Which of the following is a task the Author is responsible for, as part of a typical formal review?
For each test case to be executed, the following table specifies its dependencies and the required configuration of the test environment for running such test case:
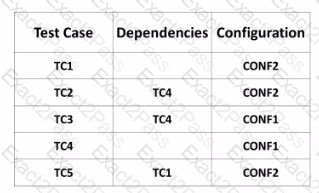
Assume that C0NF1 is the initial configuration of the test environment Based on this assumption, which of the following is a test execution schedule that is compatible with the specified dependencies and allows minimising the number of switches between the different configurations of the test environment^
An application is subjected to a constant load for an extended period of time as part of a performance test While running this test, the response time of the application steadily slows down, which results in a requirement not being met This slowdown is caused by a memory leak where the application code does not properly release some of the dynamically allocated memory when it is no longer needed. Which of the following statements is TRUE?
A state transition diagram describes a control system’s behavior in different operational modes. The initial state is“NORMAL MODE”.
Which ONE of the following test cases covers anINVALID sequence?
The following rules determine the annual bonus to be paid to a salesman of a company based on the total annual amount of the sales made (referred to as TAS).
If the TAS is between 50k€ and 80k€, the bonus is 10%. If the TAS exceeds 80k€ by a value not greater than 40k€, the bonus is 15%. Finally, if the TAS
exceeds the maximum threshold which entitles to a 15% bonus, the bonus is 22%.
Consider applying equivalence partitioning to the TAS (Note: 1k€ = 1000 euros).
Which one of the following answers contain only test cases that belong to the same equivalence partition?
Which of the following statements is incorrect regarding the involvement of testers in the software development lifecycle (SDLC)?
Consider the following testing levels:
1) Component Testing
2) Integration Testing
3) System Testing
4) Acceptance Testing
Which of the following statements is true?
Which of the following statements about static testing and dynamic testing is TRUE?
Which or the following would be a key difference between a peer review of code and static analysis of code using a tool?
Testing Quadrants, as a model, is effective in aligning stakeholders within Agile teams.
Which of the following examples demonstrates this?
Which of the following BEST matches the attributes with a level of testing?
I. Stubs and drivers are often used
II The lest environment should correspond to the production environment
III Finding defects is not the main focus
IV Testing can be based on use cases
V Testing is normally performed by testers
VI Testing for functional and non-functional characteristics
Which ONE of the following work products TYPICALLY belongs to test execution?
Consider the following examples of risks identified in different software development projects:
[I]. The contrast color ratio for both normal text and large text of a website does not comply with the applicable accessibility guidelines, making it difficult for many users to read the content on the pages
[II]. A development vendor fails to deliver their software system on time, causing significant delays to system integration testing activities that have been planned as part of a development project for a system of systems
[III]. People in the test team do not have sufficient skills to automate tests at the test levels required by the test automation strategy which does not allow production of an effective regression test suite
[IV]. In a web application, data from untrusted sources is not subject to proper input validation, making the application vulnerable to several security attacks
Which of the following statements is true?
As the last stage of a test cycle of an embedded device, you are performing exploratory testing. You observed that some character. (A, X andZ)sent via a serial port to the device do not get registered on the device whereas they should be. You suspect that this could be due to a wrong configuration of the "bit parity" parameter.
Which of the following items of an incident report would you beUNABLEto write down based on this information?
Given the following requirement:
Requirement ID: 2 8
Requirement Description Additional Entrance Fee
Detailed Description
An additional fee of S3 is charged during the weekend, but
1) Visitors aged under 7 are not charged.
2) Visitors aged 7 to 13 inclusive get a 20% discount off the additional fee.
3) Visitors aged greater than 65 get a 50% discount off the additional fee.
Age should be an integer of 0 or above.
Weekend means Friday to Sunday inclusive.
Which of the following statements isNOTcorrect?
During iteration planning, a scrum team uses an estimation technique called planning poker to estimate the effort required to deliver a critical user story. In advance of the estimation session, the team agreed on some ground rules to limit the number of poker rounds and save time.
The team agreed on the following:
1. They will use the following progression for estimation: Extra-small, Small, Medium, Large, Extra-large, and Extra-extra-large.
2. If estimation values differ significantly, the highest score will be used for estimation purposes.
The result of the first round of planning poker:
Team MemberEstimation
BusinessLarge
DevelopmentExtra-extra-large
TestingExtra-extra-large
Which of the following options best represent the team’s next actions?
Consider the followingiteration planning taskswhere a tester can provide value:
Break down user stories into tasks (particularly testing tasks)
Estimate test effort for all testing tasks
Identify and refine functional and non-functional aspects of the test object
Which ONE of the following tasks should be ADDED to the above list?
Which ONE of the following options CORRECTLY describes one of the seven principles of the testing process?
A software module to be used in a mission critical application incorporates an algorithm for secure transmission of data.
Which review type is most appropriate to ensure high quality and technical correctness of the algorithm?
Which of the following tasks is MOST LIKELY to be performed by the tester?
An alphanumeric password must be between 4 and 7 characters long and must contain at least one numeric character, one capital (uppercase) letter and one lowercase letter of the alphabet.
Which one of the following sets of test cases represents the correct outcome of a two-value boundary value analysis applied to the password length? (Note: test cases are separated by a semicolon)
Which of the following BEST distinguishes the terms "validation" and "verification"?
Which of the following statements about testing in the context of an agile (iterative-incremental) development model is correct?
Which ONE of the following options MOST ACCURATELY describesbranch testing?
The following 4 equivalence classes are given:
Which of the following alternatives includes correct test values for x. based on equivalence partitioning?
Which of the following statements about the value of maintaining traceability between the test basis and test work products is not true?
Which ONE of the following statements about acceptance testing isNOTcorrect?
A mid-size software product development company has analyzed data related to defects detected in its product and found out that detects fixed in earlier builds are getting re-opened after a few months.
The company management now seeks your advice in order to reverse this trend and prevent re-opening of defects fixed earlier.
What would be your FIRST recommendation to the company?
A class grade application for instructors assigns letter grades based on students' numerical grades.
The letter grades for different numerical grades should be:
Above 89, up to 100 - A
Above 79, up to 89 • B
Above 69, up to 79 • C
Above 59, up to 69 - D
Below 60- F
Which of the following sets of test inputs would achieve the relatively highest equivalence partition coverage?
Which of the following is the BEST reason for selecting a particular type of software development lifecycle model?
Given the following state model of sales order software:
PLACED -> IN PRODUCTION
IN PRODUCTION -> CANCELLED
IN PRODUCTION -> SHIPPED
SHIPPED -> INVOICED
INVOICED -> CANCELLED
CANCELLED -> PLACED
Which of the following sequences of tran-sitions provides the highest level of tran-sition coverage for the model (assuming you can start in any state)?
Which of the following is a factor that contributes to a successful review?
Use Scenario 1 “Happy Tomatoes” (from the previous question).
Using theBoundary Value Analysis (BVA)technique (in its two-point variant), identify the set of input values that provides the HIGHEST coverage.
Following a risk-based testing approach you have designed 10 tests to cover a product risk with a high-risk level. You want to estimate, adopting the three-point test estimation technique, the test effort required to reduce the risk level to zero by executing those 10 tests. You made the following three initial estimates:
• most optimistic = 6 person hours
• most likely = 30 person hours
• most pessimistic = 54 person hours
Based only on the given information, which of the following answers about the three-point test estimation technique applied to this problem is true?
Which ONE of the following options corresponds to an activity in the testing process in which testable features are identified?
A test manager defined the following test levels in her test plan; Component, System and Acceptance.
Which Software Development lifecycle is the Test Manager most likely following?
Manager responsibilities in formalreview includes adexceptone of the following:
A company wants to reward each of its salespeople with an annual bonus that represents the sum of all the bonuses accumulated for every single sale made by that salesperson. The bonus for a single sale can take on the following four values: 3%, 5%, 7% and 10% (the percentage refers to the amount of the single sale). These values are determined on the basis of the type of customer (classified as "Basic" or "Premium") to which such sale was made, and on the amount of such sale classified into the following three groups G1, G2 and G3:
• [G1]: less than 300 euros
• [G2]: between 300 and 2000 euros
• [G3]: greater than 2000 euros
Which of the following is the minimum number of test cases needed to cover the full decision table associated with this scenario?
Which of the following activities does NOT belong to a typical technical review?
A software application incorrectly provided customers discounts of 50% off their total purchases if the purchases exceeded S100. It was discovered through an audit that the discount should have been only 5% off these purchases. A root cause analysis uncovered that the requirements Incorrectly stated 50% instead of 5% in this scenario.
Which of the following MOST accurately reflects this scenario?
A Static analysis tool analyzes a given program's CONTROL FLOW among other things. Which of the following options represents the most likely outcome of the control flow analysis:
Which ONE of the following options BEST describes thethird test quadrant (Q3)?
Given the following state model of sales order software:
PLACED -> IN PRODUCTION
IN PRODUCTION -> CANCELLED
IN PRODUCTION -> SHIPPED
SHIPPED -> INVOICED
INVOICED -> CANCELLED
CANCELLED -> PLACED
Which of the following sequences of transitions provides the highest level of transition coverage for the model (assuming you can start in any state)?
In Agile teams, testers closely collaborate with all other team members. This close collaboration could be problematic and result in testing-related organizational risks.
Which TWO of the following organization risks could be encountered?
I.Testers lose motivation and fail at their core tasks.
ii.Close interaction with developers causes a loss of the appropriate tester mindset.
iii.Testers are not able to keep pace with incoming changes in time-constrained iterations.
iv.Testers, once they have acquired technical development or business skills, leave the testing team.
Who of the following has the best knowledge to decide what tests in a test project should be automated?
In addition to thorough testing of the requirements specification, a development team aims to involve users as early as possible in the development process, using practices such as prototyping, to ensure that the software systems being developed will meet the users' expectations. This approach is especially useful at mitigating the risks associated with one of the seven testing principles, which one?
Given the following review types and review characteristics:
a.Pair review
b.Walkthrough
c.Technical review
d.Inspection
1.Formal
2.Informal
3.Purposes include evaluating the quality of the work product under review and generating new ideas (e.g., brainstorming solutions)
4.Purposes include Improving the software product and training the review participants
Which of the following BEST matches the review type with the review characteristic?
Which of the following is a possible reason for introducing a defect in software code?
A QA manager of a start-up company needs to implement within a week a low cost incident management tool. Which of the following is the best option?
Use Scenario 1 “Happy Tomatoes” (from the previous question).
When running test caseTC_59, the actual result fort = 35degrees Celsius isOUTPUT = Xinstead of the expected output.
Which information should NOT be included in the defect report?
The following requirement is given “Set X to be the sum of Y and Z”.
All the following four implementations have bugs.
Which one of the following bugs can be caught by Static Analysis?
Which of the following statements refers to a good testing practice that applies to all software development lifecycles?
Which sequence of state transition stated in the answer choices is correct in accordance with the following figure depicting me life-cycle of a defect?

Which of the following work products cannot be examined by static analysis?
You are responsible for applying the correct technique for a review of the requirements document for a project to develop a new software application. You identify the reviewers and the required roles, including the meeting leader, who is the requirements document author, and a separate role for a scribe. Additionally, you decide to take a relatively informal approach to the requirements review. The goal of the review is to find defects in the requirements document, such as omissions, Inconsistencies, and duplications. Another goal of the review is to improve the software application's usability and accessibility by considering the various stakeholders' viewpoints.
Which of the following statements BEST describes this scenario?
Select which of the following statements describe the key principles of software testing?
i. Testing shows the presence of defects, not their absence.
ii. Testing everything Is possible.
iii. Early testing Is more expensive and is a waste of time.
iv. Defects cluster together.
v. Testing is context dependent.
vi. Beware of the pesticide paradox.
vii. Absence of errors is a fallacy.
Select the correct answer:
Which of the following activities are part of test planning?
I) Setting the entry and exit criteria
II) Determining the validity of bug reports
III) Determining the number of resources required
IV) Determining the expected result for test cases
Which of the following statements is the BEST example of non-functional testing?
The ISTOB glossary defines Quality Assurance as: "Pail or quality management focused on providing confidence that quality requirements will be fulfilled. Which of the following Is not one of the Quality Assurance activity?
Which of the following best describes the relationship between a test progress report and a test summary report?
Which of the following provides the BEST description of statement coverage?
You are testing a system that is used in motor vehicles to warn the driver of an obstacle when re-versing. Output is provided by a series of LED lights (green, yellow, and red), each illuminated based on clearly defined conditions.
The following summary describes the functionality:
•Object within 10 metres, green LED lit.
•Object within 5 metres, yellow LED lit.
•Object within 1 metre, red LED lit.
•Setting sensitivity mode to "ON" will result in only the red LED being lit when the object is within 1 metre.
The following decision table describes the rules associated with the functioning of this proximity warning system:

Which intended functionality is tested by Rule 5 in the decision table?
Which statement is true regarding confirmation testing and regression testing?
You are testing the latest version of an air-traffic control system prior to production deployment using exploratory testing. After following an unusual sequence of input steps,the system crashes. After the crash, you document a defect report with the following information:
•Title: System crashes unexpectedly during input.
•Brief summary: System crashes when an unusual sequence of inputs is used.
•Version: V1.001
•Test: Exploratory testing prior to production deployment
•Priority: Urgent
•Risk: High
•References: Screenshot of crashed application
What critical Information Is missing from this report?
The following open incident report provided:
Date: 01.01.01
Description: When pressing the stop button the application status remain in "Attention" instead of "Ready'.
Severity: High
Life Cycle: Integration
Which of the following details are missing in the giving incident report?
I. Identification or configuration of the application
II. The name of the developer
III. Recommendation of the developer
IV The actions and/or conditions that came before the pressing of the button
Which of the following statements about decision tables are TRUE?
I. Generally, decision tables are generated for low risk test items.
II. Test cases derived from decision tables can be used for component tests.
III. Several test cases can be selected for each column of the decision table.
IV. The conditions in the decision table represent negative tests generally.
Which of the following is an INCORRECT statement about the benefit of traceability between the test basis and test work products?
Which ONE of the following options identifies the perspectives through which acollective authorship processgenerates a shared vision of user stories?
Which of the following applications will be the MOST suitable for testing by Use Cases
After being in operation for many years, a document management system must be decommissioned as it has reached its end of life. This system will not be replaced by any other new system. A legal obligation provides that all documents within the system must be kept for at least 20 years in a state archive. Which of the following statements about maintenance testing for decommissioning of this system is TRUE?