Which of the following is not a response action for abnormal file identification?
When Eth-Trunk is deployed for the heartbeat links between firewalls, the Eth-Trunk interface can be configured as a Layer 2 interface as long as the total bandwidth of active links on the Eth-Trunk is greater than 30% of the bandwidth required by service traffic.
Predefined URL categories on Huawei firewalls reside in the URL category database delivered with the device and do not need to be manually loaded.
Which of the following are components of Huawei's anti-DDoS solution?(Select All that Apply)
Which of the following actions can be performed when the firewall identifies file anomalies?(Select All that Apply)
Which of the following items are recorded in the IPS service module logs of a Huawei NGFW?(Select All that Apply)
Which of the following statements is false about hot standby networking?(Select All that Apply)
The difference between DoS attacks and DDoS attacks is that DoS attacks are usually directly initiated by attackers, whereas DDoS attacks are usually initiated by attackers controlling multiple zombies.
Authentication rules configured on iMaster NCE-Campus support multiple matching conditions, such as matching account information, SSID information, and terminal IP address ranges, so that different authentication rules can be executed for different users.
In quota control policies, which of the following can be set for users?(Select All that Apply)
The Common Vulnerability Scoring System (CVSS) is a widely used open standard for vulnerability scoring. It uses a modular scoring system. Which of the following is not included in the CVSS?
The figure shows the PBR-based injection scenario. Which of the following statements are true about this scenario?(Select All that Apply)

Which of the following statements is false about virtual system resource allocation?
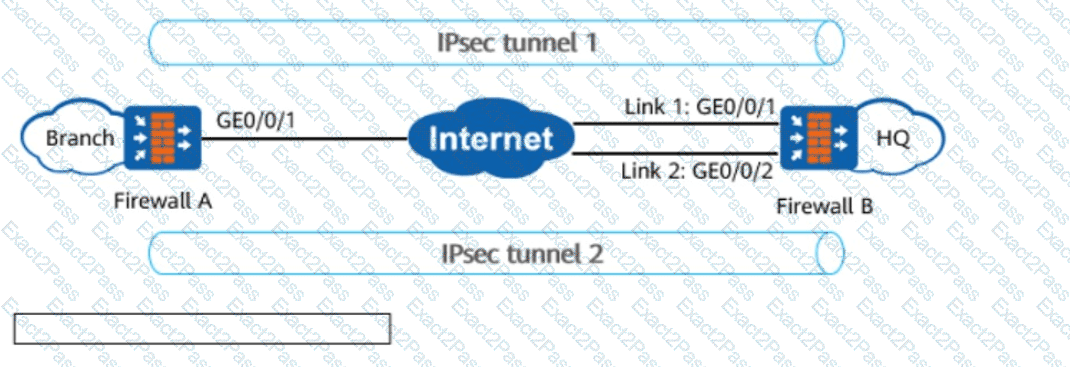
In the figure, FW_A connects to FW_B through two links working in active/standby mode. When the active link of FW_A is faulty, the old IPsec tunnel 1 needs to be torn down, and IPsec tunnel 2 needs to be established with FW_B through the standby link to route traffic. In this case, configuring the IKE _____ detection mechanism on FW_A helps detect link faults and tear down the IPsec tunnel.(Enter lowercase letters.)
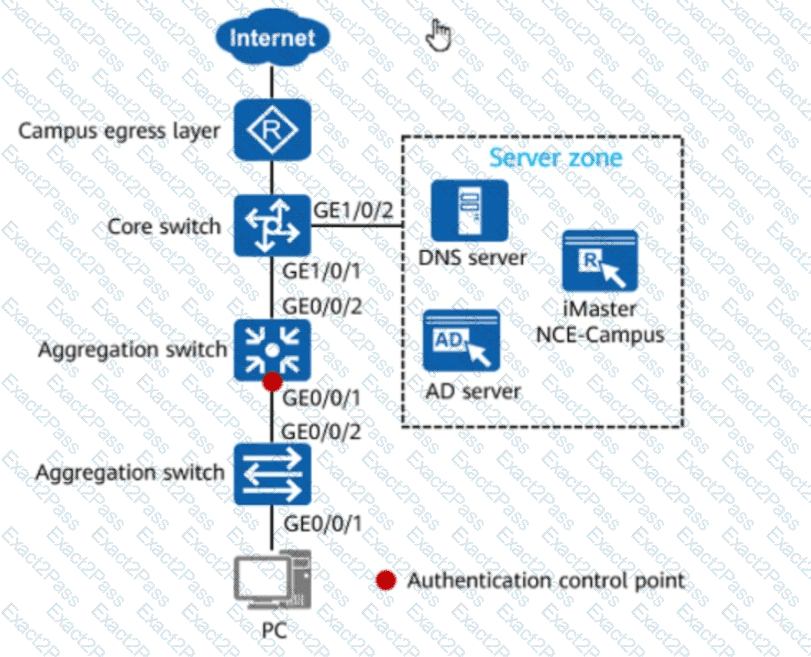
In the figure, if 802.1X authentication is used for wired users on the network, the network admission device and terminals must be connected through a Layer 2 network.
Options: