Which of the following are secure options for storing the contents of the Operator CD, while still allowing the contents to be accessible upon a planned Vault restart? (Choose three.)
You are installing PSM for SSH with AD-Bridge in CyberArkSSHD mode for your customer. ACME Corp What do you need to install to meet your customer's needs? (Choose 2)
When a group is granted the 'Authorize Account Requests' permission on a safe Dual Control requests must be approved by
A customer is deploying PVWAs in the Amazon Web Services Public Cloud. Which load balancing option does CyberArk recommend?
Before the hardening process your customer identified a PSM Universal Connector executable that will be required to run on the PSM Which file should you update to allow this to run?
Match each PTA alert category with the PTA sensors that collect the data for it.

Which type of automatic remediation can be performed by the PTA in case of a suspected credential theft security event?
Which onboarding method would you use to integrate CyberArk with your accounts provisioning process?
CyberArk implements license limits by controlling the number and types of users that can be provisioned in the vault.
Which option in the PrivateArk client is used to update users' Vault group memberships?
PTA can automatically suspend sessions if suspicious activities are detected in a privileged session, but only if the session is made via the CyberArk PSM.
When a DR Vault Server becomes an active vault, it will automatically revert back to DR mode once the Primary Vault comes back online.
For an account attached to a platform that requires Dual Control based on a Master Policy exception, how would you configure a group of users to access a password without approval.
An auditor initiates a live monitoring session to PSM server to view an ongoing live session. When the auditor’s machine makes an RDP connection the PSM server, which user will be used?
In addition to disabling Windows services or features not needed for PVWA operations, which tasks does PVWA Hardening.ps1 perform when run?
In order to connect to a target device through PSM, the account credentials used for the connection must be stored in the vault?
Ad-Hoc Access (formerly Secure Connect) provides the following features. Choose all that apply.
Which browser is supported for PSM Web Connectors developed using the CyberArk Plugin Generator Utility (PGUP
To enable the Automatic response “Add to Pending” within PTA when unmanaged credentials are found, what are the minimum permissions required by PTAUser for the PasswordManager_pending safe?
Your organization requires all passwords be rotated every 90 days.
Where can you set this regulatory requirement?
Which Cyber Are components or products can be used to discover Windows Services or Scheduled Tasks that use privileged accounts? Select all that apply.
In the Private Ark client, how do you add an LDAP group to a CyberArk group?
Due to network activity, ACME Corp’s PrivateArk Server became active on the OR Vault while the Primary Vault was also running normally. All the components continued to point to the Primary Vault.
Which steps should you perform to restore DR replication to normal?
When creating Distributed Vault environment architecture, what is the maximum number of Vault servers that can be deployed''
What is the name of the Platform parameters that controls how long a password will stay valid when One Time Passwords are enabled via the Master Policy?
You need to enable the PSM for all platforms. Where do you perform this task?
Via Password Vault Web Access (PVWA), a user initiates a PSM connection to the target Linux machine using RemoteApp. When the client’s machine makes an RDP connection to the PSM server, which user will be utilized?
A customer is moving from an on-premises to a public cloud deployment. What is the best and most cost-effective option to secure the server key?
The Privileged Access Management solution provides an out-of-the-box target platform to manage SSH keys, called UNIX Via SSH Keys.
How are these keys managed?
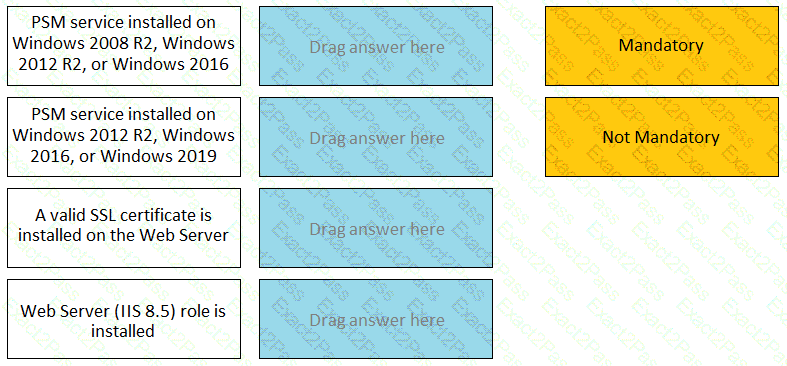
For each listed prerequisite, identify if it is mandatory or not mandatory to run the PSM Health Check.
Which parameter controls how often the CPM looks for accounts that need to be changed from recently completed Dual control requests.
Which SMTP address can be set on the Notification Settings page to re-invoke the ENE setup wizard after the initial Vault installation.
You have been asked to design the number of PVWAs a customer must deploy. The customer has three data centers with a distributed vault in each, requires high availability, and wants to use all vaults, at all times. How many PVWAs does the customer need?
Which of the following PTA detections require the deployment of a Network Sensor or installing the PTA Agent on the domain controller?
A user is receiving the error message “ITATS006E Station is suspended for User jsmith” when attempting to sign into the Password Vault Web Access (PVWA). Which utility would a Vault administrator use to correct this problem?
Which of the following PTA detections are included in the Core PAS offering?
In a rule using “Privileged Session Analysis and Response” in PTA, which session options are available to configure as responses to activities?
When a DR Vault Server becomes an active vault, it will automatically fail back to the original state once the Primary Vault comes back online.
CyberArk user Neil is trying to connect to the Target Linux server 192.168.1.64 using a domain account ACME/linuxuser01 on Domain Acme.corp using PSM for SSH server 192.168.65.145. What is the correct syntax?
You are onboarding 5,000 UNIX root accounts for rotation by the CPM. You discover that the CPM is unable to log in directly with the root account and will need to use a secondary account.
How should this be configured to allow for password management using least privilege?
According to the DEFAULT Web Options settings, which group grants access to the REPORTS page?
If the AccountUploader Utility is used to create accounts with SSH keys, which parameter do you use to set the full or relative path of the SSH private key file that will be attached to the account?
Customers who have the ‘Access Safe without confirmation’ safe permission on a safe where accounts are configured for Dual control, still need to request approval to use the account.