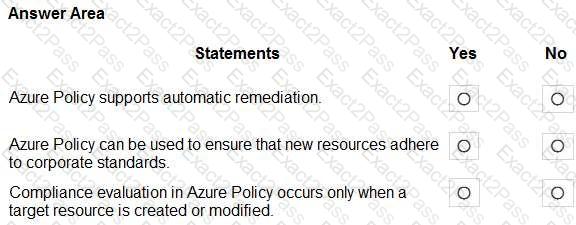
For each of the following statement, select Yes if the statement is true Otherwise, select No.
NOTE: Each connect selection a worth one point.
