Last Update 1 hour ago Total Questions : 93
The Netskope Certified Cloud Security Integrator (NCCSI) content is now fully updated, with all current exam questions added 1 hour ago. Deciding to include NSK200 practice exam questions in your study plan goes far beyond basic test preparation.
You'll find that our NSK200 exam questions frequently feature detailed scenarios and practical problem-solving exercises that directly mirror industry challenges. Engaging with these NSK200 sample sets allows you to effectively manage your time and pace yourself, giving you the ability to finish any Netskope Certified Cloud Security Integrator (NCCSI) practice test comfortably within the allotted time.
Review the exhibit.
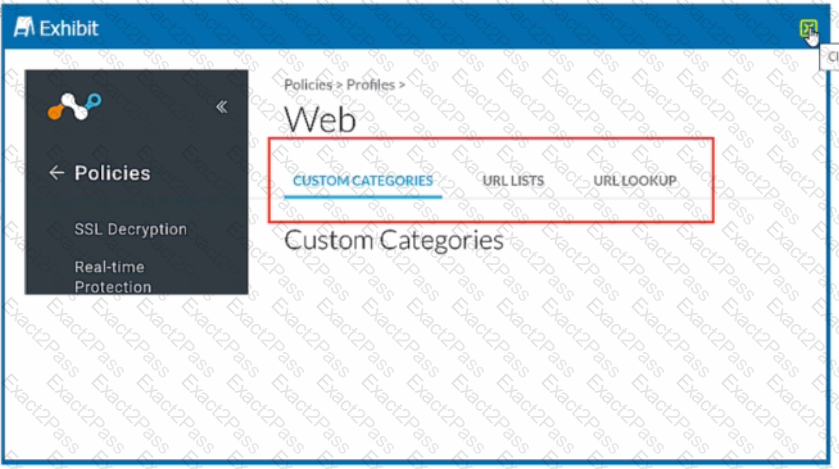
You want to create a custom URL category to apply a secure Web gateway policy combining your own list of URLs and Netskope predefined categories.
In this scenario, which task must be completed?
Your customer is migrating all of their applications over to Microsoft 365 and Azure. They have good practices and policies in place (or their inline traffic, but they want to continuously detect reconfigurations and enforce compliance standards.
Which two solutions would satisfy their requirements? (Choose two.)
Review the exhibit.
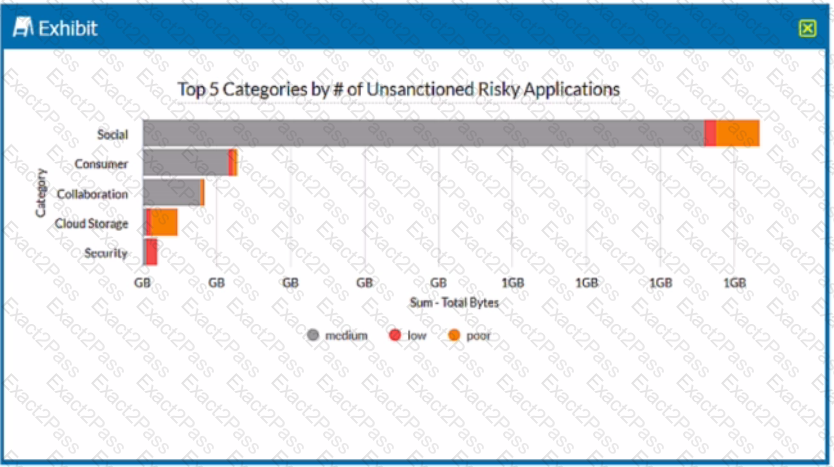
A security analyst needs to create a report to view the top five categories of unsanctioned applications accessed in the last 90 days. Referring to the exhibit, what are two data collections in Advanced Analytics that would be used to create this report? (Choose two.)
Review the exhibit.

Your Real-time Protection policy contains some rules with only a browse activity. The exhibit shows a new policy rule.
Where is the correct location to place this rule?
You are configuring GRE tunnels from a Palo Alto Networks firewall to a Netskope tenant with the Netskope for Web license enabled. Your tunnel is up as seen from the Netskope dashboard. You are unable to ping hosts behind the Netskope gateway.
Which two statements are true about this scenario? (Choose two.)
Review the exhibit.
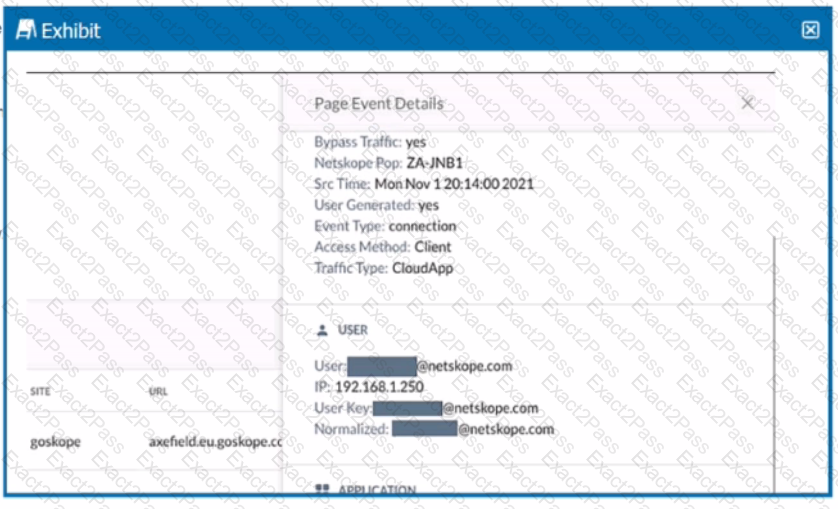
You are asked to restrict users from accessing YouTube content tagged as Sport. You created the required real-time policy; however, users can still access the content
Referring to the exhibit, what is the problem?
Review the exhibit.
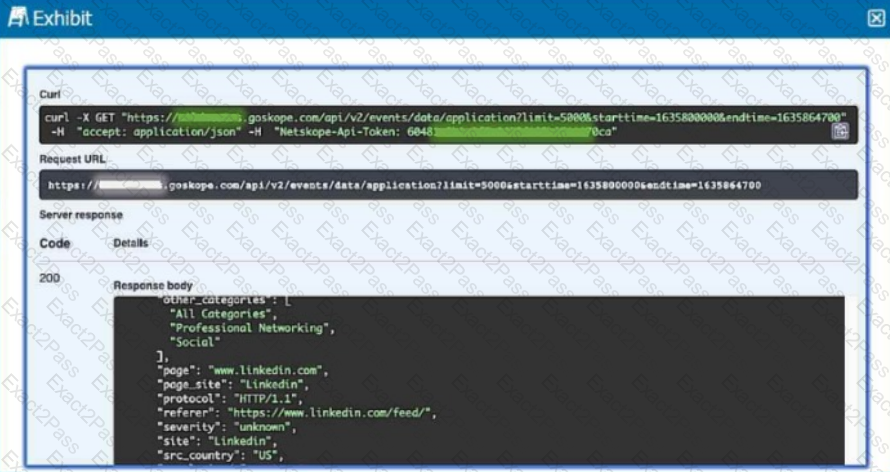
Referring to the exhibit, which three statements are correct? (Choose three.)

