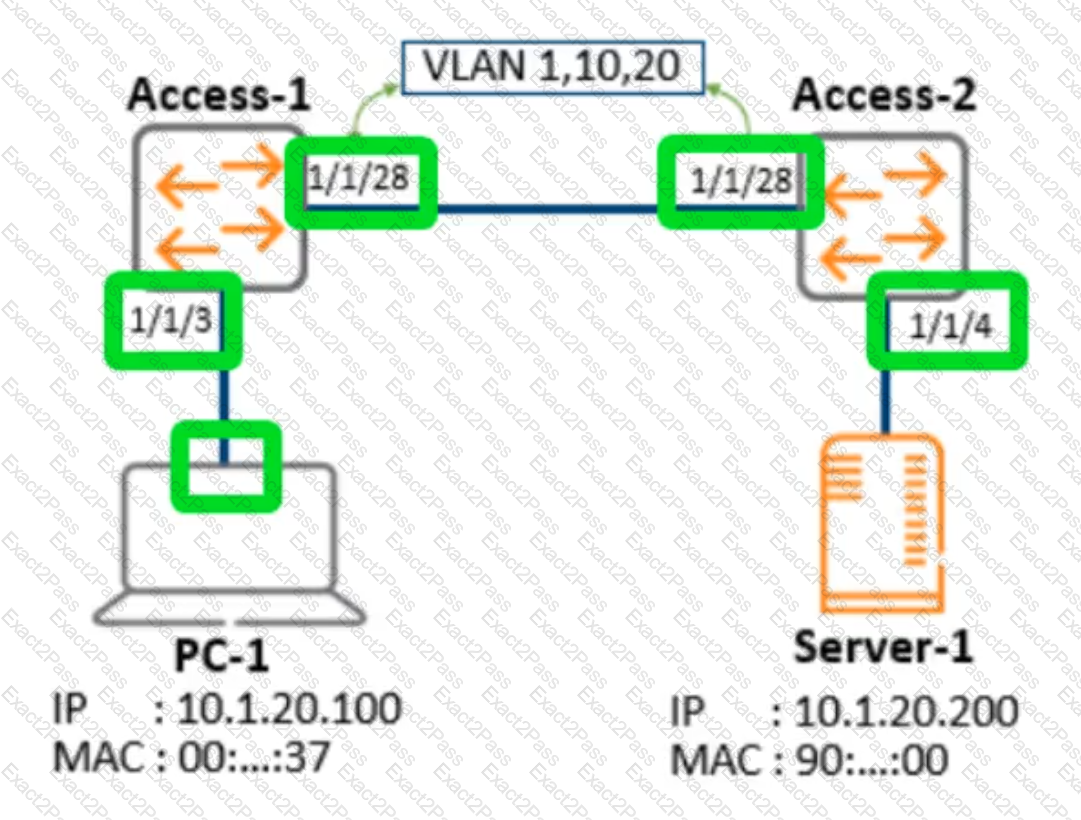
You have completed a successful VSF stack between two switches.
Without manually assigning a backup switch, what is the expected output when issuing a show vsf command?
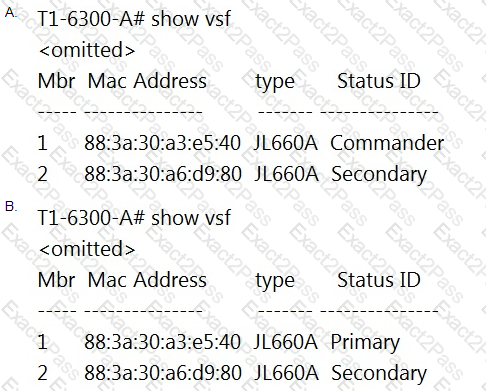
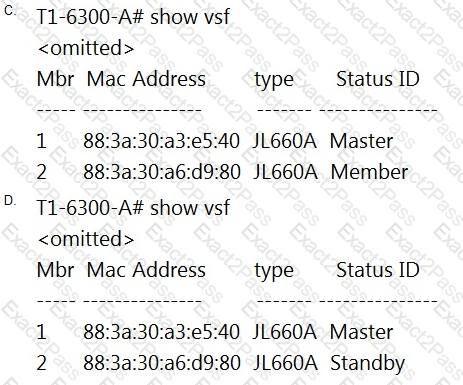
Which two statements accurately describe stacking with Aruba switches? (Choose two.)
What are two available options as part of a DHCP offer message? (Choose two.)
Which two types of routes can be found in the IP routing table of an Aruba AOS-CX switch? (Choose two.)
Refer to the exhibit.
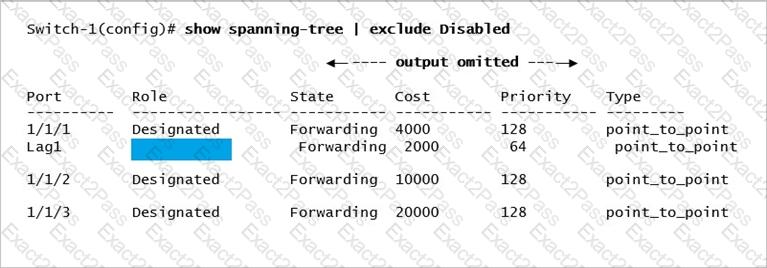
Switch-1 is not the root bridge. The ports shown are all the connected pointtopoint interfaces. What Role (hidden by the blue rectangle) will be assigned to theLag 1interface?
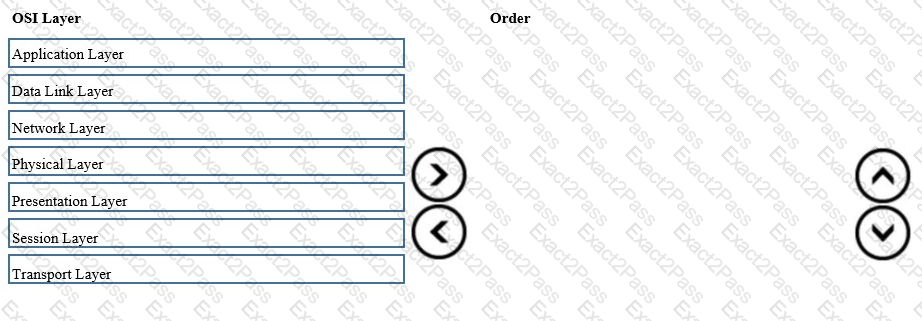
Place the OSI Layers in the correct order. Arrange them from least to greatest, starting with Layer 1 on the top, and progressing to Layer 7 on the bottom.
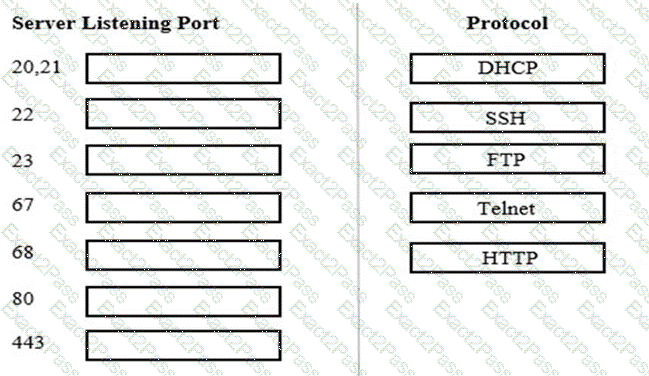
Match each network protocol to the correct server listening port. Not all answers will be used.
What are the commands to disable SSH and HTTPS services from the default VRF?
Which two statements accurately describe the features of NetEdit? (Choose two.)
What are two methods for remotely managing an Aruba AOS-CX switch? (Choose two.)
What are two OSPF attributes within the hello messages that must match to successfully establish neighbor relationships? (Choose two.)
Refer to the exhibit.
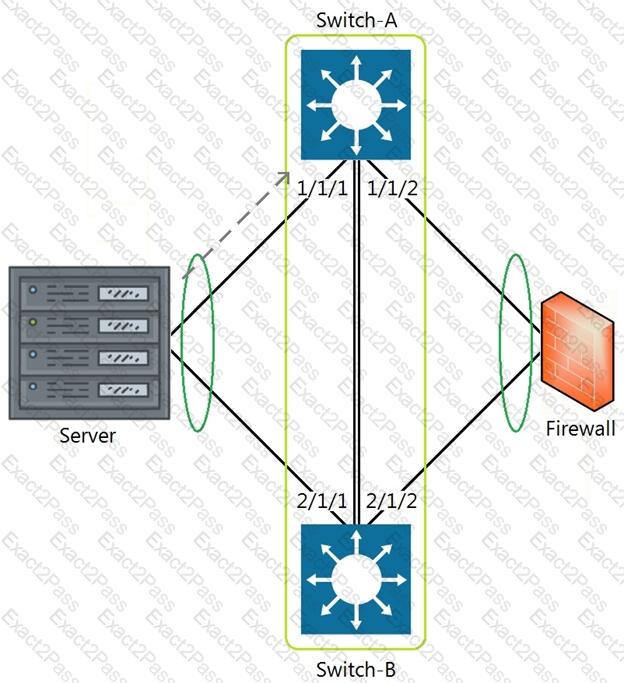
The above scenario shows a packet from the Server destined for the Firewall. Switch-A and Switch-B are bundled as VSF stack. The LAG between the VSF stack and the firewall indicates a hash function to forward the packet on port 2/1/2.
Which statement is true regarding how Switch-A will forward the packet?
The customer has 778 developers testing computer games on the network.
Which two actions resolve Broadcast storms? (Choose two.)
Aruba Access Points tunnel traffic in a campus to the Mobility Controller using which protocol?
Which two port characteristics must match between LAG interfaces? (Choose two.)
ServiceOS login:admin
SVOS>password
Enter password:********
Confirm password:********
The login password to access an Aruba AOS-CX was lost. After connecting to the switch console port, a reboot is performed and the Service OS console is accessed as shown above.
What is the default password that is required for the admin account while under the Service OS console?
Which two statements are true regarding Checkpoints on Aruba switches? (Choose two.)
Refer to the exhibit.
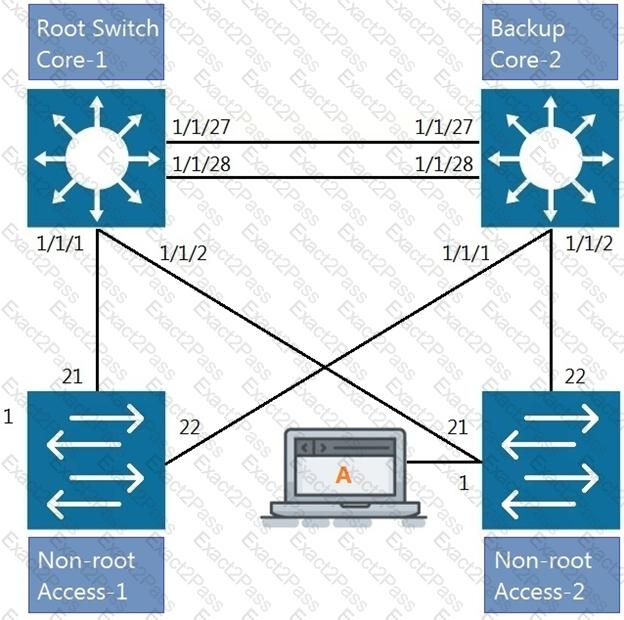
All four switches in the diagram have been configured with the region name "Aruba1".
What two other MSTP configurations must match for switches within the same MST region? (Choose two.)
Review the exhibit.
Which ports should be configured as access ports? Click in the green box to make your selection. (Select two.)