Which network file sharing protocol provides cloud-based file sharing through a REST API interface?
An organization wants to protect data from accidental deletion, application crashes, data corruption, and disaster.
Which solution should the organization adopt?
An organization has two data centers separated by a distance of 1600 km. They want to replicate between these data centers for disaster recovery purposes. They are concerned that this will impact application response time.
Which solution will address this concern?
In an SDS environment, which protocol supports the resource-oriented architecture for the development of scalable and lightweight web applications while adhering to a set of constraints?
What set of components are part of a block-based storage array controller?
Which backup component sends metadata and tracking information about each backup to the system that maintains this information?
An Ethernet switch has eight ports and all ports must be operational for 24 hours; from Monday through Friday. However, a failure of Port 5 occurs as follows:
Tuesday = 6 AM to 7 AM Thursday = 5 PM to 9 PM Friday = 8 AM to 9 AM
What is the MTBF of Port 5?
A company finance department needs 250 GB of storage for their business applications. A LUN is created with 250 GB, and RAID 1 protection. The LUN is configured to support application I/O performance.
If storage cost is $2 per GB, what is the chargeback amount to the department for application storage?
Why is it important for organizations to store protect and manage their data?
Which data deduplication method would a cloud service provider use when storing back up data at their location?
A user lost access to a key VM due to a hardware failure. A proxy server regularly takes PIT snapshots of the VM to protect the data.
What type of data protection method is this called'?
Which Connectrix FC switch model supports NVMe in a 32Gb/s SAN fabric exclusively?
What is the effect of implementing link aggregation in an FC SAN environment?
Which layer of the OSI reference model provides logical end-to-end connections, sequencing, and integrity?
in a NAS environment, which file system provides a public or open variation of the Server Message Block (SMB) protocol and uses the TCP/IP protocol?
What triggers an appropriate workflow upon receiving a service provisioning or management request?
What is an accurate statement about the Do-It-Yourself approach for building modern Infrastructure?
Which Dell EMC product is a software-defined storage platform that abstracts, pools, and automates a data center’s physical storage infrastructure?
Refer to the Exhibit:
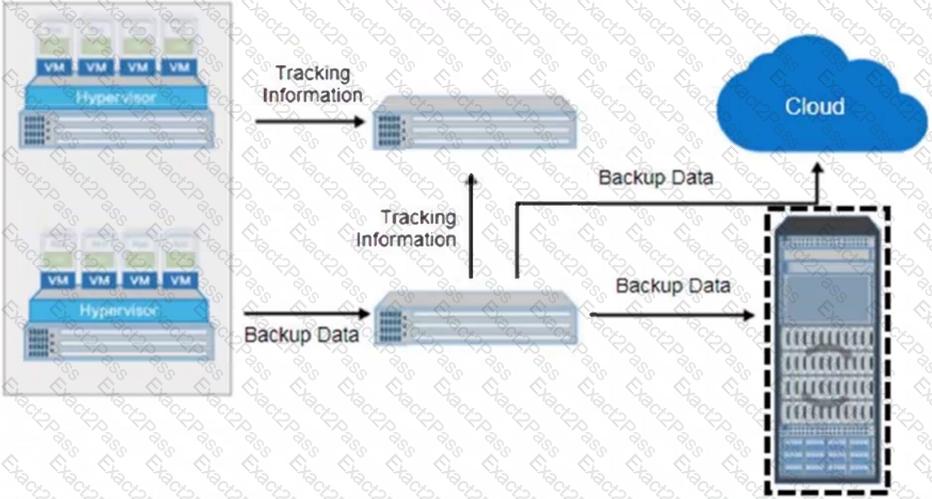
What is the name of the selected backup architecture component?
What is a function of the metadata service in an object-based storage device (OSD)?
What is a benefit of using an existing Ethernet network infrastructure for storage connectivity?
A company is using an intrusion detection and prevention system (IDPS) to scan and analyze intrusion events.
Which IDPS technique uses a database that contains known attack patterns?
Why is it important for organizations lo deploy business continuity solutions in their data center environment?
What functionality does the control layer provide in a software-defined networking architecture?
An Ethernet switch has eight ports and all ports must be operational for 24 hours from Monday through Friday. However, failures of Port 6 occur within the week as follows:
Tuesday = 6 AM to 8 AM
Thursday = 5 PM to 10 PM
Friday = 7 AM to 9 AM
What is the MTBF of Port 6?
In a data archiving environment, which component scans primary storage to find the files that are required to archive?
A Fibre Channel switch has eight ports and all ports must be operational 24 hours 7 days. However, a failure of Port 5 occurs on a particular week as follows:
Monday = 11 AM to 3 PM -
Thursday = 6 AM to 11 AM -
Saturday = 11 AM to 4 PM -
What is the availability of Port 5 in that week?
Which data deduplication method increases the probability of identifying duplicate data even when there is only a minor difference between two documents?
The Ethernet switch has eight ports and all ports must be operational for 24 hours, from Monday through Friday. However, a failure of Port 4 occurs as follows:
Monday = 8 PM to 11 PM -
Wednesday = 7 PM to 10 PM -
Thursday = 6 AM to 12 PM -
What is the MTTR of Port 4?
Which block storage volume allocates all of the physical storage specified at the time it is created?
What occurs when a company’s IT infrastructure security is breached by a passive attack?
Which modern technology enables data to be securely collected and processed at point of creation to create new value?
Which storage management function ensures that the services and service levels are delivered per SLAs?