Last Update 15 hours ago Total Questions : 293
The LPIC-1 Exam 101, Part 1 of 2, version 5.0 content is now fully updated, with all current exam questions added 15 hours ago. Deciding to include 101-500 practice exam questions in your study plan goes far beyond basic test preparation.
You'll find that our 101-500 exam questions frequently feature detailed scenarios and practical problem-solving exercises that directly mirror industry challenges. Engaging with these 101-500 sample sets allows you to effectively manage your time and pace yourself, giving you the ability to finish any LPIC-1 Exam 101, Part 1 of 2, version 5.0 practice test comfortably within the allotted time.
Consider the following output from the command ls –i:
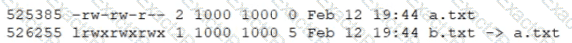
How would a new file named c.txt be created with the same inode number as a.txt (Inode 525385)?
Which of the following regular expressions represents a single upper-case letter?
Which of the following examples for Bash file globbing matches a file named root-can-do-this.txt when used in the directory holding that file? (Choose three correct answers.)
When piping the output of find to the xargs command, what option to find is useful if the filenames have spaces in them?
Which command reads and displays the current contents of the Kernel Ring Buffer on the command line? (Specify ONLY the command without any path or parameters.)
After running the command umount /mnt, the following error message is displayed:
umount: /mnt: device is busy.
What is a common reason for this message?
Which of the following apt-get commands will install the newest versions of all currently installed packages?

