A client needs a custom quicklink, which only managers can launch, in order to launch a simple workflow. Is this a valid step to take during the development of this custom quicklink?
Solution: Enter the name of the workflow to launch in the quicklink object.
An engineer is developing an instance of IdentitylQ using the Services Standard Build (SSB) for a client. Is this a valid action the engineer can perform when setting up or using the SSB?
Solution:Place the patch jar file in the build's base/patch folder that matches the patch version the client is using
Is this a benefit of using the Run Rule feature of the Debug-Object page?
Solution: It can be used to create/modify/delete SailPoint database objects.
Is the following statement about workflow step types and their usage true?
Solution:When a wait step is encountered in a foreground workflow, the user will notice this, because the screen will freeze for the specified number of seconds.
Is this a default functionality of the Lifecycle Manager (LCM) module?
Solution:Terminate Identity
An organization is making a change at the regional level.
Many users of a financial system have incorrect entitlements. Some users are missing entitlements, and some users have excess entitlements. Work needs to be performed to clean up access.
Is this one of the IdentuylQ batch request types that can help meet this goal?
Solution:Delete Entitlement
Is this a valid statement about connector rules?
Solution: A Post-Iterate Rule, if configured, is run after reading accounts from a SQL Loader application.
Can the search type in Syslog be used to accomplish this result?
Solution:Identifying all Link objects from a particular application
A client needs a custom quicklink, which only managers can launch, in order to launch a simple workflow. Is this a valid step to take during the development of this custom quicklink?
Solution:Place a quicklink object on the workflow that is to be launched
Is this a purpose of an IdentitylQ certification?
Solution:to certify user expense reports
A bank is two years into an ongoing project to provide all access through roles. The bank is actively using roles and actively adding to their role model. They need to ensure that all roles include the correct entitlements.
Will this certification type achieve the goal?
Solution:Role Composition Certification
Is this statement true about identitylQ's syslog event storage?
Solution:IdentitylQ logging and auditing both require extra function calls within the application and will generate data that can be compressed to avoid any storage and Improve overall performance.
An engineer is assigned to configure an account attribute. The requirements are:
Purpose: Flag privileged accounts
Read from: Financial application, privileged attribute
Calculate from: Keystore application, responsibility-code attribute
Usage 1: Display as option in Advanced Analytics
Usage 2: Use when writing rules
Usage 3: Include in policies
Does the engineer need to set this configuration option on the account attribute to meet the requirements?
Solution: Source Mappings: Application Rule
Is this a purpose of an IdentitylQ certification?
Solution: to attest to a user's integrity
Can the Provisioning tab under "Administrator Console' be used to do the following task?
Solution:Map the associated WorkflowCase to a particular Provisioning Transaction.
How should an engineer schedule the tasks to most efficiently achieve the following goals?
Goals:
• Process the Employee Authoritative application at 5:00 AM and 12:00 PM.
• Process the Contractor Authoritative application at 5:10 AM and 12:10 PM.
• Process the Active Directory application at 5:20 AM and 12:20 PM.
• Process the Finance application at 8:00 PM.
• Check for expired work items at 12:00 AM.
• Perform identity request maintenance at 2:00 AM.
Schedule parameters:
• Each application aggregation takes anywhere between 30 minutes and 2 hours.
• The run schedule is for a 24-hour period, which begins at 12:00 AM.
Instructions:
• Drag the required tasks from the left into the answer area on the right, and place them in the correct order, starting at 12:00 AM.
• Ordinal numbers (such as 1st, 2nd, and 3rd) in the options indicate which run of the day it is for the task type.
• There will be unused task options.
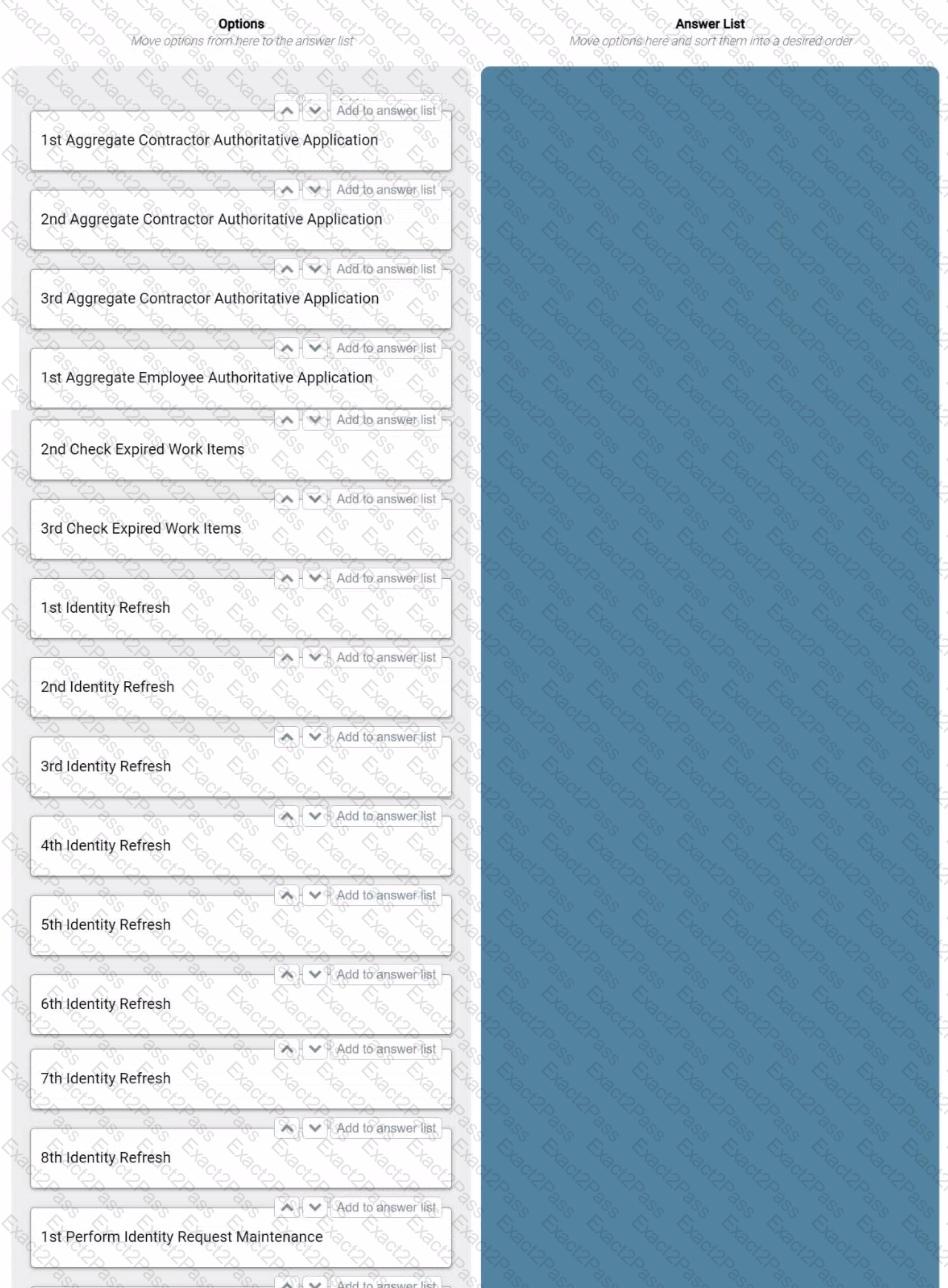
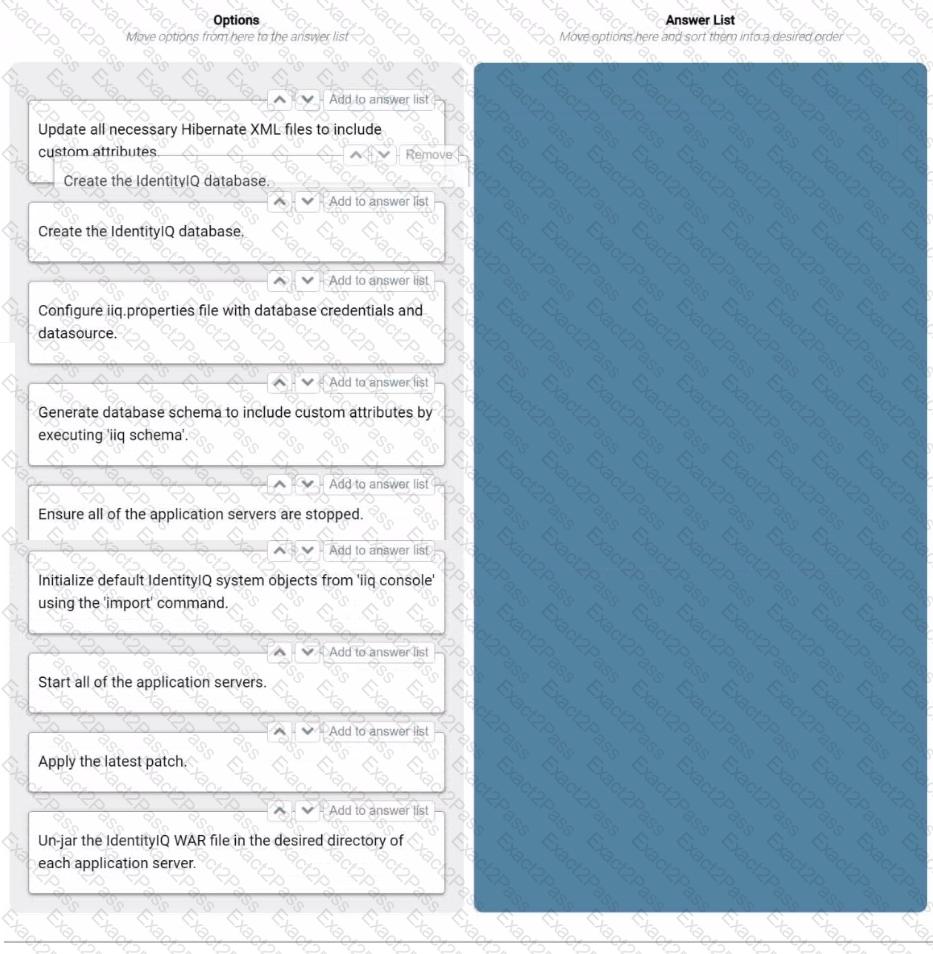
An implementation engineer needs to perform an initial installation of identitylQ.
Drag the options from the left into the answer area on the right, and place them in the correct order.
Can a Workgroup be used for the following scenario?
Solution: Providing a group of users with specific capabilities.
Is this an example of a mover lifecycle event?
Solution:An employee quits their job and needs all of their accounts disabled.
Is this a purpose of an IdentitylQ certification?
Solution:to attest lo a user's system access
Can the search type in Syslog be used to accomplish this result?
Solution: Identifying the number of employees that report to a specific person
A manager wants to extend the access granted to an employee.
Is this a default role type that is available for the manager to request in IdentitylQ during the access request process?
Solution: Business Role
Is this statement true about certifications?
Solution:All certifications include generation, the active period, sign-off, and the end period.
Is this statement valid regarding the control and usability of the Debug pages in IdentitylQ?
Solution:The application server must be restarted after reloading the logging file through the Debug-Logging page.
An engineer needs to first create a custom audit event and then set up an associated report. What are four steps to accomplish this goal?
Solution:

Is this statement valid regarding the control and usability of the Debug pages in IdentitylQ?
Solution:The current version and patch level of IdentitylQ can be found through the Debug-About page.
Is this a true statement about localization support in IdentitylQ?
Solution:The default language can be changed from English by replacing the appropriate message files.
An implementation engineer needs to perform an upgrade of IdentitylQ between releases. Is the following statement true?
Solution:Supported platforms of an older version of IdentitylQ will always be supported in newer versions of IdentitylQ.
Is this statement true about identitylQ's syslog event storage?
Solution:Both logging and auditing can have a negative influence on performance. Logging and auditing both require extra function calls within The application and will generate data that will need to be stored.
Can an Escalation Rule be used to handle this scenario?
Solution: Automatically reassign parts of an access review to a different certifier.
Is this a correct procedure for testing generated emails in a non-production system?
Solution: Change the Email Notification Type to POP3 under Global Settings > Configure IdentitylQ Settings > Mail Settings, run the test scenario. and verity if the emails were successfully delivered to mailboxes specified on Identity objects.
Is this statement correct about writing and executing source mapping rules to populate identity attributes?
Solution:The Identity object is passed to the rule.
Can the following action be performed using Rapid Setup application onboarding?
Solution: Specify account correlation using a rule.