Without a prior version check, an engineer configures IGMP snooping on a device and the version of IGMP snooping is earlier than the IGMP versions on user hosts. In this case, which of the following situations will occur?
According to BGP route selection rules, the route with the higher Local_Pref is preferred.
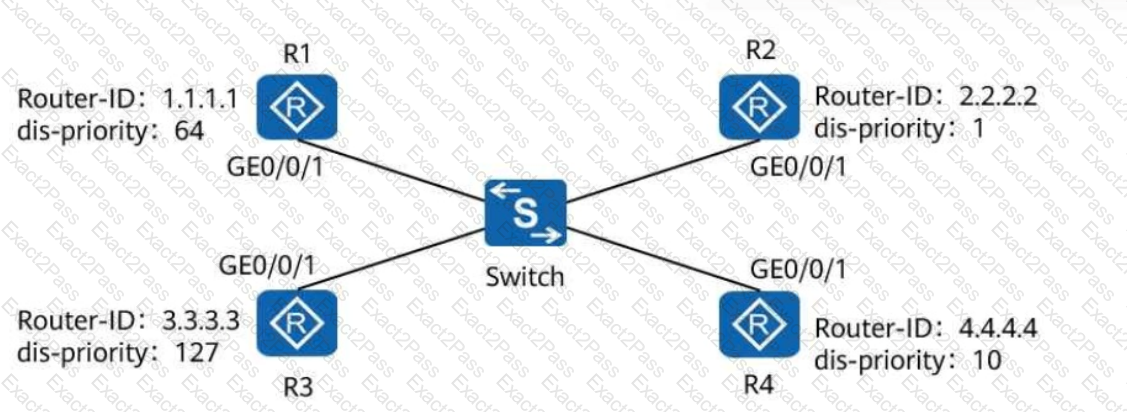
On a broadcast IS-IS network shown in the following figure, a DIS needs to be elected to create and update pseudonodes. Which of the following routers is elected as the DIS?
Which of the following messages are sent when BGP establishes peer relationships?
A wide area network (WAN) is a remote network that connects local area networks (LANs) or metropolitan area networks (MANs) in different areas for communication purposes. It is typically used to interconnect campus networks or data center networks.
When receiving a packet, a Huawei router matches the packet against ACL rules. The default ACL matching order used by the Huawei router is.
On an STP network, only the designated port processes inferior BPDUs. On an RSTP network, a port with any role processes inferior BPDUs.
An OSPF AS-external LSA describes a route to an AS external network. When the field in the LSA is 0.0.0.0, the traffic destined for the external network is sent to the ASBR that imports this external route. (Enter the acronym in uppercase.)
On a broadcast IS-IS network, a DIS needs to be elected to create and update pseudonodes. Which of the following values is the default DIS priority of an IS-IS interface?
The Internet Assigned Numbers Authority (IANA) allocates Class D addresses to IPv4 multicast. An IPv4 address is 32 bits long, and the four most significant bits of a Class D address are 1110.
If the interval for two consecutive packets of a TCP session reaching the firewall is longer than the aging time of the session, the firewall deletes the session information from the session table to ensure network security.
On Huawei switches, which of the following planes provides network information and forwarding entries that are mandatory for data plane forwarding?
In an OSPF routing domain, two routers must be specified as one DR and one BDR in a broadcast or NBMA network with at least two routers.
In BGP, the origin attribute of the routes imported using the import-route command is incomplete.
On an OSPF network, if a router receives an update of an LSA that exists in the local LSDB, the router updates the LSDB and floods the LSA.
On an IS-IS network, each router can generate LSPs. Which of the following events trigger the generation of a new LSP?
A BGP device receives a route carrying an unknown attribute from a peer but does not know whether other devices need the attribute. In this case, the BGP device retains this attribute when advertising the route to other peers. Which of the following attributes is of this type?
Which of the following statements regarding the summary automatic command and BGP route summarization is false?
GRE is a VPN technology that can implement packet transmission over heterogeneous networks. Which of the following statements are true about GRE?
After BGP initiates a TCP connection, the ConnectRetry timer is disabled if the TCP connection is successfully established. If the TCP connection fails to be established, the device tries to reestablish the TCP connection when the ConnectRetry timer expires.
Which of the following statements regarding the MED value in BGP are true?
After the administrator of an enterprise deploys a DHCP server, employees complain that their clients cannot obtain IP addresses from the DHCP server. Which of the following may cause this problem?
In IPv6, to communicate with a destination host, a host must obtain the link-layer address of the destination host through ARP.
BGP routes have multiple path attributes. When a router advertises a BGP route to its peers, the route carries multiple path attributes. These attributes describe the characteristics of the BGP route and affect route selection in some scenarios. The attribute is Huawei-specific. It is valid only on the local device and is not transmitted to BGP peers. (Enter the attribute name in lowercase as it appears in the command output about the BGP routing table.)
A network entity title consists of an area address and a system ID. It is a special NSAP (the SEL has a fixed value of 00) and is mainly used for route calculation.
ACLs are a common matching tool in routing policies. An ACL can be configured on a router to match routes.
Link aggregation is a common network technology. Which of the following are advantages of link aggregation?
GRE is a Layer 2 VPN encapsulation technology that encapsulates packets of certain data link layer protocols so that the encapsulated packets can be transmitted over an IP network.
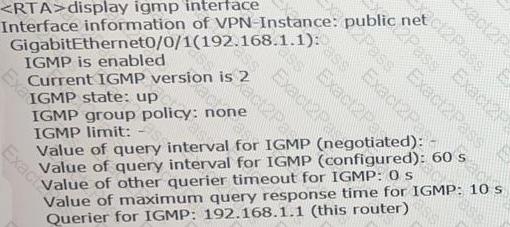
Which of the following statements is false, based on the following IGMP information on an interface of RTA?XC
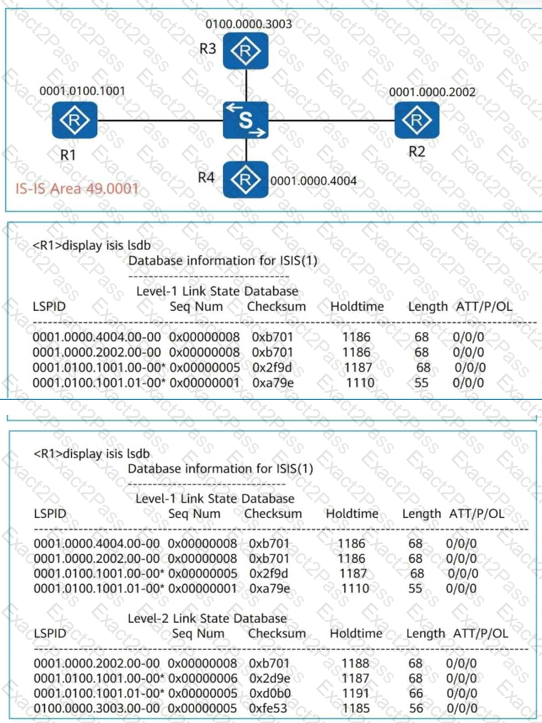
See the following figure. All routers on the network run IS-IS and are in area 49.0001. By referring to the LSDB of R1, the Level-2 DIS is. (Enter the device name, for example, R1.)
BFD for OSPF is deployed on a directly connected link. If the physical link is disconnected, drag the following BFD processes to the corresponding sequence numbers.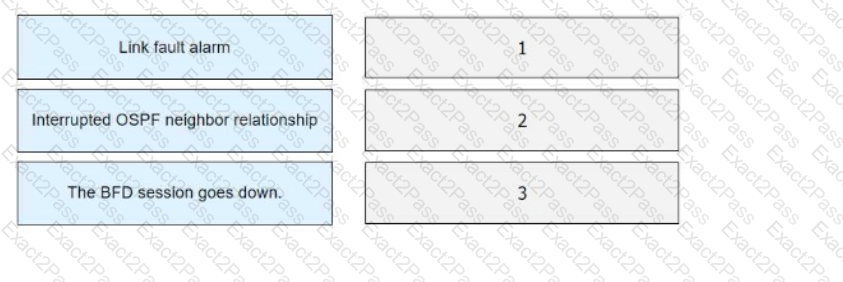
An enterprise uses Huawei routers to deploy an IS-IS network for network-wide communication. An engineer wants to change the interface cost to control route selection. By default, which of the following values is the maximum cost that can be configured?
A switch running a later IGMP version can identify Report messages of an earlier IGMP version, but the switch running an earlier IGMP version cannot identify Report messages of a later IGMP version. To ensure that IGMP runs properly, you are advised to set the IGMP version on the switch to be the same as or later than the IGMP version of member hosts.
OSPF networks are classified into broadcast, P2P, P2MP, and NBMA networks. Which of the following types of networks use the default Hello time (30s)?
During routine operation and maintenance, an engineer checks the IGMP configuration on RTA. The configuration is as follows:
Interface information of VPN-Instance: public net
GigabitEthernet0/0/1 (192.168.1.1):
IGMP is enabled
Current IGMP version is 2
IGMP state: up
IGMP group policy: none
IGMP limit: -
Value of query interval for IGMP (negotiated): -
Value of query interval for IGMP (configured): 60 s
Value of other querier timeout for IGMP: 0 s
Value of maximum query response time for IGMP: 10 s
Querier for IGMP: 192.168.1.1 (this router)
Given this, which of the following statements is false?
During BGP route summarization configuration, the keyword can be used to suppress all specific routes so that only the summary route is advertised. The summary route carries the Atomic-aggregate attribute rather than the community attributes of specific routes.
An IP prefix list is configured on a router using the following command:
ip ip-prefix huawei index 10 permit 10.1.1.0 24 greater-equal 26
In this case, the value of greater-equal-value is ____, and the value of less-equal-value is ____.
Which of the following TLVs is used by ISIS to describe the IP address of an interface?
Which of the following statement regarding the display ospf peer command output is true?
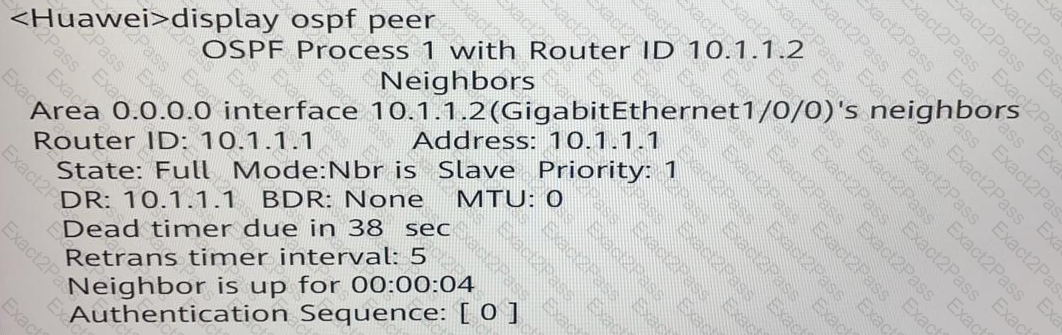
A campus network uses OSPF for network communication. The display ospf peer command is run on a router, and the command output is as follows:
vbnet
Copy
Edit
OSPF Process 1 with Router ID 10.0.2.2
Area 0.0.0.0 interface 10.0.235.2 (GigabitEthernet0/0/1)'s neighbors
Router ID: 10.0.5.5 Address: 10.0.235.5
State: Full Mode: Nbr is Master Priority: 1
DR: 10.0.235.5 BDR: 10.0.235.3 MTU: 0
Dead timer due in 40 sec
Area 0.0.0.0 interface 10.0.24.2 (Serial1/0/1)'s neighbors
Router ID: 10.0.4.4 Address: 10.0.24.4
State: Full Mode: Nbr is Master Priority: 1
DR: None BDR: None MTU: 0
Dead timer due in 35 sec
Which of the following statements are true about the device?
Which of the following statements regarding routing policy and policy-based routing are true?
In the OSPF protocol, inter-area route calculation involves only Router LSA, Network LSA, and Summary LSA.
Both MQC and PBR can be applied on device interfaces to filter received and sent packets or control packet forwarding paths.
GRE is a VPN encapsulation technology that is widely used to transmit packets across heterogeneous networks. Which of the following statements is false about GRE?
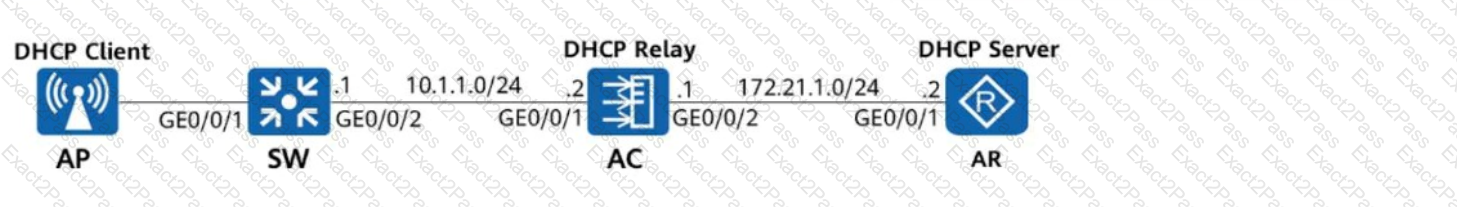
On the network shown in the following figure, the management VLAN is VLAN 10, and the AP is configured to obtain an IP address on the network segment 10.1.1.0/24 through DHCP. The AP, AC, and AR function as the DHCP client, DHCP relay agent, and DHCP server, respectively. Which of the following configurations for the DHCP relay agent and DHCP server are correct?
On an OSPF network, interfaces are classified into four types based on link layer protocols. Which of the following types can interfaces on an IS-IS network be classified into based on physical links?
When multiple access channels are set for the same access requirement, the insecure access channels are not used and secure access channels are selected in normal cases. Which of the following are secure access channels?
To enable PC1 to access PC2 using the IP address of the firewall's GE0/0/2, you need to configure NAPT for source address translation. In the following figure, fill in the blank to complete the command. 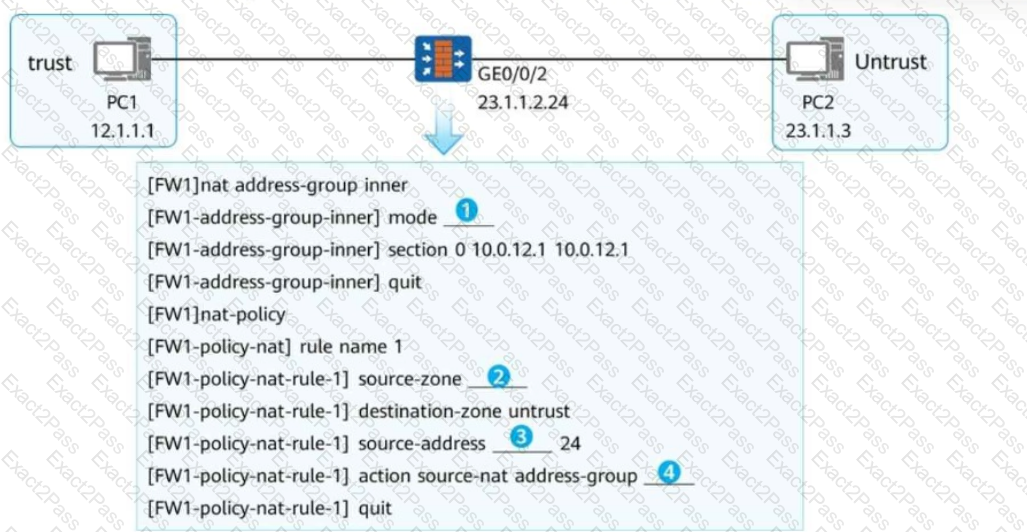

Typically, a protocol that occupies two ports during communication is called a multi-channel protocol. For such protocols, the ASPF function must be enabled on the firewall to ensure smooth setup of the data channel and reduce the risk of attacks. Which of the following protocols is not a multi-channel protocol?
On an OSPF network, if two routers with the same router ID run in different areas and one of the routers is an ASBR, LSA flapping occurs.
Which of the following statements regarding multicast MAC addresses are false?
Which of the following PIM protocol packets have unicast destination addresses.
The Neighbor Discovery Protocol (NDP) is an important basic protocol in the IPv6 protocol suite and plays an important role. Which of the following functions and features does it support?
Which of the following statements regarding OSPF route summarization commands are true?
The IP prefix list configuration on a Huawei router is shown below. Which of the following routes can match this IP prefix list?
bash
Copy
[huawei] ip ip-prefix test index 10 permit 10.0.0.0 8 less-equal 32
ASPF enables the firewall to support multi-channel protocols such as FTP and to define security policies for complex applications.
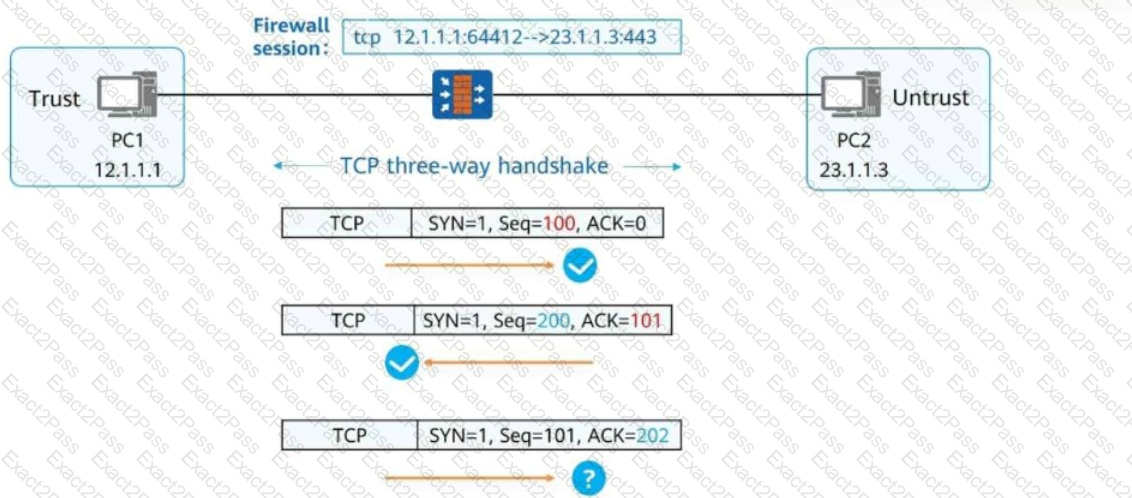
As shown in the figure, the stateful inspection firewall forwards the packet because the packet matches the session status of the firewall.
On an OSPF network, one router with P2P as the network type is directly connected to another router with P2MP as the network type. If the Hello intervals on the two routers are changed to be the same, neighbor relationship establishment and LSDB synchronization are not affected.
Which of the following scenarios is not suitable for deploying interface PBR?