An administrator is building Security rules within a device group to block traffic to and from malicious locations.
How should those rules be configured to ensure that they are evaluated with a high priority?
An administrator would like to determine which action the firewall will take for a specific CVE. Given the screenshot below, where should the administrator navigate to view this information?
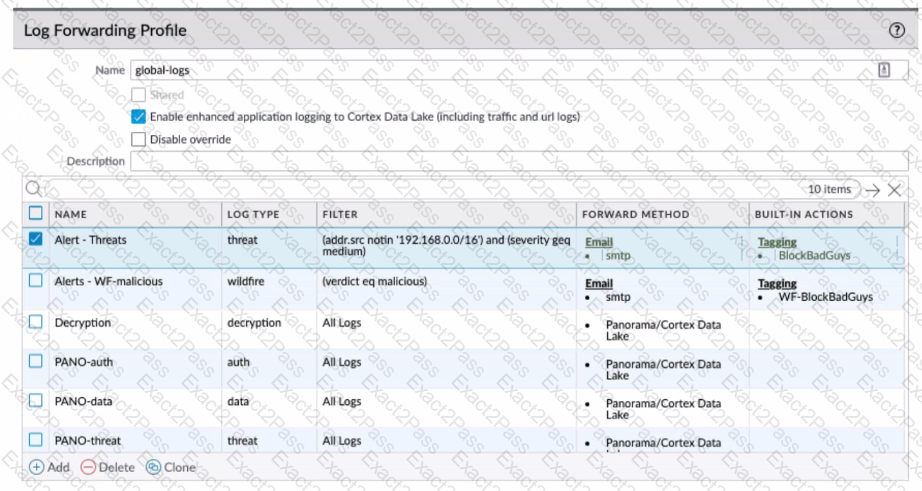
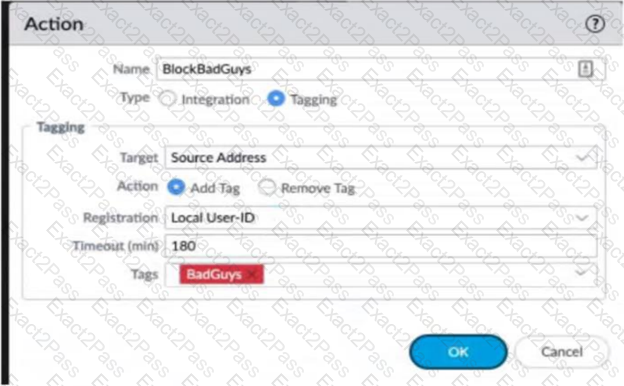
Review the images. A firewall policy that permits web traffic includes the global-logs policy is depicted
What is the result of traffic that matches the "Alert - Threats" Profile Match List?
An administrator receives the following error message:
"IKE phase-2 negotiation failed when processing Proxy ID. Received local id 192.168 33 33/24 type IPv4 address protocol 0 port 0, received remote id 172.16 33.33/24 type IPv4 address protocol 0 port 0."
How should the administrator identify the root cause of this error message?
Which two actions can the administrative role called "vsysadmin" perform? (Choose two)
Which three authentication types can be used to authenticate users? (Choose three.)
A network security engineer needs to enable Zone Protection in an environment that makes use of Cisco TrustSec Layer 2 protections
What should the engineer configure within a Zone Protection profile to ensure that the TrustSec packets are identified and actions are taken upon them?
When backing up and saving configuration files, what is achieved using only the firewall and is not available in Panorama?
An engineer is configuring a template in Panorama which will contain settings that need to be applied to all firewalls in production.
Which three parts of a template an engineer can configure? (Choose three.)
An administrator is attempting to create policies tor deployment of a device group and template stack. When creating the policies, the zone drop down list does not include the required zone.
What must the administrator do to correct this issue?
An administrator is required to create an application-based Security policy rule to allow Evernote. The Evernote application implicitly uses SSL and web browsing.
What is the minimum the administrator needs to configure in the Security rule to allow only Evernote?
Which type of zone will allow different virtual systems to communicate with each other?
A company wants to use GlobalProtect as its remote access VPN solution.
Which GlobalProtect features require a Gateway license?
How should an administrator enable the Advance Routing Engine on a Palo Alto Networks firewall?
An engineer has been given approval to upgrade their environment to the latest version of PAN-OS. The environment consists of both physical and virtual firewalls, a virtual Panorama, and virtual log collectors. What is the recommended order of operational steps when upgrading?
A network security administrator wants to enable Packet-Based Attack Protection in a Zone Protection profile. What are two valid ways to enable Packet-Based Attack Protection? (Choose two.)
Exhibit.
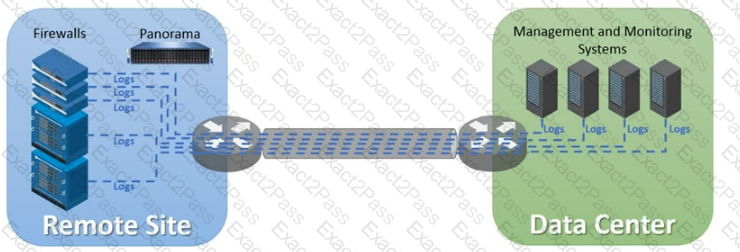
An organization has Palo Alto Networks NGFWs that send logs to remote monitoring and security management platforms The network team has reported excessive traffic on the corporate WAN How could the Palo Alto Networks NGFW administrator reduce WAN traffic while maintaining support for all the existing monitoring/security platforms?
A company has configured a URL Filtering profile with override action on their firewall. Which two profiles are needed to complete the configuration? (Choose two)
An organization is interested in migrating from their existing web proxy architecture to the Web Proxy feature of their PAN-OS 11.0 firewalls. Currently. HTTP and SSL requests contain the c IP address of the web server and the client browser is redirected to the proxy
Which PAN-OS proxy method should be configured to maintain this type of traffic flow?
View the screenshots
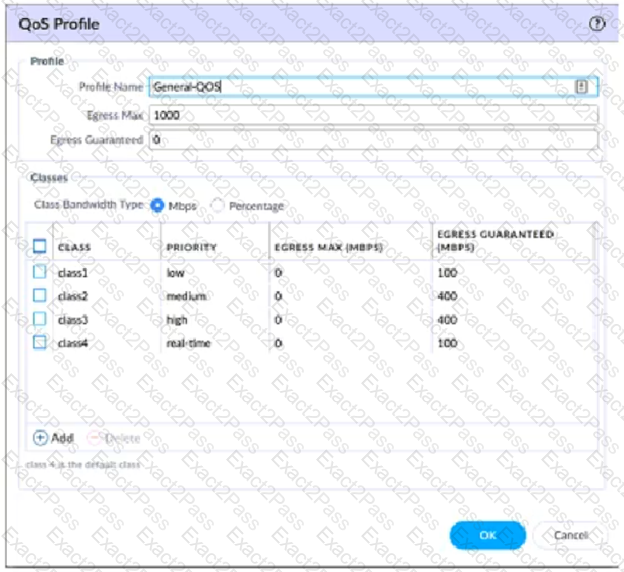
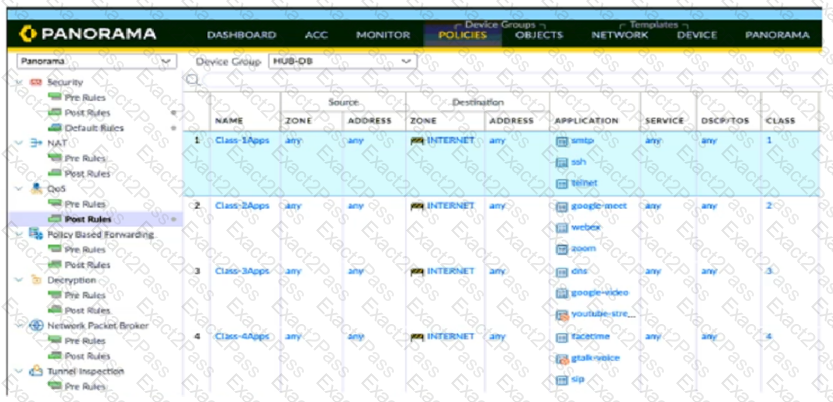
A QoS profile and policy rules are configured as shown. Based on this information which two statements are correct?
An engineer is configuring a Protection profile to defend specific endpoints and resources against malicious activity.
The profile is configured to provide granular defense against targeted flood attacks for specific critical systems that are accessed by users from the internet.
Which profile is the engineer configuring?
Certain services in a customer implementation are not working, including Palo Alto Networks Dynamic version updates.
Which CLI command can the firewall administrator use to verify if the service routes were correctly installed and that they are active in the Management Plane?
A firewall administrator is investigating high packet buffer utilization in the company firewall. After looking at the threat logs and seeing many flood attacks coming from a single source that are dropped by the firewall, the administrator decides to enable packet buffer protection to protect against similar attacks.
The administrator enables packet buffer protection globally in the firewall but still sees a high packet buffer utilization rate.
What else should the administrator do to stop packet buffers from being overflowed?
An administrator plans to deploy 15 firewalls to act as GlobalProtect gateways around the world. Panorama will manage the firewalls.
The firewalls will provide access to mobile users and act as edge locations to on-premises infrastructure. The administrator wants to scale the configuration out quickly and wants all of the firewalls to use the same template configuration.
Which two solutions can the administrator use to scale this configuration? (Choose two.)
When a new firewall joins a high availability (HA) cluster, the cluster members will synchronize all existing sessions over which HA port?
An engineer troubleshoots a Panorama-managed firewall that is unable to reach the DNS servers configured via a global template. As a troubleshooting step, the engineer needs to configure a local DNS server in place of the template value.
Which two actions can be taken to ensure that only the specific firewall is affected during this process? (Choose two )
ln a security-first network, what is the recommended threshold value for apps and threats to be dynamically updated?
An administrator needs to gather information about the CPU utilization on both the management plane and the data plane. Where does the administrator view the desired data?
Which User-ID mapping method should be used in a high-security environment where all IP address-to-user mappings should always be explicitly known?
A firewall administrator is changing a packet capture filter to troubleshoot a specific traffic flow Upon opening the newly created packet capture, the administrator still sees traffic for the previous fitter What can the administrator do to limit the captured traffic to the newly configured filter?
How can a firewall be set up to automatically block users as soon as they are found to exhibit malicious behavior via a threat log?
A firewall engineer reviews the PAN-OS GlobalProtect application and sees that it implicitly uses web-browsing and depends on SSL.
When creating a new rule, what is needed to allow the application to resolve dependencies?
A company is deploying User-ID in their network. The firewall team needs to have the ability to see and choose from a list of usernames and user groups directly inside the Panorama policies when creating new security rules.
How can this be achieved?
A firewall engineer creates a destination static NAT rule to allow traffic from the internet to a webserver hosted behind the edge firewall. The pre-NAT IP address of the server is 153.6 12.10, and the post-NAT IP address is 192.168.10.10. Refer to the routing and interfaces information below.
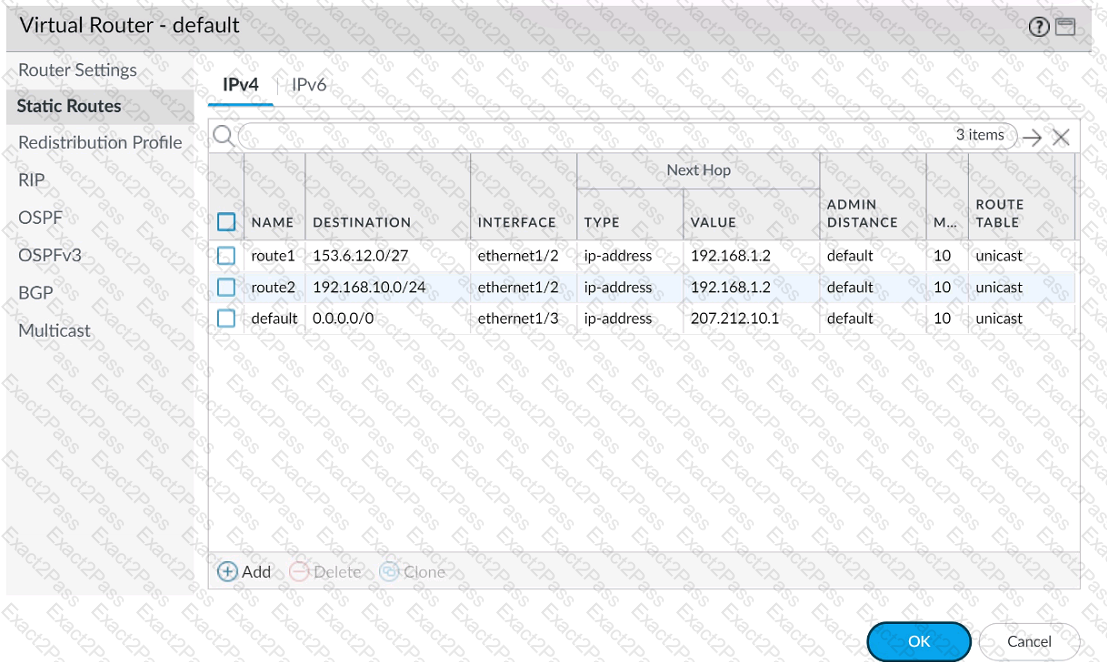
What should the NAT rule destination zone be set to?
A root cause analysis investigation into a recent security incident reveals that several decryption rules have been disabled. The security team wants to generate email alerts when decryption rules are changed.
How should email log forwarding be configured to achieve this goal?
Information Security is enforcing group-based policies by using security-event monitoring on Windows User-ID agents for IP-to-User mapping in the network. During the rollout, Information Security identified a gap for users authenticating to their VPN and wireless networks.
Root cause analysis showed that users were authenticating via RADIUS and that authentication events were not captured on the domain controllers that were being monitored Information Security found that authentication events existed on the Identity Management solution (IDM). There did not appear to be direct integration between PAN-OS and the IDM solution
How can Information Security extract and learn iP-to-user mapping information from authentication events for VPN and wireless users?
What must be taken into consideration when preparing a log forwarding design for all of a customer’s deployed Palo Alto Networks firewalls?
Which Panorama mode should be used so that all logs are sent to. and only stored in. Cortex Data Lake?
Which GlobalProtect gateway selling is required to enable split-tunneling by access route, destination domain, and application?
When you troubleshoot an SSL Decryption issue, which PAN-OS CL1 command do you use to check the details of the Forward Trust certificate. Forward Untrust certificate, and SSL Inbound Inspection certificate?
Users are intermittently being cut off from local resources whenever they connect to GlobalProtect. After researching, it is determined that this is caused by an incorrect setting on one of the NGFWs. Which action will resolve this issue?
Which two key exchange algorithms consume the most resources when decrypting SSL traffic? (Choose two)
Which Panorama feature protects logs against data loss if a Panorama server fails?
What is the best description of the Cluster Synchronization Timeout (min)?
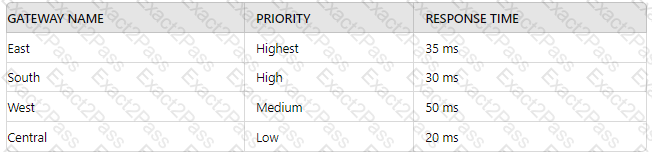
A security engineer has configured a GlobalProtect portal agent with four gateways Which GlobalProtect Gateway will users connect to based on the chart provided?
A firewall architect is attempting to install a new Palo Alto Networks NGFW. The company has previously had issues moving all administrative functions onto a data plane interface to meet the design limitations of the environment. The architect is able to access the device for HTTPS and SSH; however, the NGFW can neither validate licensing nor get updates. Which action taken by the architect will resolve this issue?
What action does a firewall take when a Decryption profile allows unsupported modes and unsupported traffic with TLS 1.2 protocol traverses the firewall?
As a best practice, which URL category should you target first for SSL decryption?
A network administrator configured a site-to-site VPN tunnel where the peer device will act as initiator None of the peer addresses are known
What can the administrator configure to establish the VPN connection?
An administrator is receiving complaints about application performance degradation. After checking the ACC, the administrator observes that there is an excessive amount of VoIP traffic.
Which three elements should the administrator configure to address this issue? (Choose three.)
An engineer needs to configure a standardized template for all Panorama-managed firewalls. These settings will be configured on a template named "Global" and will be included in all template stacks.
Which three settings can be configured in this template? (Choose three.)
An engineer troubleshooting a VPN issue needs to manually initiate a VPN tunnel from the CLI Which CLI command can the engineer use?
Which three methods are supported for split tunneling in the GlobalProtect Gateway? (Choose three.)
An administrator plans to install the Windows-Based User-ID Agent.
What type of Active Directory (AD) service account should the administrator use?
What happens when an A/P firewall pair synchronizes IPsec tunnel security associations (SAs)?
A company is expanding its existing log storage and alerting solutions All company Palo Alto Networks firewalls currently forward logs to Panorama. Which two additional log forwarding methods will PAN-OS support? (Choose two)
A security engineer wants to upgrade the company's deployed firewalls from PAN-OS 10.1 to 11.0.x to take advantage of the new TLSvl.3 support for management access.
What is the recommended upgrade path procedure from PAN-OS 10.1 to 11.0.x?
A company uses GlobalProtect for its VPN and wants to allow access to users who have only an endpoint solution installed. Which sequence of configuration steps will allow access only for hosts that have antivirus or anti-spyware enabled?
Which type of policy in Palo Alto Networks firewalls can use Device-ID as a match condition?
An administrator connects a new fiber cable and transceiver Ethernet1/1 on a Palo Alto Networks firewall. However, the link does not come up. How can the administrator troubleshoot to confirm the transceiver type, tx-power, rxpower, vendor name, and part number by using the CLI?
The server team is concerned about the high volume of logs forwarded to their syslog server, it is determined that DNS is generating the most logs per second. The risk and compliance team requests that any Traffic logs indicating port abuse of port 53 must still be forwarded to syslog. All other DNS. Traffic logs can be exclude from syslog forwarding. How should syslog log forwarding be configured?
Which three firewall multi-factor authentication factors are supported by PAN-OS? (Choose three.)
What is the benefit of the Artificial Intelligence Operations (AIOps) Plugin for Panorama?
All firewall at a company are currently forwarding logs to Palo Alto Networks log collectors. The company also wants to deploy a sylog server and forward all firewall logs to the syslog server and to the log collectors. There is known logging peak time during the day, and the security team has asked the firewall engineer to determined how many logs per second the current Palo Alto Networking log processing at that particular time. Which method is the most time-efficient to complete this task?
During the process of developing a decryption strategy and evaluating which websites are required for corporate users to access, several sites have been identified that cannot be decrypted due to technical reasons. In this case, the technical reason is unsupported ciphers Traffic to these sites will therefore be blocked if decrypted.
How should the engineer proceed?
An administrator is informed that the engineer who previously managed all the VPNs has left the company. According to company policies the administrator must update all the IPSec VPNs with new pre-shared keys Where are the pre-shared keys located on the firewall?
An administrator configures a preemptive active-passive high availability (HA) pair of firewalls and configures the HA election settings on firewall-02 with a device priority value of 100, and firewall-01 with a device priority value of 90.
When firewall-01 is rebooted, is there any action taken by the firewalls?
A customer requires that virtual systems with separate virtual routers can communicate with one another within a Palo Alto Networks firewall. In addition to confirming Security policies, which three configurations will accomplish this goal? (Choose three)
An organization wants to begin decrypting guest and BYOD traffic.
Which NGFW feature can be used to identify guests and BYOD users, instruct them how to download and install the CA certificate, and clearly notify them that their traffic will be decrypted?
Which two policy components are required to block traffic in real time using a dynamic user group (DUG)? (Choose two.)
Refer to Exhibit:
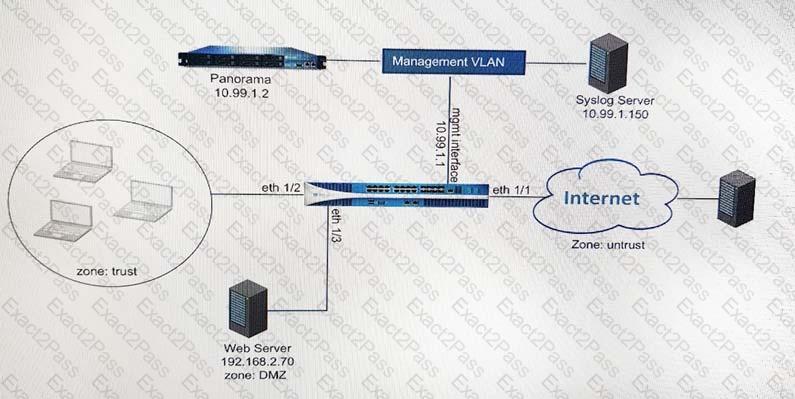
An administrator can not see any Traffic logs from the Palo Alto Networks NGFW in Panorama reports. The configuration problem seems to be on the firewall. Which settings, if configured incorrectly, most likely would stop only Traffic logs from being sent from the NGFW to Panorama?
A)
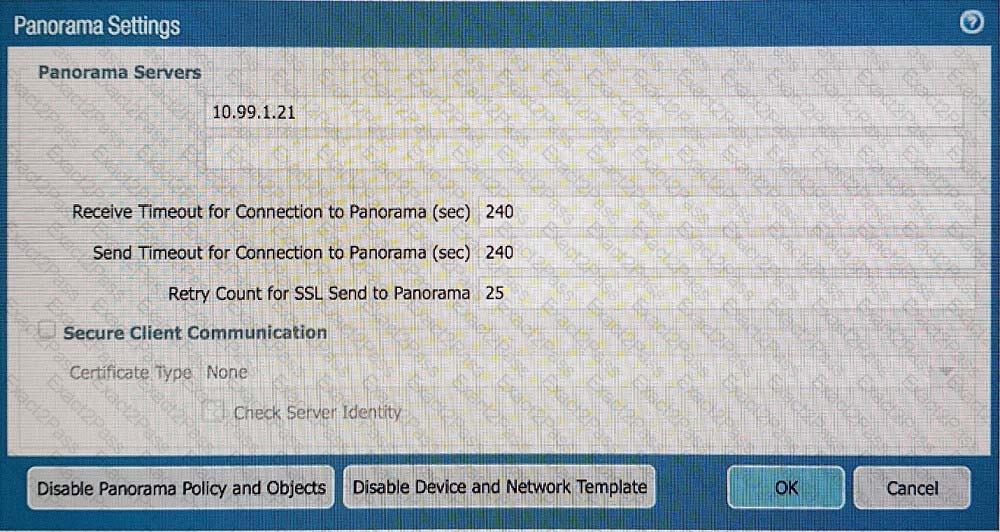
B)
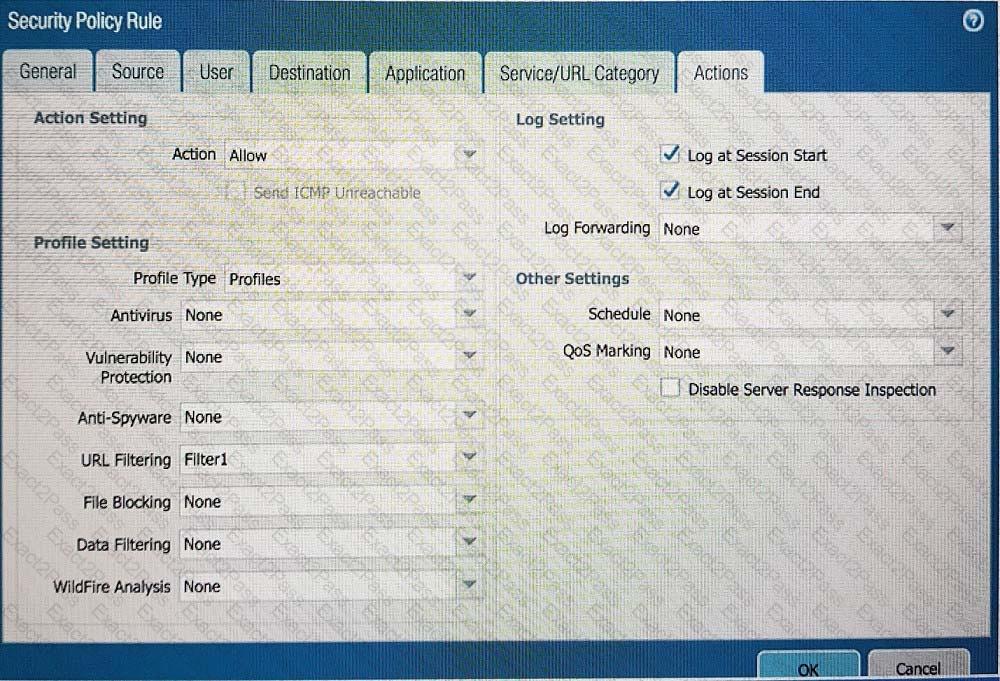
C)
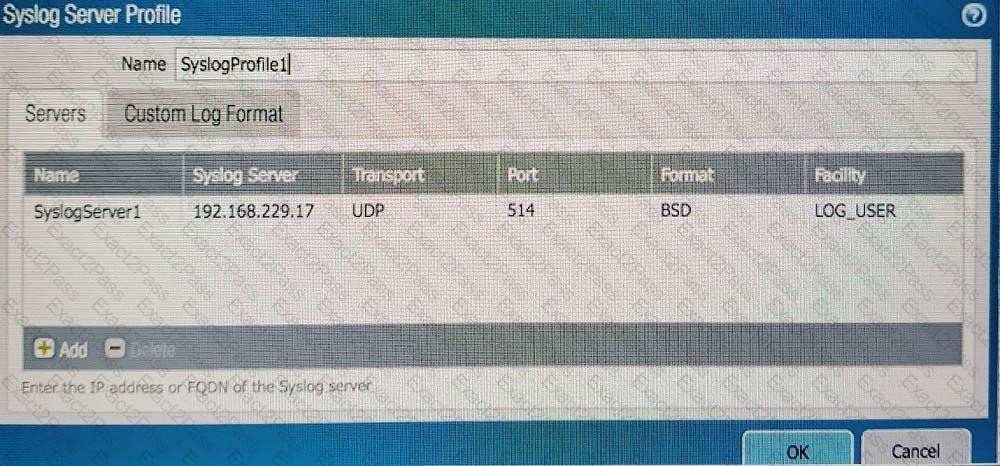
D)
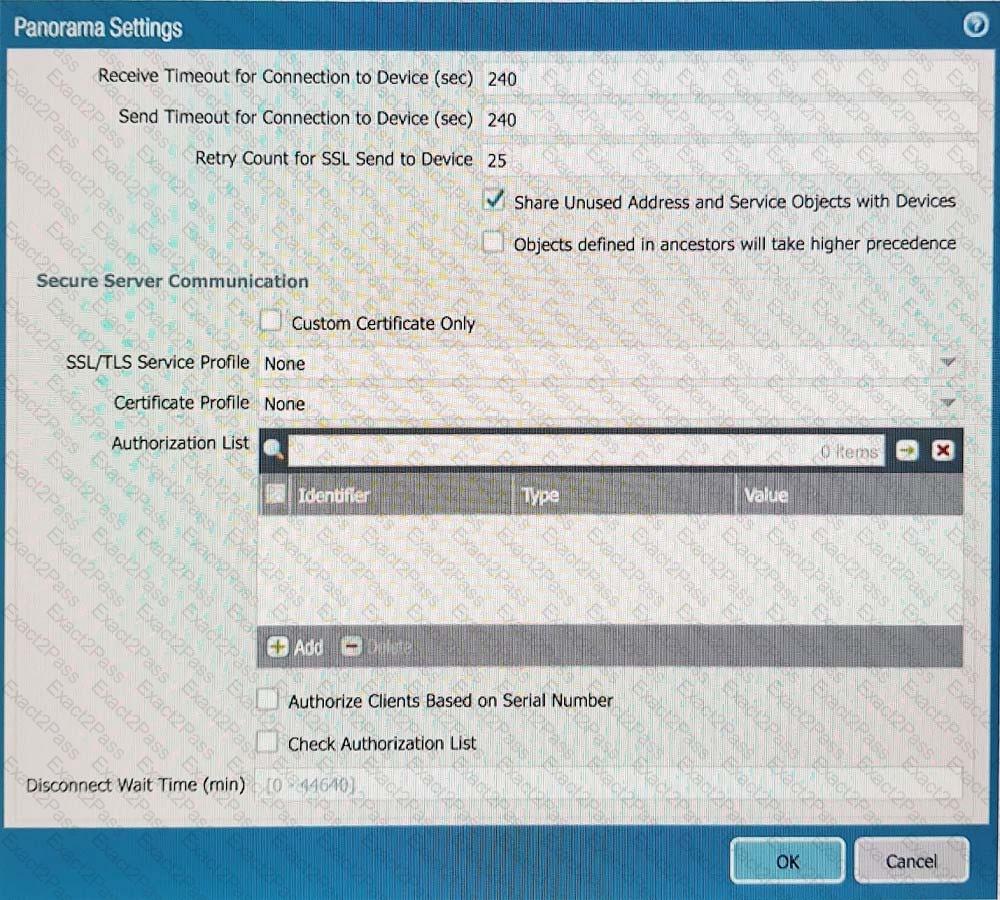
A consultant advises a client on designing an explicit Web Proxy deployment on PAN-OS 11 0 The client currently uses RADIUS authentication in their environment
Which two pieces of information should the consultant provide regarding Web Proxy authentication? (Choose two.)
A company requires that a specific set of ciphers be used when remotely managing their Palo Alto Networks appliances.
Which profile should be configured in order to achieve this?
Which statement explains the difference between using the PAN-OS integrated User-ID agent and the standalone User-ID agent when using Active Directory for user-to-IP mapping?
An engineer configures a destination NAT policy to allow inbound access to an internal server in the DMZ. The NAT policy is configured with the following values:
- Source zone: Outside and source IP address 1.2.2.2
- Destination zone: Outside and destination IP address 2.2.2.1
The destination NAT policy translates IP address 2.2.2.1 to the real IP address 10.10.10.1 in the DMZ zone.
Which destination IP address and zone should the engineer use to configure the security policy?
A network administrator is trying to prevent domain username and password submissions to phishing sites on some allowed URL categories
Which set of steps does the administrator need to take in the URL Filtering profile to prevent credential phishing on the firewall?
An engineer needs to collect User-ID mappings from the company’s existing proxies. What two methods can be used to pull this data from third-party proxies? (Choose two)
A firewall engineer needs to update a company's Panorama-managed firewalls to the latest version of PAN-OS. Strict security requirements are blocking internet access to Panorama and to the firewalls. The PAN-OS images have previously been downloaded to a secure host on the network.
Which path should the engineer follow to deploy the PAN-OS images to the firewalls?
During the implementation of SSL Forward Proxy decryption, an administrator imports the company's Enterprise Root CA and Intermediate CA certificates onto the firewall. The company's Root and Intermediate CA certificates are also distributed to trusted devices using Group Policy and GlobalProtect. Additional device certificates and/or Subordinate certificates requiring an Enterprise CA chain of trust are signed by the company's Intermediate CA.
Which method should the administrator use when creating Forward Trust and Forward Untrust certificates on the firewall for use with decryption?
An administrator notices that an interface configuration has been overridden locally on a firewall. They require all configuration to be managed from Panorama and overrides are not allowed. What is one way the administrator can meet this requirement?
A company has configured GlobalProtect to allow their users to work from home. A decrease in performance for remote workers has been reported during peak-use hours.
Which two steps are likely to mitigate the issue? (Choose TWO)
An administrator notices interface ethernet1/2 failed on the active firewall in an active / passive firewall high availability (HA) pair Based on the image below what - if any - action was taken by the active firewall when the link failed?
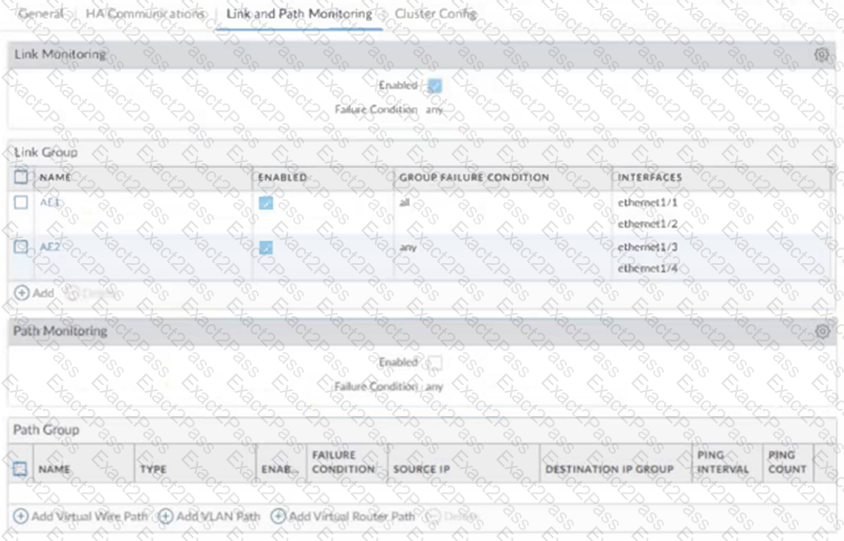
A remote administrator needs access to the firewall on an untrust interface. Which three options would you configure on an interface Management profile to secure management access? (Choose three)
When an engineer configures an active/active high availability pair, which two links can they use? (Choose two)
When you import the configuration of an HA pair into Panorama, how do you prevent the import from affecting ongoing traffic?
An enterprise Information Security team has deployed policies based on AD groups to restrict user access to critical infrastructure systems. However, a recent phishing campaign against the organization has prompted Information Security to look for more controls that can secure access to critical assets. For users that need to access these systems. Information Security wants to use PAN-OS multi-factor authentication (MFA) integration to enforce MFA.
What should the enterprise do to use PAN-OS MFA?
What should an engineer consider when setting up the DNS proxy for web proxy?
A company requires that a specific set of ciphers be used when remotely managing their Palo Alto Networks appliances. Which profile should be configured in order to achieve this?
An administrator plans to install the Windows User-ID agent on a domain member system.
What is a best practice for choosing where to install the User-ID agent?
What can the Log Forwarding built-in action with tagging be used to accomplish?