Refer to the exhibit.
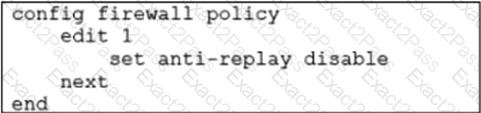
In a dual-hub hub-and-spoke SD-WAN deployment, which is a benefit of disabling theanti-replaysetting on the hubs?
Which diagnostic command can you use to show the configured SD-WAN zones and their assigned members?
Refer to the exhibit.

Which configuration change is required if the responder FortiGate uses a dynamic routing protocol to exchange routes over IPsec?
Refer to the exhibit.
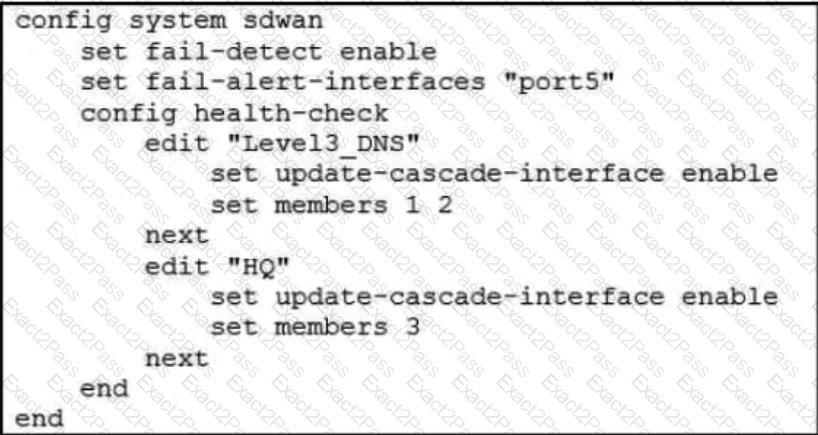
Based on the exhibit, which action does FortiGate take?
Refer to the Exhibits:
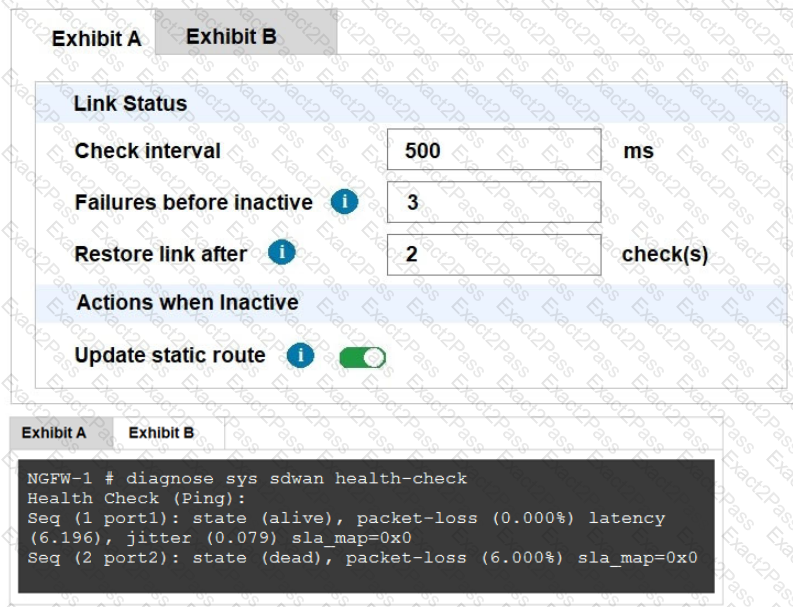
Exhibit A, which shows the SD-WAN performance SLA and exhibit B shows the health of the participating SD-WAN members.
Based on the exhibits, which statement is correct?
Which are two benefits of using CLI templates in FortiManager? (Choose two.)
What are two benefits of using the Internet service database (ISDB) in an SD-WAN rule? (Choose two.)
Exhibit.
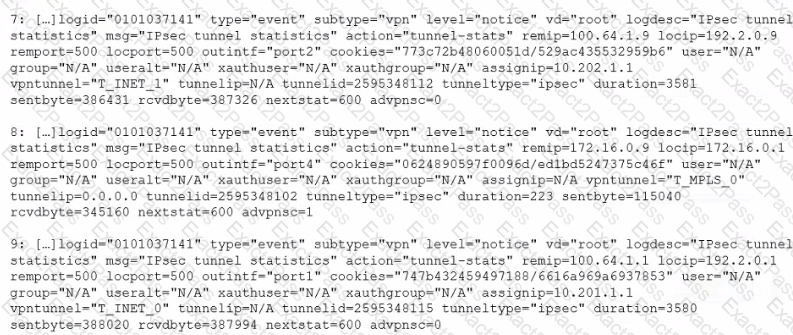
The exhibit shows VPN event logs on FortiGate. In the output shown in the exhibit, which statement is true?
Refer to the exhibits.
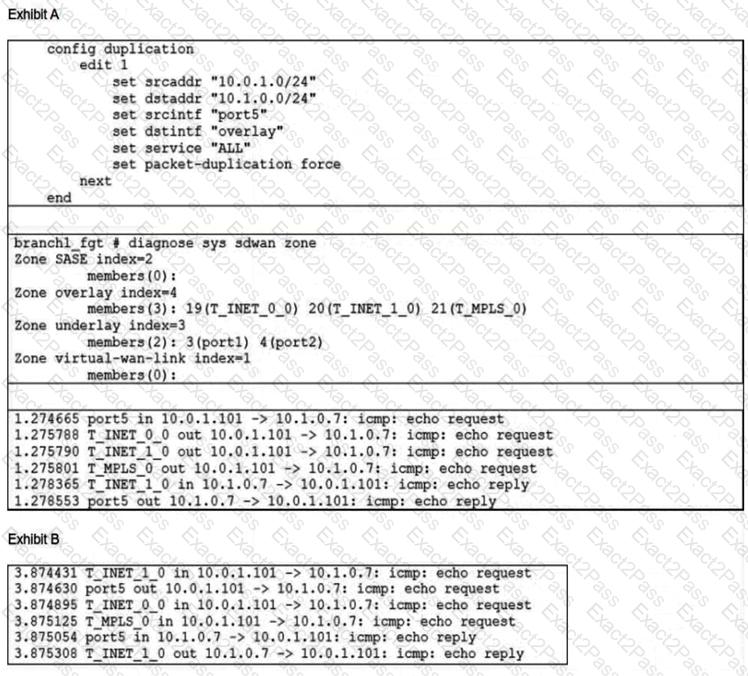
Exhibit A shows the packet duplication rule configuration, the SD-WAN zone status output, and the sniffer output on FortiGate acting as the sender. Exhibit B shows the sniffer output on a FortiGate acting as the receiver.
The administrator configured packet duplication on both FortiGate devices. The sniffer output on the sender FortiGate shows that FortiGate forwards an ICMP echo request packet over three overlays, but it only receives one reply packet through T_INET_1_0.
Based on the output shown in the exhibits, which two reasons can cause the observed behavior? (Choose two.)
Refer to the exhibits.
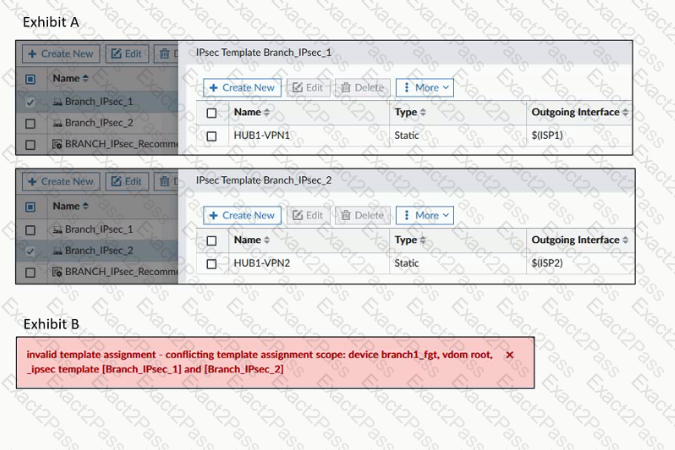
Exhibit A shows two IPsec templates to define Branch_IPsec_1 and Branch_IPsec_2. Each template defines a VPN tunnel.
Exhibit B shows the error message that FortiManager displayed when the administrator tried to assign the second template to the FortiGate device.
Which statement best explain the cause for this issue?
Which two statements about SD-WAN central management are true? (Choose two.)
Refer to the exhibit.
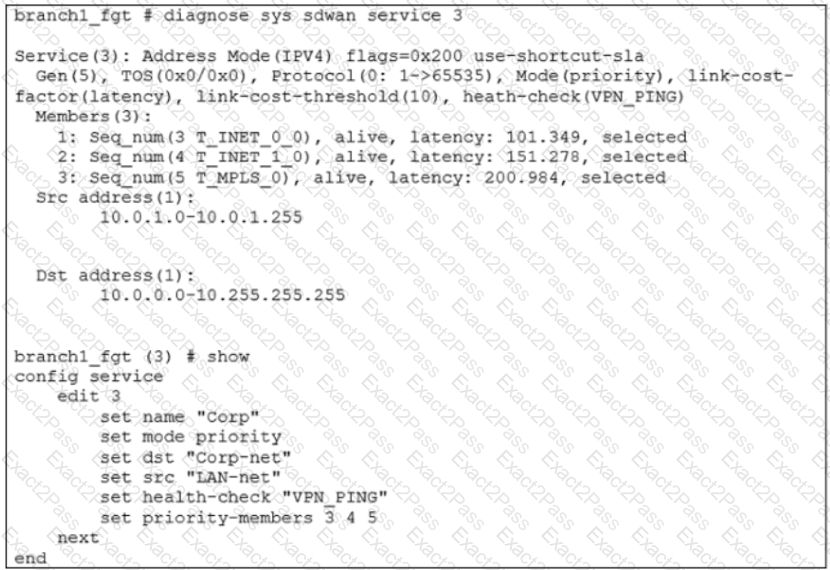
The exhibit shows the SD-WAN rule status and configuration.
Based on the exhibit, which change in the measured latency will make T_MPLS_0 the new preferred member?
Refer to the exhibit.
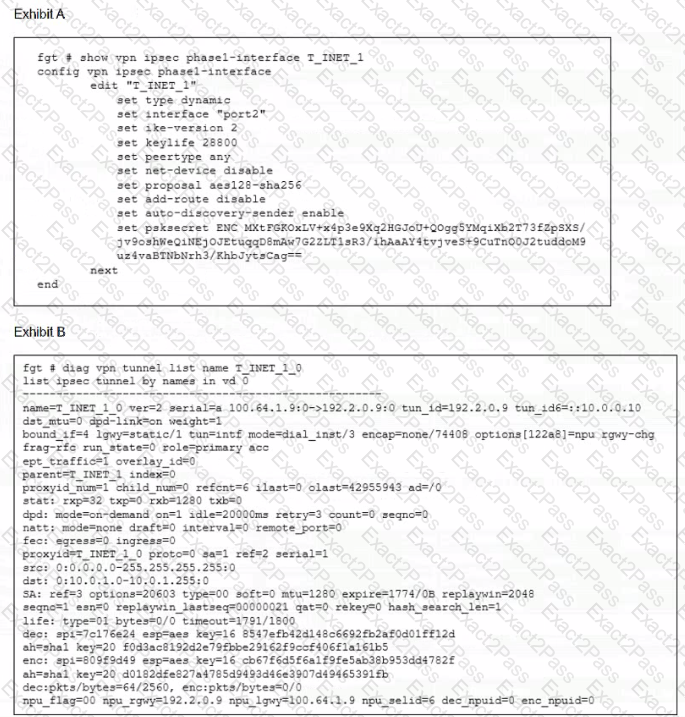
Which two statements about the IPsec VPN configuration and the status of the IPsec VPN tunnel are true? (Choose two.)
What are two advantages of using an IPsec recommended template to configure an IPsec tunnel in an hub-and-spoke topology? (Choose two.)
The SD-WAN overlay template helps to prepare SD-WAN deployments. To complete the tasks performed by the SD-WAN overlay template, the administrator must perform some post-run tasks. What are three mandatory post-run tasks that must be performed? (Choose three.)
Which two statements about the SD-WAN zone configuration are true? (Choose two.)
Refer to the exhibits.
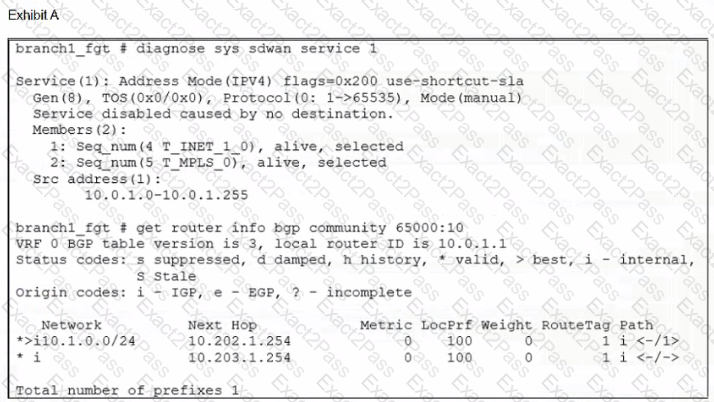
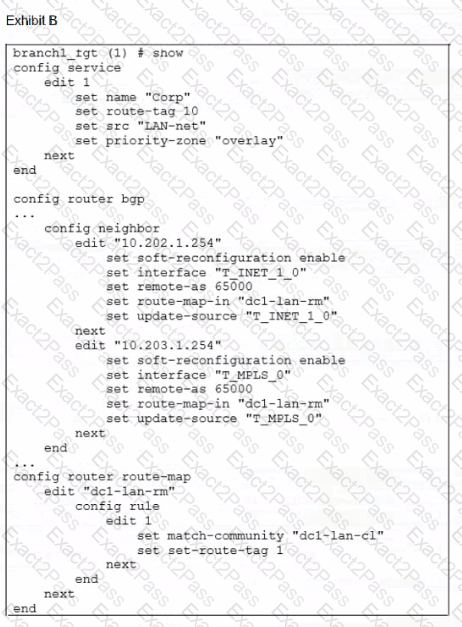
Exhibit A shows the SD-WAN rule status and the learned BGP routes with community 65000:10.
Exhibit B shows the SD-WAN rule configuration, the BGP neighbor configuration, and the route map configuration.
The administrator wants to steer corporate traffic using routes tags in the SD-WAN rule ID 1.
However, the administrator observes that the corporate traffic does not match the SD-WAN rule ID 1.
Based on the exhibits, which configuration change is required to fix issue?
Which two statements about SD-WAN central management are true? (Choose two.)
Refer to the exhibit.
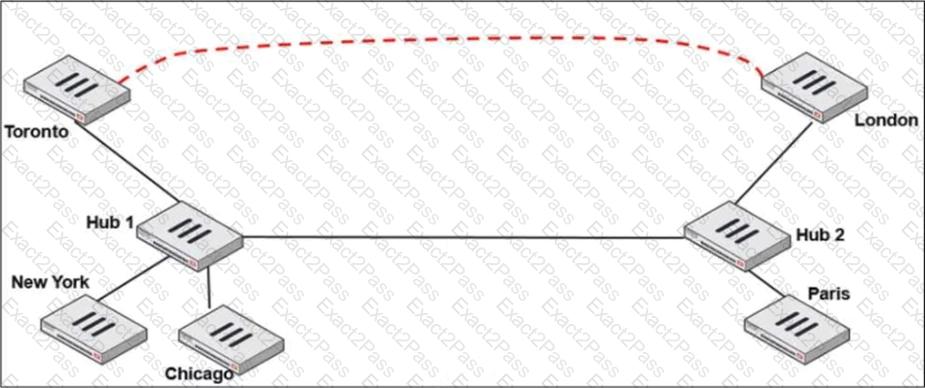
Two hub-and-spoke groups are connected through a site-to-site IPsec VPN between Hub 1 and Hub 2.
Which two configuration settings are required for Toronto and London spokes to establish an ADVPN shortcut? (Choose two.)
Refer to the exhibit.
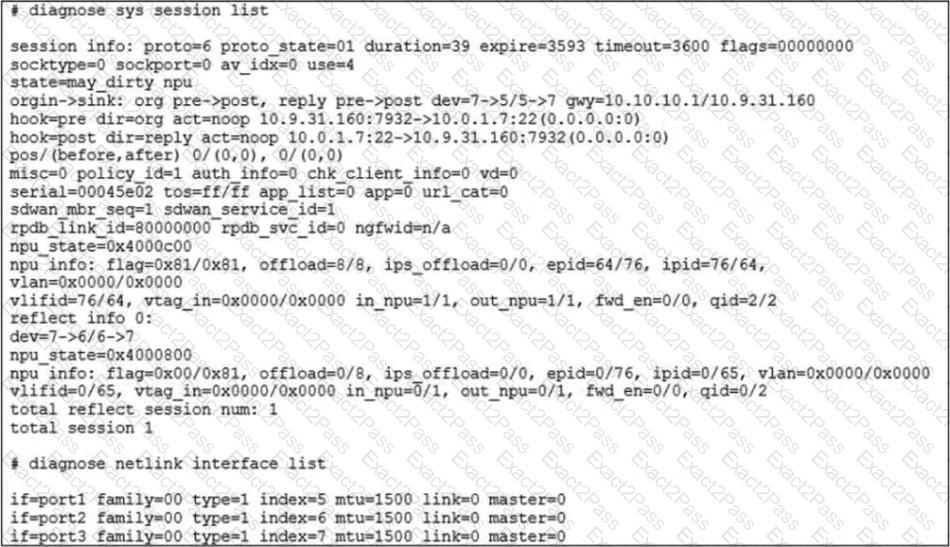
The exhibit shows the details of a session and the index numbers of some relevant interfaces on a FortiGate appliance that supports hardware offloading. Based on the information shown in the exhibits, which two statements about the session are true? (Choose two.)
Refer to the exhibits.
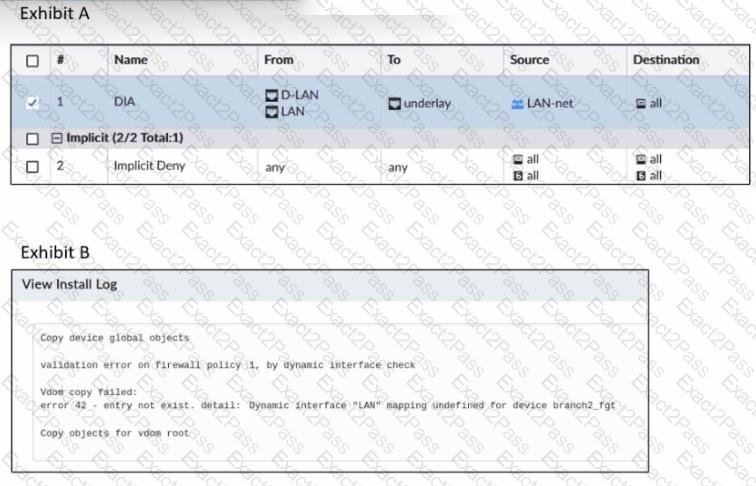
Exhibit A shows a policy package definition Exhibit B shows the install log that the administrator received when he tried to install the policy package on FortiGate devices.
Based on the output shown in the exhibits, what can the administrator do to solve the Issue?
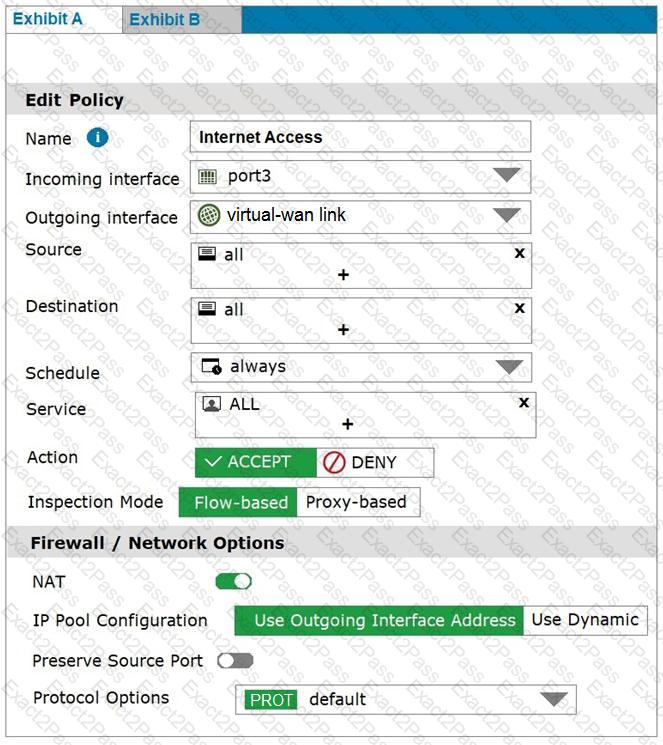
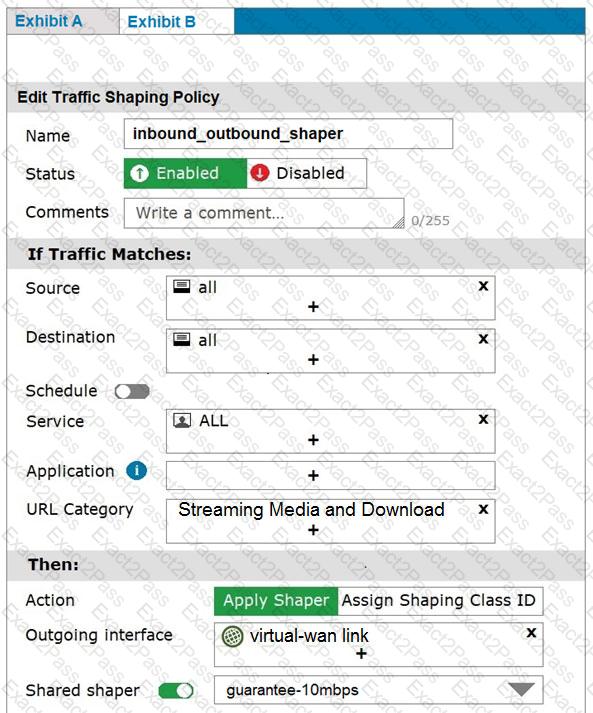
Exhibit A shows the firewall policy and exhibit B shows the traffic shaping policy.
The traffic shaping policy is being applied to all outbound traffic; however, inbound traffic is not being evaluated by the shaping policy.
Based on the exhibits, what configuration change must be made in which policy so that traffic shaping can be applied to inbound traffic?