Which application is used for the central management and deployment of licenses and packages?
Of all the Check Point components in your network, which one changes most often and should be backed up most frequently?
When an Admin logs into SmartConsole and sees a lock icon on a gateway object and cannot edit that object, what does that indicate?
Fill in the blanks: A Security Policy is created in_____, stored in the_____ and Distributed to the various
Fill in the blank: Browser-based Authentication sends users to a web page to acquire identities using ___________.
What are two basic rules Check Point recommending for building an effective security policy?
Which of the following is used to extract state related information from packets and store that information in state tables?
When doing a Stand-Alone Installation, you would install the Security Management Server with which other Check Point architecture component?
Fill in the blank: When tunnel test packets no longer invoke a response, SmartView Monitor displays _____________ for the given VPN tunnel.
Vanessa is attempting to log into the Gaia Web Portal. She is able to login successfully. Then she tries the same username and password for SmartConsole but gets the message in the screenshot image below. She has checked that the IP address of the Server is correct and the username and password she used to login into Gaia is also correct.
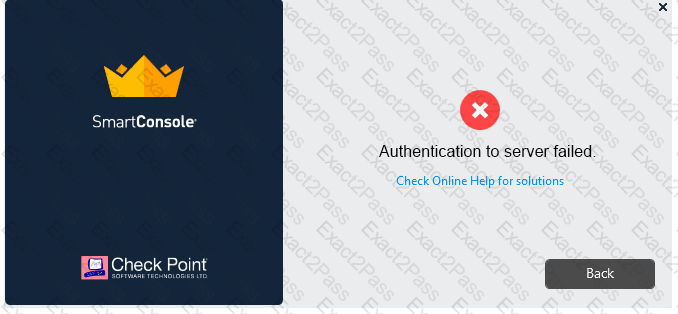
What is the most likely reason?
Fill in the blank: The_____is used to obtain identification and security information about network users.
Choose what BEST describes the reason why querying logs now are very fast.
R80.10 management server can manage gateways with which versions installed?
Name the file that is an electronically signed file used by Check Point to translate the features in the license into a code?
What is the user ID of a user that have all the privileges of a root user?
Sticky Decision Function (SDF) is required to prevent which of the following? Assume you set up an Active-Active cluster.
In the Check Point Security Management Architecture, which component(s) can store logs?
Fill in the blank: In Security Gateways R75 and above, SIC uses ______________ for encryption.
Fill in the blank: To create policy for traffic to or from a particular location, use the _____________.
What needs to be configured if the NAT property ‘Translate destination on client side’ is not enabled in Global properties?
Fill in the blank: Each cluster, at a minimum, should have at least ___________ interfaces.
In order for changes made to policy to be enforced by a Security Gateway, what action must an administrator perform?
Which of the following is NOT a valid application navigation tab in the R80 SmartConsole?
Which of the following is NOT an authentication scheme used for accounts created through SmartConsole?
Which Check Point software blade monitors Check Point devices and provides a picture of network and security performance?
Which option in tracking allows you to see the amount of data passed in the connection?
Which part of SmartConsole allows administrators to add, edit delete, and clone objects?
Bob and Joe both have Administrator Roles on their Gaia Platform. Bob logs in on the WebUI and then Joe logs in through CLI. Choose what BEST describes the following scenario, where Bob and Joe are both logged in:
When a Security Gateways sends its logs to an IP address other than its own, which deployment option is installed?
A Check Point Software license consists of two components, the Software Blade and the Software Container. There are ______ types of Software Containers: ________.
Identity Awareness lets an administrator easily configure network access and auditing based on three items Choose the correct statement.
You are the Check Point administrator for Alpha Corp with an R80 Check Point estate. You have received a call by one of the management users stating that they are unable to browse the Internet with their new tablet connected to the company Wireless. The Wireless system goes through the Check Point Gateway. How do you review the logs to see what the problem may be?
Which type of Check Point license is tied to the IP address of a specific Security Gateway and cannot be transferred to a gateway that has a different IP address?
What is the most complete definition of the difference between the Install Policy button on the SmartConsole’s tab, and the Install Policy within a specific policy?
A layer can support different combinations of blades What are the supported blades:
Fill in the blank: SmartConsole, SmartEvent GUI client, and ___________ allow viewing of billions of consolidated logs and shows them as prioritized security events.
What Check Point tool is used to automatically update Check Point products for the Gaia OS?
AdminA and AdminB are both logged into SmartConsole. What does it mean if AdminB sees a lock icon on a rule? Choose the BEST answer.
Administrator Dave logs into R80 Management Server to review and makes some rule changes. He notices that there is a padlock sign next to the DNS rule in the Rule Base.
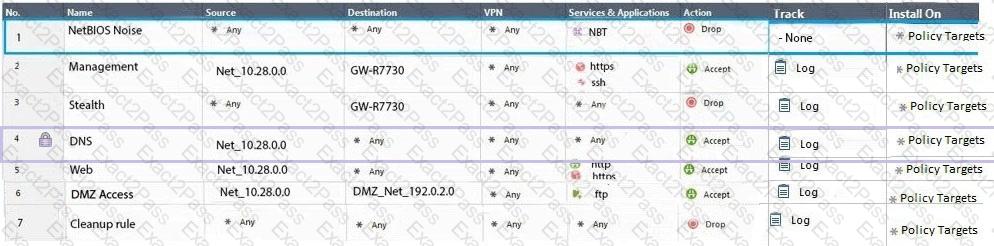
What is the possible explanation for this?
Which of the completed statements is NOT true? The WebUI can be used to manage Operating System user accounts and
The purpose of the Communication Initialization process is to establish a trust between the Security Management Server and the Check Point gateways. Which statement best describes this Secure Internal
Communication (SIC)?
Gaia has two default user accounts that cannot be deleted. What are those user accounts?
Which of the following blades is NOT subscription-based and therefore does not have to be renewed on a regular basis?
In a Distributed deployment, the Security Gateway and the Security Management software are installed on what platforms?
What key is used to save the current CPView page in a filename format cpview_“cpview process ID”. cap”number of captures”?
When configuring LDAP with User Directory integration, changes applied to a User Directory template are:
Which single Security Blade can be turned on to block both malicious files from being downloaded as well as block websites known to host malware?
In which scenario is it a valid option to transfer a license from one hardware device to another?
You are asked to check the status of several user-mode processes on the management server and gateway. Which of the following processes can only be seen on a Management Server?
When configuring LDAP User Directory integration, Changes applied to a User Directory template are:
Which of the following statements about Site-to-Site VPN Domain-based is NOT true?
Route-based— The Security Gateways will have a Virtual Tunnel Interface (VTI) for each VPN Tunnel with a peer VPN Gateway. The Routing Table can have routes to forward traffic to these VTls. Any traffic routed through a VTI is automatically identified as VPN Traffic and is passed through the VPN Tunnel associated with the VTI.
You want to store the GAiA configuration in a file for later reference. What command should you use?
What data MUST be supplied to the SmartConsole System Restore window to restore a backup?
What are the software components used by Autonomous Threat Prevention Profiles in R8I.20 and higher?
Identify the ports to which the Client Authentication daemon listens on by default?
What is required for a certificate-based VPN tunnel between two gateways with separate management systems?
What does it mean if Deyra sees the gateway status:
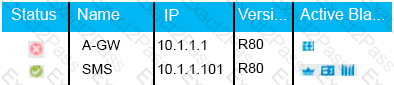
Choose the BEST answer.
Which of the following is a new R80.10 Gateway feature that had not been available in R77.X and older?
In which deployment is the security management server and Security Gateway installed on the same appliance?
For Automatic Hide NAT rules created by the administrator what is a TRUE statement?
While enabling the Identity Awareness blade the Identity Awareness wizard does not automatically detect the windows domain Why does it not detect the windows domain?
Which product correlates logs and detects security threats, providing a centralized display of potential attack patterns from all network devices?
Phase 1 of the two-phase negotiation process conducted by IKE operates in ______ mode.
Most Check Point deployments use Gaia but which product deployment utilizes special Check Point code (with unification in R81.10)?
Which deployment adds a Security Gateway to an existing environment without changing IP routing?
Which of the following methods can be used to update the trusted log server regarding the policy and configuration changes performed on the Security Management Server?
When changes are made to a Rule base, it is important to _______________ to enforce changes.
Which of the following is NOT an advantage to using multiple LDAP servers?
When logging in for the first time to a Security management Server through SmartConsole, a fingerprint is saved to the:
Which option in a firewall rule would only match and allow traffic to VPN gateways for one Community in common?
You are the Check Point administrator for Alpha Corp. You received a call that one of the users is unable to browse the Internet on their new tablet which is connected to the company wireless, which goes through a Check Point Gateway. How would you review the logs to see what is blocking this traffic?
Using ClusterXL, what statement is true about the Sticky Decision Function?
Which configuration element determines which traffic should be encrypted into a VPN tunnel vs. sent in the clear?
Which Identity Source(s) should be selected in Identity Awareness for when there is a requirement for a higher level of security for sensitive servers?
A stateful inspection firewall works by registering connection data and compiling this information. Where is the information stored?
What is the most recommended installation method for Check Point appliances?