An engineer is tasked to improve throughput for connection-oriented traffic by decreasing round-trip latency. Which configuration will achieve this goal?
The Cisco SD-WAN engineer is configuring service chaining for a next-generation firewall located at the headquarters. Which configuration creates the service?
A)
B)
C)
D)
Which percentage for total memory or total CPU usage for a device is classified as normal in the WAN Edge Health pane?
Refer to the exhibit.
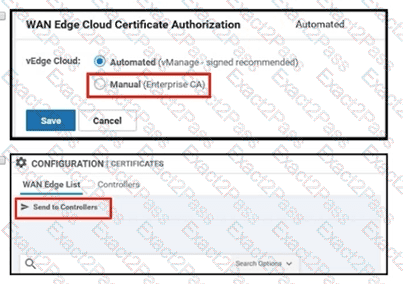
Which two configurations are needed to get the WAN Edges registered with the controllers when certificates are used? (Choose two)
Refer to the exhibit.
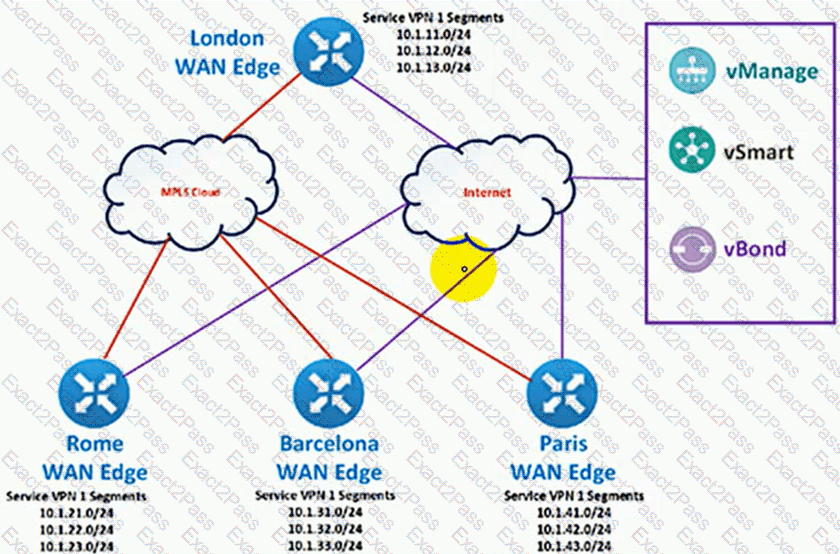
The Cisco SD-WAN network is configured with a default full-mesh topology. An engineer wants Paris WAN Edge to use the Internet HOC as the preferred TLOC for MSN Messenger and AOL Messenger traffic. Which policy achieves this goal?
A)

B)
C)

D)

What are two benefits of installing Cisco SD-WAN controllers on cloud-hosted services? (Choose two.)
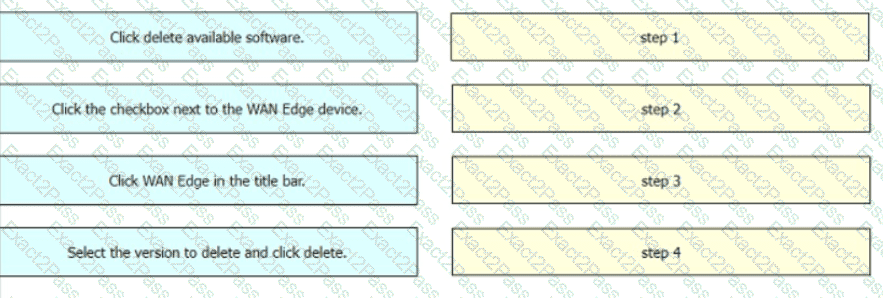
Drag and drop the steps from the left Into the order on the right to delete a software image for a WAN Edge router starting with Maintenance > Software Upgrade > Device list on vManage.
Which protocol is used to propagate multicast join requests over the Cisco SD-WAN fabric?
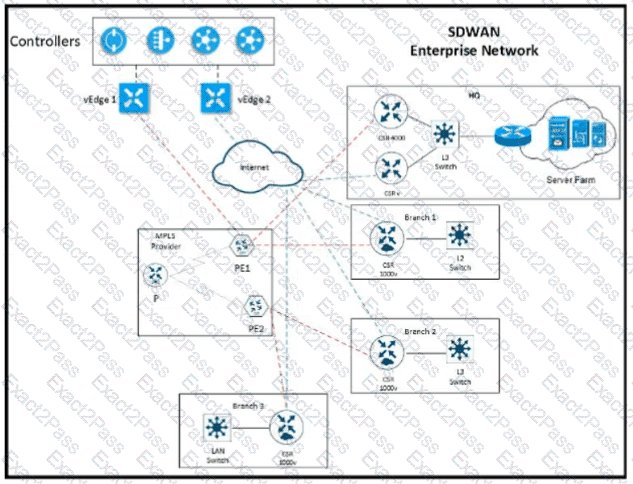
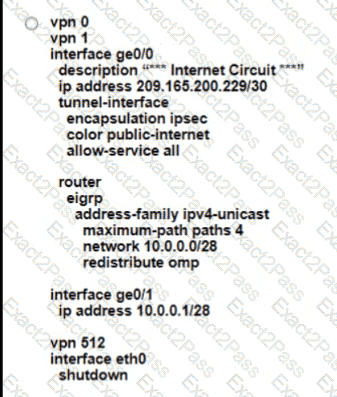
Refer to the exhibit The network team must configure ElGRP peering at HQ with devices in the service VPN connected to WAN Edge CSRv. CSRv is currently configured with
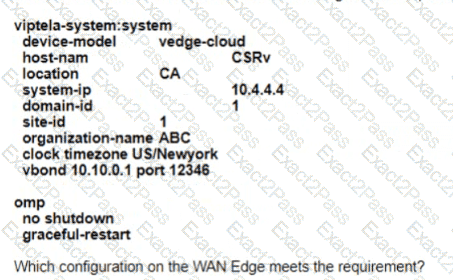
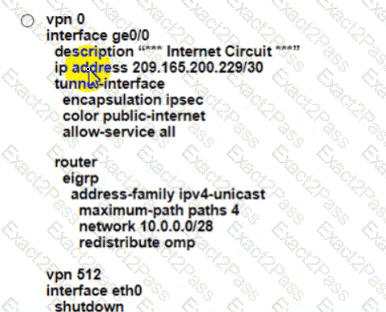
Which configuration on the WAN Edge meets the requiremnet
A)
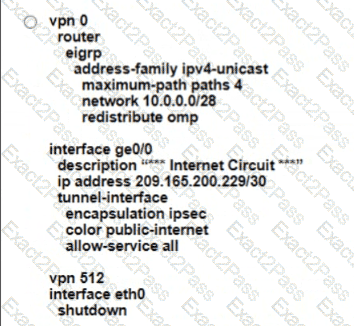
B)
C)

D)
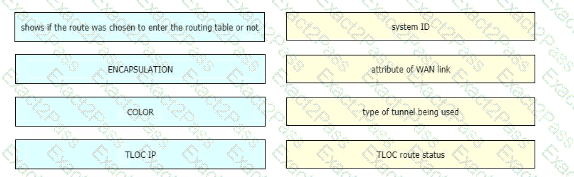
Drag and drop the route verification output from show omp tlocs from the left onto the correct explanations on the right.
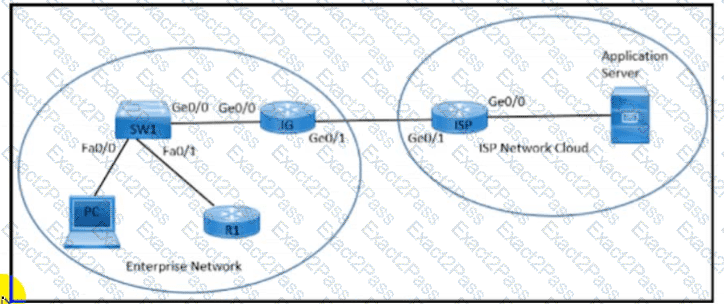
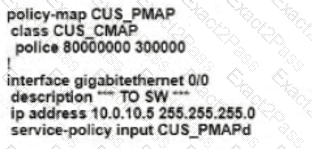
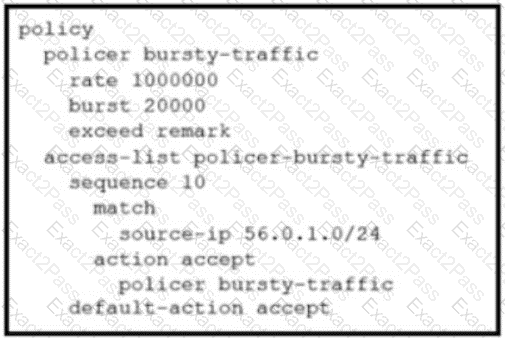
Refer to the exhibit. An enterprise network is connected with an ISP network on an 80 Mbps bandwidth link. The network operation team observes 100 Mbps traffic on the 1Gig-ISP link during peak hours Which configuration provides bandwidth control to avoid traffic congestion during peak hours?
A)
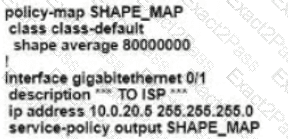
B)
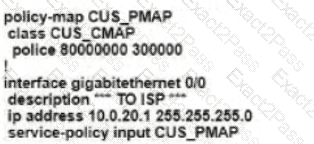
C)
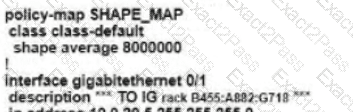
D)
Which type of lists are used to group related items via an application-aware routing policy under the policy lists command hierarchy on vSmart controllers?
Which queue must an engineer configure for control and BFD traffic for convergence on a WAN Edge router?
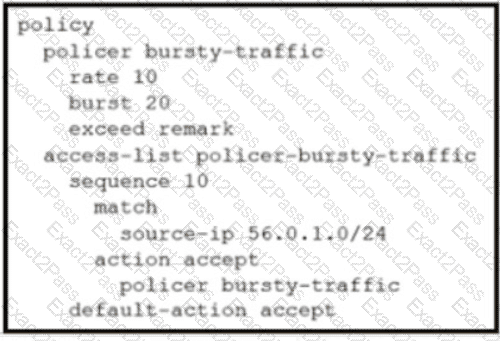
An engineer configures policing with a rate of 125 Bps and a burst rate of 8000 bits, as shown here:
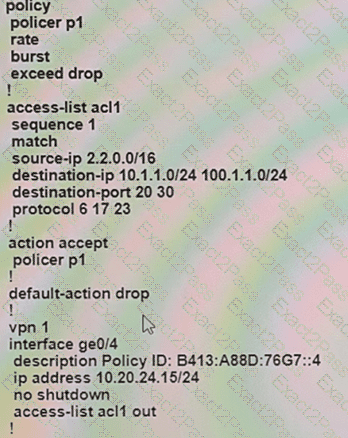
Which configuration completes this task?
What is the threshold to generate a warning alert about CPU or memory usage on a WAN Edge router?
How is multicast routing enabled on devices in the Cisco SD-WAN overlay network?
A policy is created to influence routing in the network using a group of prefixes. What policy application will achieve this goal when applied to a site list?
An engineer must apply the configuration for certificate installation to vBond Orchestrator and vSmart Controller. Which configuration accomplishes this task?
The network administrator is configuring a QoS scheduling policy on traffic received from transport side tunnels on WAN Edge 5000 routers at location 406141498 Which command must be configured on these devices?
Which routes are similar to the IP route advertisements when the routing information of WAN Edge routers is learned from the local site and local routing protocols?
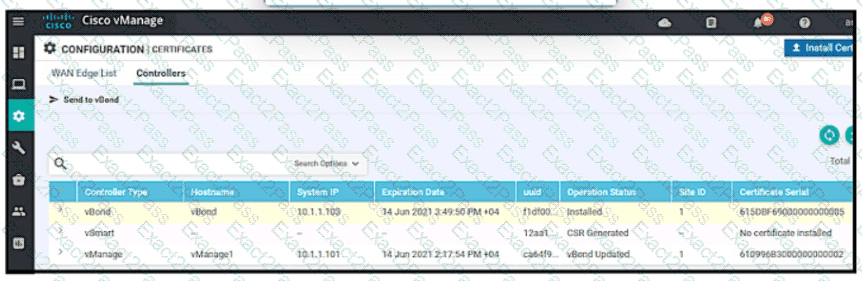
Refer to the exhibit vManage and vBond have an issue establishing a connection to vSmart Which two actions does the administrator take to fix the issue? (Choose two)
Install the certificate received from the certificate server.

Refer to the exhibit. An administrator is configuring a policy in addition to an existing hub-and-spoke policy for two sites that should directly communicate with each other. How is this policy configured?
Which action is performed during the onboarding process when a WAN Edge router is connected to ZTP server ztp.viptela com?
Refer to the exhibit.
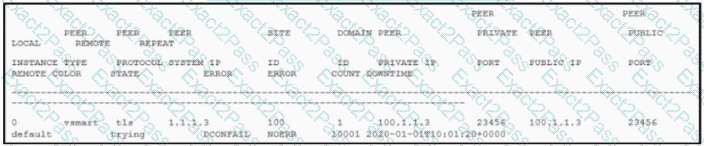
The control connection is failing. Which action resolves the issue?
Exhibit.
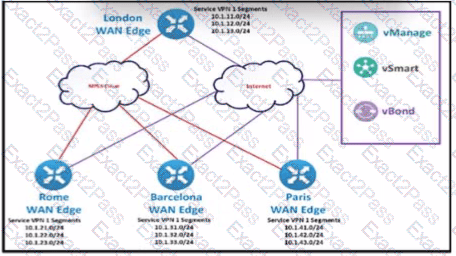
The SD-WAN network is configured with a default full-mash topology. An engineer wants Barcelona and Paris to communicate to each other through the London site using a control Which control policy configuration accomplishes the task?
A)

B)
C)
D)
An administrator must deploy the controllers using the On-Prem method while vManage can access the PnP portal from inside How are the two WAN Edge authorized allowed lists to be made available to vManage? (Choose two)

What happens if the intelligent proxy is unreachable in the Cisco SD-WAN network?
Which two products are used to deploy Cisco WAN Edge Router virtual platforms? (Choose two.)
How should the IP addresses be assigned for all members of a Cisco vManage cluster located in the same data center?
Which two platforms for the Cisco SD-WAN architecture are deployable in a hypervisor on-premises or in IAAS Cloud? (Choose two.)
An engineer must improve video quality by limiting HTTP traffic to the Internet without any failover. Which configuration in vManage achieves this goal?

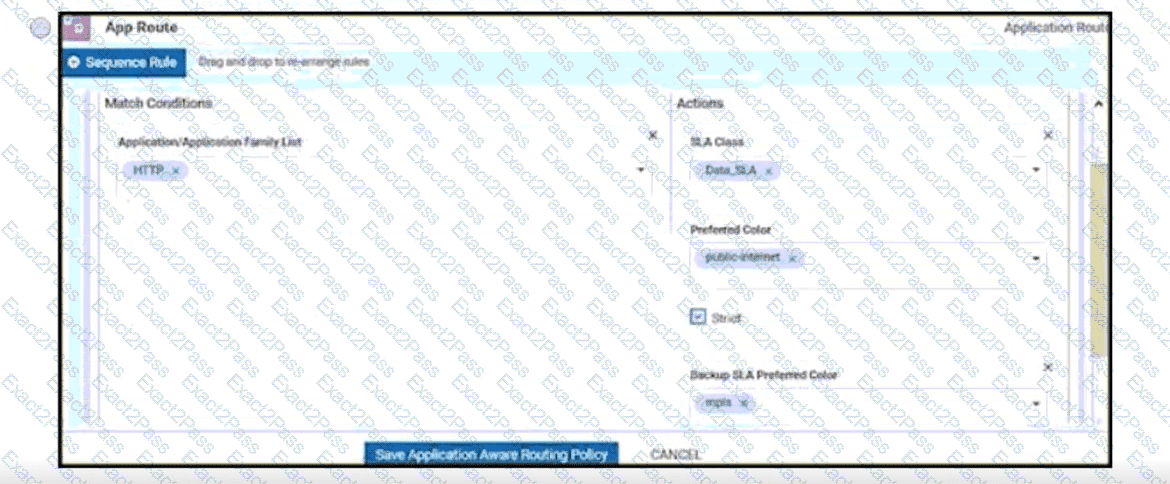
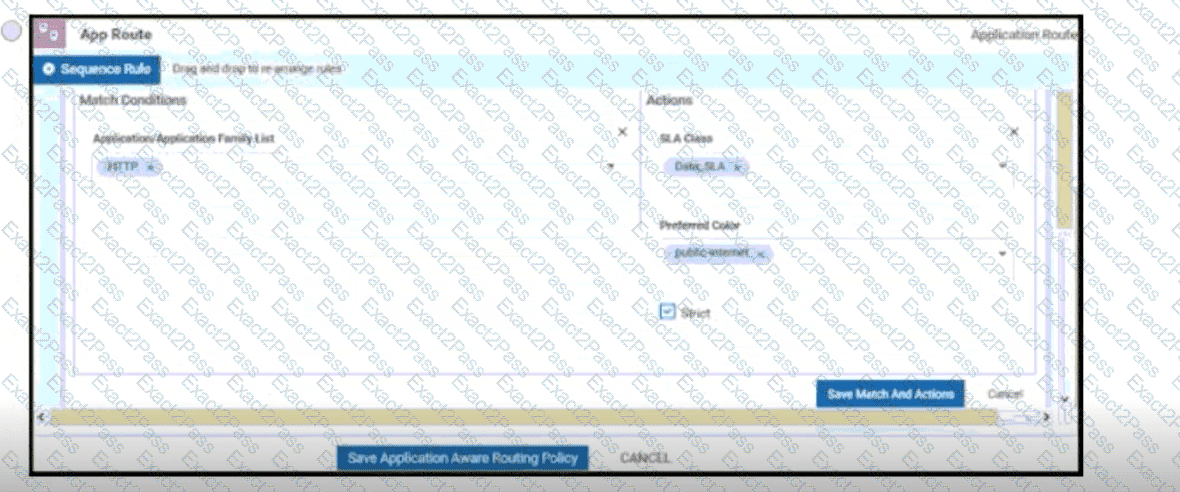
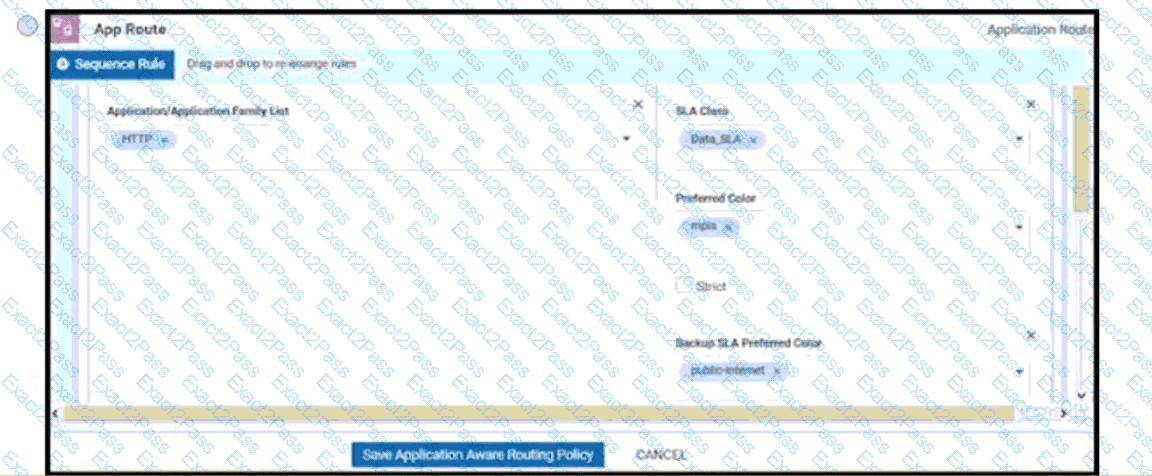
When a WAN Edge device joins the SD-WAN overlay, which Cisco SD-WAN components orchestrates the connection between the WAN Edge device and a vSmart controller?
What is the maximum number of IPsec that are temporarily created and converged on a new set if IPsec Sas in the pairwise keys process during a simultaneous rekey?
I
In which file format is a critical severity report downloaded from the MONITOR I ALARM tab in the vManage GUI?
What is a requirement for deployment of on-premises vBond controllers through the Cisco Plug and Play Connect process?
What is the minimum Red Hat Enterprise Linux operating system requirement for a Cisco SD-WAN controller deployment via KVM?
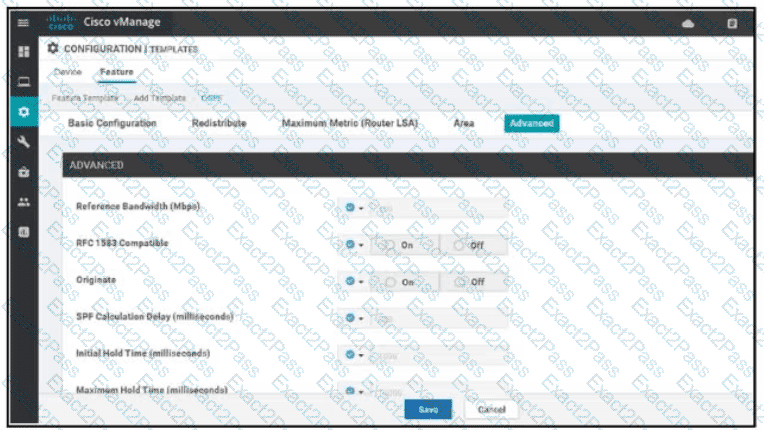
Refer to the exhibit. A network administrator is configuring OSPF advanced configuration pararmeters from a template using the vManager GUI for a branch WAN Edge router to calculate the cost of summary routes to an ASBR. Which action achieves this configuration?
A vEdge platform is sending VRRP advertisement messages every 10 seconds. Which value configures the router back to the default timer?
Which OMP route is selected for equal OMP route preference values on WAN Edge routers?
Refer to the exhibit.
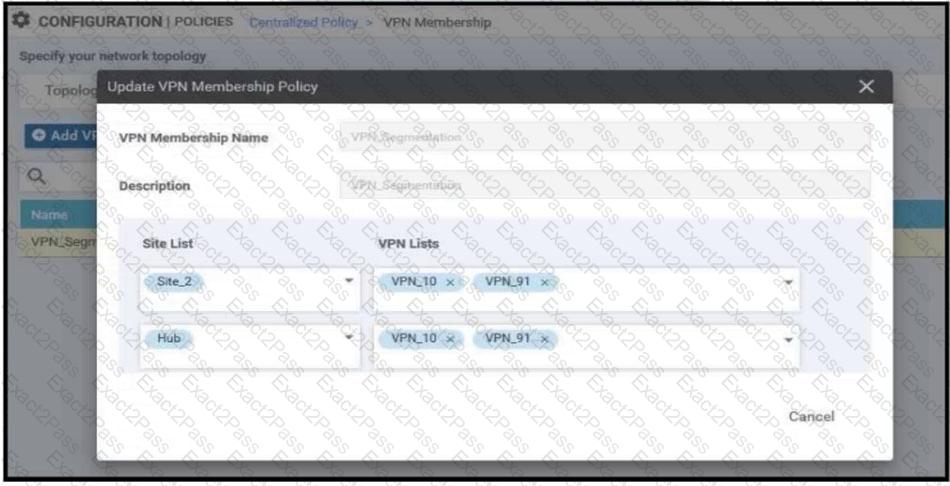
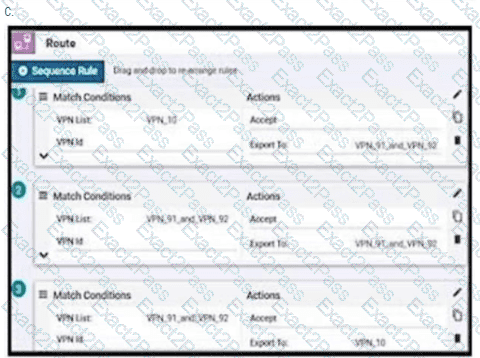
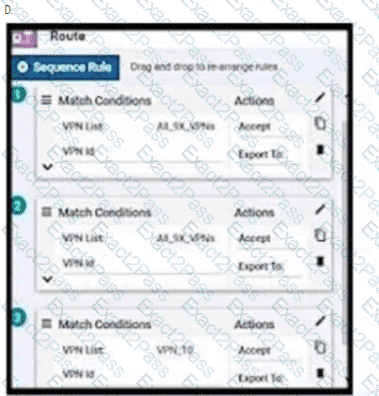
An enterprise has hub and spoke topology where it has several VPNs. An engineer must allow users in VPN91 to reach users in VPN92 and VPN10 to reach VPN91 and VPN92. Which configuration meets these requirements?
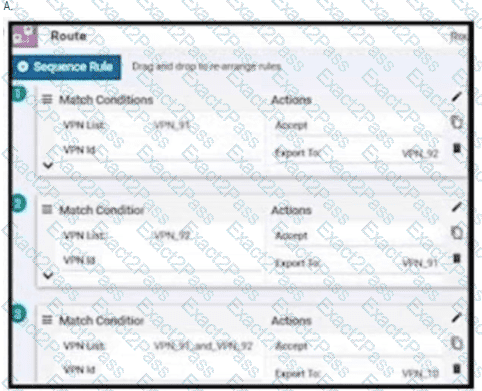
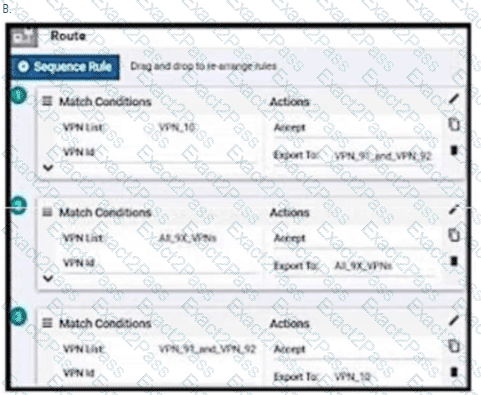
Which two services are critical for zero touch provisioning on-boarding? (Choose two)
Which component is used for stateful inspection of TCP, UDP. and ICMP flows in Cisco SD-WAN firewall policies?
Which Cisco SD-WAN component facilitates the initial communication between WAN Edge devices to join the fabric?
Which protocol runs between the vSmart controllers and WAN Edge routers when the vSmart controller acts like a route reflector?
What is the OMP graceful restart default value on vSmart controllers and WAN Edge routers?
Which service VPN must be reachable from all WAN Edge devices and the controllers?
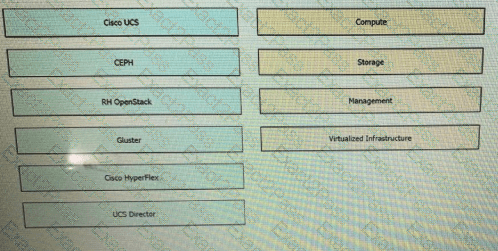
Drag and drop the components from the left onto the corresponding Cisco NFV infrastructure Building Blocks on the right. Not all options are used.
What are the default username and password for vSmart Controller when it is installed on a VMware ESXi hypervisor'?
In the Cisco SD_WAN solution, vSmart controller is responsible for which two actions? (Choose two.)
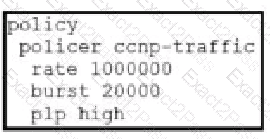
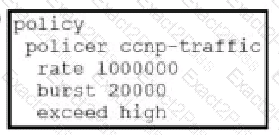
Which configuration changes the packet loss priority from low to highly?
A)
B)
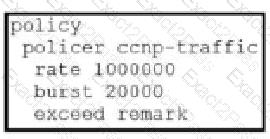
C)
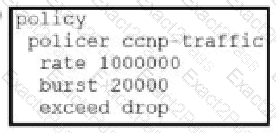
D)
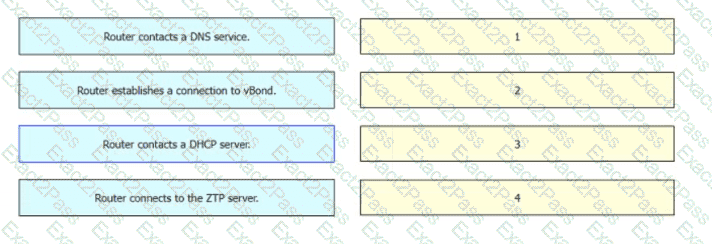
Drag and drop the steps from the left into the sequence on the right for a WAN Edge router after powering on for zero touch provisioning.
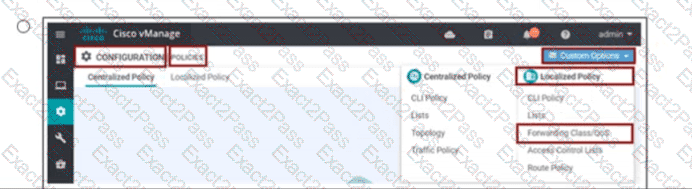
Which pathway under Monitor > Network > Select Device is used to verify service insertion configuration?
An administrator must configure an ACL for traffic coming in from the service-side VPN on a specific WAN device with circuit ID 391897770. Which policy must be used to configure this ACL?
Refer to the exhibit.

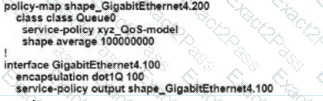
Which shaping-rate does the engineer use to shape traffic at 9 Mbps?
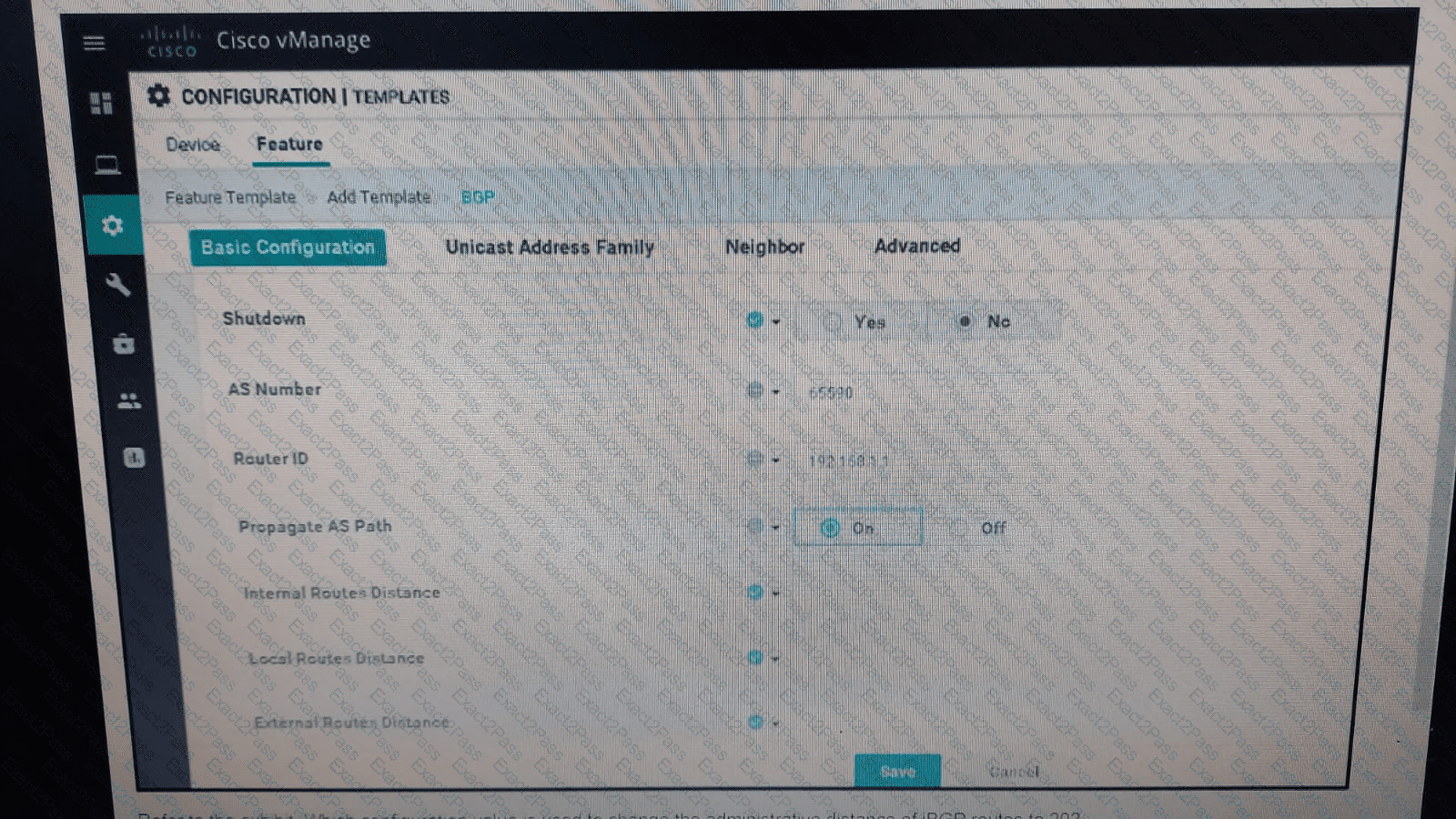
Refer to the exhibit. Which configuration value is used to change the administrative distance of iBGP routes to 20?
Refer to the exhibit.
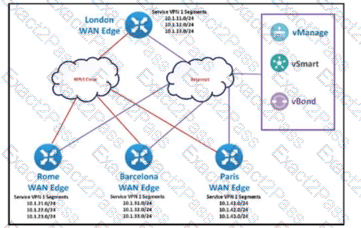
The SD-WAN network is configured with a default full-mesh topology. The SD-WAN engineer wants the Barcelona WAN Edge to use MPLS TLOC as the preferred TLOC when communicating with Rome site. Which configuration must the engineer use to create a list to select MPLS color toward the Rome TLOC?
A)
B)
C)

D)
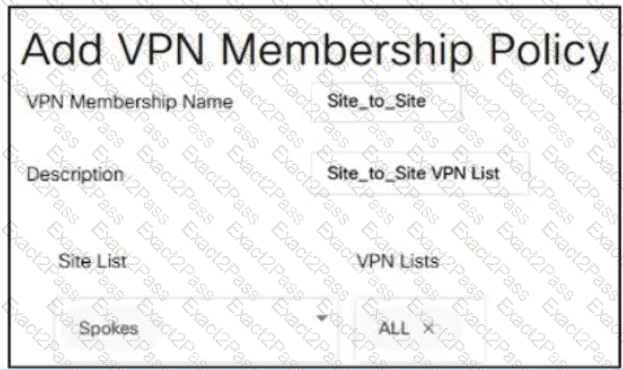
Refer to the exhibit.
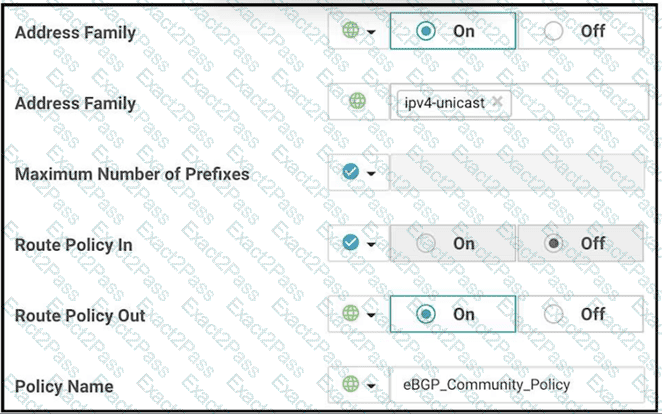
The engineer must assign community tags to 3 of its 74 critical server networks as soon as that are advertised to BGP peers. These server networks must not be advertised outside AS. Which configuration fulfill this requirement?
A)

B)

C)

D)

Which type of certificate is installed on vManage for a user to access vManage via a web browser?
Which table is used by the vSmart controller to maintain service routes of the WAN Edge routers in the hub and local branches?
An engineer is configuring a data policy for IPv4 prefixes for a single WAN Edge device on a site with multiple WAN Edge devices How is this policy added using the policy configuration wizard?
Which component of the Cisco SD-WAN architecture oversees the control plane of overlay network to establish, adjust, and maintain the connections between the WAN Edge devices that form the Cisco SD-WAN fabric?
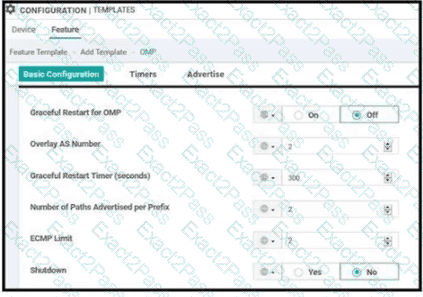
A company must avoid downtime at the remote sites and data plane to continue forwarding traffic between WAN Edge devices if the branch router loses connectivity to its OMP peers Which configuration meets the requirement?
A)
B)
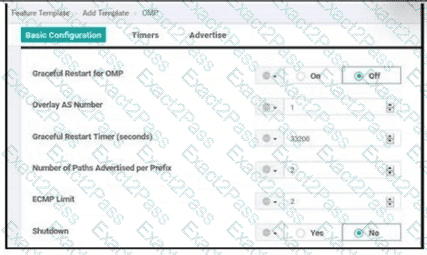
C)

D)

Which issue triggers the Cisco Umbrella resolver to toward DNS requests to the intelligent proxy?
Which issue triggers the Cisco Umbrella resolver to toward DNS requests to the intelligent proxy?
A Cisco SD-WAN customer has a requirement to calculate the SHA value for files as they pass through the device to see the returned disposition and determine if the file is good, unknown or malicious. The customer also wants to perform real-time traffic analysis and generate alerts when threats are detected Which two Cisco SD-WAN solutions meet the requirements? (Choose two.)
Which multicast component is irrelevant when defining a multicast replicator outside the local network without any multicast sources or receivers?
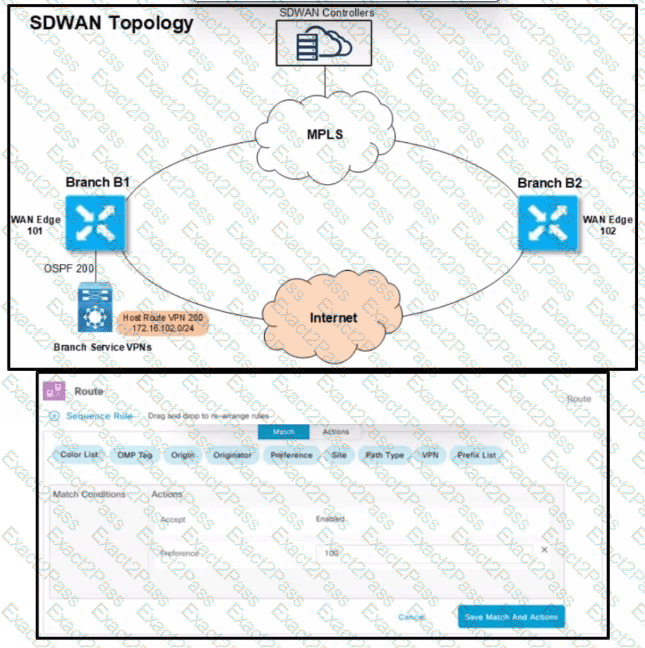
Refer to the exhibit. An engineer must configure the Overlay Management Protocol route preference so that when B2 tries to reach host routes advertised by B1 it always chooses the MPLS circuit. Which two match conditions must be configured to accomplish this task? (Choose two.)
A network administrator configures SNMFV3 on a Cisco WAN Edge router from CL I for monitoring purposes How many characters are supported by the snmp user username command?
How many vCPUs and how much RAM are recommended to run the vSmart controller on the KVM server for 251 to 1000 devices in software version 20.4.x?
Which policy configures an application-aware routing policy under Configuration > Policies?
Which device information is requited on PNP/ZTP to support the zero-touch onboarding process?
Which two advanced security features are available on the Cisco SD-WAN WAN Edge (vEdge) device? (Choose two.)
Refer to the exhibit.

An engineer is troubleshooting a control connection Issue. What does "connect" mean in this how control connections output?
Which TCP Optimization feature is used by WAN Edge to prevent unnecessary retransmissions and large initial TCP window sizes to maximize throughput and achieve a better quality?
An engineer modifies a data policy for DIA in VPN 67. The location has two Internet-bound circuits. Only the web browsing traffic must be admitted for DIA. without further discrimination about which transport to use.
Here is the existing data policy configuration:

Which policy configuration sequence meets the requirements?
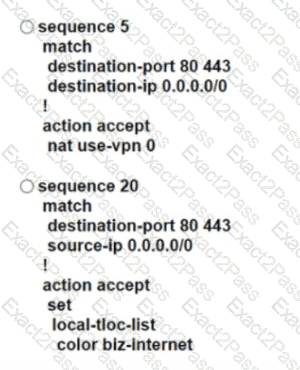
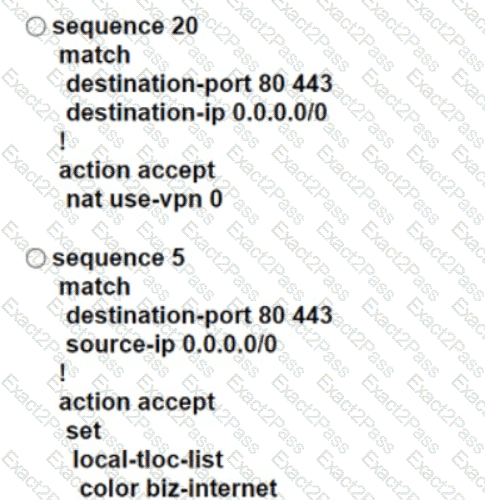
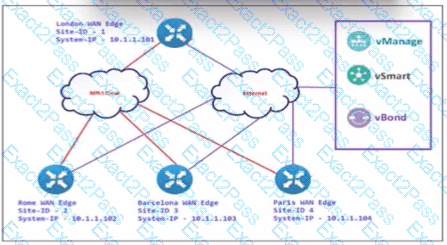
An engineer configures Rome WAN Edge 10 use MPLS cloud as the preferred link to reach Paris WAN Edge and use biz-internet as a backup. Which policy configuration must be led in the outbound direction toward Rome to accomplish the task?
A)

B)

C)

D)

An engineer must avoid routing loops on the SD-WAN fabric for routes advertised between data center sites Which BGP loop prevention attribute must be configured on the routers to meet this requirement?
How do WAN Edge devices operate when vSmart is inaccessible or fails to be reached by the WAN Edge?
What must an engineer conewef when decoying an SD-WAN on-pfemlses architecture based on ESXi hypervisor?
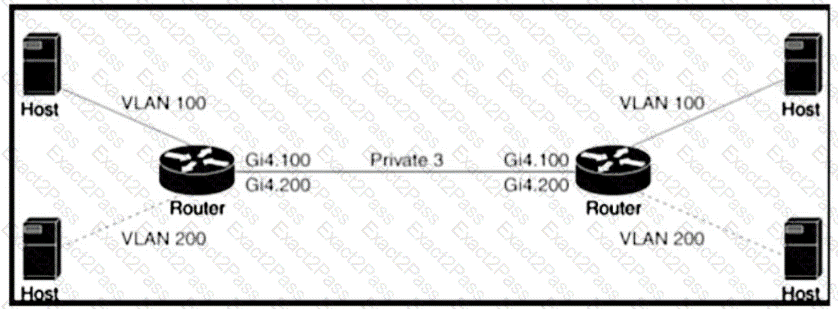
Refer to the exhibit An engineer is configuring a QoS policy to shape traffic for VLAN 100 on a subinterface Which policy configuration accomplishes the task?
A)
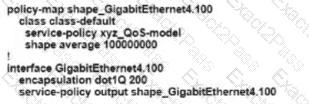
B)
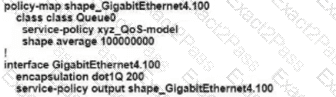
C)
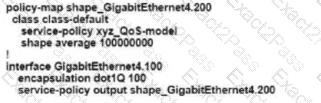
D)
Which secure tunnel type should be used to connect one WAN Edge router to other WAN Edge routers?
An engineer must create a QoS policy by creating a class map and assigning it to the LLQ queue on a WAN Edge router Which configuration accomplishes the task?
A)
 B)
B)
C)
D)
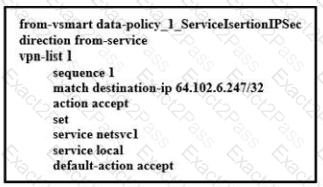
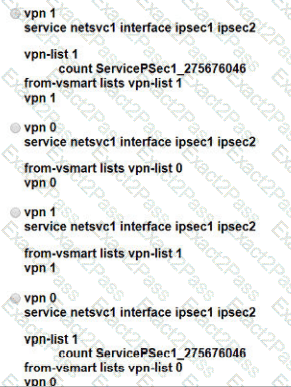
Refer to the exhibit, which configuration configures IPsec tunnels in active and standby?
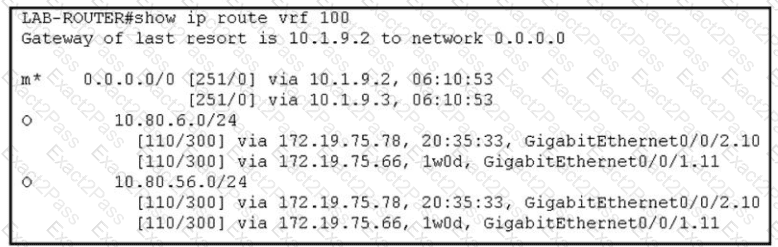
Refer to the exhibit. The network administrator has configured a centralized topology policy that results in the displayed routing table at a branch office. Which two configurations are verified by the output? [Choose two.)
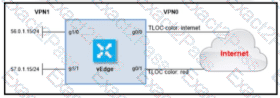
Refer to the exhibit. The ge0/0 interface connects to a 30-MB link. A network administrator wants to always have 10 MB available for high priority traffic. When lower-priority traffic busts exceed 20 MB. Traffic should be redirected to the second WAN interface ge0/1. Which set of configurations accomplishes this task?
A)

B)

C)
D)
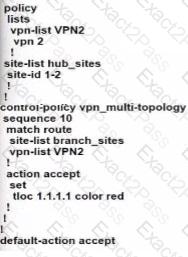
Which control policy assigned to Drenches in the out direction establishes a strict hub-and-spoke topology tor VPN2?
A)

B)
C)

D)
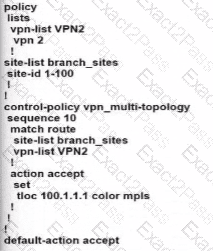
Which attributes are configured to uniquely Identify and represent a TLOC route?
Which two image formats are supported for controller codes? (Choose two.)
Which component is used to optimize the multicast distribution tree enabled through the multicast network?
Refer to the exhibit The network team must configure application-aware routing for the Service VPN 50.0.0.0/16 The SLA must prefer MPLS for video traffic but the remaining traffic must use a public network What must be defined other than applications before the application-aware policy is create?
An engineer is adding a tenant with location JD 306432373 in vManage. What is the maximum number of alphanumeric characters that are accepted in the tenant name field?
What is a benefit of the application aware firewall feature in the Cisco SD-WAN solution?
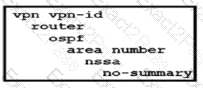
Which OSPF command makes the WAN Edge router a less preferred exit from a site with a dual WAN Edge design?
A)
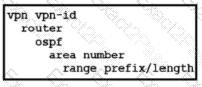
B)
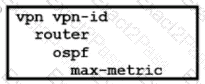
C)

D)
Which type of connection is created between a host VNet and a transit VNet when configuring Cloud OnRamp for laaS?
A network administrator configures SNMPv3 on a Cisco WAN Edge router from CLI for monitoring purposes How many characters are supported by the snmp user
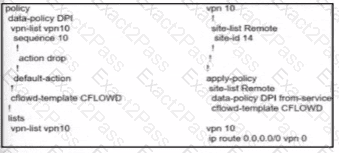
Which configuration allows VPN 10 traffic to have direct internet access locally from the WAN Edge device?
A)

B)

C)
D)

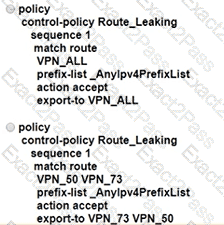
An enterprise has several sites with multiple VPNs that are isolated from each other A new requirement came where users in VPN 73 must be able to talk to users in VPN 50 Which configuration meets this requirement?


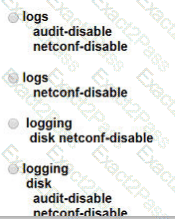
Refer to the exhibit. Which configuration stops Netconf CLI logging on WAN Edge devices during migration?
Refer to the exhibit.
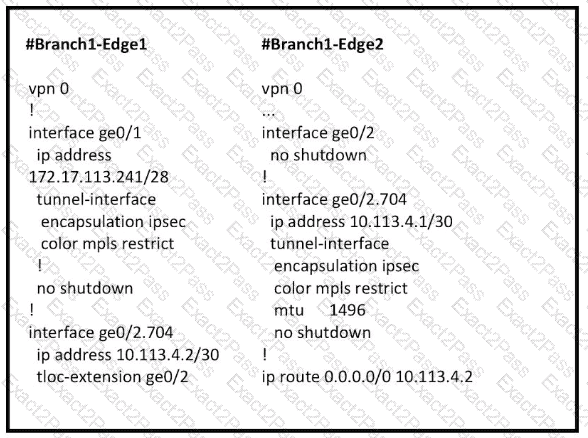
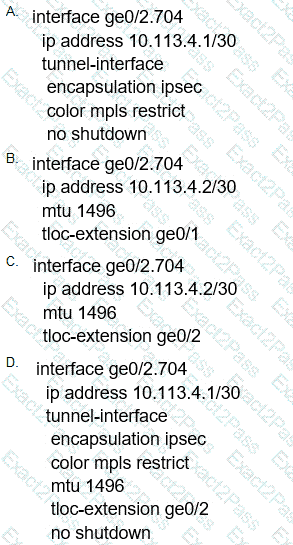
Which configuration change is needed to configure the tloc-extention on Branch1-Edge1?
Which IP address must be reachable by a WAN Edge device for the ZIP process to work?
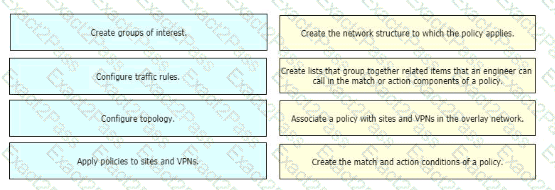
Drag and drop the vManage policy configuration procedures from the left onto the correct definitions on the right.