Last Update 1 hour ago Total Questions : 272
The CompTIA PenTest+ Exam content is now fully updated, with all current exam questions added 1 hour ago. Deciding to include PT0-003 practice exam questions in your study plan goes far beyond basic test preparation.
You'll find that our PT0-003 exam questions frequently feature detailed scenarios and practical problem-solving exercises that directly mirror industry challenges. Engaging with these PT0-003 sample sets allows you to effectively manage your time and pace yourself, giving you the ability to finish any CompTIA PenTest+ Exam practice test comfortably within the allotted time.
During a pre-engagement activity with a new customer, a penetration tester looks for assets to test. Which of the following is an example of a target that can be used for testing?
A penetration tester wants to check the security awareness of specific workers in the company with targeted attacks. Which of the following attacks should the penetration tester perform?
During an assessment, a penetration tester wants to extend the vulnerability search to include the use of dynamic testing. Which of the following tools should the tester use?
A penetration tester needs to identify all vulnerable input fields on a customer website. Which of the following tools would be best suited to complete this request?
A tester runs an Nmap scan against a Windows server and receives the following results:
Nmap scan report for win_dns.local (10.0.0.5)
Host is up (0.014s latency)
Port State Service
53/tcp open domain
161/tcp open snmp
445/tcp open smb-ds
3389/tcp open rdp
Which of the following TCP ports should be prioritized for using hash-based relays?
A penetration tester is working on a security assessment of a mobile application that was developed in-house for local use by a hospital. The hospital and its customers are very concerned about disclosure of information. Which of the following tasks should the penetration tester do first?
During an engagement, a penetration tester receives a list of target systems and wants to enumerate them for possible vulnerabilities. The tester finds the following script on the internet:
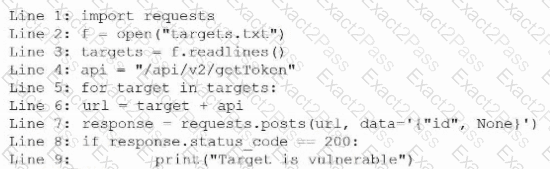
After running the script, the tester runs the following command:
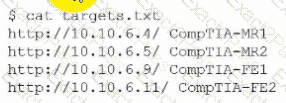
Which of the following should the tester do next?

