A customer is experiencing slow performance while executing long, adhoc analytic searches Which FortiSIEM component can make the searches run faster?
An administrator is using SNMP and WMI credentials to discover a Windows device. How will the WMI method handle this?
Which FortiSIEM components can do performance availability and performance monitoring?
Refer to the exhibit.
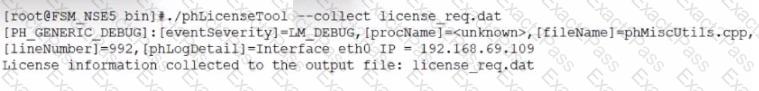
An administrator is investigating a FortiSIEM license issue.
The procedure is for which offline licensing condition?
Where do you configure rule notifications and automated remediation on FortiSIEM?
Which two FortiSIEM components work together to provide real-time event correlation?
When configuring collectors located in geographically separated sites, what ports must be open on a front end firewall?
An administrator wants to search for events received from Linux and Windows agents.
Which attribute should the administrator use in search filters, to view events received from agents only.