Which two dynamic routing protocols are supported when using Cisco ACI to connect to an external Layer 3 network? (Choose two.)
Cisco ACI fabric must send a packet between two pods in a Cisco AC1 Multi-Pod topology where ARP flooding is disabled within the bridge domain. How does a Cisco ACI spine switch .. ARP messages from a leaf switch in POD1 to POD2?
All workloads in VLAN 1001 have been migrated into EPG-1001. The requirement is to move the gateway address for VLAN 1001 from the core outside the Cisco ACI fabric into the Cisco ACI fabric. The endpoints in EPG-1001 must route traffic to endpoints in other EPGs and minimize flooded traffic in the fabric. Which configuration set is needed on the bridge domain to meet these requirements?
Engineer must configure SNMP inside a Cisco ACI fabric. The engineer has created an SNMP Policy, called SNMP-policy and an SNMP Monitoring Group called SNMP-group1 that Contains five trap receivers. Which configuration set completes the configuration?
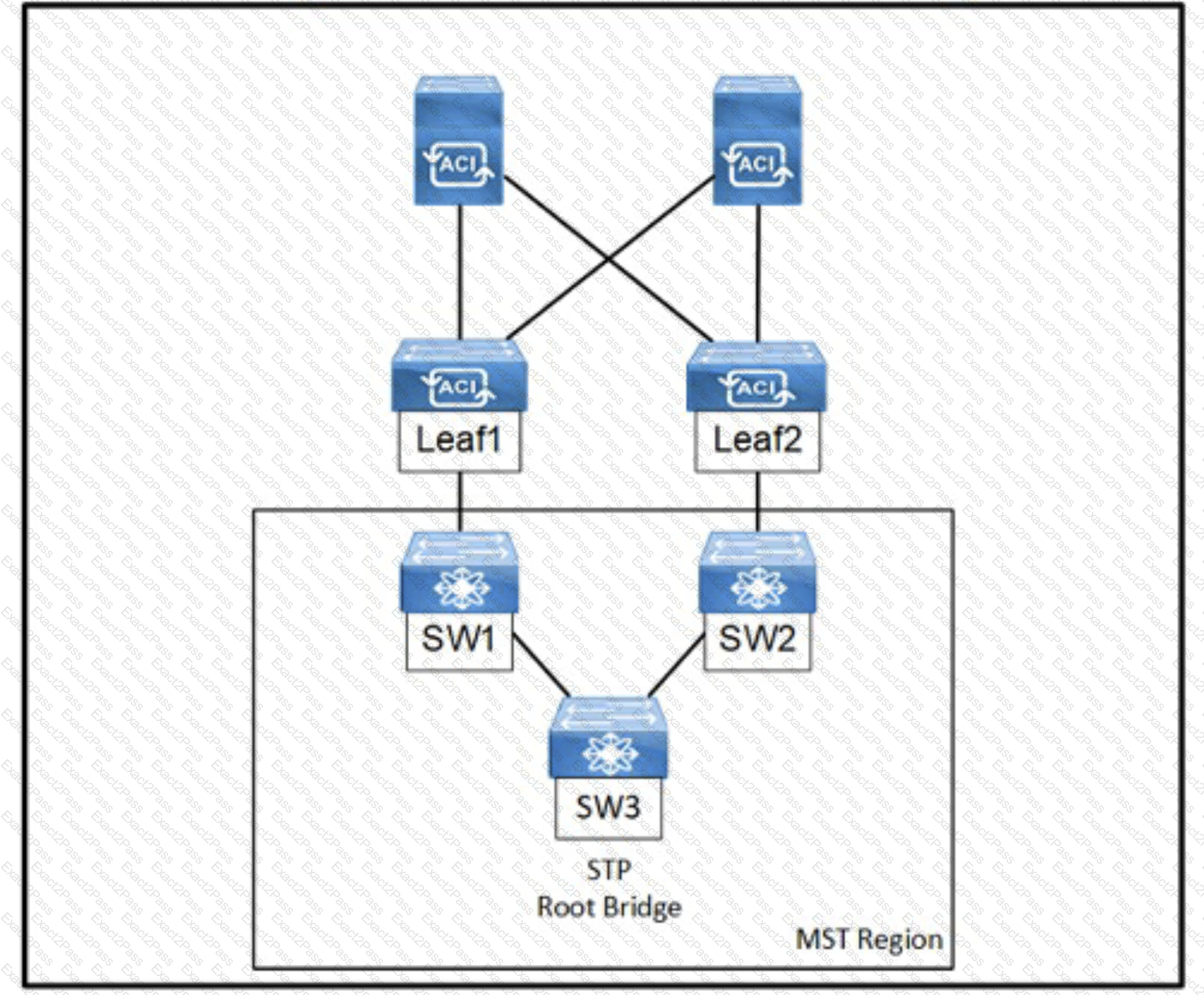
Refer to the exhibit, An engineer is deploying a Cisco ACI environment but experiences a STP loop between switch1 and switch2. Which configuration step is needed to break the STP loop?
Refer to the exhibit.
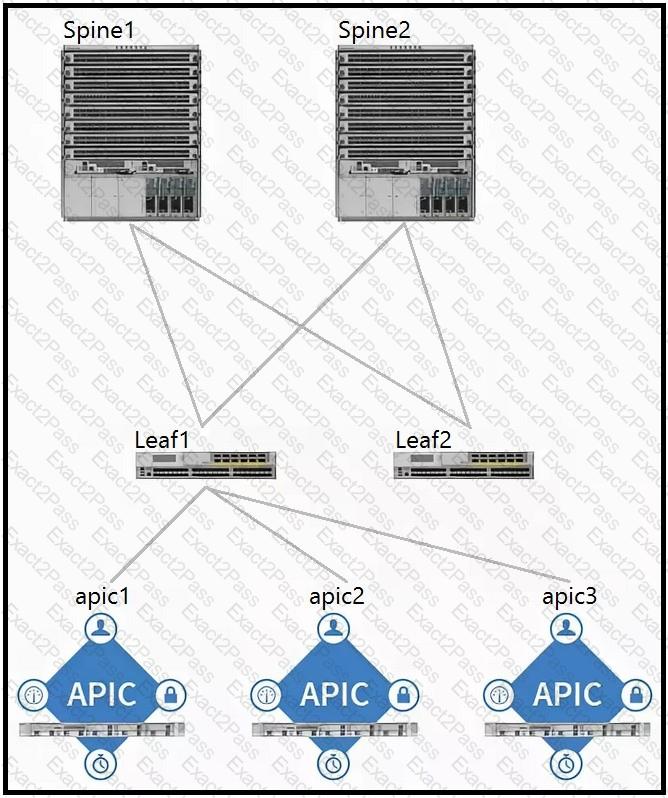
Which two components should be configured as route reflectors in the ACI fabric? (Choose two.)
What is the result of selecting the On Demand attribute in the Deploy Immediacy feature during VMM domain association to an EPG?
An engineer needs to deploy a leaf access port policy group in ACI Fabric to support the following requirements:
• Control the amount of application data flowing into the system
• Allow the newly connected device to auto-negotiate link speed with the leaf switch
Which two ACI policies must be configured to achieve these requirements? (Choose two.)
Which feature allows firewall ACLs to be configured automatically when new endpoints are attached to an EPG?
An organization has encountered many STP-related issues in the past due to failed hardware components. They are in the process of long-term migration to a newly deployed ACI fabric. Senior engineers are worried that spanning-tree loops in the existing network may be extended to the ACI fabric. Which feature must be enabled on the ACI leaf ports to protect the fabric from spanning-tree loops?
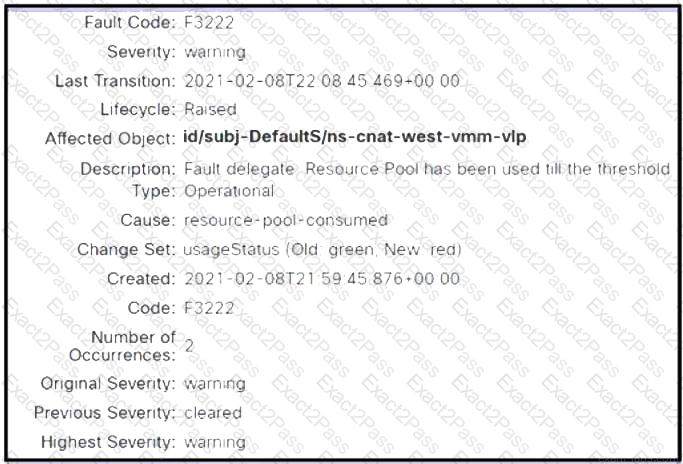
Refer to the exhibit. A Cisco APIC raises an error when the EPG must accept endpoints from a VMM domain created. Which action clears the fault?
A customer migrates a legacy environment to Cisco ACI. A Layer 2 trunk is configured to interconnect the two
environments. The customer also builds ACI fabric in an application-centric mode. Which feature should be
enabled in the bridge domain to reduce instability during the migration?
Which endpoint learning operation is completed on the egress leaf switch when traffic is received from an L3Out?
An engineer must connect Cisco ACI fabric using Layer 2 with external third-party switches. The third-party
switches are configured using 802.1s protocol. Which two constructs are required to complete the task?
(Choose two.)
Refer to the exhibit.
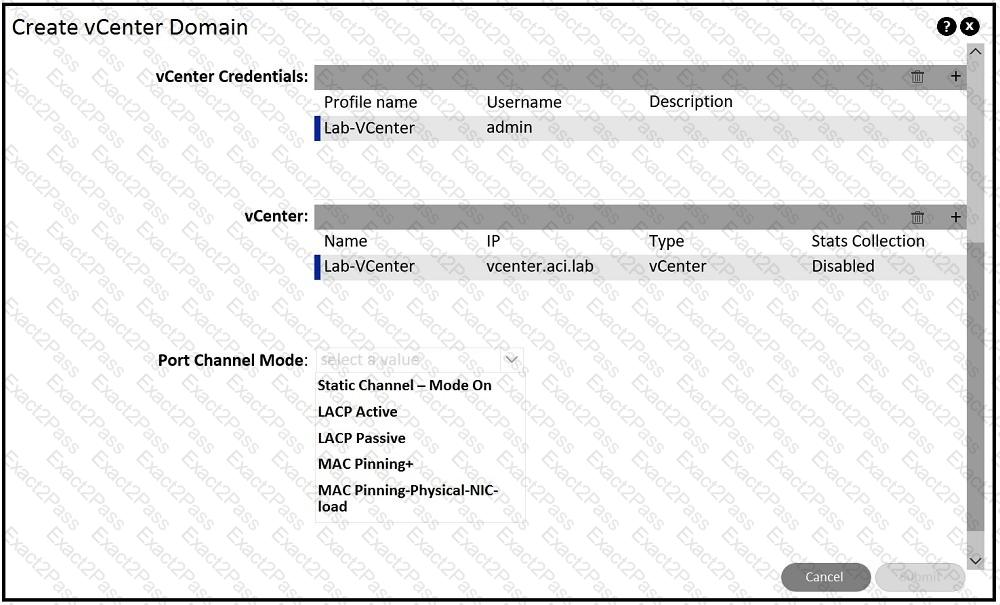
An engineer is implementing Cisco ACI – VMware vCenter integration for a blade server that lacks support of bonding. Which port channel mode results in “route based on originating virtual port” on the VMware VDS?
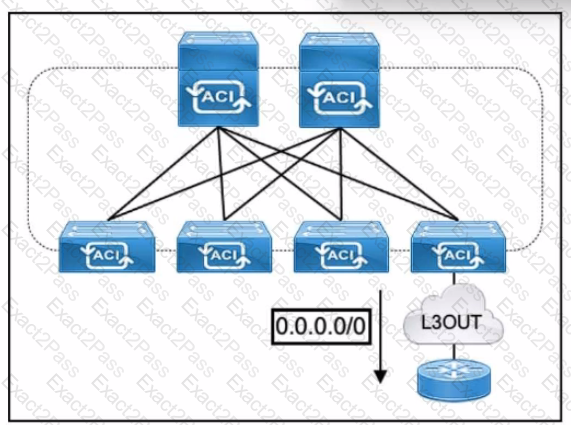
Refer to the exhibit. The default route is not present in the routing tables of the Cisco ACI leaf switches. All static and direct routes are currently being redistributed and advertised. Which jn must be taken to advertise a default route on the eBGP L30ut?
Regarding the MTU value of MP-BGP EVPN control plane packets in Cisco ACI, which statement about communication between spine nodes in different sites is true?
An engineer is implementing a Cisco ACI environment that consists of more than 20 servers. Two of the servers support only Cisco Discovery Protocol with no order link discovery protocol. The engineer wants the servers to be discovered automatically by the Cisco ACI fabric when connected. Which action must be taken to meet this requirement?
An engineer is extending EPG connectivity to an external network. The external network houses the Layer 3 gateway and other end hosts. Which ACI bridge domain configuration should be used?
Which type of profile needs to be created to deploy an access port policy group?
Which action sets Layer 2 loop migration in an ACI Fabric with a Layer 2 Out configured?
An engineer must attach an ESXi host to the Cisco ACI fabric. The host is connected to Leaf 1 and has its gateway IP address 10.10.10.254/24 configured inside the ACI fabric. A new wall is attached to Leaf 2 and mapped to the same EPG and BD as the ESXi host. The engineer must migrate the gateway of the ESXi host to the firewall. Which configuration set complishes this goal?
A Cisco ACI environment consists of multiple silent hosts that are often relocated between leaf switches. When the host is relocated, the bridge domain takes more than a few seconds to relearn the host’s new location. The requirement is to minimize the relocation impact and make the ACI fabric relearn the new location of the host faster. Which action must be taken to meet these requirements?
In the context of ACI Multi-Site, when is the information of an endpoint (MAC/IP) that belongs to site 1 advertised to site 2 using the EVPN control plane?
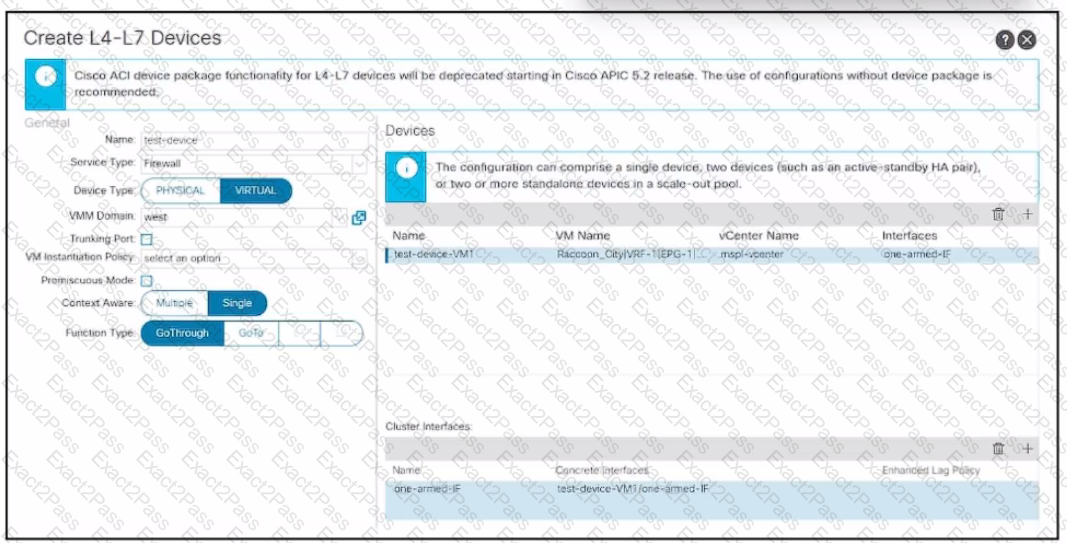
Refer to the exhibit. An engineer configures a Layer 4 to Layer 7 device object. The device is a virtual firewall with a single network adapter and it must be deployed in routed mode. Which .. completes the configuration of the device object?
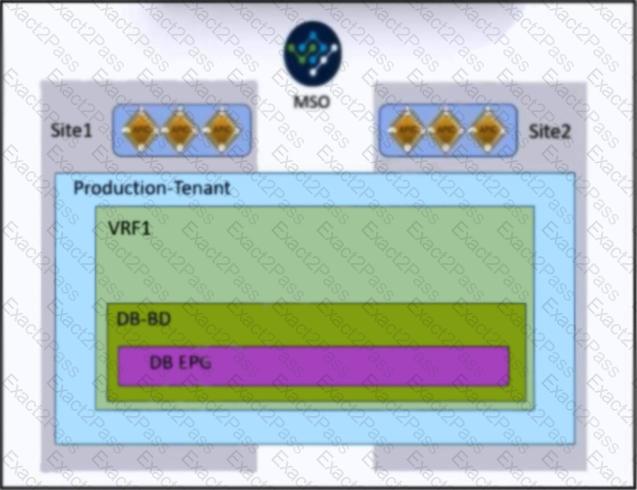
Refer to the exhibit. An engineer must allow IP mobility between Site1 and Site2 in a Cisco ACI Multi-Site orchestrator. The design must meet these requirements:
A disaster recovery (DR) solution must exist between the sites that do not require vMotion support.
The application must be started at a DR site without having to re-IP the application servers.
The solution must avoid any broadcast storms between the sites.
Which two actions meet these criteria? (Choose two.)
When does the Cisco ACI leaf learn a source IP or MAC as a remote endpoint?
Refer to the exhibit.
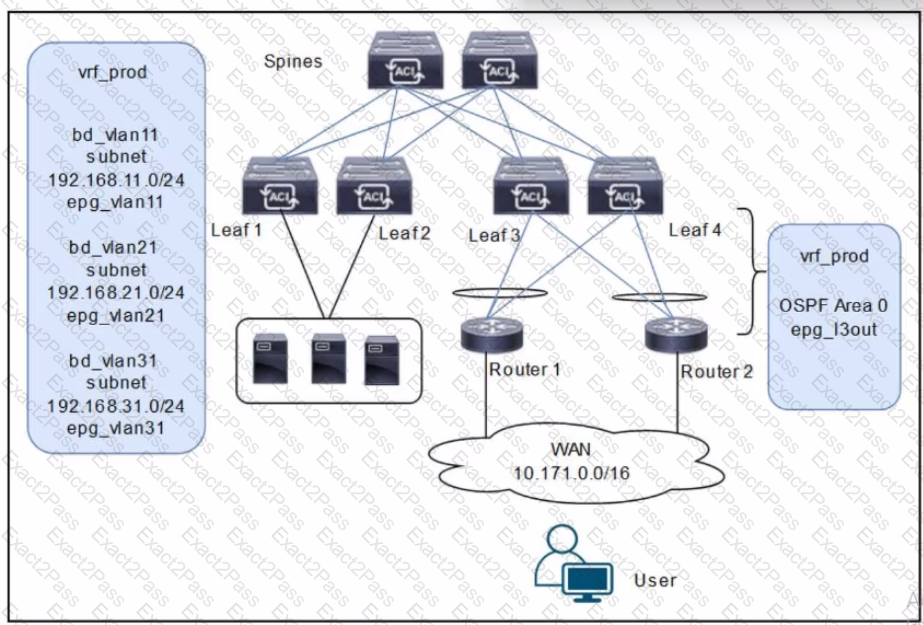
A customer is deploying a WAN with these requirements: •Routers 1 and 2 must receive only routes 192.168.11.0/24 and 192.168.21.0724 from the Cisco ACI fabric •Reachability to the WAN users must be permitted only for the servers that are located in vrf_prod.
Which settings must be configured to meet these objectives?
What are two PBR characteristics of the Cisco ACI Active-Active Across Pods deployment mode in Cisco ACI Multi-Pod design? (Choose two.)
Cisco ACI fabric contains 10 standalone leaf switches. An engineer must configure only the first two leaf switches in a VPC. Which VPC protection type must be configured to accomplish goal?
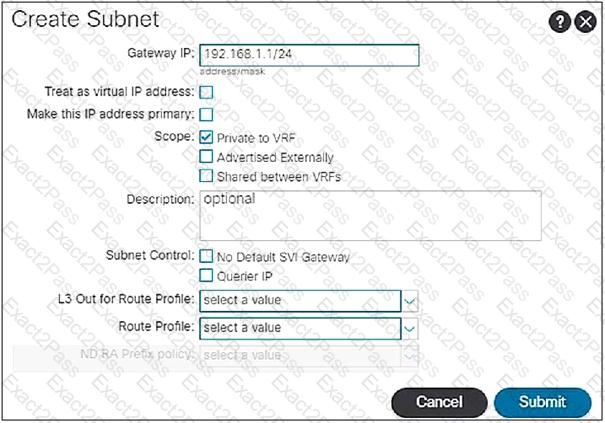
When the subnet is configured on a bridge domain, on which physical devices is the gateway IP address configured?
Refer to the exhibit.
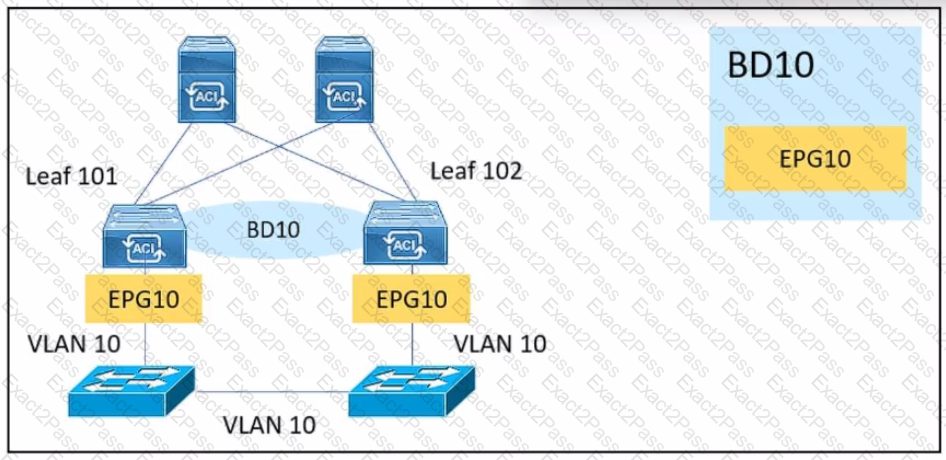
An engineer is implementing a BPDU filter on external switch interfaces That face the Cisco ACI fabric to prevent excessive TCNs from impacting the fabric. Which Configuration must be applied on Cisco ACI to avoid a Layer 2 loop?
An engineer deploys a two-pod Cisco ACI Multi-Pod environment. Why should no more than two Cisco APIC controllers be deployed in the same pod?
Which two IP address types are available for transport over the ISN when they are configured from Cisco ACI Multi-Site Orchestrator? (Choose two.)
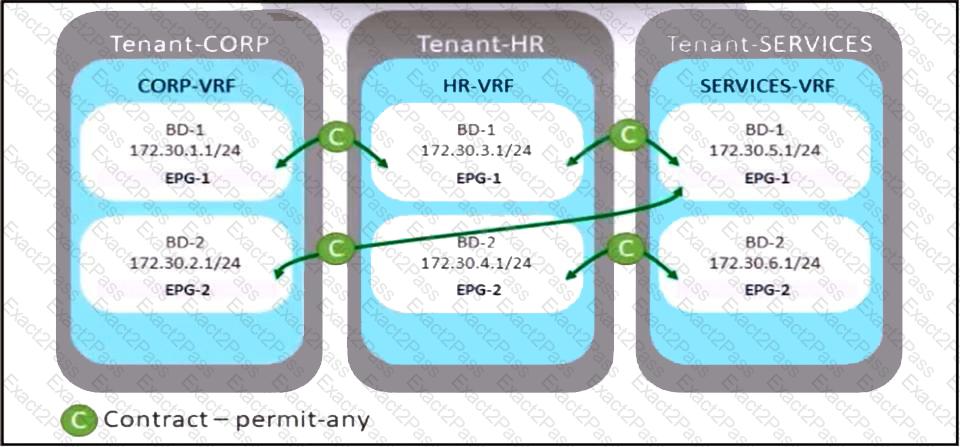
Refer to the exhibit. A company merges three of its departments: CORP, HR, and SERVICES, Currently, the connectivity between departments is achieved by using VRF route leaking. The requirement is to redesign the Cisco ACI networking architecture to communicate between EPGs and BDs from any tenant without configuring contracts or VRF route leaking. Which configuration meets these criteria?
How is broadcast forwarded in Cisco ACI Multi-Pod after ARP flooding is enabled?
An engineer is implementing an out-of-band (OOB) management access for the Cisco ACI fabric. The secure access must meet these requirements:
• Only GUI and secure shell must be allowed to access the management interfaces of the ACIs.
• The only IP ranges that must be permitted to connect the fabric will be 10.10.10.0724 and 192.168.15.0/24.
Which configuration set meets these requirements?
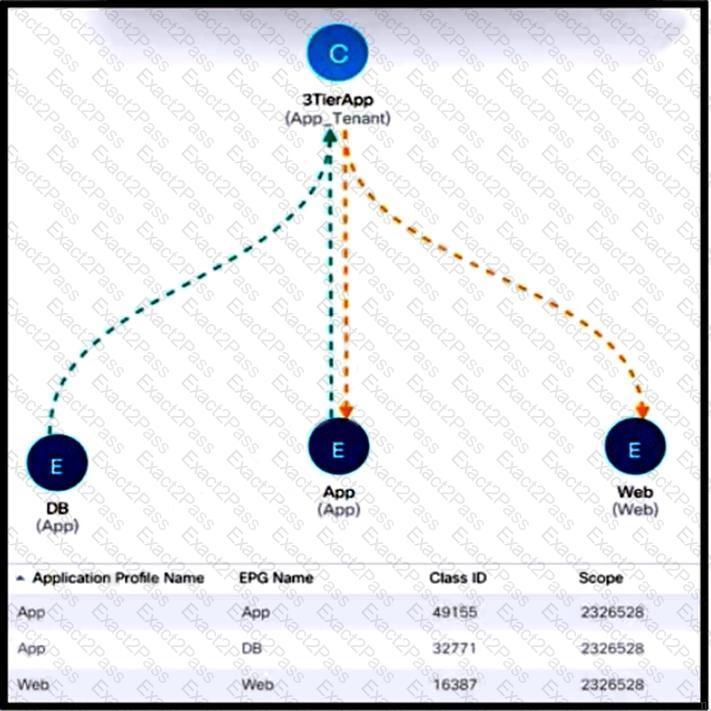
Refer to the exhibit. New e-commerce software is deployed on Cisco ACI fabric. The environment must meet these requirements:
The overall number of contracts must be reduced by reusing the existing contracts within a VRF when possible.
The e-commerce software must communicate only with software EPGs that are part of the same ANP.
The e-commerce software must be prevented from communicating with applications in different ANPs.
Which scope must be selected to meet these requirements?
Which statement about ACI syslog is true or Which statement describes the ACI syslog?
An engineer must set up a Cisco ACI fabric to send Syslog messages related to hardware events, such as chassis line card failures. The messages should be sent to a dedicated Syslog server. Where in the Cisco APIC should the policy be configured to meet this requirement?
A Cisco ACI endpoint group must have its gateway address migrated out of the ACI fabric. An engineer configures EPG-TEST with a static port binding and configures the encap VLAN with the required VLAN. Which configuration set must be used on the bridge domain to meet these requirements?
A Cisco APIC is configured with RADIUS authentication as the default The network administrator must ensure that users can access the APIC GUI with a local account if the RADIUS server is unreachable. Which action must be taken to accomplish this goal?
Refer to the exhibit.
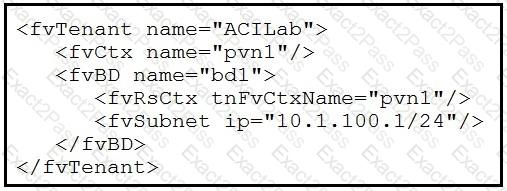
Which two objects are created as a result of the configuration? (Choose two.)
Which table holds IP address, MAC address and VXLAN/VLAN information on a Cisco ACI leaf?
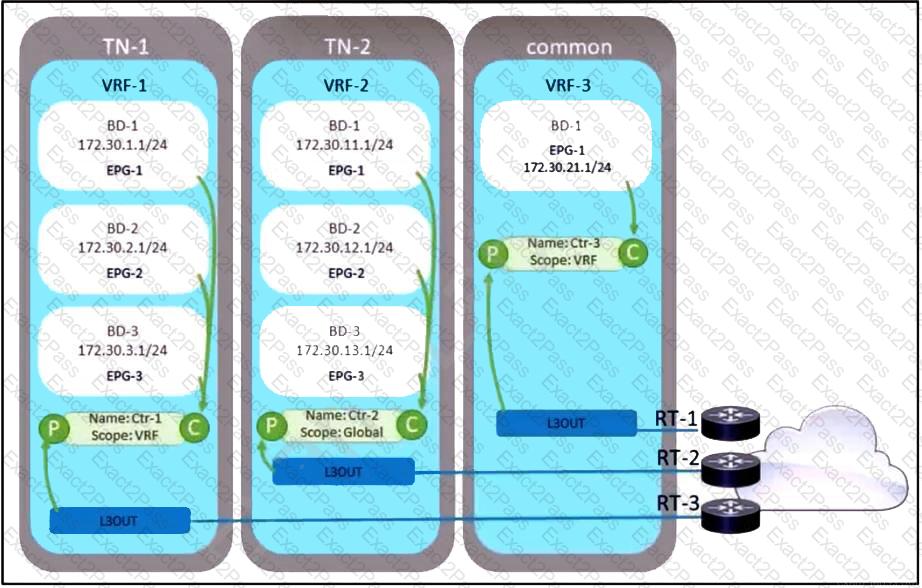
Refer to the exhibit. A company decided to decrease its routing footprint and remove RT-2 and RT-3 devices from its data center. Because of that, the exit point must be created from all the tenants by using the common tenant. Which two configuration tasks must be completed to meet these requirements? (Choose two.)
An engineer plans a Cisco ACI firmware upgrade. The ACI fabric consists of three Cisco APIC controllers, two spine switches, and four leaf switches. Two leaf switches have 1-Gb copper s for bare metal servers, and the other two leaf switches have 10-Gb SFP ports to connect storage. Which set of actions accomplishes an upgrade with minimal disruptions?
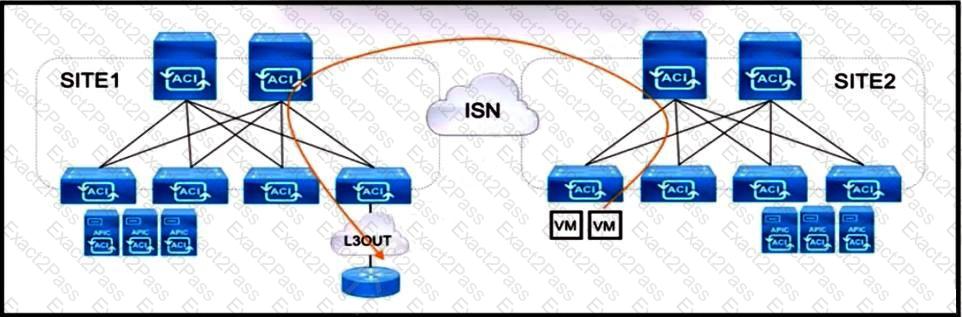
Refer to the exhibit. An engineer is configuring a production Multi-Site solution to provide connectivity from EPGs from a specific site to networks reachable through a remote site L3OUT. All required schema and template objects are already defined. Which additional configuration must be implemented in the Multi-Site Orchestrator to support the cross-site connectivity?
Refer to the exhibit.
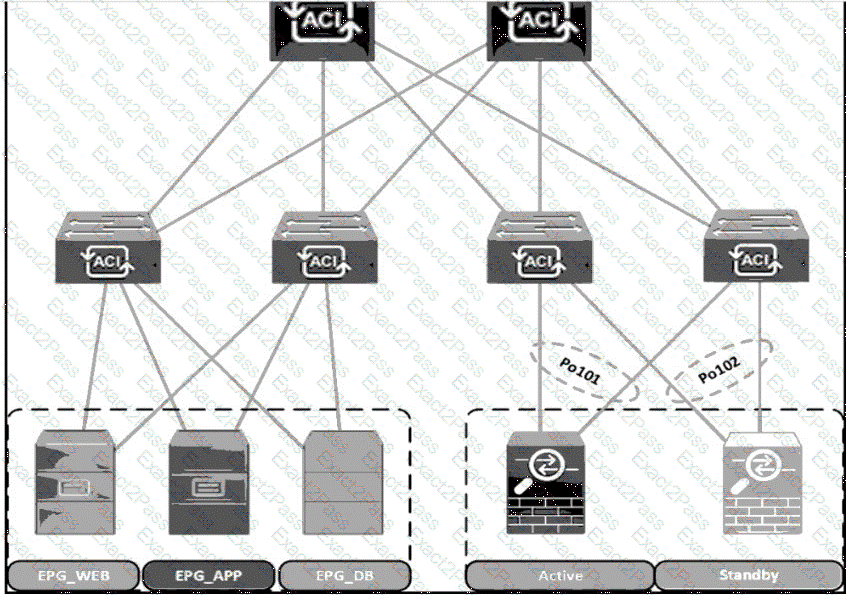
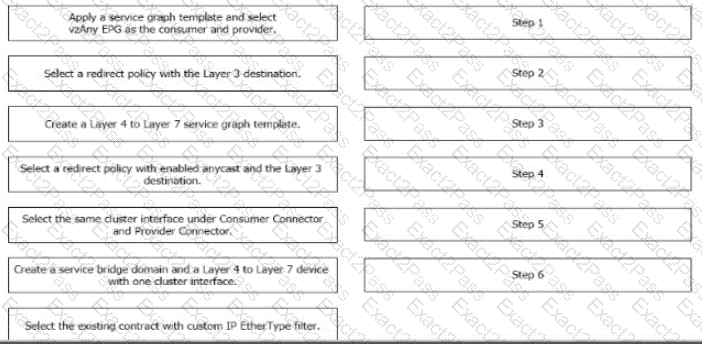
A Cisco ACI fabric is newly deployed, and the security team requires more visibility of all inter-EPG traffic flows. All traffic in a VRF must be forwarded to an existing firewall pair. During fallover, the standby firewall must continue to use the same IP and MAC as the primary firewall. Drag and drop the steps from the left Into the Implementation order on the right to configure the service graph that meets the requirements. (Not all steps are used.)
A customer creates Layer 3 connectivity to the outside network. However, only border leaf switches start receiving destination updates to other networks from the newly created L3Out. The updates must also be propagated to other Cisco ACI leaf switches. The L3Out is linked with the EPGs via a contract. Which action must be taken in the pod policy group to accomplish this goal?
When Cisco ACI connects to an outside Layers 2 network, where does the ACI fabric flood the STP BPDU frame?
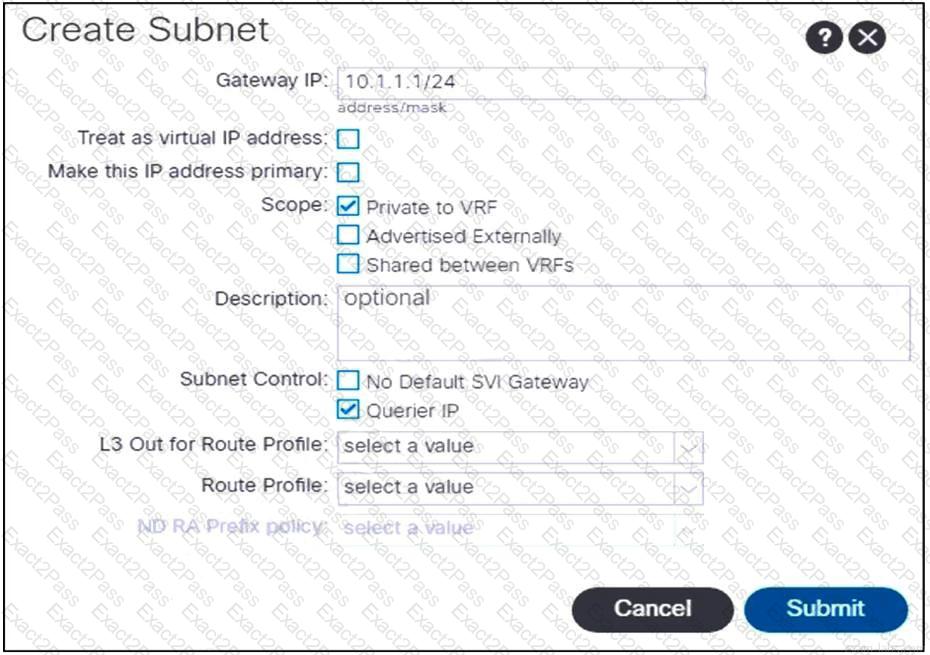
Refer to the exhibit. An engineer configures communication between the EPGs in different tenants. Which action should be taken to create the subnet?
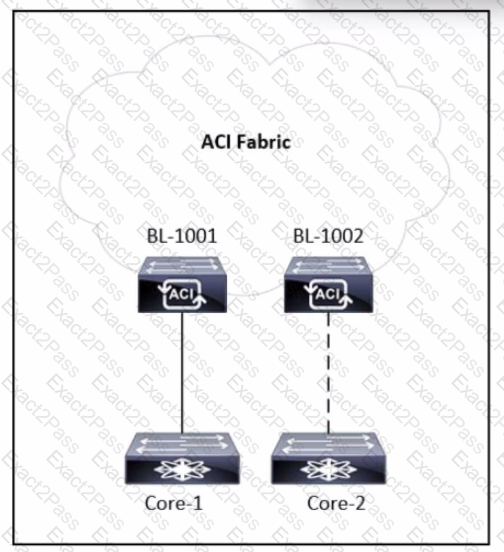
Refer to the exhibit. A tenant is configured with a single L30ut and a single-homed link to the core router called Core-1. An engineer must add a second link to the L30ut that connects to Core-2 router. Which action allows the traffic from Core-2 to BL-1002 to have the same connectivity as the traffic from Core-1 to BL-1001?
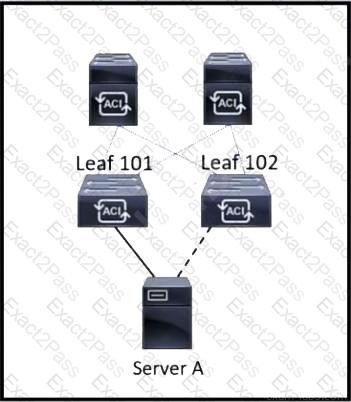
Refer to the exhibit. Server A is connected to the Cisco ACI fabric using two teamed interfaces. One interface in a team is configured as active and the other remains in standby mode. When a failover occurs and the standby interface becomes active, it uses its built-in MAC address to send traffic. Which bridge domain configuration must be applied to resolve the issue?
Which components must be configured for the BGP Route Reflector policy to take effect?
Which setting prevents the learning of Endpoint IP addresses whose subnet does not match the bridge domain subnet?
Refer to the exhibit.
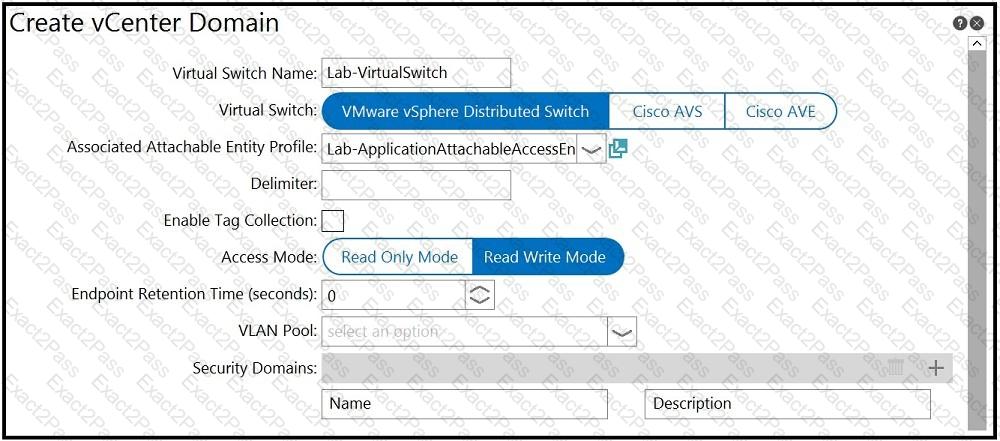
An engineer is integrating a VMware vCenter with Cisco ACI VMM domain configuration. ACI creates port-group names with the format of “Tenant | Application | EPG”. Which configuration option is used to generate port groups with names formatted as “Tenant=Application=EPG”?
An engineer configures a Cisco ACI Multi-Pod for disaster recovery. Which action should be taken for the new nodes to be discoverable by the existing Cisco APICs?
New ESXi hosts are procured in a data center compute expansion project. An engineer must update the
configuration on the Cisco APIC controllers to support the addition of the new servers to the existing VMM
domain. Which action should be taken to support this change?
A network engineer configures the Cisco ACI fabric to connect to vCenter with these requirements:
Port groups must be automatically created on the distributed virtual switch.
Port groups must use the VLAN allocation in the range between 20-30.
The deployment must optimize the CAM space on the leaf switches.
Which set of actions meets these criteria?
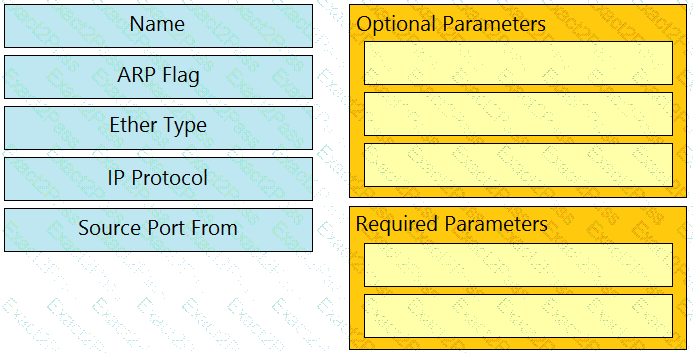
Drag and drop the Cisco ACI filter entry options from the left onto the correct categories on the right indicating what are required or optional parameters.
Refer to the exhibit.
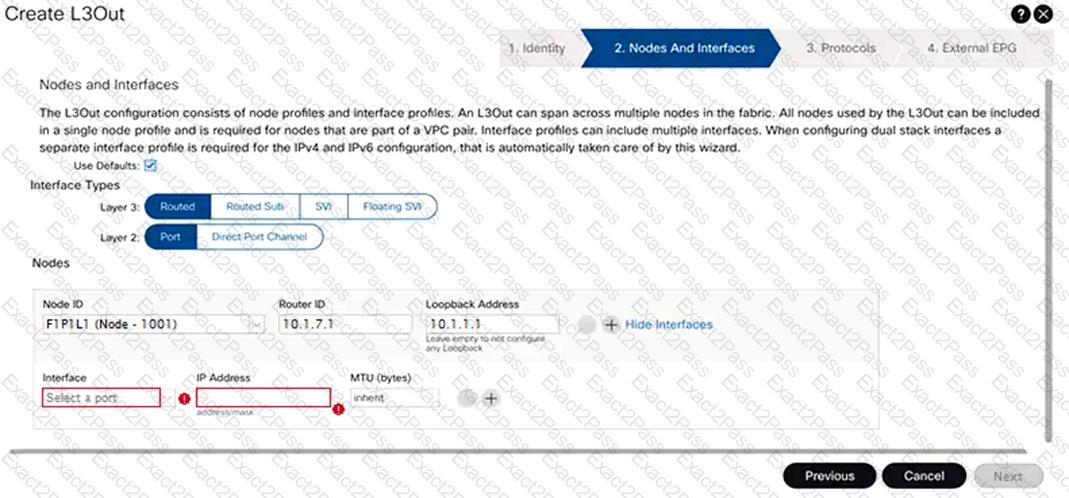
An engineer must configure an L3Out peering with the backbone network. The L3Out must forward unicast and multicast traffic over the link. Which two methods should be used to configure L3Out to meet these requirements? (Choose two.)
The existing network and ACI fabric have been connected to support workload migration. Servers will physically terminate at the Cisco ACI, but their gateway must stay in the existing network. The solution needs to adhere to Cisco’s best practices. The engineer started configuring the relevant Bridge Domain and needs to complete the configuration. Which group of settings are required to meet these requirements?
When configuring Cisco ACI VMM domain integration with VMware vCenter, which object is created in vCenter?
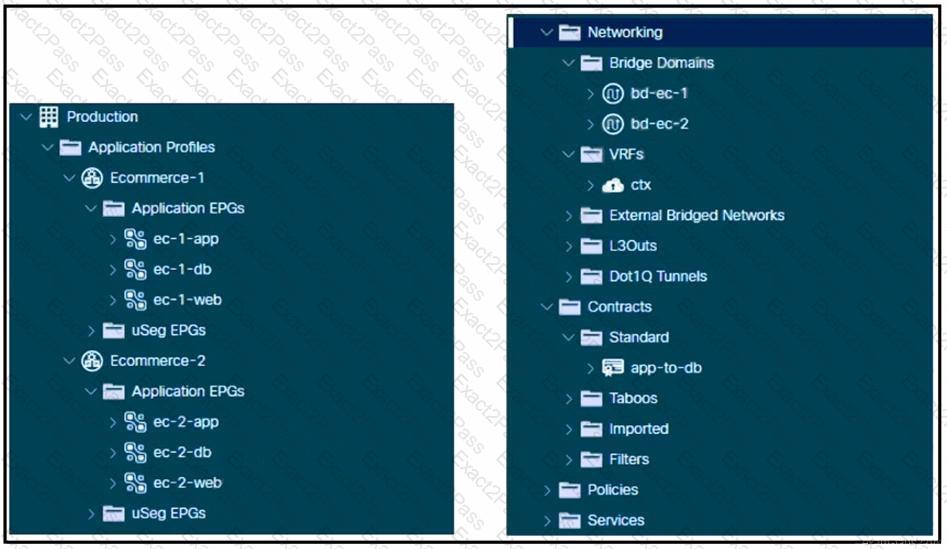
Refer to the exhibit. A Cisco ACI environment hosts two e-commerce applications. The default contract from a common tenant between different application tiers is used, and the applications work as expected. The customer wants to move to more specific contracts to prevent unwanted traffic between EPGs. A network administrator creates the app-to-db contract to meet this objective for the application and database tiers. The application EPGs must communicate only with their respective database EPGs. How should this contract be configured to meet this requirement?
A customer is deploying a new application across two ACI pods that is sensitive to latency and jitter. The application sets the DSCP values of packets to AF31 and CS6, respectively. Which configuration changes must be made on the APIC to support the new application and prevent packets from being delayed or dropped between pods?
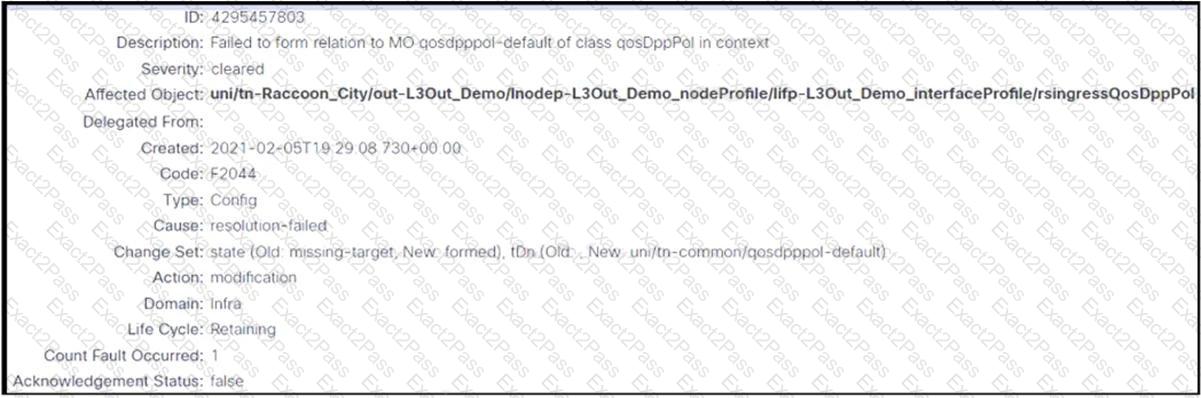
Refer to the exhibit. An engineer configures an L3Out but receives the error presented. Which action clears the fault?
An engineer configures port-12 on Leaf-101 and Leaf-102 to connect to a new server, SVR-12. The new server will belong to EPG-12 and use encap VLAN-1212. The engineer configured SVR-12 as a VPC member port and statically bound the VPC member port to EPG-12. Which additional step must the engineer take to configure connectivity?
In a Cisco ACI Multi-Site fabric, the Inter-Site BUM Traffic Allow option is enabled in a specific stretched bridge domain. What is used to forward BUM traffic to all endpoints in the same broadcast domain?