Refer to the exhibit, which shows the output of a policy route table entry.
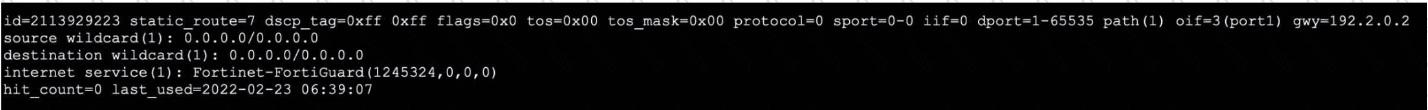
Which type of policy route does the output show?
Exhibit.
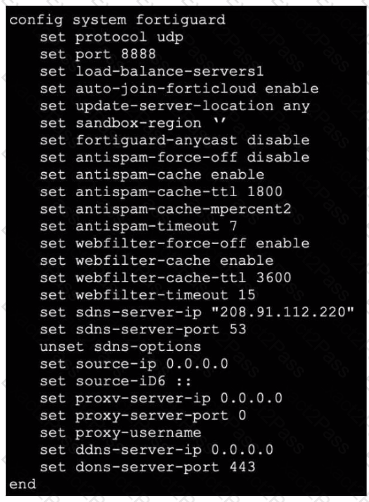
Refer to the exhibit, which shows a FortiGate configuration.
An administrator is troubleshooting a web filter issue on FortiGate. The administrator has configured a web filter profile and applied it to a policy; however the web filter is not inspecting any traffic that is passing through the policy.
What must the administrator do to fix the issue?
Exhibit 1.
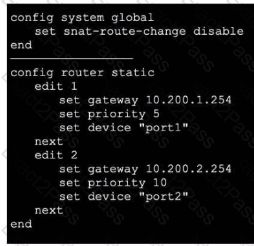
Exhibit 2.
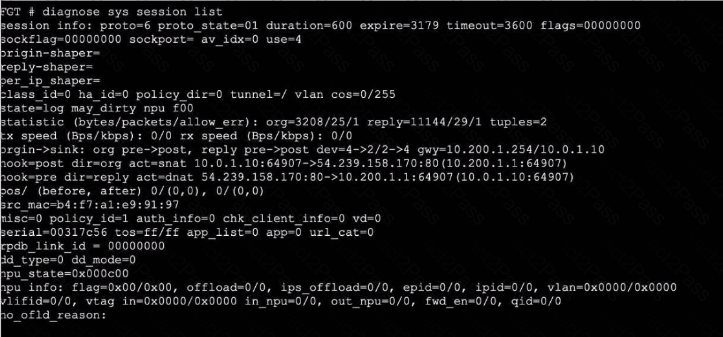
Refer to the exhibits, which show the configuration on FortiGate and partial internet session information from a user on the internal network.
An administrator would like to lest session failover between the two service provider connections.
Which two changes must the administrator make to force this existing session to immediately start using the other interface? (Choose two.)
An administrator wants to capture encrypted phase 2 traffic between two FotiGate devices using the built-in sniffer.
If the administrator knows that there Is no NAT device located between both FortiGate devices, which command should the administrator run?
Refer to the exhibit, which contains the output ofdiagnose vpn tunnellist.
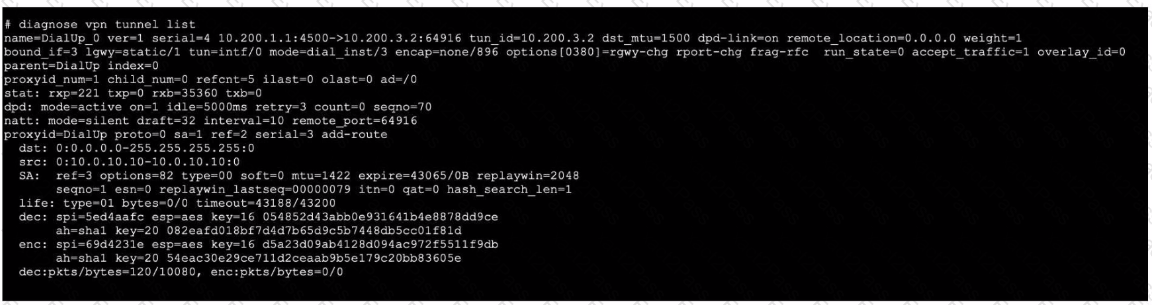
Which command will capture ESP traffic for the VPN named DialUp_0?
Exhibit.
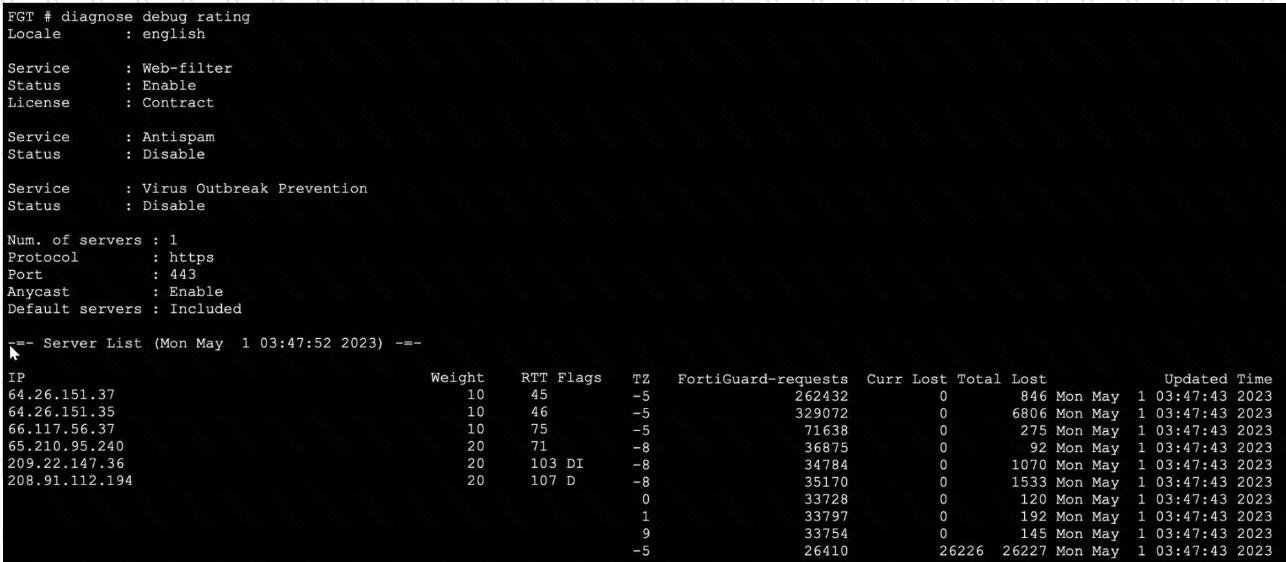
Refer to the exhibit, which shows the output of a diagnose command.
What can you conclude about the debug output in this scenario?
Exhibit.
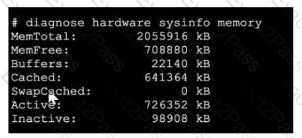
Refer to the exhibit, which shows a partial output of diagnose hardware aysinfo memory.
Which two statements about the output are true? (Choose two.)
Refer to the exhibits.
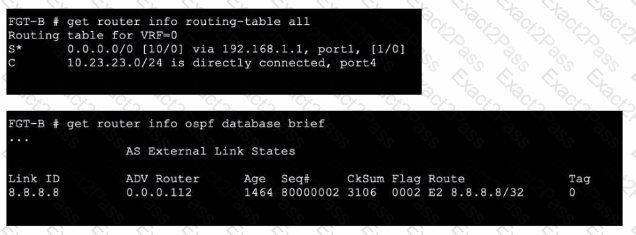
An administrator Is expecting to receive advertised route 8.8.8.8/32 from FGT-A. On FGT-B, they confirm that the route is being advertised and received, however, the route is not being injected into the routing table. What is the most likely cause of this issue?