Last Update 3 hours ago Total Questions : 59
The Fortinet NSE 7 Public Cloud Security 7.2 (FCSS) content is now fully updated, with all current exam questions added 3 hours ago. Deciding to include NSE7_PBC-7.2 practice exam questions in your study plan goes far beyond basic test preparation.
You'll find that our NSE7_PBC-7.2 exam questions frequently feature detailed scenarios and practical problem-solving exercises that directly mirror industry challenges. Engaging with these NSE7_PBC-7.2 sample sets allows you to effectively manage your time and pace yourself, giving you the ability to finish any Fortinet NSE 7 Public Cloud Security 7.2 (FCSS) practice test comfortably within the allotted time.
You need a solution to safeguard public cloud-hosted web applications from the OWASP Top 10 vulnerabilities. The solution must support the same region in which your applications reside, with minimum traffic cost
Which solution meets the requirements?
An administrator is looking for a solution that can provide insight into users and data stored in major SaaS applications in the multicloud environment Which product should the administrator deploy to have secure access to SaaS applications?
You are adding a new spoke to the existing transit VPC environment using the AWS Cloud Formation template. Which two components must you use for this deployment? (Choose two.)
An administrator decides to use the Use managed identity option on the FortiGate SDN connector with Microsoft Azure However, the SDN connector is failing on the connection What must the administrator do to correct this issue?
Refer to the exhibit
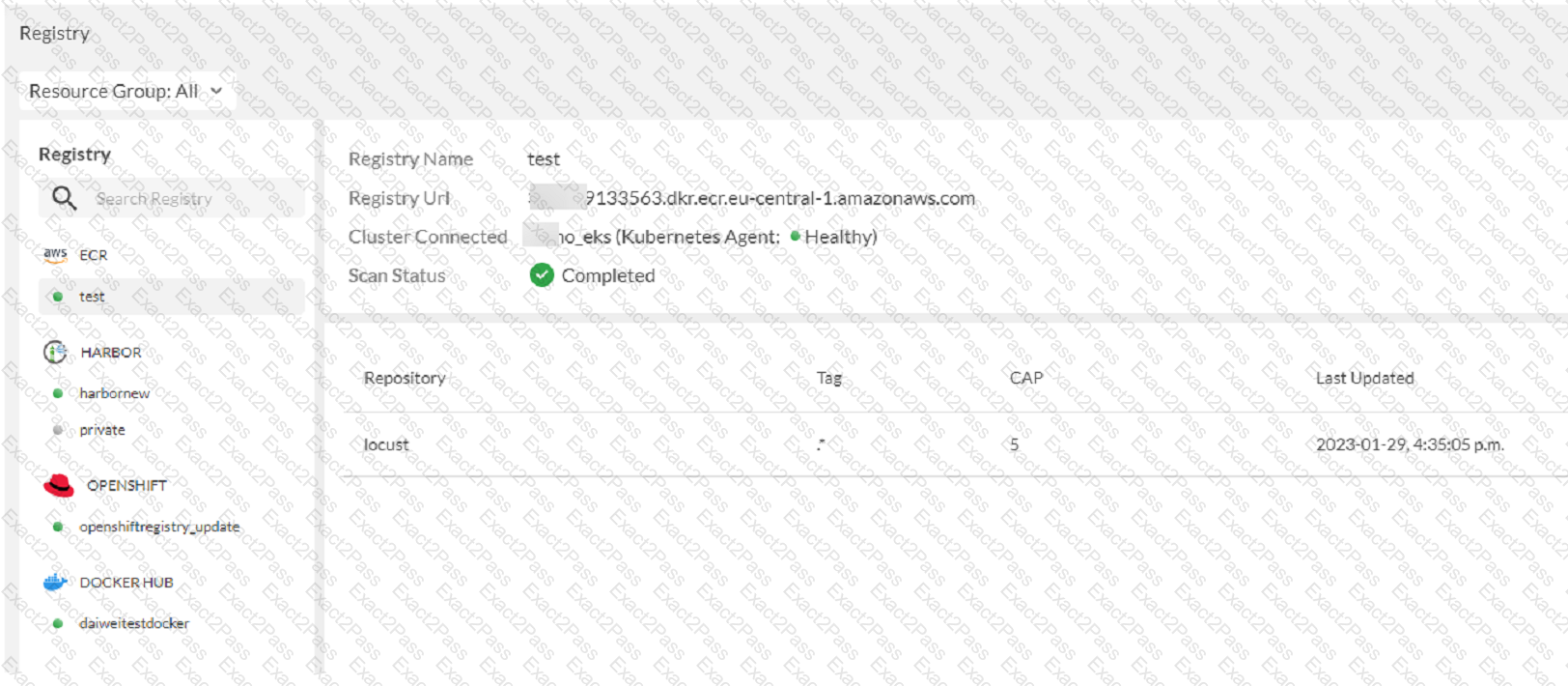
The exhibit shows the results of a FortiCNP registry scan
Which two statements are correct? (Choose two )
Your goal is to deploy resources in multiple places and regions in the public cloud using Terraform.
What is the most efficient way to deploy resources without changing much of the Terraform code?
What are two main features in Amazon Web Services (AWS) network access control lists (ACLs)? (Choose two.)

