Which option correctly describes the authentication differences between CyberArk Privilege Cloud and CyberArk PAM Self-Hosted?
Refer to the exhibit.
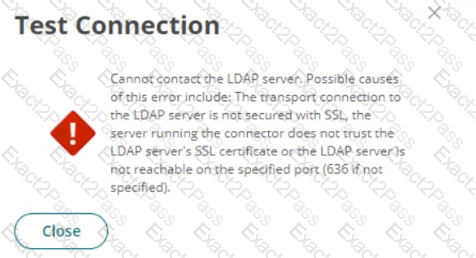
You set up your LDAP Directory in CyberArk Identity, but encountered an error during the connection test.
Which scenarios could represent a valid misconfiguration? (Choose 2.)
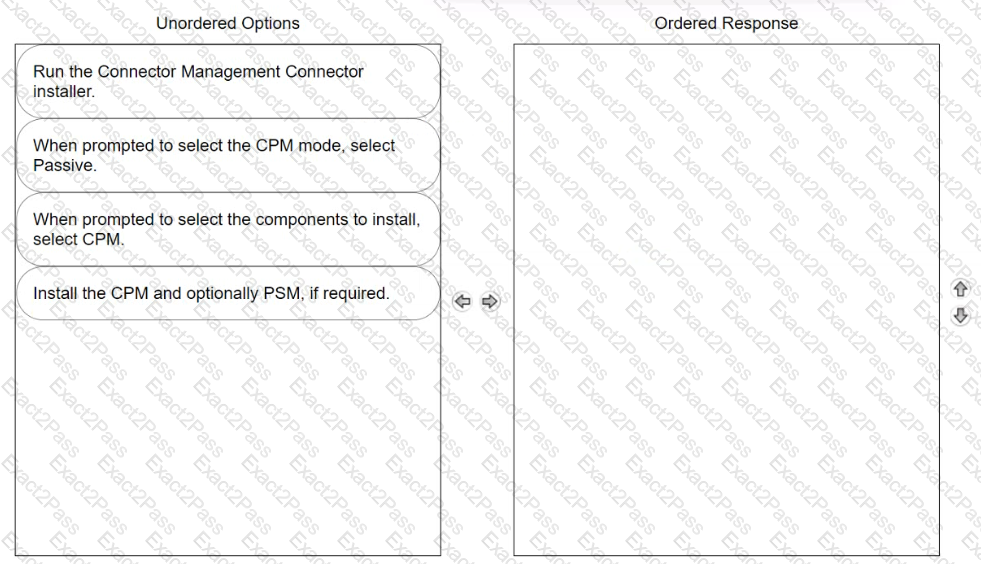
Arrange the steps to install passive CPM using Connector Management in the correct sequence
What is a requirement when installing the PSM on multiple Privileged Cloud Connector servers?
Which tool configures the user object that will be used during the installation of the PSM for SSH component?
What must be done before configuring directory mappings in the CyberArk Privilege Cloud Standard Portal for LDAP integration?
In the directory lookup order, which directory service is always looked up first for the CyberArk Privilege Cloud solution?
In large-scale environments, it is important to enable the CPM to focus its search operations on specific Safes instead of scanning all Safes it sees in the Vault. How is this accomplished?
What is the recommended method to enable load balancing and failover of the CyberArk Identity Connector?