Refer to the exhibit.
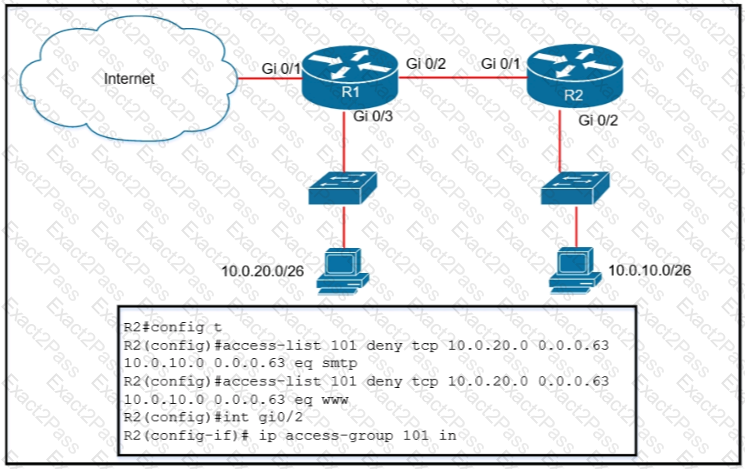
An extended ACL has been configured and applied to router R2 The configuration failed to work as intended Which two
changes stop outbound traffic on TCP ports 25 and 80 to 10.0.20 0 26 from the 10.0.10 0/26 subnet while still allowing all other traffic? (Choose
two )
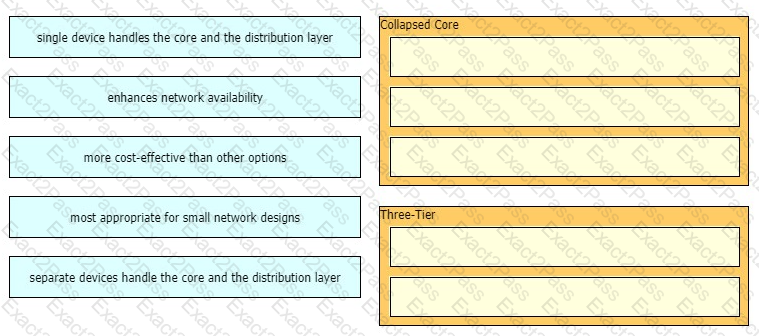
Drag and drop the characteristics of network architectures from the left onto the type of architecture on the right.
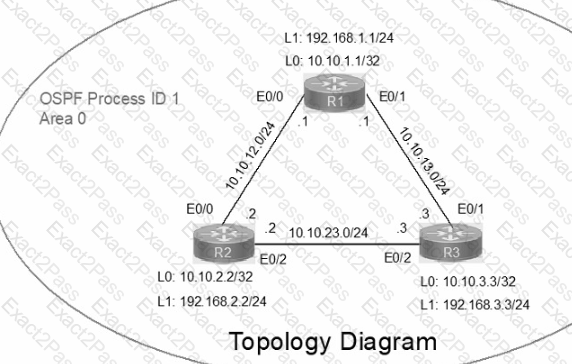
IP connectivity between the three routers is configured. OSPF adjacencies must be established.
1. Configure R1 and R2 Router IDs using the interface IP addresses from the link that is shared between them.
2. Configure the R2 links with a max value facing R1 and R3. R2 must become the DR. R1 and R3 links facing R2 must remain with the default OSPF configuration for DR election. Verify the configuration after clearing the OSPF process.
3. Using a host wildcard mask, configure all three routers to advertise their respective Loopback1 networks.
4. Configure the link between R1 and R3 to disable their ability to add other OSPF routers.
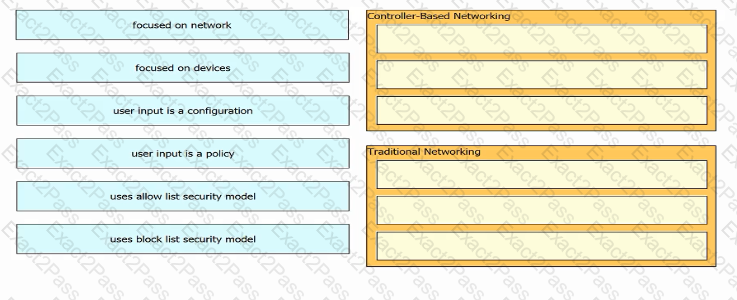
What is the main difference between traditional networks and controller-based networking?
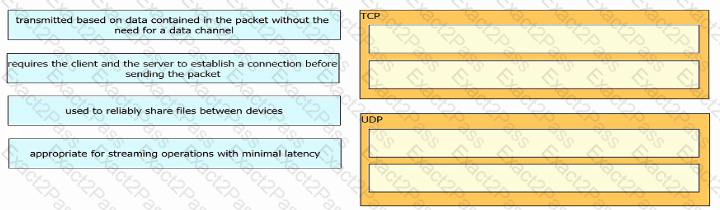
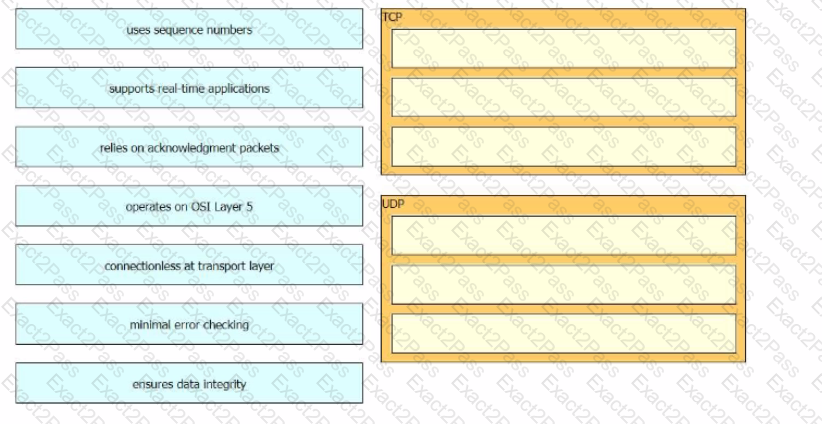
What is the difference regarding reliability and communication type between TCP and UDP?
What is a function of the core and distribution layers in a collapsed-core architecture?
Refer to the exhibit.
Which per-hop QoS behavior is R1 applying to incoming packets?
Refer to the exhibit.
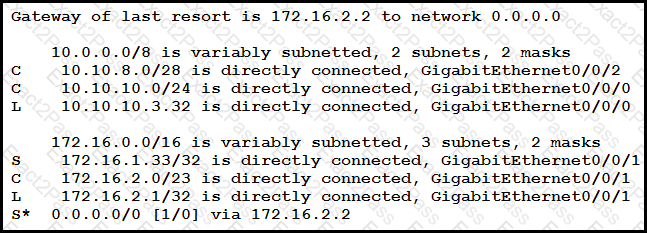
A packet sourced from 10.10.10.1 is destined for 10.10.8.14. What is the subnet mask of the destination route?
Which channel-group mode must be configured when multiple distribution interfaces connected to a WLC are bundled?
What is an advantage of using auto mode versus static mode for power allocation when an access point is connected to a PoE switch port?
What are two characteristics of the distribution layer in a three-tier network architecture? (Choose two.)
Which attribute does a router use to select the best path when two or more different routes to the same destination exist from two different routing protocols.
Drag and drop the functions from the left onto the correct network components on the right
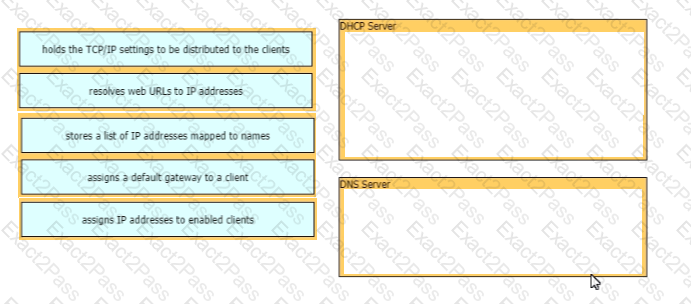
On workstations running Microsoft Windows, which protocol provides the default gateway for the device?
What are two improvements provided by automation for network management in an SDN environment? (Choose two)
TION NO: 117

Refer to the exhibit. After the configuration is applied, the two routers fail to establish an OSPF neighbor relationship. what is the reason for the problem?
Refer to the exhibit.
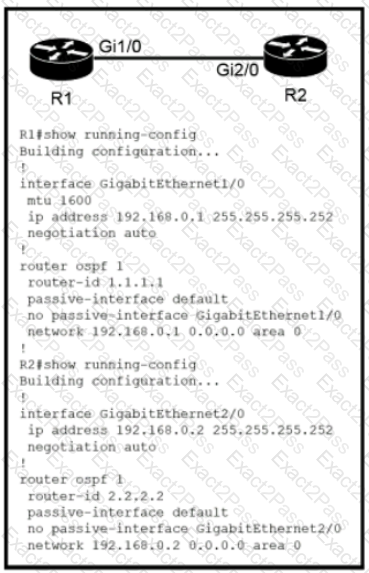
Which configuration issue is preventing the OSPF neighbor relationship from being established between the two routers?
Refer to the exhibit.
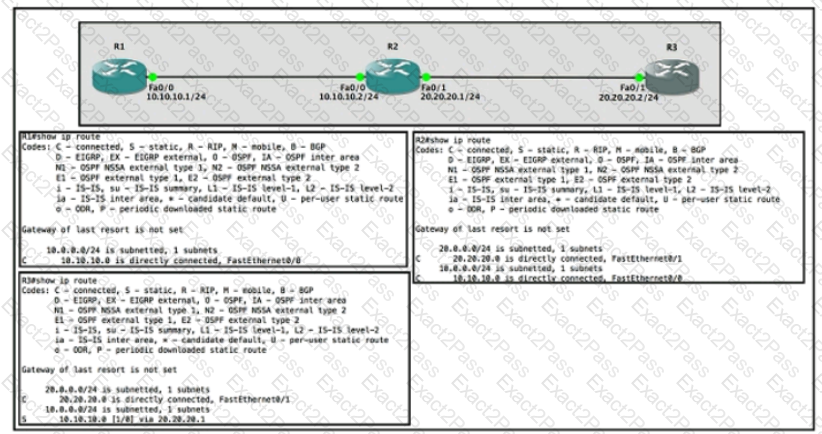
Router R1 Fa0/0 is unable ping router R3 Fa0/1.
Which action must be taken in router R1 to help resolve the configuration issue?
Refer to the exhibit.
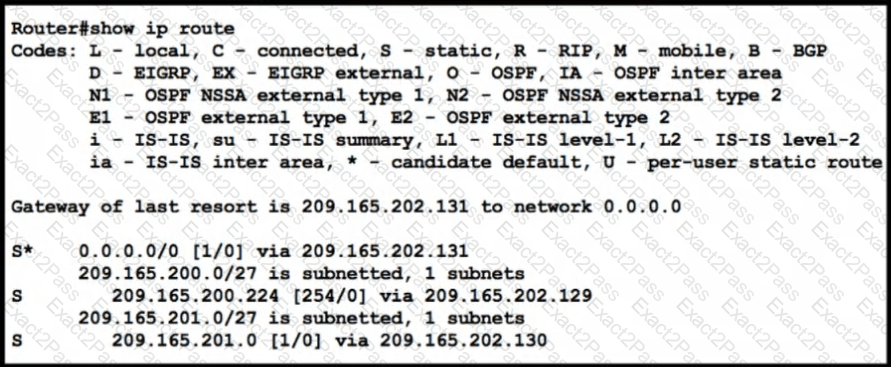
Which command configures a floating static route to provide a backup to the primary link?
Refer to the exhibit.
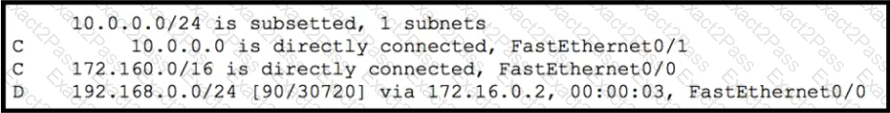
Which route type does the routing protocol Code D represent in the output?
Which two capacities of Cisco DNA Center make it more extensible as compared to traditional campus device management? (Choose two)
Refer to the exhibit.
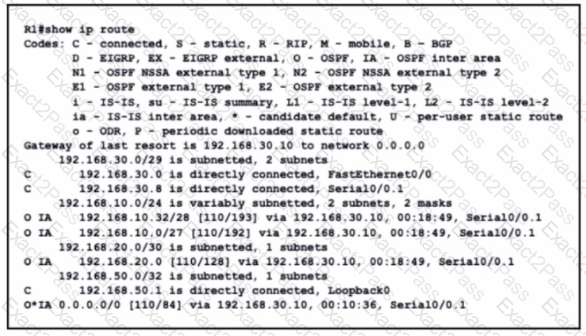
What is the metric of the route to the 192.168.10.33/28 subnet?
A network engineer is replacing the switches that belong to a managed-services client with new Cisco Catalyst switches. The new switches will be configured for updated security standards, including replacing Telnet services with encrypted connections and doubling the modulus size from 1024. Which two commands must the engineer configure on the new switches? (Choose two.)
What event has occurred if a router sends a notice level message to a syslog server?
A device detects two stations transmitting frames at the same time. This condition occurs after the first 64 bytes of the frame is received interface counter increments?
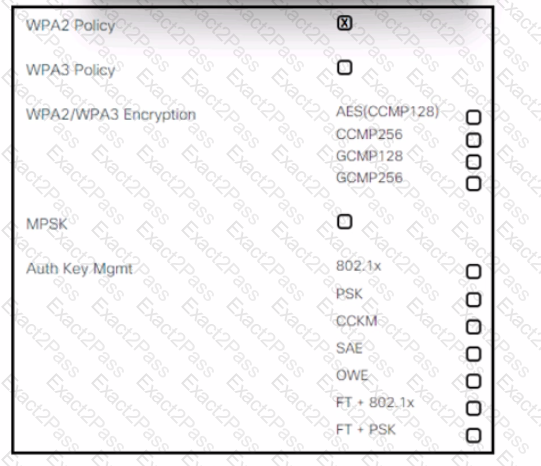
Refer to the exhibit. An engineer is creating a secure preshared key based SSID using WPA2 for a wireless network running on 2.4 GHz and 5 GHz. Which two tasks must the engineer perform to complete the process? (Choose two.)
Which alternative to password authentication Is Implemented to allow enterprise devices to log in to the corporate network?
Refer to the exhibit.
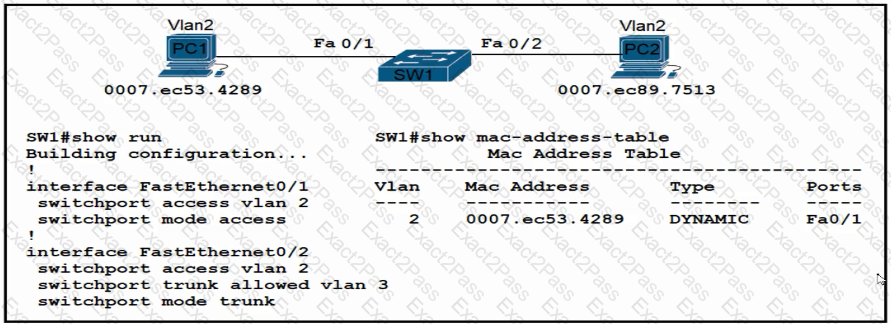
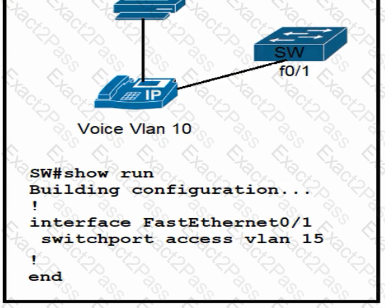
An engineer has started to configure replacement switch SW1. To verify part of the configuration, the engineer issued the commands as shown and noticed that the entry for PC2 is missing. Which change must be applied to SW1 so that PC1 and PC2 communicate normally?
A)
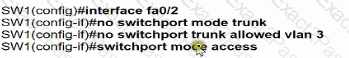
B)

C)
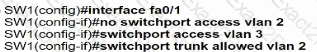
D)
What is a function of Opportunistic Wireless Encryption in an environment?
Drag and drop the characteristics of networking from the left onto the networking types on the right.
Refer to the exhibit.

Which configuration enables DHCP addressing for hosts connected to interface FastEthernetO/1 on router R4?
Refer to the exhibit.
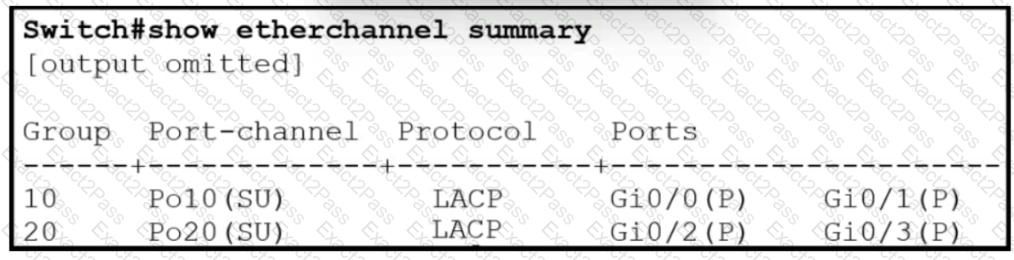
Which two commands when used together create port channel 10? (Choose two.)
Refer to the exhibit.

R1 learns all routes via OSPF Which command configures a backup static route on R1 to reach the 192 168.20.0/24 network via R3?
Refer to the exhibit.
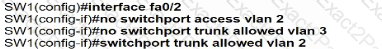
All VLANs are present in the VLAN database. Which command sequence must be applied to complete the configuration?
A network engineer must implement an IPv6 configuration on the vlan 2000 interface to create a routable locally-unique unicast address that is blocked from being advertised to the internet. Which configuration must the engineer apply?
Refer to the exhibit.
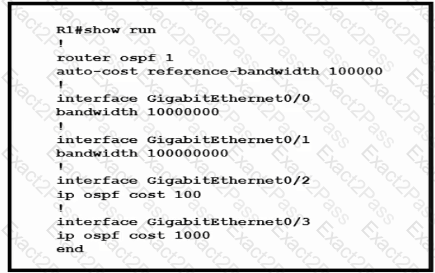
Router R1 resides in OSPF Area 0. After updating the R1 configuration to influence the paths that it will use to direct traffic, an engineer verified that each of the four Gigabit interfaces has the same route to 10.10.0.0/16. Which interface will R1 choose to send traffic to reach the route?
Refer to the exhibit.

How many objects are present in the given JSON-encoded data?
Refer to the exhibit.
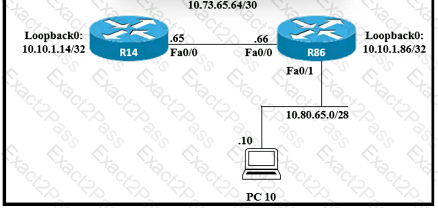
Router R14 is in the process of being configured. Which configuration must be used to establish a host route to PC 10?
Refer to the exhibit.
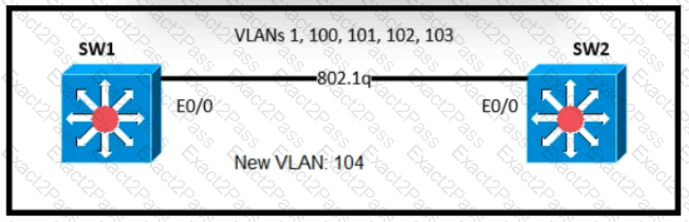
An engineer is asked to insert the new VLAN into the existing trunk without modifying anything previously configured Which command accomplishes this task?
Refer to the Exhibit.
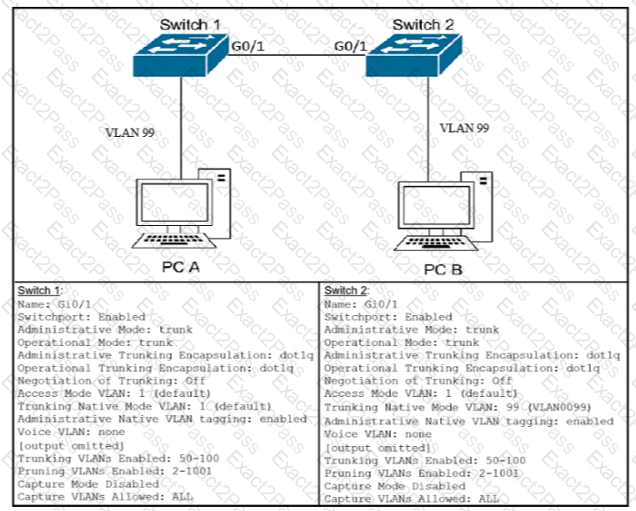
After the switch configuration the ping test fails between PC A and PC B Based on the output for switch 1. which error must be corrected?
A manager asks a network engineer to advise which cloud service models are used so employees do not have to waste their time installing, managing, and updating software which is only used occasionally Which cloud service model does the engineer recommend?
Which two WAN architecture options help a business scalability and reliability for the network? (Choose two)
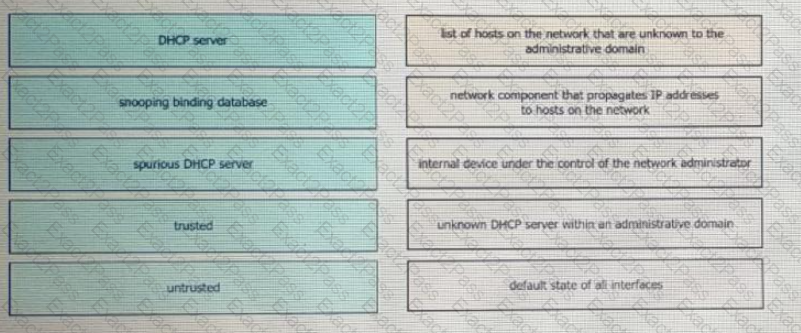
Drag and drop the DHCP snooping terms from the left onto the descriptions on the right.
Refer to the exhibit.
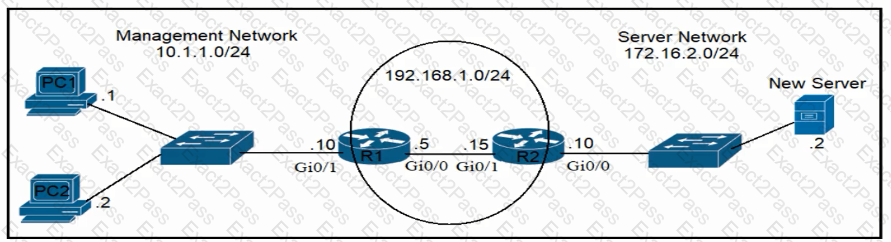
An engineer is updating the R1 configuration to connect a new server to the management network. The PCs on the management network must be blocked from pinging the default gateway of the new server. Which command must be configured on R1 to complete the task?
Refer to the exhibit.
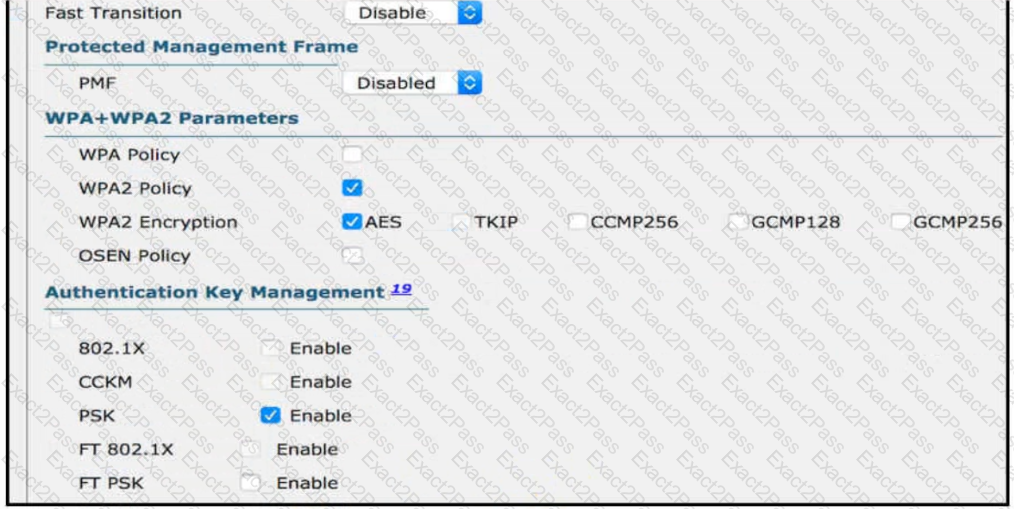
Users need to connect to the wireless network with IEEE 802. 11r-compatible devices. The connection must be maintained as users travel between floors or to other areas in the building What must be the configuration of the connection?
Refer to the exhibit.
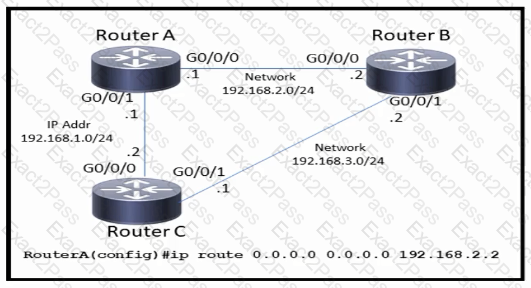
Which command must be issued to enable a floating static default route on router A?
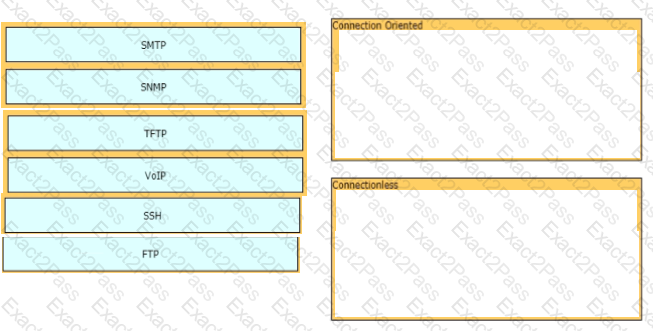
Drag and drop the TCP or UDP details from the left onto their corresponding protocols on the right.

Refer to the exhibit. A network engineer updates the existing configuration on interface fastethernet1/1 switch SW1. It must establish an EtherChannel by using the same group designation with another vendor switch. Which configuration must be performed to complete the process?
How does machine learning improve the detection of unauthorized network access?
Why is UDP more suitable than TCP tor applications that require low latency, such as VoIP?
Drag and drop the TCP and UDP characteristics from the left onto the supporting protocols on the right. Not all options are used.
All physical cabling is in place. A company plans to deploy 32 new sites.
The sites will utilize both IPv4 and IPv6 networks.
1 . Subnet 172.25.0.0/16 to meet the subnet requirements and maximize
the number of hosts
Using the second subnet
• Assign the first usable IP address to e0/0 on Sw1O1
• Assign the last usable IP address to e0/0 on Sw102
2. Subnet to meet the subnet requirements and maximize
the number of hosts
c Using the second subnet
• Assign an IPv6 GUA using a unique 64-Bit interface identifier
on e0/0 on Sw101
• Assign an IPv6 GUA using a unique 64-Bit interface identifier
on eO/O on swi02
Guidelines
This is a lab item in which tasks will be performed on virtual devices.
• Refer to the Tasks tab to view the tasks for this lab item.
• Refer to the Topology tab to access the device console(s) and perform the tasks.
• Console access is available for all required devices by clicking the device icon or using
the tab(s) above the console window.
• All necessary preconfigurations have been applied.
• Do not change the enable password or hostname for any device.
• Save your configurations to NVRAM before moving to the next item.
• Click Next at the bottom of the screen to submit this lab and move to the next question.
• When Next is clicked, the lab closes and cannot be reopened.

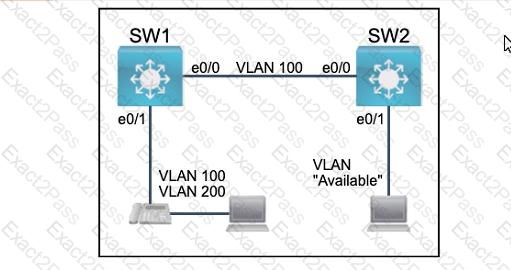
All physical cabling between the two switches is installed. Configure the network connectivity between the switches using the designated VLANs and interfaces.
1. Configure VLAN 100 named Compute and VLAN 200 named Telephony where required for each task.
2. Configure Ethernet0/1 on SW2 to use the existing VLAN named Available.
3. Configure the connection between the switches using access ports.
4. Configure Ethernet0/1 on SW1 using data and voice VLANs.
5. Configure Ethemet0/1 on SW2 so that the Cisco proprietary neighbor discovery protocol is turned off for the designated interface only.
Refer to the exhibit. The user has connectivity to devices on network 192.168.3 0/24 but cannot reach users on the network 10.10.1.0724.
What is the first step to verify connectivity?

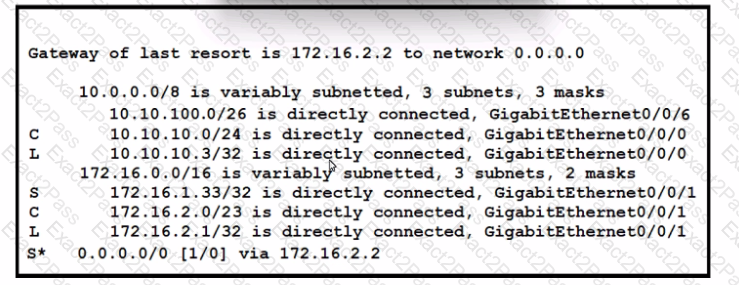
Refer to the exhibit. A packet sourced from 10.10.10.32 is destined for the Internet. What is the administrative distance for the destination route?
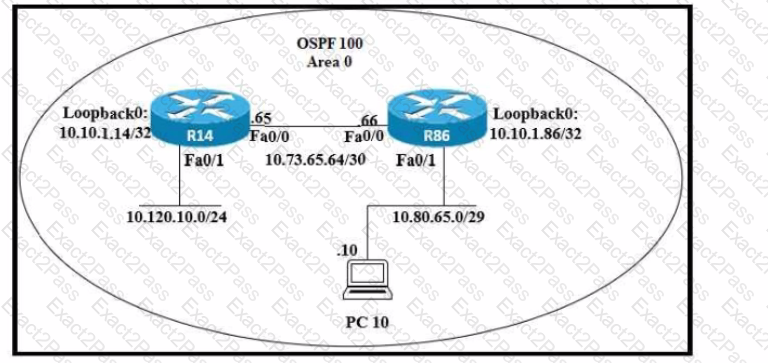
Refer to the exhibit. An engineer just installed network 10.120.10.0/24. Which configuration must be applied to the R14 router to add the new network to its OSPF routing table?
A network engineer is configuring a new router at a branch office. The router is connected to an upstream WAN network that allows the branch to communicate with the head office. The central time server with IP address 172.24.54.8 is located behind a firewall at the head office. Which command must the engineer configure so that the software clock of the new router synchronizes with the time server?
Which type of security program is violated when a group of employees enters a building using the ID badge of only one person?
All physical cabling is in place. Router R4 and PCI are fully configured and
inaccessible. R4's WAN interfaces use .4 in the last octet for each subnet.
Configurations should ensure that connectivity is established end-to-end.
1 . Configure static routing to ensure RI prefers the path through R2 to
reach only PCI on R4's LAN
2. Configure static routing that ensures traffic sourced from RI will take
an alternate path through R3 to PCI in the event of an outage along
the primary path
3. Configure default routes on RI and R3 to the Internet using the least number of hops
Guidelines
This is a lab item in which tasks will be performed on virtual devices.
• Refer to the Tasks tab to view the tasks for this lab item.
• Refer to the Topology tab to access the device console(s) and perform the tasks.
• Console access is available for all required devices by clicking the device icon or using
the tab(s) above the console window.
• All necessary preconfigurations have been applied.
• Do not change the enable password or hostname for any device.
• Save your configurations to NVRAM before moving to the next item.
• Click Next at the bottom of the screen to submit this lab and move to the next question.
• When Next is clicked, the lab closes and cannot be reopened.
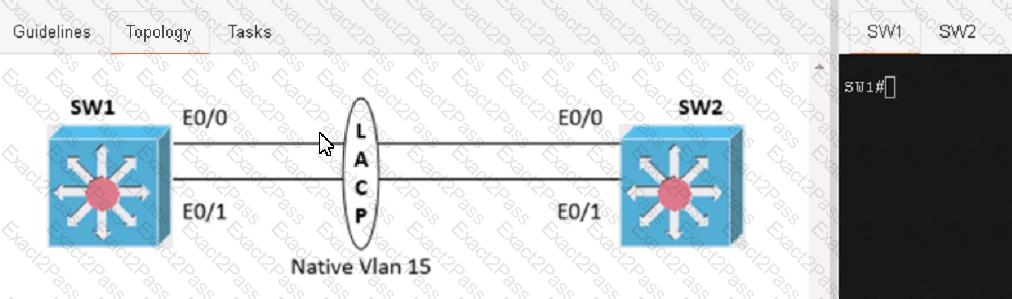
Physical connectivity is implemented between the two Layer 2 switches, and the network connectivity between them must be configured
1. Configure an LACP EtherChannel and number it as 1; configure it between switches SW1 and SVV2 using interfaces Ethernet0/0 and Ethernet0/1 on both sides. The LACP mode must match on both ends
2 Configure the EtherChannel as a trunk link.
3. Configure the trunk link with 802.1 q tags.
4. Configure the native VLAN of the EtherChannel as VLAN 15.

Configure IPv4 and IPv6 connectivity between two routers. For IPv4, use a /28 network from the 192.168.1.0/24 private range. For IPv6, use the first /64 subnet from the 2001:0db8:aaaa::/48 subnet.
1. Using Ethernet0/1 on routers R1 and R2, configure the next usable/28 from the 192.168.1.0/24 range. The network 192.168.1.0/28 is unavailable.
2. For the IPv4 /28 subnet, router R1 must be configured with the first usable host address.
3. For the IPv4 /28 subnet, router R2 must be configured with the last usable host address.
4. For the IPv6 /64 subnet, configure the routers with the IP addressing provided from the topology.
5. A ping must work between the routers on the IPv4 and IPv6 address ranges.

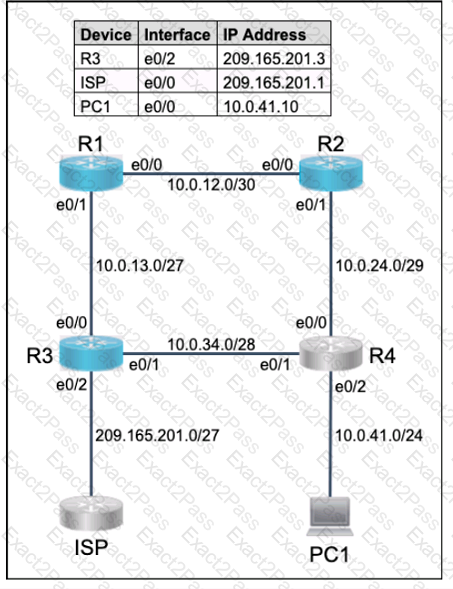
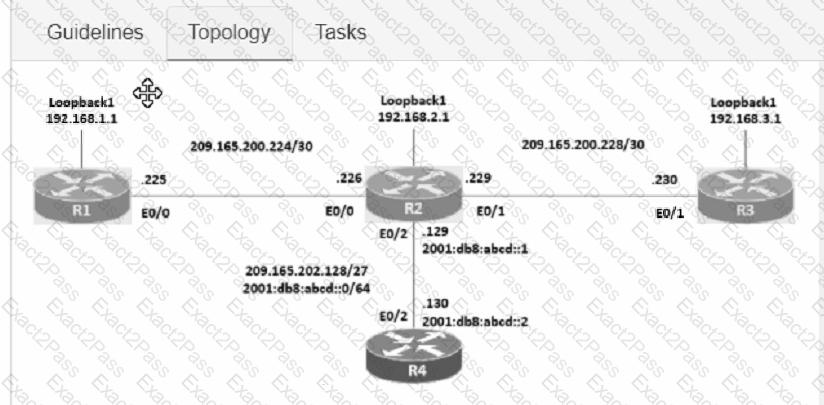
Connectivity between four routers has been established. IP connectivity must be configured in the order presented to complete the implementation. No dynamic routing protocols are included.
1. Configure static routing using host routes to establish connectivity from router R3 to the router R1 Loopback address using the source IP of 209.165.200.230.
2. Configure an IPv4 default route on router R2 destined for router R4.
3. Configure an IPv6 default router on router R2 destined for router R4.
Which two statements distinguish authentication from accounting? (Choose two.)
Which interface or port on the WLC is the default for in-band device administration and communications between the controller and access points?
Refer to the exhibit.
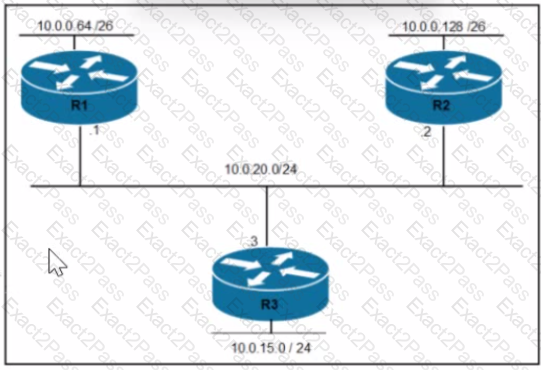
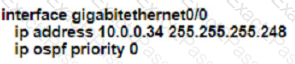
Rooter R1 is added to the network and configured with tie 10 0 0 64/26 and 10.0.20.0/24 subnets However traffic destined for the LAN on R3 is not access. Which command when executed on R1 defines a tunic route to reach the R3 LAN?
A)
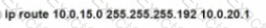
B)
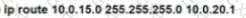
C)

Which two practices are recommended for an acceptable security posture in a network? (Choose two)
A router has two static routes to the same destination network under the same OSPF process. How does the router forward packets to the destination if the next-hop devices are different?
What is the operating mode and role of a backup port on a shared LAN segment in Rapid PVST+?
A network administrator wants the syslog server to filter incoming messages into different files based on their Importance. Which filtering criteria must be used?
Drag and drop the common functions from the left onto the cofresponding network topology architecture layer on the right. Not all common functions are used.

What is the difference between controller-based networks and traditional networks as they relate to control-plane and/or data-plane functions?
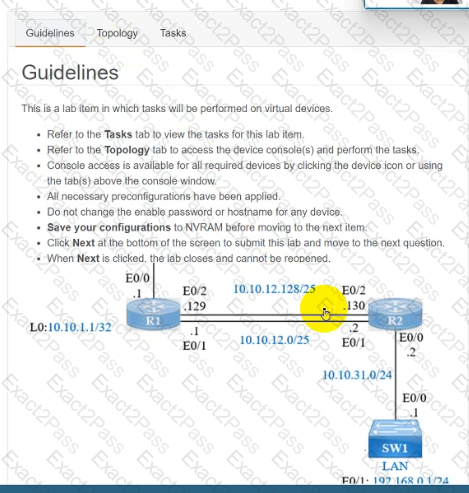
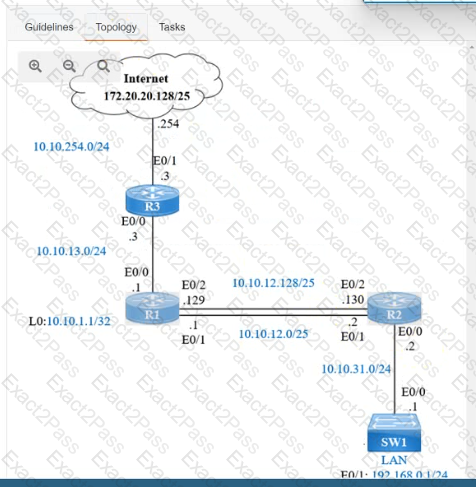
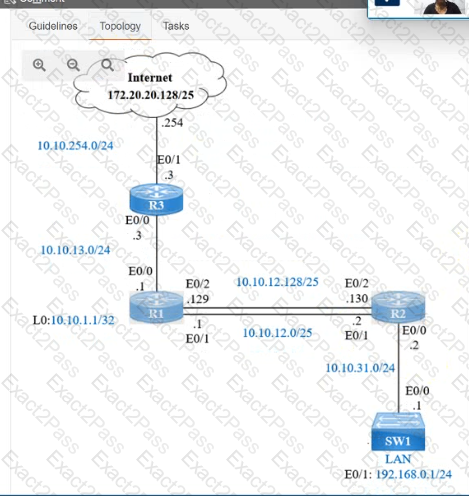
IP connectivity and OSPF are preconfigured on all devices where necessary. Do not make any changes to the IP addressing or OSPF. The company policy uses connected interfaces and next hops when configuring static routes except for load balancing or redundancy without floating static. Connectivity must be established between subnet 172.20.20.128/25 on the Internet and the LAN at 192.168.0.0/24 connected to SW1:
1. Configure reachability to the switch SW1 LAN subnet in router R2.
2. Configure default reachability to the Internet subnet in router R1.
3. Configure a single static route in router R2 to reach to the Internet subnet considering both redundant links between routers R1 and R2. A default route is NOT allowed in router R2.
4. Configure a static route in router R1 toward the switch SW1 LAN subnet where the primary link must be through Ethernet0/1. and the backup link must be through Ethernet0/2 using a floating route. Use the minimal administrative distance value when required.
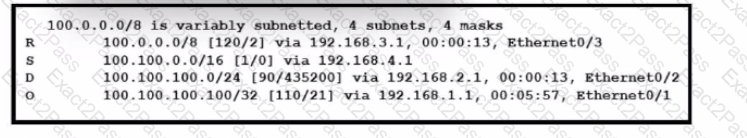
Refer to the exhibit. How will the device handle a packet destined to IP address 100.100.100.100?
Which authentication method requires the user to provide a physical attribute to authenticate successfully?
An engineer must configure a core router with a floating static default route to the backup router at 10.200.0.2. Which command meets the requirements?
What are two facts that differentiate optical-fiber cabling from copper cabling? (Choose two.)
Which AP feature provides a captive portal for users to authenticate register and accept terms before accessing the internet?
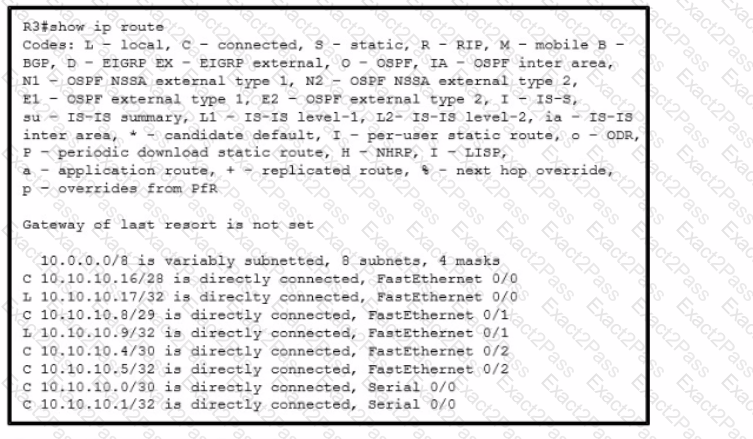
Refer to the exhibit. Which interface does a packet take to reach the destination address of 10.10.10.147?
A HCP pool has been created with the name CONTROL. The pool uses the next to last usable IP address as the default gateway for the DHCP clients. The server is located at 172.16 32.15. What is the step in the process for clients on the 192.168.52.0/24 subnet to reach the DHCP server?
Which solution is appropriate when mitigating password attacks where the attacker was able to sniff the clear-text password of the system administrator?
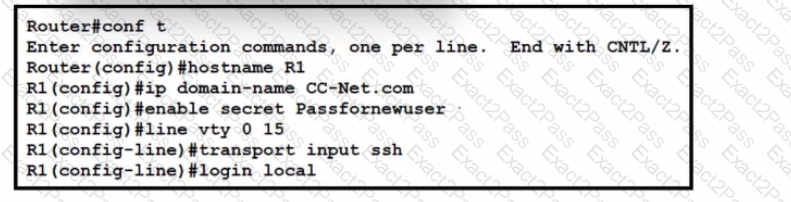
Refer to the exhibit. A network administrator is configuring a router for user access via SSH. The service-password encryption command has been issued. The configuration must meet these requirements:
• Create the username as CCUser.
• Create the password as NA!2Scc.
• Encrypt the user password.
What must be configured to meet the requirements?
Which WLC management connection type is vulnerable to man-in-the-middIe attacks?
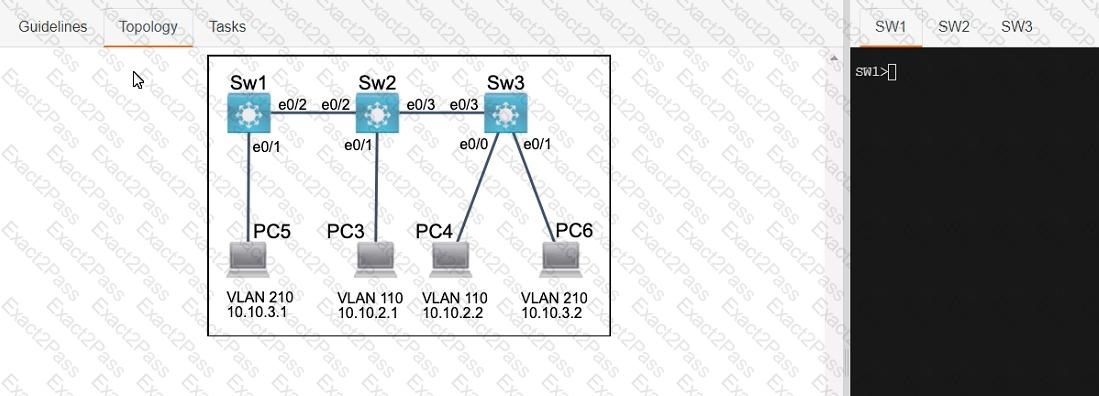
Three switches must be configured for Layer 2 connectivity. The company requires only the designated VLANs to be configured on their respective switches and permitted accross any links between switches for security purposes. Do not modify or delete VTP configurations.
The network needs two user-defined VLANs configured:
VLAN 110: MARKETING
VLAN 210: FINANCE
1. Configure the VLANs on the designated switches and assign them as access ports to the interfaces connected to the PCs.
2. Configure the e0/2 interfaces on Sw1 and Sw2 as 802.1q trunks with only the required VLANs permitted.
3. Configure the e0/3 interfaces on Sw2 and Sw3 as 802.1q trunks with only the required VLANs permitted.
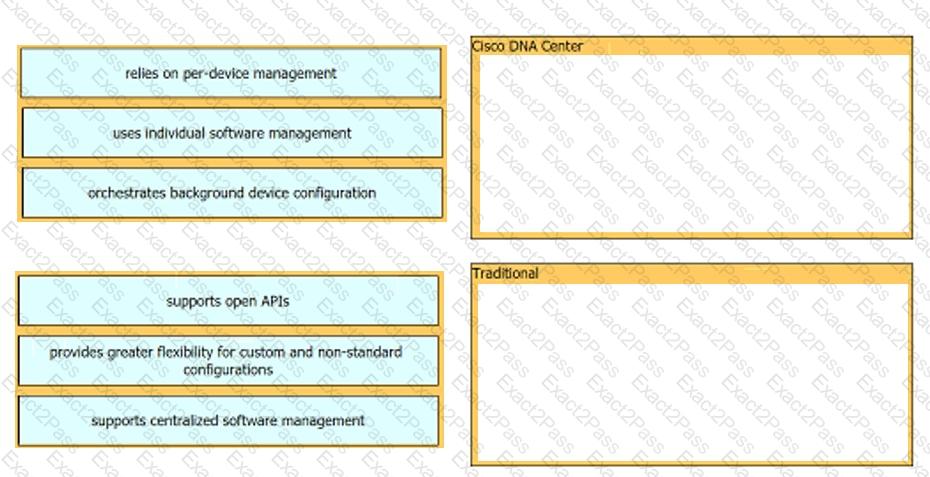
Drag and drop each characteristic of device-management technologies from the left onto the deployment type on the right.
Refer to the exhibit.
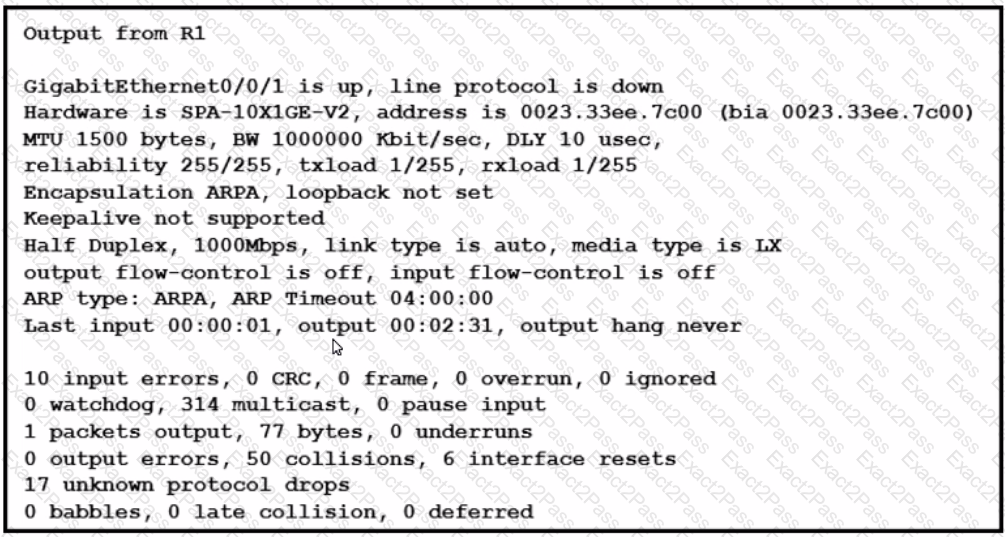
What is the issue with the interface GigabitEthernet0/0/1?
Refer to the exhibit.
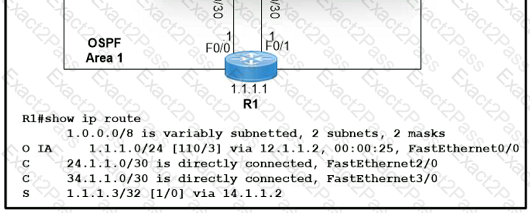
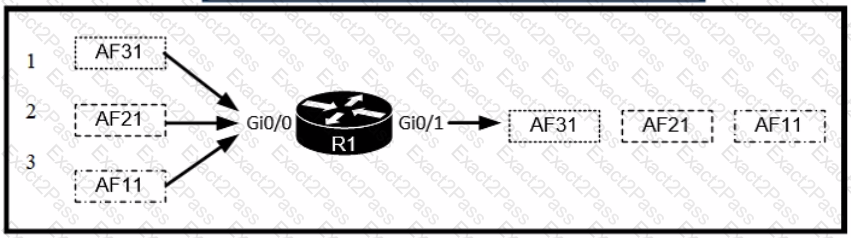
Which two values does router R1 use to determine the best path to reach destinations in network 1,0.0.0/8? (Choose two.)
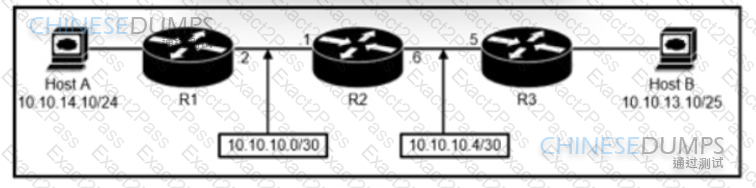
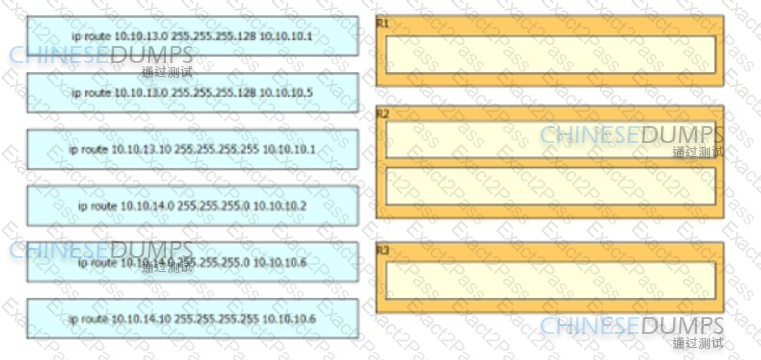
Refer to the exhibit. An engineer must configure a static network route between two networks so that host A communicates with host B. Drag and drop the commands from the left onto the routers where they must be configured on the right. Not all commands are used.
Refer to the exhibit.

In which structure does the word "warning" directly reside?
Which cipher is supported for wireless encryption only with the WPA2 standard?
Which QoS queuing method discards or marks packets that exceed the desired bit rate of traffic flow?
Refer to the exhibit.
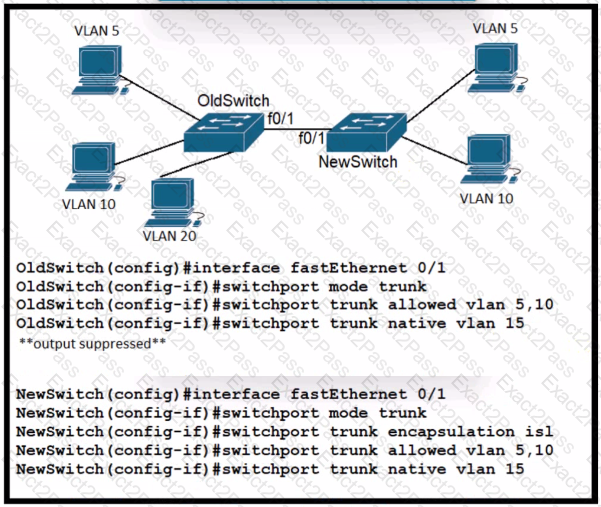
A new VLAN and switch are added to the network. A remote engineer configures OldSwitch and must ensure that the configuration meets these requirements:
• accommodates current configured VLANs
• expands the range to include VLAN 20
• allows for IEEE standard support for virtual LANs
Which configuration on the NewSwitch side of the link meets these requirements?
A)

B)

C)
D)

Refer to the exhibit.
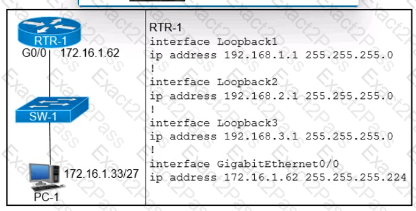
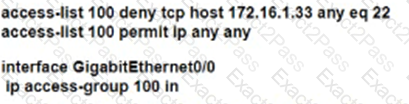
Which configuration for RTR-1 deniess SSH access from PC-1 to any RTR-1 interface and allows all other traffic?
A)
B)
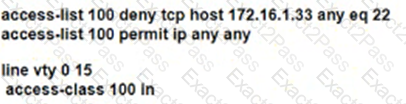
C)
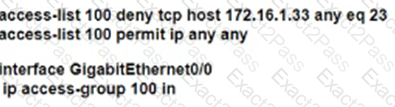
D)

Which advantage does the network assurance capability of Cisco DNA Center provide over traditional campus management?
What are two benefits of controller-based networking compared to traditional networking?
Refer to the exhibit.
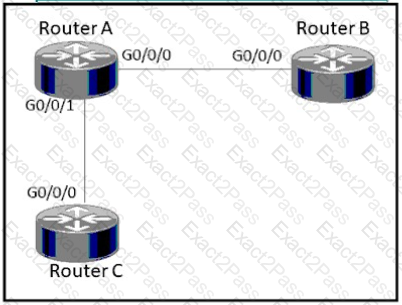
How must router A be configured so that it only sends Cisco Discovery Protocol Information to router C?
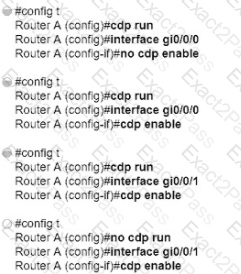
What is the difference in data transmission delivery and reliability between TCP and UDP?
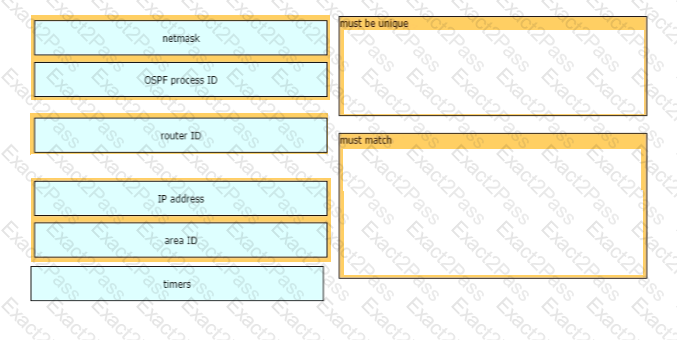
A network engineer is configuring an OSPFv2 neighbor adjacency Drag and drop the parameters from the left onto their required categories on the right. Not all parameters are used
Which resource is able to be shared among virtual machines deployed on the same physical server?
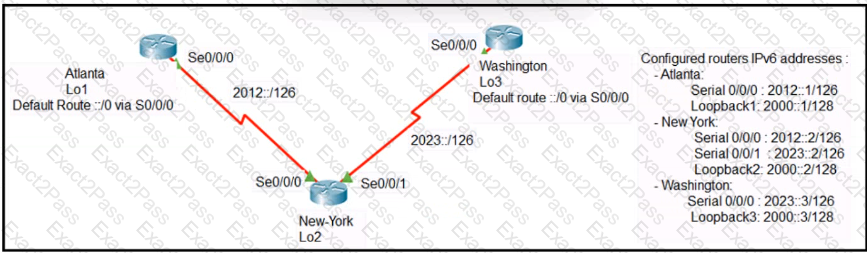
Refer to Exhibit.
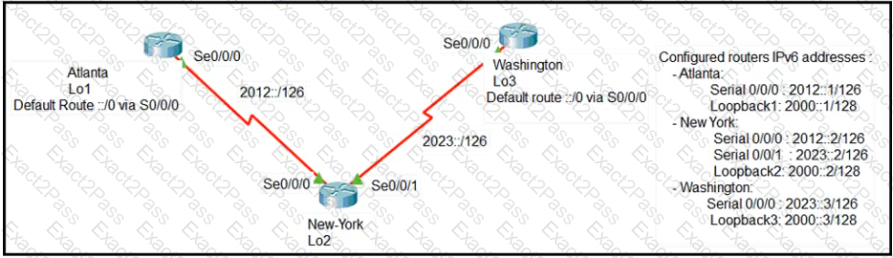
The loopback1 interface of the Atlanta router must reach the loopback3 interface of the Washington router. Which two static host routes must be configured on the NEW York router? (Choose two)
Which type of wireless encryption is used for WPA2 in preshared key mode?
A frame that enters a switch fails the Frame Check Sequence. Which two interface counters are incremented? (Choose two)
Aside from discarding, which two states does the switch port transition through while using RSTP (802.1w)? (Choose two)
Which syslog severity level is considered the most severe and results in the system being considered unusable?
What differentiates the Cisco OfficeExtend AP mode from FlexConnect AP mode?
Refer to the exhibit.
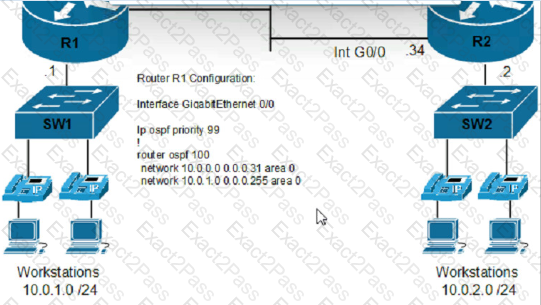
An engineer must configure router R2 so it is elected as the DR on the WAN subnet. Which command sequence must be configured?
A)
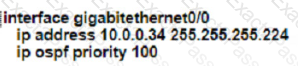
B)
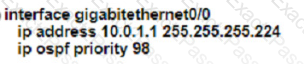
C)
D)

Drag and chop the TCP/IP protocols from the left onto their primary transmission protocols on the right.

Refer to the exhibit.
The loopback1 interface of the Atlanta router must reach the lookback3 interface of the Washington router.
A network architect is deciding whether to implement Cisco autonomous access points or lightweight access points. Which fact about firmware updates must the architect consider? Unlike lightweight access points, which require
Which (unction generally performed by a traditional network device is replaced by a software-defined controller?
What must be considered for a locally switched FlexConnect AP if the VLANs that are used by the AP and client access are different?
When the LAG configuration is updated on a Cisco WLC which additional task must be performed when changes are complete?
Which interface IP address serves as the tunnel source for CAPWAP packets from the WLC to an AP?
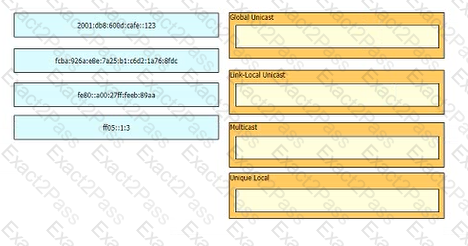
Drag and drop the IPv6 addresses from the left onto the corresponding address types on the right.
What are two reasons lo configure PortFast on a switch port attached to an end host? (Choose two.)
Refer to the exhibit.
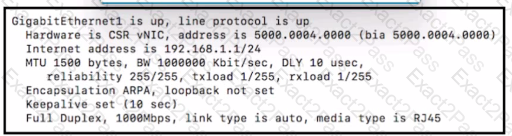
Which format matches the Modified EUI-64 IPv6 interface address for the network 2001:db8::/64?
Which two protocols are used by an administrator for authentication and configuration on access points?
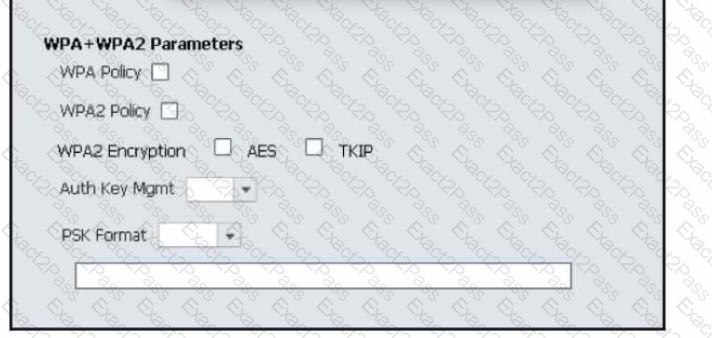
Refer to the exhibit. An engineer is using the Cisco WLC GUI to configure a WLAN for WPA2 encryption with AES and preshared key Cisc0123456. After the engineer selects the WPA + WPA2 option from the Layer 2 Security drop-down list, which two tasks must they perform to complete the process? (Choose two.)
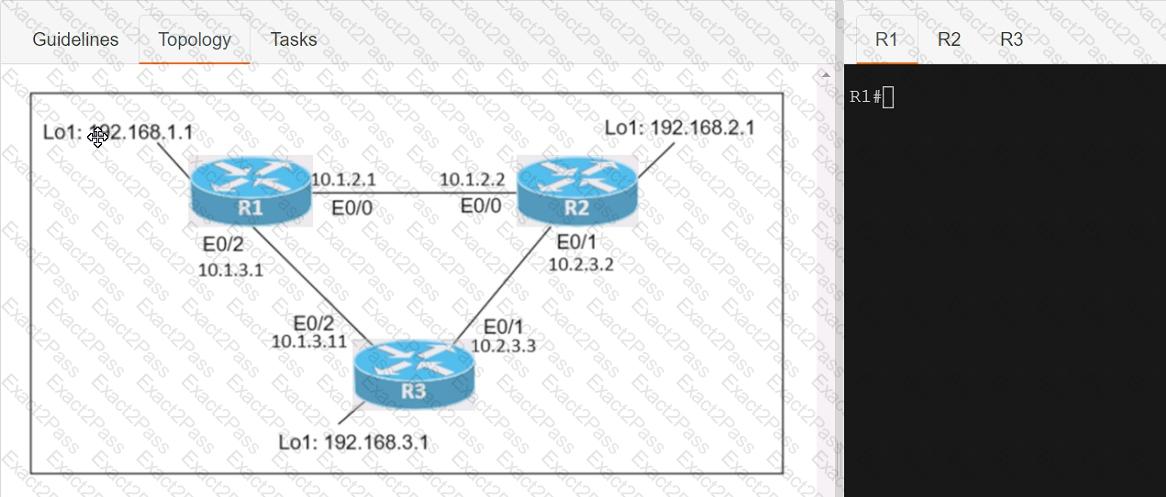
Connectivity between three routers has been established, and IP services must be configured jn the order presented to complete the implementation Tasks assigned include configuration of NAT, NTP, DHCP, and SSH services.
1. All traffic sent from R3 to the R1 Loopback address must be configured for NAT on R2. All source addresses must be translated from R3 to the IP address of Ethernet0/0 on R2, while using only a standard access list named NAT To verify, a ping must be successful to the R1 Loopback address sourced from R3. Do not use NVI NAT configuration.
2. Configure R1 as an NTP server and R2 as a client, not as a peer, using the IP address of the R1 Ethernet0/2 interface. Set the clock on the NTP server for midnight on January 1, 2019.
3. Configure R1 as a DHCP server for the network 10.1.3.0/24 in a pool named TEST. Using a single command, exclude addresses 1-10 from the range. Interface Ethernet0/2 on R3 must be issued the IP address of 10.1.3.11 via DHCP.
4. Configure SSH connectivity from R1 to R3, while excluding access via other remote connection protocols. Access for user root and password Cisco must be set on router R3 using RSA and 1024 bits. Verify connectivity using an SSH session from router R1 using a destination address of 10.1.3.11. Do NOT modify console access or line numbers to accomplish this task.
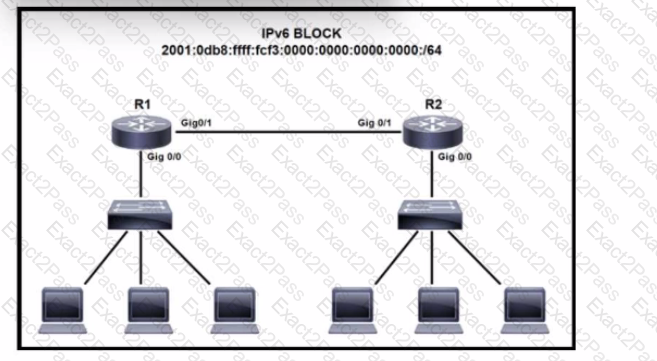
Refer to the exhibit. IPv6 is being Implemented within the enterprise. The command Ipv6 unlcast-routing is configure. Interlace GlgO/0 on R1 must be configured to provide a dynamic assignment using the assigned IPv6 block Which command accomplishes this task?
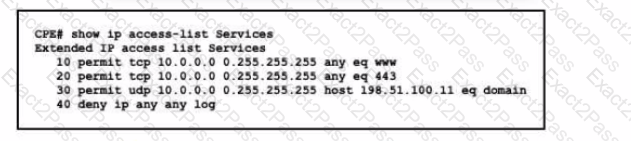
Refer to the exhibit. This ACL is configured to allow client access only to HTTP, HTTPS, and DNS services via UDP. The new administrator wants to add TCP access to the DNS service. Which configuration updates the ACL efficiently?
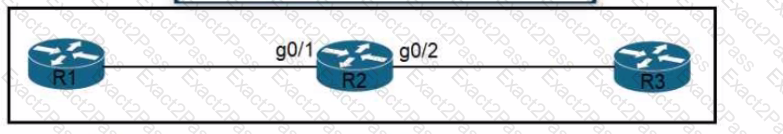
Refer to the exhibit Routers R1 R2 and R3 use a protocol to identify their neighbors' IP addresses hardware platforms, and software versions. A network engineer must configure R2 to avoid sharing any neighbor information with R3, and maintain its relationship with R1. What action meets this requirement?
Physical connectivity is implemented between the two Layer 2 switches,
and the network connectivity between them must be configured.
I . Configure an LACP EtherChanneI and number it as 44; configure it
between switches SWI and SW2 using interfaces EthernetO/O and
Ethernet0/1 on both sides. The LACP mode must match on both ends.
2. Configure the EtherChanneI as a trunk link.
3. Configure the trunk link with 802. Iq tags.
4. Configure VLAN 'MONITORING' as the untagged VLAN of the
EtherChannel.
==================
Guidelines
This is a lab item in which tasks will be performed on virtual devices.
• Refer to the Tasks tab to view the tasks for this lab item.
• Refer to the Topology tab to access the device console(s) and perform the tasks.
• Console access is available for all required devices by clicking the device icon or using
the tab(s) above the console window.
• All necessary preconfigurations have been applied.
• Do not change the enable password or hostname for any device.
• Save your configurations to NVRAM before moving to the next item.
• Click Next at the bottom of the screen to submit this lab and move to the next question.
• When Next is clicked, the lab closes and cannot be reopened.
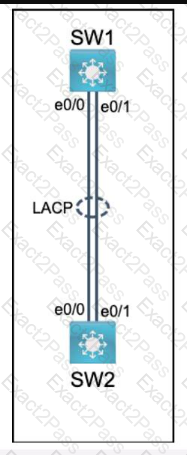
Which two events occur automatically when a device is added to Cisco DNA Center? (Choose two. )
Which action does the router take as it forwards a packet through the network?
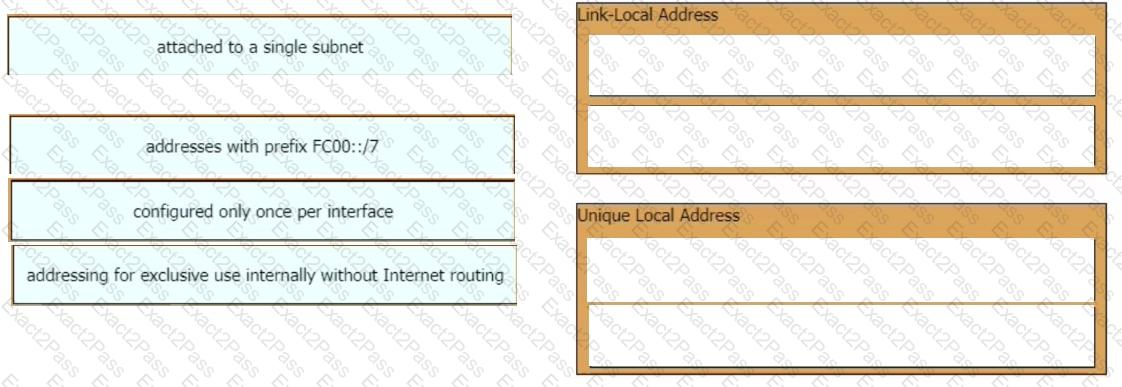
Drag and drop the IPv6 address type characteristics from the left to the right.
What are two roles of the Dynamic Host Configuration Protocol (DHCP)? (Choose two)
Drag and drop the network protocols from the left onto the correct transport services on the right.
Refer to the exhibit.
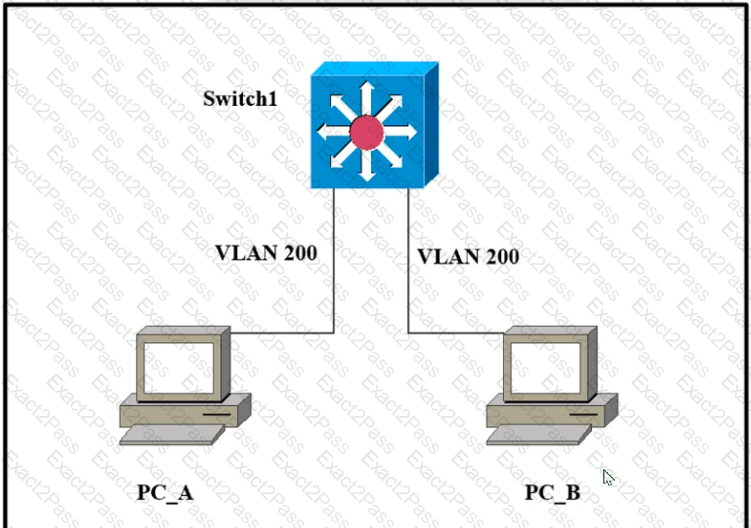
Which outcome is expected when PC_A sends data to PC_B?
Which security program element involves installing badge readers on data-center doors to allow workers to enter and exit based on their job roles?
Which technology allows for multiple operating systems to be run on a single host computer?
Several new coverage cells are required to improve the Wi-Fi network of an organization. Which two standard designs are recommended? (choose two.)
An organization has decided to start using cloud-provided services. Which cloud service allows the organization to install its own operating system on a virtual machine?
Which WAN access technology is preferred for a small office / home office architecture?
When a site-to-site VPN is configured, which IPsec mode provides encapsulation and encryption of the entire original P packet?
Refer to the exhibit.
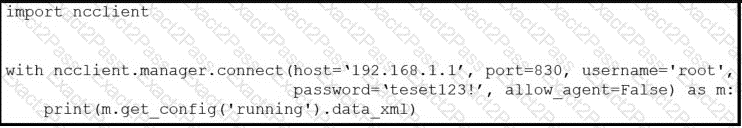
After running the code in the exhibit, which step reduces the amount of data that the NETCONF server returns to the NETCONF client, to only the interface's configuration?
How does a switch process a frame received on Fa0/1 with the destination MAC address of 0e38.7363.657b when the table is missing the address?
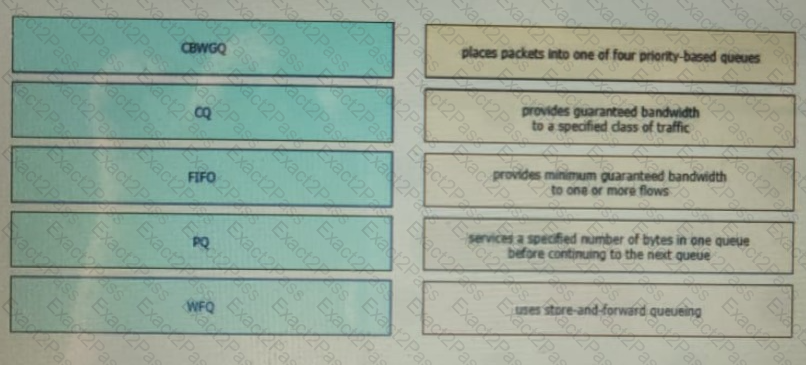
Drag and drop the QoS congestion management terms from the left onto the description on the right.
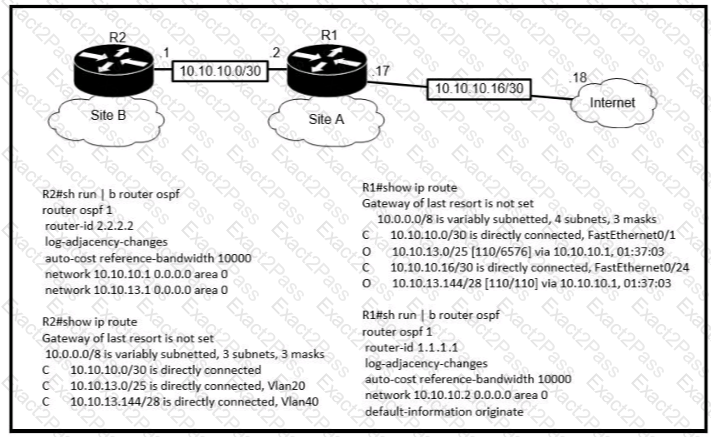
Refer to the exhibit.

If OSPF is running on this network, how does Router 2 handle traffic from Site B to 10.10.13/25 at Site A?
Refer to the exhibit.
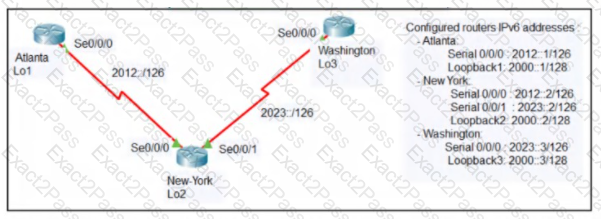
An engineer configured the New York router with state routes that point to the Atlanta and Washington sites. When command must be configured on the Atlanta and Washington routers so that both sites are able to reach the loopback2 interface on the New York router?
An engineer must configure traffic for a VLAN that is untagged by the switch as it crosses a trunk link. Which command should be used?
How does CAPWAP communicate between an access point in local mode and a WLC?
Which two must be met before SSH can operate normally on a Cisco IOS switch? (Choose two)
Which unified access point mode continues to serve wireless clients after losing connectivity to the Cisco Wireless LAN Controller?
When a client and server are not on the same physical network, which device is used to forward requests and replies between client and server for DHCP?
Which statement correctly compares traditional networks and controller-based networks?
Which two values or settings must be entered when configuring a new WLAN in the Cisco Wireless LAN Controller GUI? (Choose two)
Which 802.11 frame type is indicated by a probe response after a client sends a probe request?
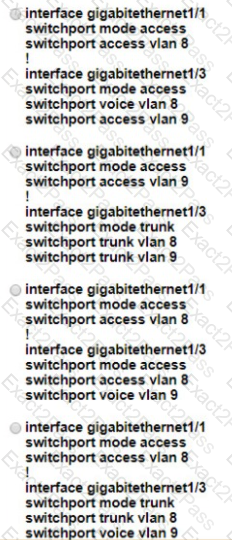
Refer to the exhibit.
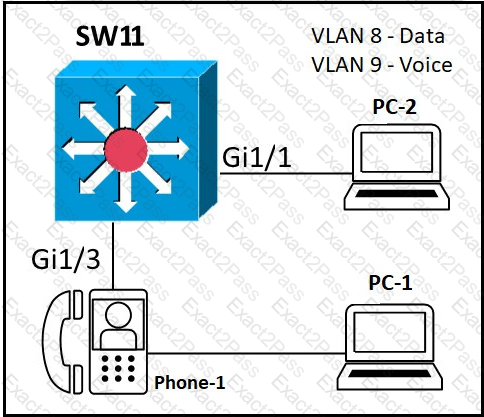
An administrator must configure interfaces Gi1/1 and Gi1/3 on switch SW11 PC-1 and PC-2 must be placed in the Data VLAN and Phone-1 must be placed in the Voice VLAN Which configuration meets these requirements?
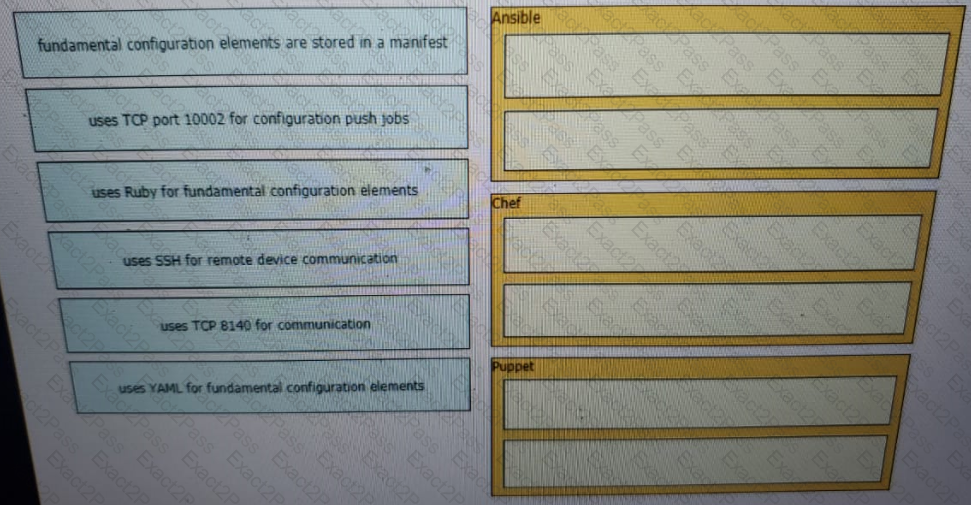
Drag and drop the descriptions from the left onto the configuration-management technologies on the right.
What is the same for both copper and fiber interfaces when using SFP modules?
Which action is taken by a switch port enabled for PoE power classification override?
Which port type supports the spanning-tree portfast command without additional configuration?
Which protocol prompts the Wireless LAN Controller to generate its own local web administration SSL certificate for GUI access?
Refer to the exhibit.
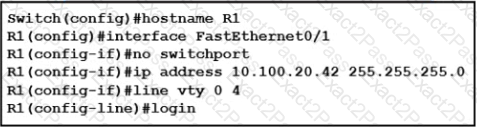
An engineer booted a new switch and applied this configuration via the console port. Which additional configuration must be applied to allow administrators to authenticate directly to enable privilege mode via Telnet using a local username and password?
Which QoS tool is used to optimize voice traffic on a network that is primarily intended for data traffic?
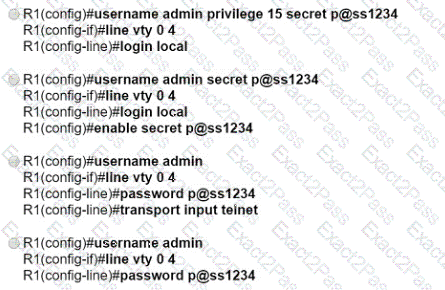
Refer to the exhibit.
With which metric was the route to host 172.16.0.202 learned?
A corporate office uses four floors in a building
• Floor 1 has 24 users
• Floor 2 has 29 users
• Floor 3 has 28 users
•Floor 4 has 22 users
Which subnet summarizes and gives the most efficient distribution of IP addresses for the router configuration?
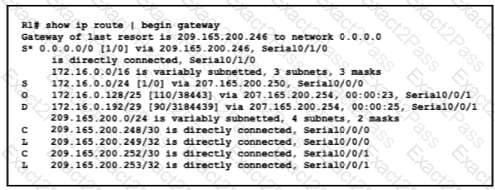
Refer to the exhibit.
An engineer is bringing up a new circuit to the MPLS provider on the Gi0/1 interface of Router1 The new circuit uses eBGP and teams the route to VLAN25 from the BGP path What s the expected behavior for the traffic flow for route 10.10.13.0/25?
Refer to the exhibit.

Which two commands were used to create port channel 10? (Choose two )

Refer to the exhibit.
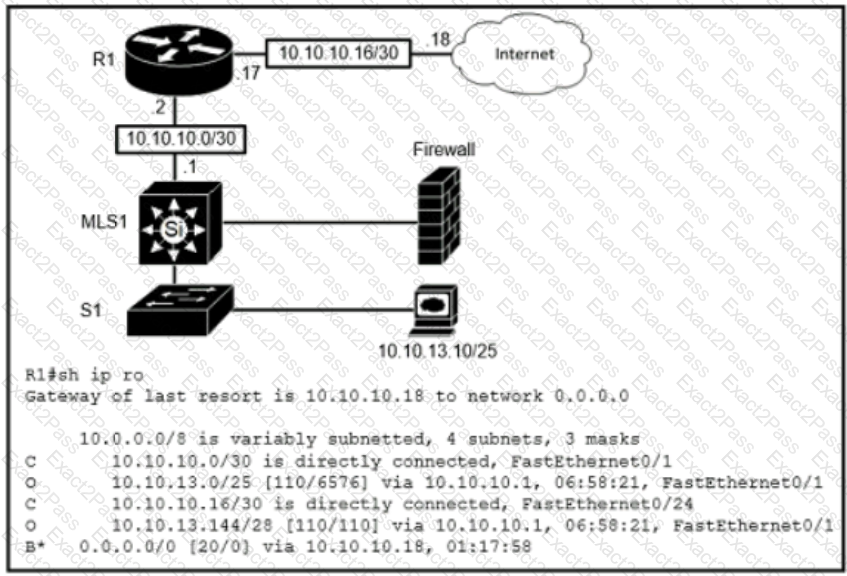
Which route type is configured to reach the internet?
Router A learns the same route from two different neighbors, one of the neighbor routers is an OSPF neighbor and the other is an EIGRP neighbor. What is the administrative distance of the route that will be installed in the routing table?
Which action does the router take as rt forwards a packet through the network?
Refer to the exhibit.
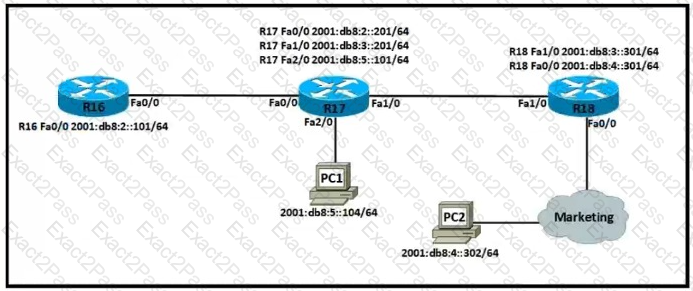
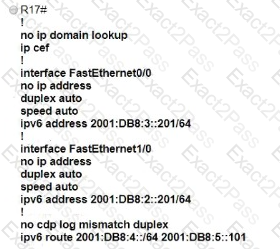
Which IPv6 configuration is required for R17 to successfully ping the WAN interface on R18?
A)
B)
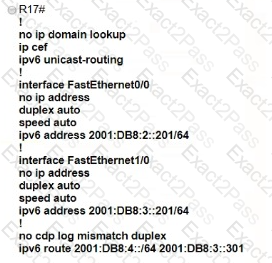
C)

D)
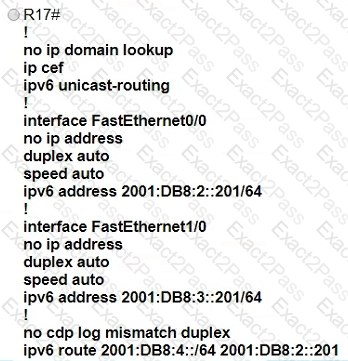
Which mode must be set for APs to communicate to a Wireless LAN Controller using the Control and Provisioning of Wireless Access Points (CAPWAP) protocol?
Refer to the exhibit.

An administrator is tasked with configuring a voice VLAN. What is the expected outcome when a Cisco phone is connected to the GigabitEfriemet3/1/4 port on a switch?
Which configuration management mechanism uses TCP port 22 by default when communicating with managed nodes?
While examining excessive traffic on the network, it is noted that all incoming packets on an interface appear to be allowed even though an IPv4 ACL is applied to the interface.
Which two misconfigurations cause this behavior? (Choose two)
Which condition must be met before an NMS handles an SNMP trap from an agent?
Refer to the exhibit.
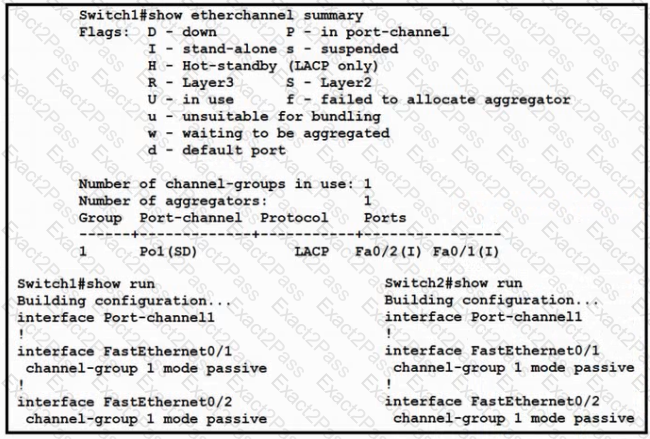
Which change to the configuration on Switch?
allows the two switches to establish an GtherChannel?
An administrator must secure the WLC from receiving spoofed association requests. Which steps must be taken to configure the WLC to restrict the requests and force the user to wait 10 ms to retry an association request?
A user configured OSPF and advertised the Gigabit Ethernet interface in OSPF By default, which type of OSPF network does this interface belong to?
The service password-encryption command is entered on a router. What is the effect of this configuration?
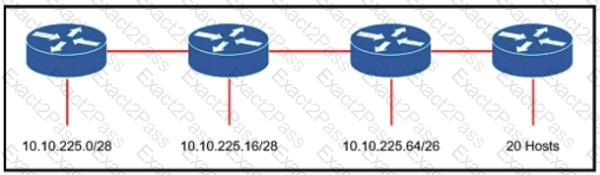
Refer to the exhibit. An engineer must add a subnet for a new office that will add 20 users to the network. Which IPv4 network and subnet mask combination does the engineer assign to minimize wasting addresses?
Which technology must be implemented to configure network device monitoring with the highest security?
What is the effect when loopback interfaces and the configured router ID are absent during the OSPF Process configuration?
An engineer requires a scratch interface to actively attempt to establish a trunk link with a neighbor switch. What command must be configured?
Refer to the exhibit.
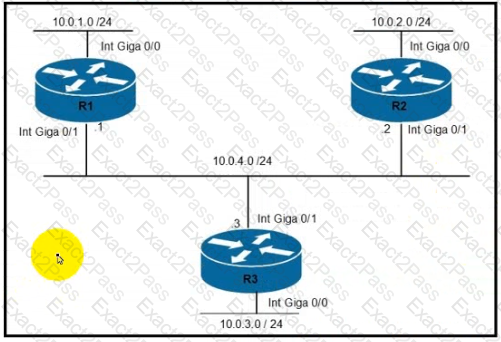
Router R1 must be configured to reach the 10.0.3.0/24 network from the 10.0.1.0/24 segment.
Which command must be used to configure the route?
Refer to the exhibit.
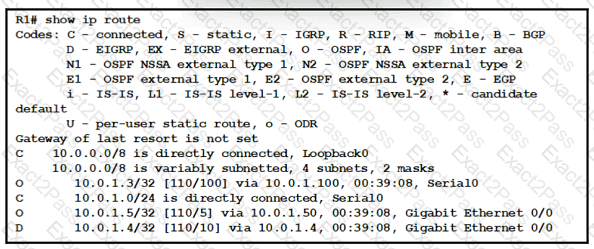
What does route 10.0.1.3/32 represent in the routing table?
The clients and OHCP server reside on different subnets. Which command must be used to forward requests and replies between clients on the 10.10.0.1/24 subnet and the DHCP server at 192.168.10.1?
A network analyst is tasked with configuring the date and time on a router using EXEC mode. The date must be set to January 1. 2020 and the time must be set to 12:00 am. Which command should be used?
Refer to the exhibit.
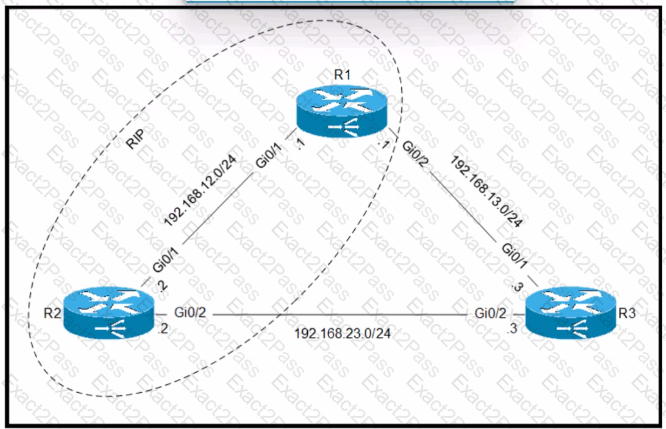
Routers R1 and R2 are configured with RIP as the dynamic routing protocol. A network engineer must configure R1 with a floating static route to serve as a backup route to network 192.168.23. Which command must the engineer configure on R1?
Refer to the exhibit.
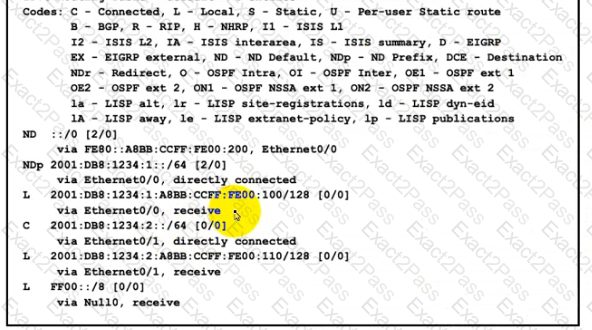
The administrator must configure a floating sialic default route that points to 2001:db8:1234:2::1 and replaces the current default route only if it fails. Which command must the engineer configure on the CPE?
Which two wireless security stewards use Counter Mode Cipher Block Chaining Message Authentication Code Protocol for encryption and data integrity'? (Choose two.)
Exhibit.
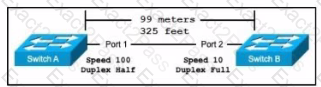
The switches are connected via a Cat5 Ethernet cable that was successfully tested. The Interfaces are configured as access ports and are both in a 'down" status. What is the cause of this issue?
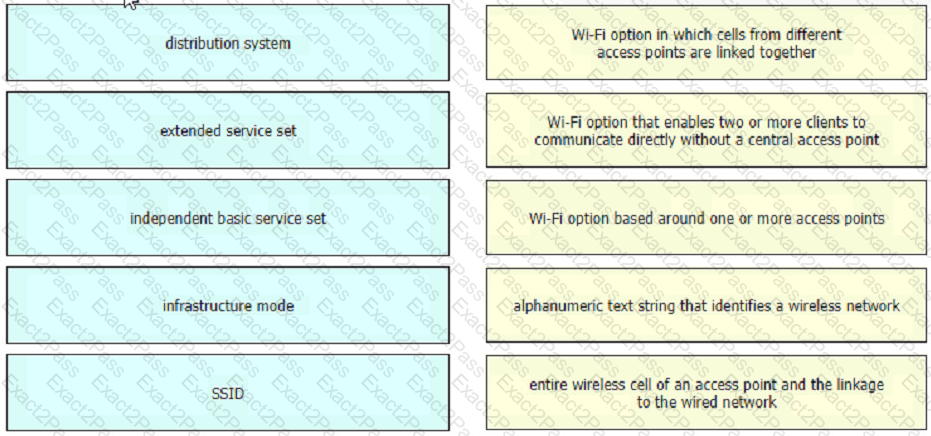
Drag and drop the Wi-Fi terms from the left onto the descriptions on the right.
Refer to the exhibit.
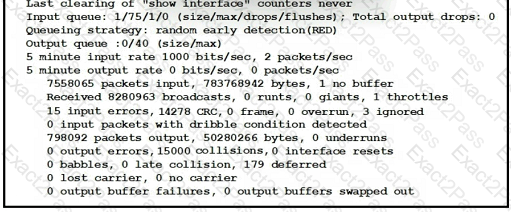
An administrator received a call from a branch office regarding poor application performance hosted at the headquarters. Ethernet 1 is connected between Router1 and the LAN switch. What identifies the issue?
Refer to the exhibit.
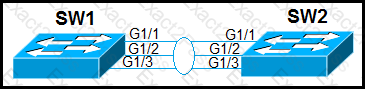
Which configuration establishes a Layer 2 LACP EtherChannel when applied to both switches?