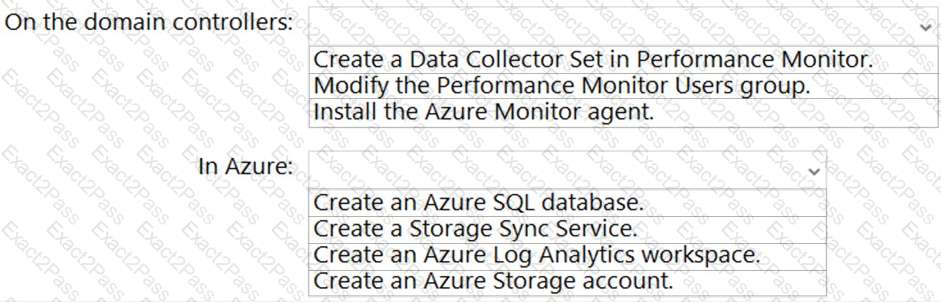
You need to implement alerts for the domain controllers. The solution must meet the technical requirements.
What should you do on the domain controllers, and what should you create on Azure? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
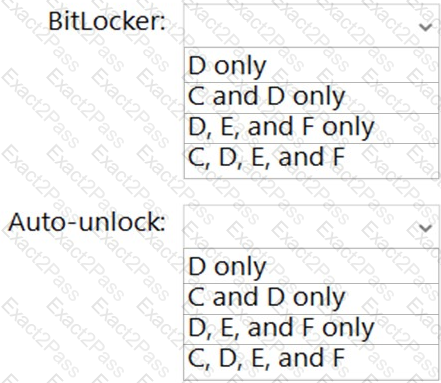
You need to configure BitLocker on Server4.
On which volumes can you turn on BitLocker, and on which volumes can you turn on auto-unlock? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
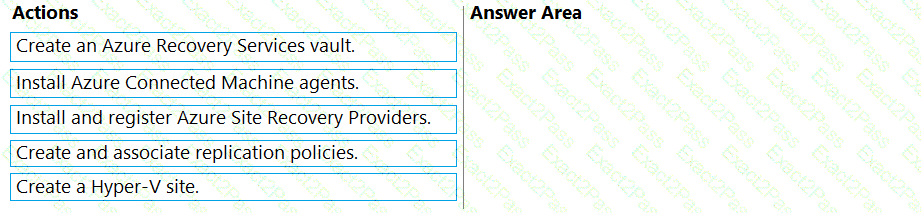
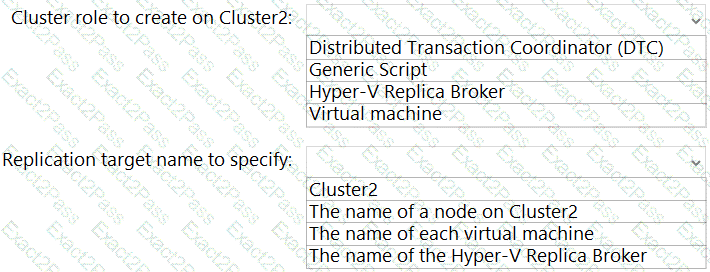
You need to meet the technical requirements for Cluster2.
Which four actions should you perform in sequence before you can enable replication? To answer, move the appropriate actions from the list of actions to the answer area and arrange them in the correct order.
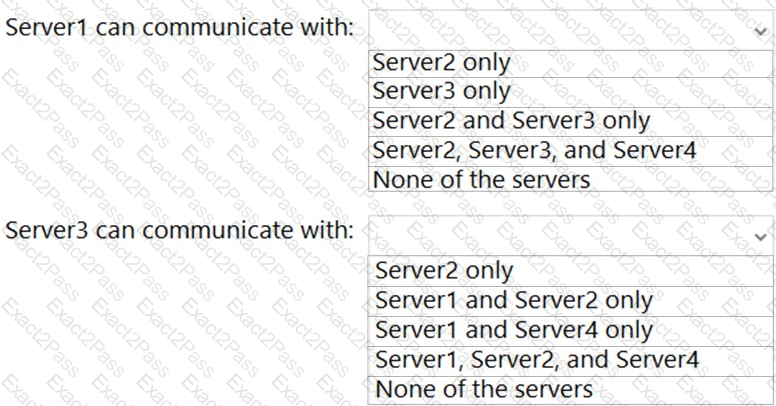
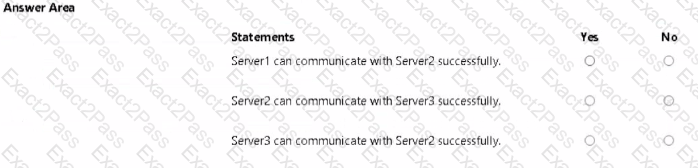
With which servers can Server1 and Server3 communicate? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.
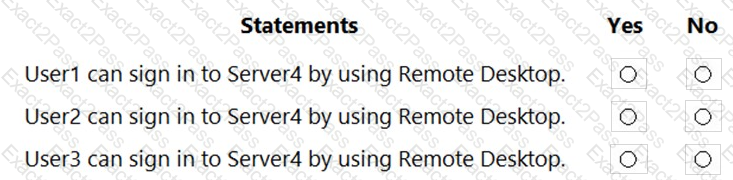
What is the effective minimum password length for User1 and Admin1? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
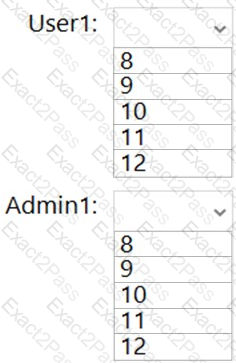
You need to back up Server 4 to meet the technical requirements.
What should you do first?
You need to meet the technical requirements for User1.
To which group in contoso.com should you add User1?
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
You have a failover cluster named Cluster1 that hosts an application named App1.
The General tab in App1 Properties is shown in the General exhibit. (Click the General tab.)
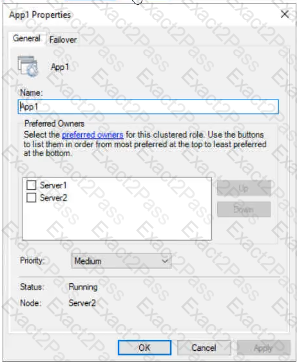
The Failover tab in App1 Properties is shown in the Failover exhibit. (Click the Failover tab.)
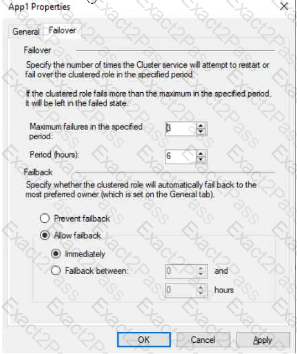
Server1 shuts down unexpectedly.
You need to ensure that when you start Server1, App1 continues to run on Server2.
Solution: You increase Maximum failures in the specified period for the App1 cluster role.
Does this meet the goal?
You have a Hyper-V failover cluster named Cluster1 at a main datacenter. Cluster1 contains two nodes that have the Hyper-V server role installed. Cluster1 hosts 10 highly available virtual machines.
You have a cluster named Cluster2 in a disaster recovery site. Cluster2 contains two nodes that have the Hyper-V server role installed.
You plan to use Hyper-V Replica to replicate the virtual machines from Cluster1 to Cluster2.
What should you do? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
You have a Site-to-Site VPN between an on-premises network and an Azure VPN gateway. BGP is disabled for the Site-to-Site VPN.
You have an Azure virtual network named Vnet1 that contains a subnet named Subnet1. Subnet1 contains a virtual machine named Server1.
You can connect to Server1 from the on-premises network.
You extend the address space of Vnet1. You add a subnet named Subnet2 to Vnet1. Subnet2 uses the extended address space. You deploy an Azure virtual machine named Server2 to Subnet2.
You cannot connect to Server2 from the on-premises network. Server1 can connect to Server2.
You need to ensure that you can connect to Subnet2 from the on-premises network.
What should you do?
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
Your network contains a single-domain Active Directory Domain Services (AD DS) forest named contoso.com. The functional level of the forest is Windows Server 2012 R2. All domain controllers run Windows Server 2012 R2.
Sysvol replicates by using the File Replication Service (FRS).
You plan to replace the existing domain controllers with new domain controllers that will run Windows Server 2022.
You need to ensure that you can add the first domain controller that runs Windows Server 2022.
Solution: You run the Active Directory Migration Tool (ADMT).
Does this meet the goal?
You are planning the data share migration to support the on-premises migration plan.
What should you use to perform the migration?
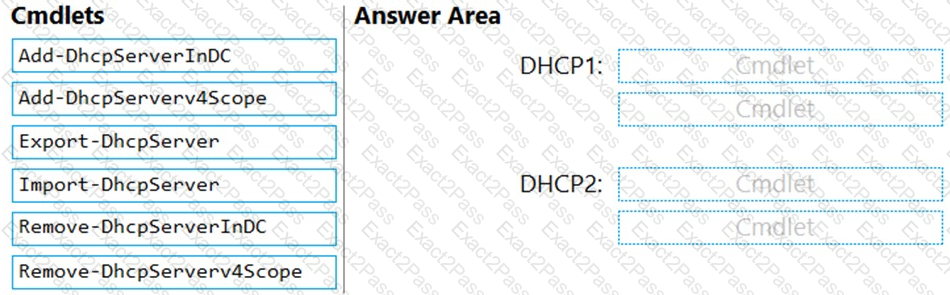
You are planning the DHCP1 migration to support the DHCP migration plan.
Which two PowerShell cmdlets should you run on DHCP1, and which two PowerShell cmdlets should you run on DHCP2? To answer, drag the appropriate cmdlets to the correct servers. Each cmdlet may be used once, more than once, or not at all. You may need to drag the split bar between panes or scroll to view content.
NOTE: Each correct selection is worth one point.
You have an on-premises server named Setver1 that runs Windows Server 2022 Standard.
You have an Azure subscription that contains the virtual machines shown in the following table.
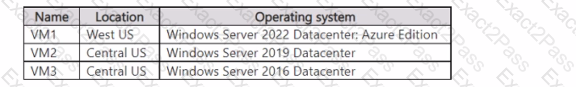
The subscription contains a Microsoft Sentinel instance named Sentinel1 in the Central US Azure region. You need to implement the Windows Firewall connector. Which servers can send Windows Firewall logs to Sentinel1?
You are remediating the firewall security risks to meet the security requirements.
What should you configure to reduce the risks?
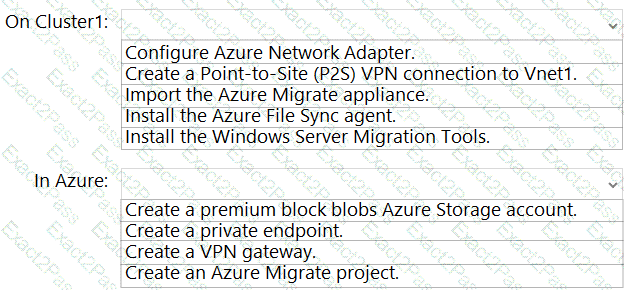
You are planning the migration of APP3 and APP4 to support the Azure migration plan.
What should you do on Cluster1 and in Azure before you perform the migration? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
Your network contains a single-domain Active Directory Domain Services (AD DS) forest named contoso.com. The functional level of the forest is Windows Server 2012 R2. All domain controllers run Windows Server 2012 R2.
Sysvol replicates by using the File Replication Service (FRS).
You plan to replace the existing domain controllers with new domain controllers that will run Windows Server 2022.
You need to ensure that you can add the first domain controller that runs Windows Server 2022.
Solution: You migrate sysvol from FRS to Distributed File System (DFS) Replication.
Does this meet the goal?
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
You have an on-premises server named Server1 that runs Windows Server.
You have a Microsoft Sentinel instance.
You add the Windows Firewall data connector in Microsoft Sentinel.
You need to ensure that Microsoft Sentinel can collect Windows Firewall logs from Server1.
Solution: You install the Microsoft Integration Runtime on Server1.
Does this meet the goal?
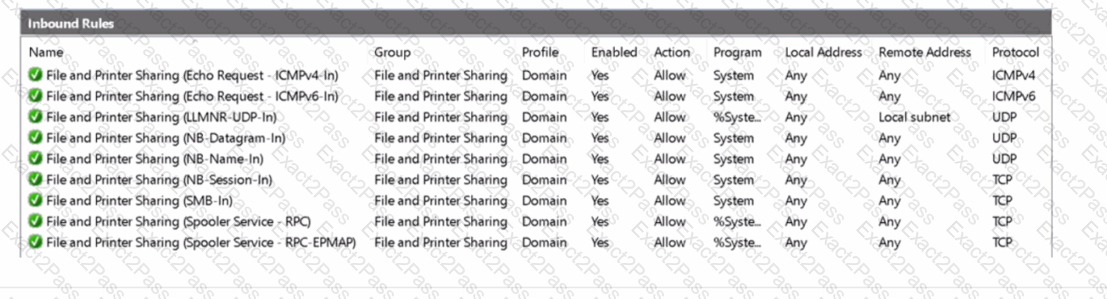
Your network contains an on-premises Active Directory Domain Services (AD DS) domain.
The domain contains the servers shown in the following table.
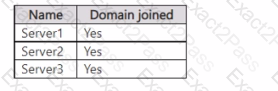
Server1 has the connection security rule as shown in the Server1 exhibit. (Click the Server1 tab.)

Server2 has the connection security rule as shown in the Server2 exhibit. (Click the Server2 tab.)
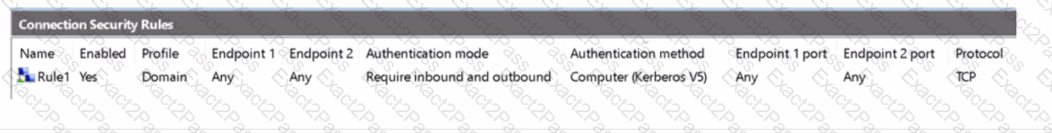
Server1 has the inbound firewall rules as shown in the Server1 inbound rules exhibit. (Click the Server1 inbound rules tab.)
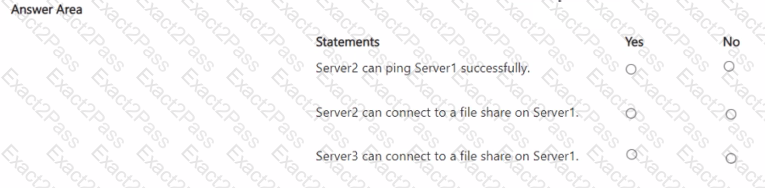
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
You have an Azure subscription that has Microsoft Defender for Cloud enabled.
You have 50 Azure virtual machines that run Windows Server.
You need to ensure that any security exploits detected on the virtual machines are forwarded to Defender for Cloud.
Which extension should you enable on the virtual machines?
You have a server that runs Windows Server. The server is configured to encrypt all incoming traffic by using a connection security rule.
You need to ensure that Server1 can respond to the unencrypted tracert commands initiated from computers on the same network.
What should you do from Windows Defender Firewall with Advanced Security?
You manage 200 physical servers that run Windows Server.
You plan to migrate the servers to Azure.
You need to prepare for discovery of the servers by using Azure Migrate.
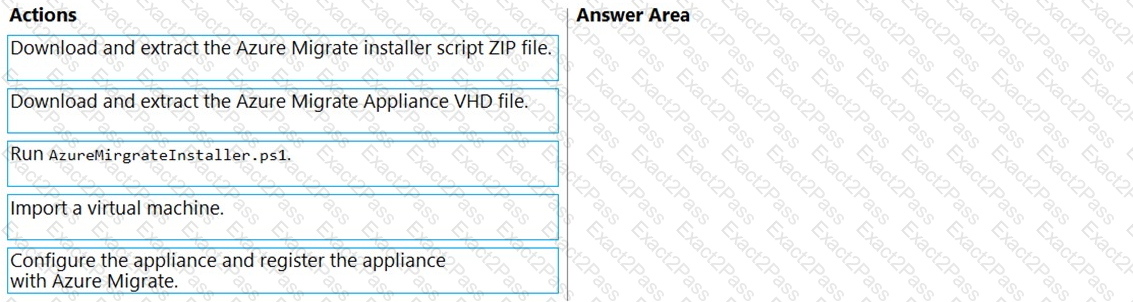
Which three actions should you perform in sequence on a physical server? To answer, move the appropriate actions from the list of actions to the answer area and arrange them in the correct order.
You have an Azure virtual machine named VM1. Crash dumps for a process named Process1 are enabled for VM1.
When process1.exe on VM1 crashes, a technician must access the memory dump files on the virtual machine. The technician must be prevented from accessing the virtual machine.
To what should you provide the technician access?
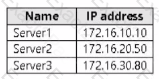
Your network contains an Active Directory Domain Services (AD DS) domain. The domain contains servers that run Windows Server as shown in the following table.
Server1 has the connection security rules shown in the following table.
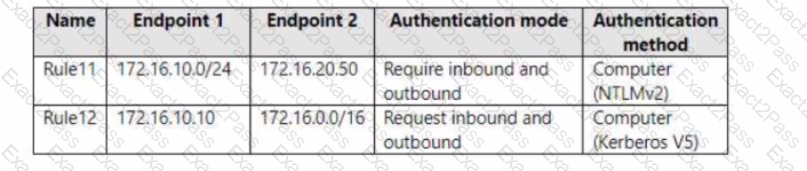
Server2 has the connection security rules shown in the following table.
.
Your on-premises network has a 200-Mbps connection to Azure and contains a server named Server1 that stores 70 TB of data files.
You have an Azure Storage account named storage 1.
You plan to migrate the data files from Server1 to a blob storage container in storage!. Testing shows that copying the data files by using azcopy will take approximately 35 days.
You need to minimize how long it will take to migrate the data to Azure.
What should you use?
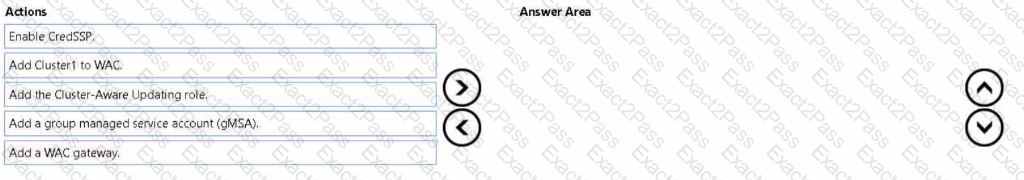
Your network contains an Active Directory Domain Services (AD DS) domain. The domain contains a failover cluster named Cluster1.
You need to configure Cluster-Aware Updating (CAU) on the cluster by using Windows Admin Center (WAC).
Which three actions should you perform in sequence? To answer, move the appropriate actions from the list of actions to the answer area and arrange them in the correct order.
You have a failover cluster named Cluster1 that contains three nodes.
You plan to add two file server cluster roles named File1 and File2 to Cluster1. File1 will use the File Server for general use role. File2 will use the Scale-Out File Server for application data role.
What is the maximum number of nodes for File1 and File2 that can concurrently serve client connections? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
