Click the Exhibit button.
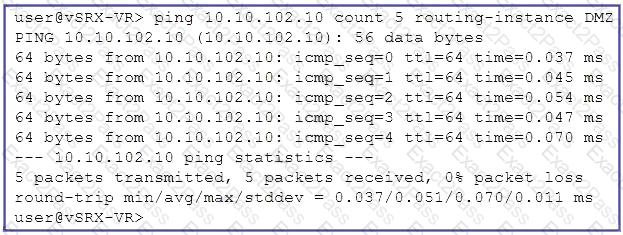
Referring to the exhibit, which two statements are correct about the ping command? (Choose two.)
Which two UTM features should be used for tracking productivity and corporate user behavior? (Choose two.)
When configuring antispam, where do you apply any local lists that are configured?
Which feature would you use to protect clients connected to an SRX Series device from a SYN flood attack?
What is the default timeout value for TCP sessions on an SRX Series device?
Which two features are included with UTM on an SRX Series device? (Choose two.)
Which statement is correct about global security policies on SRX Series devices?
What is the default value of the dead peer detection (DPD) interval for an IPsec VPN tunnel?
You need to collect the serial number of an SRX Series device to replace it. Which command will accomplish this task?
An application firewall processes the first packet in a session for which the application has not yet been identified.
In this scenario, which action does the application firewall take on the packet?
Which Juniper Networks solution uses static and dynamic analysis to search for day-zero malware threats?
Your company is adding IP cameras to your facility to increase physical security. You are asked to help protect these loT devices from becoming zombies in a DDoS attack.
Which Juniper ATP feature should you configure to accomplish this task?
You want to enable the minimum Juniper ATP services on a branch SRX Series device.
In this scenario, what are two requirements to accomplish this task? (Choose two.)
Exhibit.
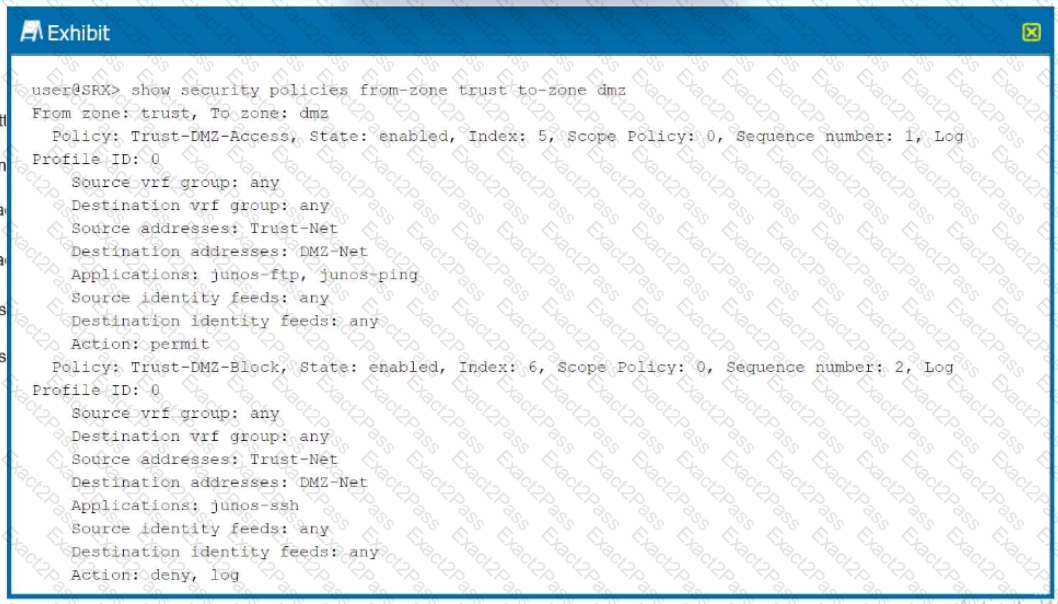
Which two statements are correct referring to the output shown in the exhibit? (Choose two.)