Last Update 22 hours ago Total Questions : 72
The GitHub Actions Certificate Exam content is now fully updated, with all current exam questions added 22 hours ago. Deciding to include GitHub-Actions practice exam questions in your study plan goes far beyond basic test preparation.
You'll find that our GitHub-Actions exam questions frequently feature detailed scenarios and practical problem-solving exercises that directly mirror industry challenges. Engaging with these GitHub-Actions sample sets allows you to effectively manage your time and pace yourself, giving you the ability to finish any GitHub Actions Certificate Exam practice test comfortably within the allotted time.
As a DevOps engineer, you are developing a container action. You need to execute a cleanup script after completing the main script execution. Which code block should be used to define the cleanup script?
As a developer, what options should you recommend to implement standards for automation reuse? (Choose two.)
As a developer, you are optimizing a GitHub workflow that uses and produces many different files. You need to determine when to use caching versus workflow artifacts. Which two statements are true? (Choose two.)
As a developer, you need to make sure that only actions from trusted sources are available for use in your GitHub Enterprise Cloud organization. Which of the following statements are true? (Choose three.)
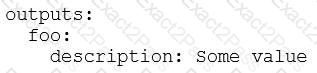
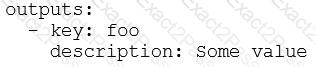
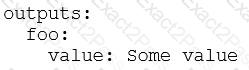
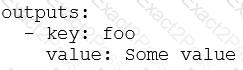
What is the minimal syntax for declaring an output named foo for an action?
A)
B)
C)
D)
You installed specific software on a Linux self-hosted runner. You have users with workflows that need to be able to select the runner based on the identified custom software. Which steps should you perform to prepare the runner and your users to run these workflows? (Choose two.)
Where should workflow files be stored to be triggered by events in a repository?

