Refer to the exhibit, and then answer the question below.

Which host is rogue?
Refer to the exhibit.
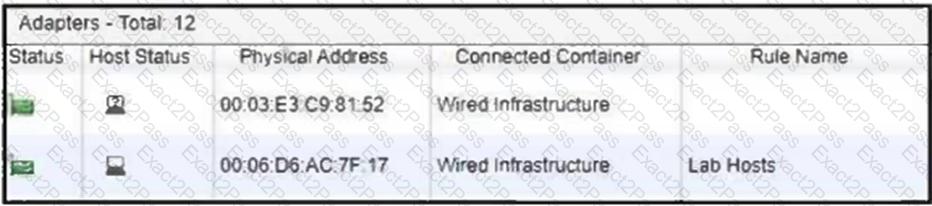
Considering the host status of the two hosts connected to the same wired port, what will happen if the port is a member of the Forced Registration port group?
Which three of the following are components of a security rule? (Choose three.)
View the command and output shown in the exhibit.

What is the current state of this host?
What would occur if both an unknown (rogue) device and a known (trusted) device simultaneously appeared on a port that is a member of the Forced Registration port group?
With enforcement for network access policies and at-risk hosts enabled, what will happen if a host matches a network access policy and has a state of "at risk"?
In an isolation VLAN which three services does FortiNAC supply? (Choose three.)
Which two policy types can be created on a FortiNAC Control Manager? (Choose two.)
By default, if more than 20 hosts are seen connected on a single port simultaneously, what will happen to the port?
Which two methods can be used to gather a list of installed applications and application details from a host? (Choose two.)
Where do you look to determine when and why the FortiNAC made an automated network access change?
Refer to the exhibit.
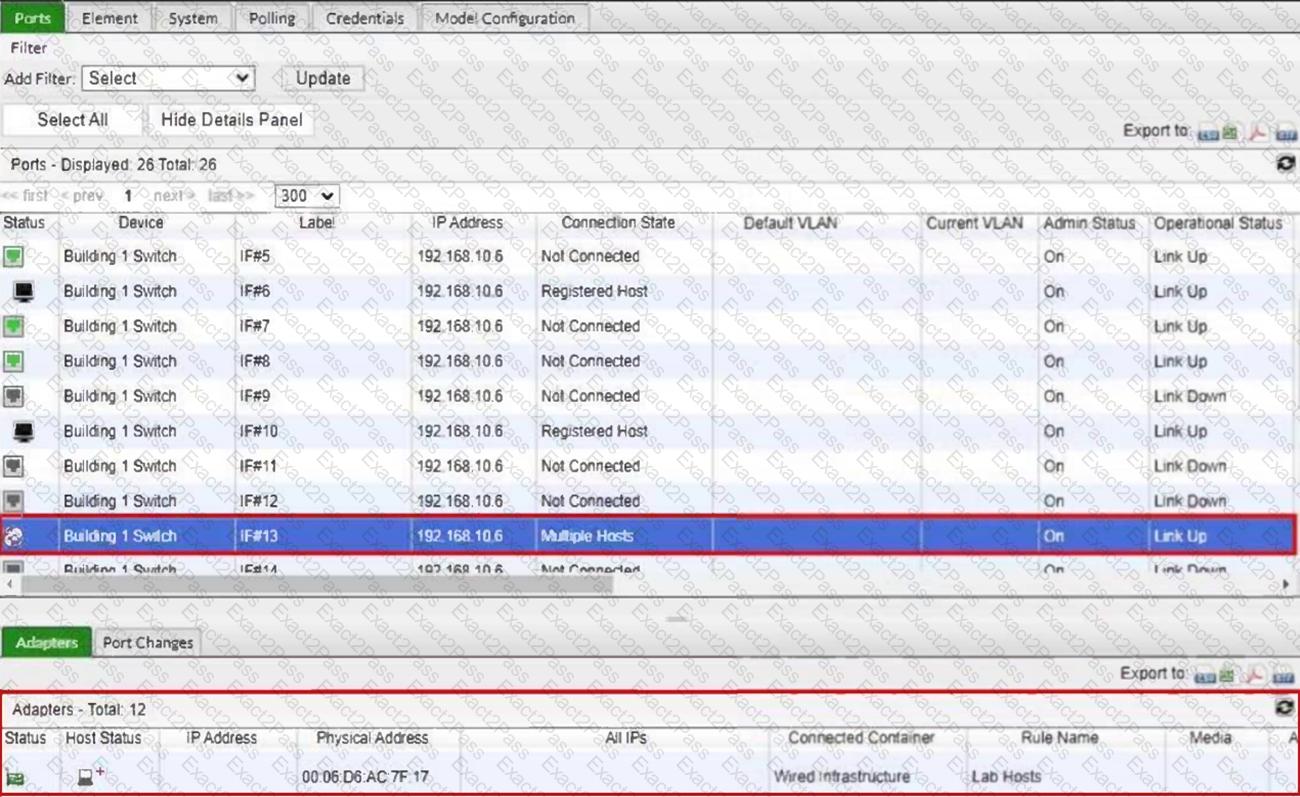
What would happen if the highlighted port with connected hosts was placed in both the Forced Registration and Forced Remediation port groups?