Review the current identity model and scenario below.
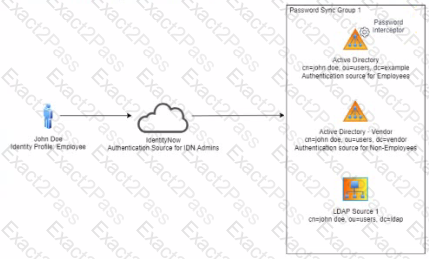
Scenario
John Doe requests "Sales" access on Salesforce for himself. In the approval process, John Doe's manager approves. The access request is tils the expected provisioning action sent to the source connectors?
Solution: Expected Provisioning No provisioning is sent out.
An IdentityNow engineer has the following problem:
IdentityNow shows status failed on a virtual appliance (VA).
Is this one of the steps that should be taken troubleshoot the issue?
Solution: Review the log files in /home/sailpoint/log for errors.
When preparing for a manager certification campaign is this a step that is considered a best practice before the campaign preview is generated?
Solution: Evaluate available campaign administration filters
An IdentityNow engineer needs to find identities with disabled AD accounts by using IdentityNow's search features. Is this the correct search syntax to perform this task?
Solution:
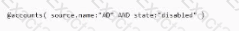
Is the following true about custom connectors in IdentityNow?
Solution: Custom connector configurations can have account correlation settings defined.
Is this an item that an IdentityNow engineer should configure when implementing a source that uses a JDBC connector?
Solution: Use a query select statement with a clause to match the incoming account to an existing account for the Single Account SQL Query configuration item
Is the following true about the web-services connector in IdentityNow?
Solution: The connector supports SAML authentication.
In an IdentityNow environment, the source lest connection is failing with a timeout error.
Is this a step an identityNow engineer should take to troubleshoot the problem?
Solution: Turn off the virtual appliance's (VA) internal firewall.
The customer has a system that matches the following description. Is this a suitable connector type to use?
The system is a modern, cloud-based, web application that uses a MySQL database backend provided by the cloud platform. The database is only accessible from the web application. The web application exposes a fully compliant SCIM 2.0 interface with OAuth 2.0 client credentials.
Solution: OpenLDAP Connector
Is this an item that an IdentityNow engineer should configure when implementing a source that uses a JDBC connector?
Solution: Select the checkbox to use database admin as service account.
Is this an appropriate use case for the Build Map?
Solution: To provide the ability to modify to modify the map data of an account for a JDBC or a Delimated File source.
Does this correctly describe Manager Correlation?
Solution: an approval process by which identifies assigned as manager must periodically review and approve all access assigned to their employees.
An IdentityNow engineer has set up an access profile for an application. The access profile allows for users to request access, and for a user's manager to approve or deny access.
After a recent staff meeting, management has expressed that they want to remove any approval requirements for this application.
Is management's request possible in IdentityNow. and. if so. are these the recommended steps the engineer should take to meet their new requirement?
Solution: It is possible. Delete the access profile.
Is this an item that an IdentityNow engineer should configure when implementing a source that uses a JDBC connector?
Solution: Define an account schema by using 'Discover Schema'' or by manually configuring the schema attributes.
A customer wants to configure a virtual appliance (VA) to use a static IP address. Does this file on the VA need to be modified to perform the configuration?
Solution: /home/sailpoint/proxy.yaml
Refer to the following diagram.
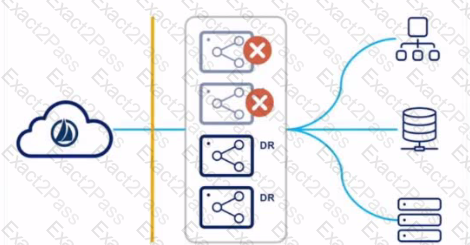
For this strategy, all virtual appliances (VAs) are deployed in a single VA cluster, with all VAs running concurrently. Some of these VAs are in the primary data center, and others {called OR VAs) are deployed in a DR data center.
While using this strategy, is this a disadvantage?
Solution: A reconfiguration will be required within identityNow to connect to the disaster recovery VAs. If there are many sources configured, this will cause overhead in performing this failover
An engineer needs to troubleshoot the following issue:
Incomplete Identities on authoritative source
Is this a reasonable action for the engineer to take?
Solution: Download the identity Exceptions report from the identity profile page.
Is this statement true about certification campaigns?
Solution: Certifications are assigned to the reviewer when the campaign status is Preview Ready.
In an IdentityNow environment, the source lest connection is failing with a timeout error.
Is this a step an identityNow engineer should take to troubleshoot the problem?
Solution: Clear the Authentication checkbox for the source in identityNow.
In an IdentityNow environment, the source lest connection is failing with a timeout error.
Is this a step an identityNow engineer should take to troubleshoot the problem?
Solution: Check that port values configured on the identityNow source are connected for the source.
Does this example accurately describe an IdentityNow data flow?
Solution:
1. Identity data is aggregated from an authoritative source.
2. The aggregated data is used to build an identity model.
3. Accounts are provisioned to source systems.
4 Identity attributes are periodically synchronized to write-enabled systems
In an optimized aggregation, if an account is unchanged since the last aggregation, does this step execute?
Solution: The virtual appliance connects to the target system to retrieve accounts.
An engineer needs to troubleshoot the following issue:
Incomplete Identities on authoritative source
Is this a reasonable action for the engineer to take?
Solution: Download the accounts data csv from the Account tab on the authoritative source.
Is this statement correct about security and/or encryption of data?
Solution: When setting up a virtual appliance cluster. SailPoint creates an asymmetnc key pair based on a user-provided passphrase. and then uses this key pair to communication with the IdentityNow tenant.
Is this statement accurate regarding SailPoint's multi-tenant processing environment?
Solution: A proprietary fairness algorithm is used to manage and distribute the workload.
Review the steps.
1______________________________________
2. Import the virtual appliance (VA) image to the virtualization platform.
3. Start the VA.
4. Log in to the VA using the default credentials.
5. Change the password for the SailPoint user.
6______________________________________
7. Create a new VA cluster in IdentityNow.
8. Create a new VA configuration in IdentityNow. 9 Download / procure the config.yaml.
10. Configure the keyPassphrase in the config.yaml.
11. Upload the config.yaml into the VA.
12______________________________________.
Are these the missing steps?
Solution: 1. Click Test Connection on the VA configuration. 6. Download / procure the VA image. 12. Configure networking configurations (as needed).
When preparing for a manager certification campaign is this a step that is considered a best practice before the campaign preview is generated?
Solution: validate the email template. Certification Due
A customer wants to configure a virtual appliance (VA) to use a static IP address. Does this file on the VA need to be modified to perform the configuration?
Solution: /etc/ systemd/network/ static, network