Last Update 23 hours ago Total Questions : 216
The Planning & Scheduling Professional (PSP) Exam content is now fully updated, with all current exam questions added 23 hours ago. Deciding to include PSP practice exam questions in your study plan goes far beyond basic test preparation.
You'll find that our PSP exam questions frequently feature detailed scenarios and practical problem-solving exercises that directly mirror industry challenges. Engaging with these PSP sample sets allows you to effectively manage your time and pace yourself, giving you the ability to finish any Planning & Scheduling Professional (PSP) Exam practice test comfortably within the allotted time.
Project schedules help control all of the following EXCEPT for_____________________.
Scenario:
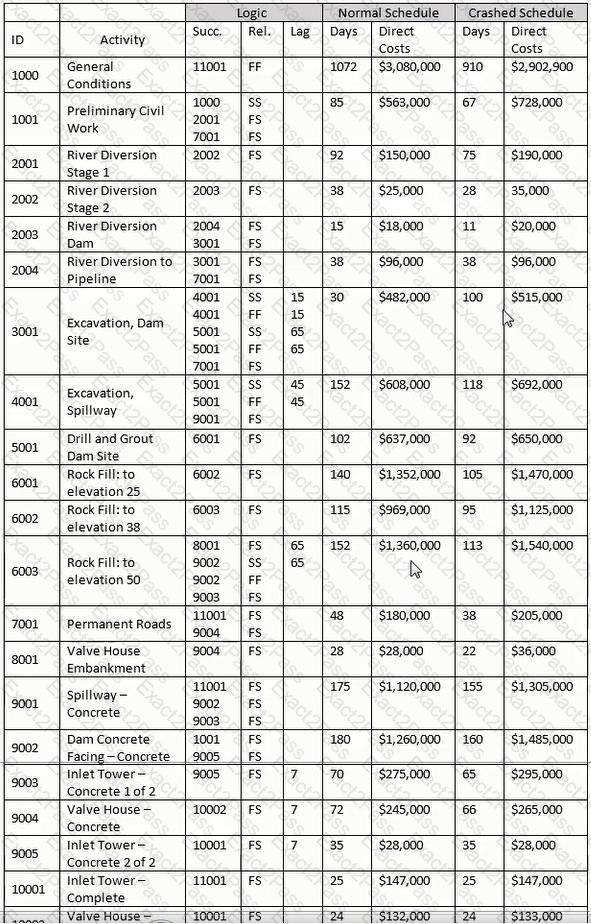
The entire network consists of the following activities and relationships. Activity A is twenty days long and is tied to Activity B, a ten-day activity, with a finish-to-finish tie with a lag value of five Activity B is tied to Activity C, a twenty-day activity, with a start-to-start relationship with a lag value of five.
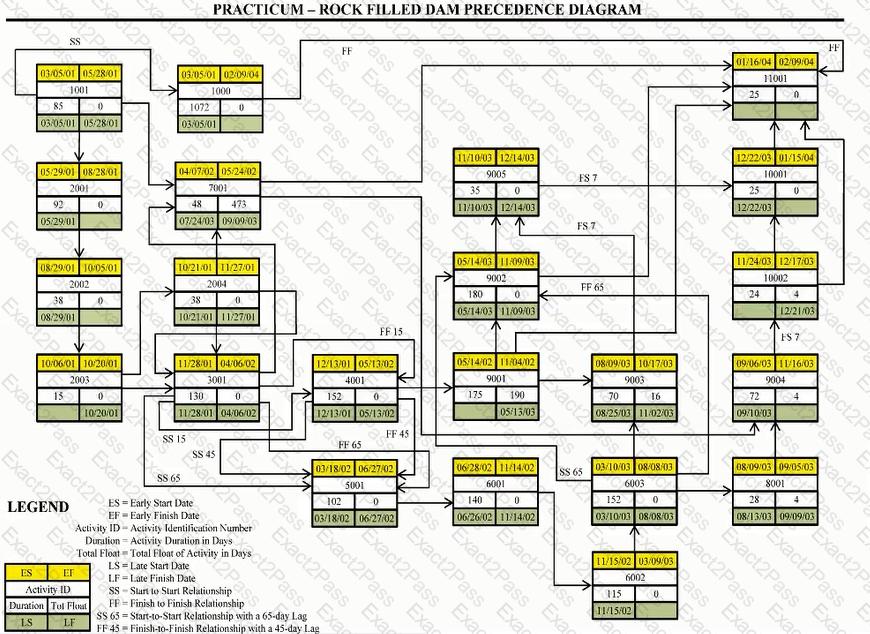
PSP Activities Table
Scope Known about Rock-Filled Dam Project:
The dam requires river diversion and work over two or more rainy seasons. The contract is lump sum, competitively bid, and will be self-performed. The owner has attempted to shift all risk to the contractor by employing "no differing sit conditions" and "no damage for delay" clauses. There is a bonus/penalty provision of $2,500 per calendar day for early or late delivery. The early completion bonus is capped at $500,000, with no cap for late delivery penalty.
Liquidated damages end at the finish of demobilization. Indirect costs per calendar day are $2,800 for the "normal" schedule and $3,200 for the "crashed" schedule. The winter/wet weather season is 151 days between October 15 and March 25 of each year, reduces the efficiency of the contractor's operations by 20% and costs the contractor $10,000 per day. Assume a start date of March 5, 2001 and use a 7-day work week.
The following table lists work activities as planned by the contractor.
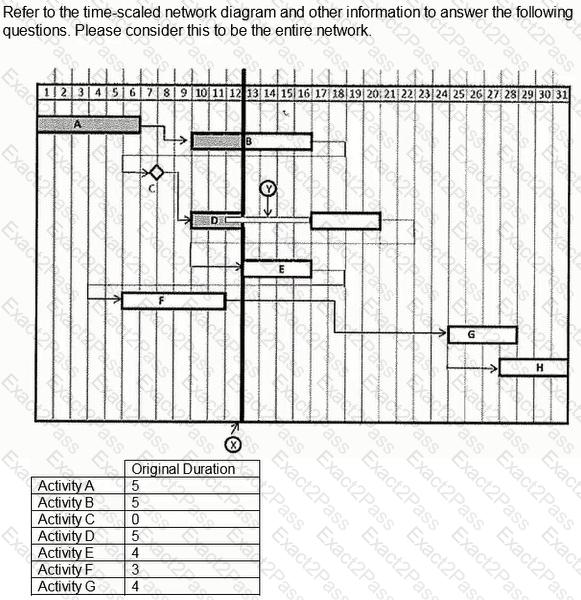
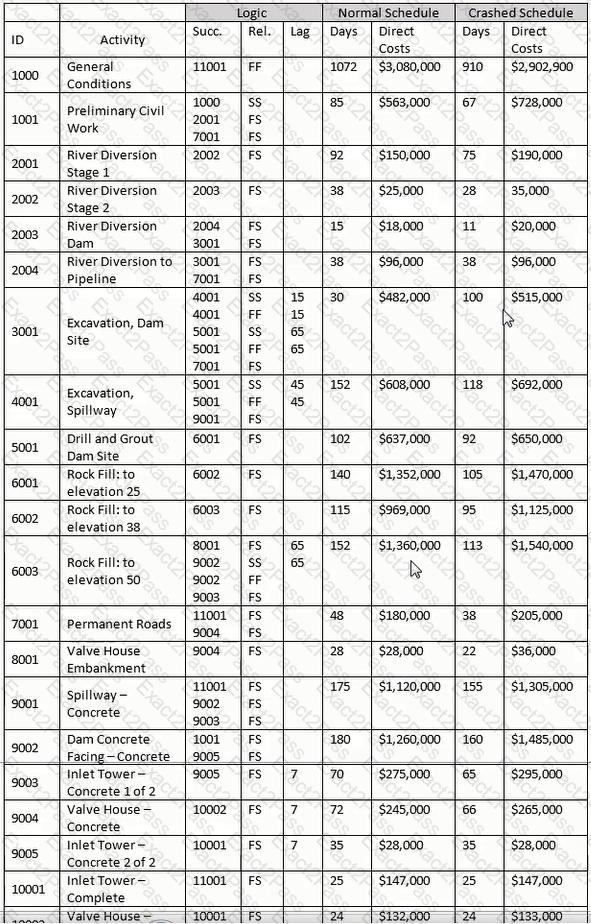
Theoretically construct a summary activity for only those activities with a finish-to-start relationship for Activities 8001 through 10001. Using the "normal" schedule, what is the cost of this hammock?
Activity 2003 started during the current reporting period and proceeded as planned with the normal schedule. If the remaining duration at the end of this period is ten workdays, then what is the earned value assignable to Activity 2003 in the pay estimate for this reporting period?
What does the narrow band at "Y" represent?
When should the Project Plan have incorporated the relevant interfaces and requirements of the project contract documents?
In a "crashed" schedule, which is a chain of activities that precede activity 2004?
In its simplest form, what is the main drawback of critical path method scheduling?

