Which system monitors local system operation and local network access for violations of a security policy?
What is personally identifiable information that must be safeguarded from unauthorized access?
Which action should be taken if the system is overwhelmed with alerts when false positives and false negatives are compared?
Which signature impacts network traffic by causing legitimate traffic to be blocked?
An engineer is working with the compliance teams to identify the data passing through the network. During analysis, the engineer informs the compliance team that external penmeter data flows contain records, writings, and artwork Internal segregated network flows contain the customer choices by gender, addresses, and product preferences by age. The engineer must identify protected data. Which two types of data must be identified'? (Choose two.)
Which two elements of the incident response process are stated in NIST Special Publication 800-61 r2? (Choose two.)
Which classification of cross-site scripting attack executes the payload without storing it for repeated use?
An engineer is analyzing a recent breach where confidential documents were altered and stolen by the receptionist. Further analysis shows that the threat actor connected an externa USB device to bypass security restrictions and steal data. The engineer could not find an external USB device Which piece of information must an engineer use for attribution in an investigation?
Which attack is the network vulnerable to when a stream cipher like RC4 is used twice with the same key?
Which evasion technique is indicated when an intrusion detection system begins receiving an abnormally high volume of scanning from numerous sources?
Which process is used when IPS events are removed to improve data integrity?
Refer to the exhibit.
Which kind of attack method is depicted in this string?
A user reports difficulties accessing certain external web pages. When an engineer examines traffic to and from the external domain in full packet captures, they notice that many SYNs have the same sequence number, source, and destination IP address, but they have different payloads. What is causing this situation?
An analyst is using the SIEM platform and must extract a custom property from a Cisco device and capture the phrase, "File: Clean." Which regex must the analyst import?
Which type of evidence supports a theory or an assumption that results from initial evidence?
An engineer runs a suspicious file in a sandbox analysis tool to see the outcome. The analysis report shows that outbound callouts were made post infection.
Which two pieces of information from the analysis report are needed to investigate the callouts? (Choose two.)
What are the two differences between stateful and deep packet inspection? (Choose two )
What is the difference between indicator of attack (loA) and indicators of compromise (loC)?
Which information must an organization use to understand the threats currently targeting the organization?
A user received a malicious attachment but did not run it. Which category classifies the intrusion?
According to the NIST SP 800-86. which two types of data are considered volatile? (Choose two.)
Refer to the exhibit.
What is the potential threat identified in this Stealthwatch dashboard?
Which two pieces of information are collected from the IPv4 protocol header? (Choose two.)
Which type of attack uses a botnet to reflect requests off of an NTP server to overwhelm a target?
Which data format is the most efficient to build a baseline of traffic seen over an extended period of time?
Refer to the exhibit.
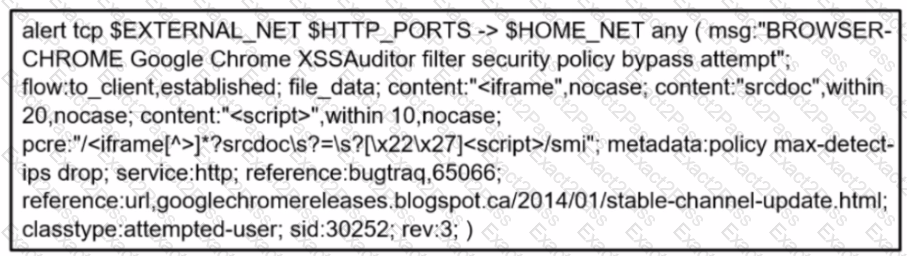
A company's user HTTP connection to a malicious site was blocked according to configured policy What is the source technology used for this measure'?
An engineer configured regular expression “.”\.(pd][Oo][Cc)|[Xx][LI][Ss]|[Pp][Pp][Tt]) HTTP/1 .[01]" on Cisco ASA firewall. What does this regular expression do?
Which step in the incident response process researches an attacking host through logs in a SIEM?
Drag and drop the uses on the left onto the type of security system on the right.
An engineer needs to have visibility on TCP bandwidth usage, response time, and latency, combined with deep packet inspection to identify unknown software by its network traffic flow. Which two features of Cisco Application Visibility and Control should the engineer use to accomplish this goal? (Choose two.)
An organization is cooperating with several third-party companies. Data exchange is on an unsecured channel using port 80 Internal employees use the FTP service to upload and download sensitive data An engineer must ensure confidentiality while preserving the integrity of the communication. Which technology must the engineer implement in this scenario'?
What causes events on a Windows system to show Event Code 4625 in the log messages?
A security engineer must investigate a recent breach within the organization. An engineer noticed that a breached workstation is trying to connect to the domain "Ranso4730-mware92-647". which is known as malicious. In which step of the Cyber Kill Chain is this event?
Refer to the exhibit.
Which kind of attack method is depicted in this string?
Which two components reduce the attack surface on an endpoint? (Choose two.)
An analyst is exploring the functionality of different operating systems.
What is a feature of Windows Management Instrumentation that must be considered when deciding on an operating system?
What is the impact of false positive alerts on business compared to true positive?
An engineer needs to fetch logs from a proxy server and generate actual events according to the data received. Which technology should the engineer use to accomplish this task?
Which open-sourced packet capture tool uses Linux and Mac OS X operating systems?
Refer to the exhibit.
An attacker scanned the server using Nmap.
What did the attacker obtain from this scan?
What is the difference between the ACK flag and the RST flag in the NetFlow log session?
Endpoint logs indicate that a machine has obtained an unusual gateway address and unusual DNS servers via DHCP Which type of attack is occurring?
A SOC analyst detected connections to known C&C and port scanning activity to main HR database servers from one of the HR endpoints via Cisco StealthWatch. What are the two next steps of the SOC team according to the NISTSP800-61 incident handling process? (Choose two)
An engineer received a flood of phishing emails from HR with the source address HRjacobm@companycom. What is the threat actor in this scenario?
An analyst received a ticket regarding a degraded processing capability for one of the HR department's servers. On the same day, an engineer noticed a disabled antivirus software and was not able to determine when or why it occurred. According to the NIST Incident Handling Guide, what is the next phase of this investigation?
What is the difference between inline traffic interrogation and traffic mirroring?
Refer to the exhibit.
An engineer is reviewing a Cuckoo report of a file. What must the engineer interpret from the report?
Which incidence response step includes identifying all hosts affected by an attack?
An engineer is addressing a connectivity issue between two servers where the remote server is unable to establish a successful session. Initial checks show that the remote server is not receiving an SYN-ACK while establishing a session by sending the first SYN. What is causing this issue?
Refer to the exhibit.
Which stakeholders must be involved when a company workstation is compromised?
An engineer needs to discover alive hosts within the 192.168.1.0/24 range without triggering intrusive portscan alerts on the IDS device using Nmap. Which command will accomplish this goal?
Which metric should be used when evaluating the effectiveness and scope of a Security Operations Center?
Which HTTP header field is used in forensics to identify the type of browser used?
Refer to the exhibit.
An analyst was given a PCAP file, which is associated with a recent intrusion event in the company FTP server Which display filters should the analyst use to filter the FTP traffic?
What is a difference between signature-based and behavior-based detection?
Which two elements of the incident response process are stated in NIST Special Publication 800-61 r2? (Choose two.)
When an event is investigated, which type of data provides the investigate capability to determine if data exfiltration has occurred?
What is a benefit of agent-based protection when compared to agentless protection?
An engineer discovered a breach, identified the threat’s entry point, and removed access. The engineer was able to identify the host, the IP address of the threat actor, and the application the threat actor targeted. What is the next step the engineer should take according to the NIST SP 800-61 Incident handling guide?
Refer to the exhibit.
A suspicious IP address is tagged by Threat Intelligence as a brute-force attempt source After the attacker produces many of failed login entries, it successfully compromises the account. Which stakeholder is responsible for the incident response detection step?
Refer to the exhibit.
What is the expected result when the "Allow subdissector to reassemble TCP streams" feature is enabled?
Refer to the exhibit.
An engineer is analyzing this Cuckoo Sandbox report for a PDF file that has been downloaded from an email. What is the state of this file?