Last Update 13 hours ago Total Questions : 65
The Data Center Specialist (JNCIS-DC) content is now fully updated, with all current exam questions added 13 hours ago. Deciding to include JN0-480 practice exam questions in your study plan goes far beyond basic test preparation.
You'll find that our JN0-480 exam questions frequently feature detailed scenarios and practical problem-solving exercises that directly mirror industry challenges. Engaging with these JN0-480 sample sets allows you to effectively manage your time and pace yourself, giving you the ability to finish any Data Center Specialist (JNCIS-DC) practice test comfortably within the allotted time.
Exhibit.
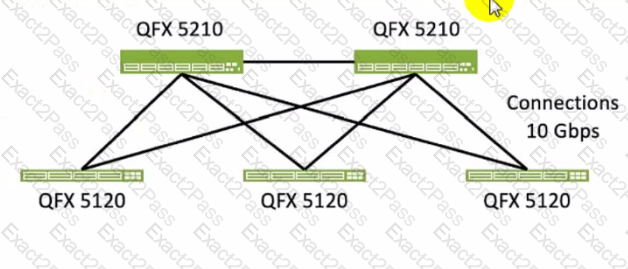
Referring to the exhibit, what needs to change in the IP fabric to make it a valid IP fabric?
When editing a device configuration to install some manual changes, which procedure should be followed?
Exhibit.
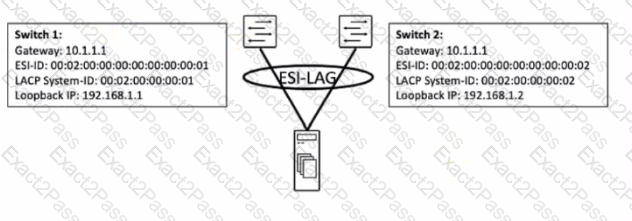
You are working to build an ESI-LAG for a multihomed server. The ESI-LAG is not coming up as multihomed.
Referring to the exhibit, what are two solutions to this problem? (Choose two.)
InJuniper Apstra. which three modes are available fordevices? (Choose three.)
Exhibit.
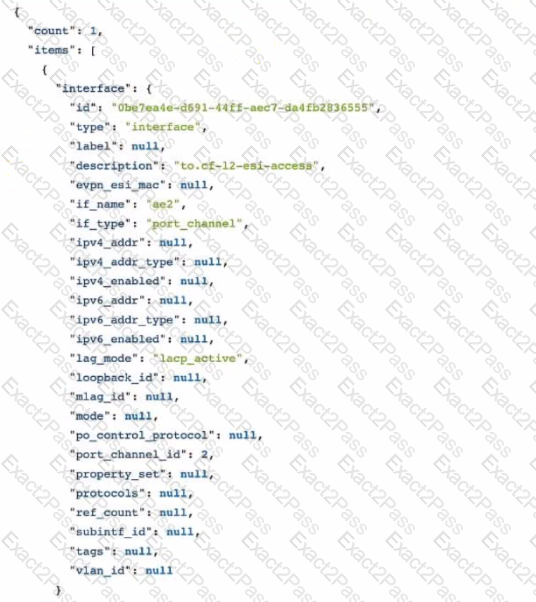
Which two statements ate correct about the graph query output shown in the exhibit? (Choose two.)
You use Juniper Apstra to enable a new VXLAN virtual network.
Which two components would be automatically derived in this situation? (Choose two.)
Which statement about Juniper Apstra role-based access control is correct?

